Five Eyes, Five Principles: Securing Innovation
Five eyes five principles secure innovation – Five Eyes, Five Principles: Securing Innovation sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. The Five Eyes alliance, a powerful collaboration of intelligence agencies from the United States, United Kingdom, Canada, Australia, and New Zealand, has played a pivotal role in global security for decades.
However, in the face of rapidly evolving technological landscapes and increasingly sophisticated cyber threats, the alliance has recognized the need to embrace a new paradigm – secure innovation.
This paradigm shift is not just about bolstering defenses; it’s about proactively shaping the future of technology in a way that safeguards national security while fostering innovation. The Five Eyes alliance has articulated five key principles that underpin this approach, principles that are designed to guide the development and deployment of secure technologies across a range of industries.
The Five Eyes Alliance
The Five Eyes alliance is a highly influential intelligence-sharing partnership between five countries: the United States, the United Kingdom, Canada, Australia, and New Zealand. It’s a unique collaboration that has shaped global security for decades, playing a crucial role in intelligence gathering, counterterrorism efforts, and international security cooperation.
History and Formation
The roots of the Five Eyes alliance can be traced back to the Second World War, when the United States and the United Kingdom established a close intelligence relationship. This partnership, known as the “Special Relationship,” laid the groundwork for the modern Five Eyes alliance.
After the war, Canada, Australia, and New Zealand joined the intelligence-sharing network, solidifying the alliance’s structure and scope. The alliance’s formalization occurred in the 1950s, driven by the need to share intelligence during the Cold War and the growing threat of Soviet espionage.
The “Five Eyes Five Principles” framework for secure innovation emphasizes collaboration and trust, aiming to balance security with progress. These principles were a hot topic at Paradoxcon, and you can check out a ranking of the best talks from the event here.
The discussions at Paradoxcon highlighted the need for a nuanced approach to secure innovation, ensuring that we protect our critical infrastructure while fostering an environment where new technologies can flourish.
The Five Eyes alliance has remained a vital component of global security, evolving to address emerging threats and challenges.
Objectives and Key Principles
The primary objective of the Five Eyes alliance is to enhance national security through intelligence sharing and collaboration. This includes:
- Sharing intelligence:Members share raw intelligence data, analytical reports, and assessments, enabling a comprehensive understanding of global threats.
- Joint operations:The alliance conducts joint operations, such as surveillance, counterterrorism, and cyber security, leveraging combined expertise and resources.
- Technological cooperation:The alliance fosters technological cooperation, sharing advancements in signal intelligence, data analysis, and cyber security.
- Mutual support:Members provide mutual support during crises and emergencies, sharing intelligence and resources to respond effectively.
The alliance operates based on a set of key principles, including:
- Mutual trust:Members share highly sensitive information based on mutual trust and a shared commitment to security.
- Confidentiality:Intelligence sharing is governed by strict confidentiality agreements, ensuring sensitive information is protected.
- Transparency:Members maintain transparency within the alliance, ensuring all partners are aware of intelligence activities and operations.
- Accountability:The alliance adheres to legal and ethical frameworks, ensuring accountability for intelligence activities and operations.
Examples of Collaboration
The Five Eyes alliance has a long history of collaboration on various intelligence-sharing and security operations. Notable examples include:
- Counterterrorism efforts:The alliance played a key role in disrupting terrorist networks, sharing intelligence and conducting joint operations against groups like Al-Qaeda and ISIS.
- Cybersecurity:The alliance has collaborated to combat cyber threats, sharing information on cyberattacks, malware, and cybercrime, and developing joint strategies to enhance cyber security.
- Nuclear non-proliferation:The alliance has worked together to monitor nuclear proliferation activities, sharing intelligence and conducting joint operations to prevent the spread of nuclear weapons.
- Espionage and counterintelligence:The alliance has collaborated to combat espionage and counterintelligence activities, sharing information on foreign intelligence agencies and their operations.
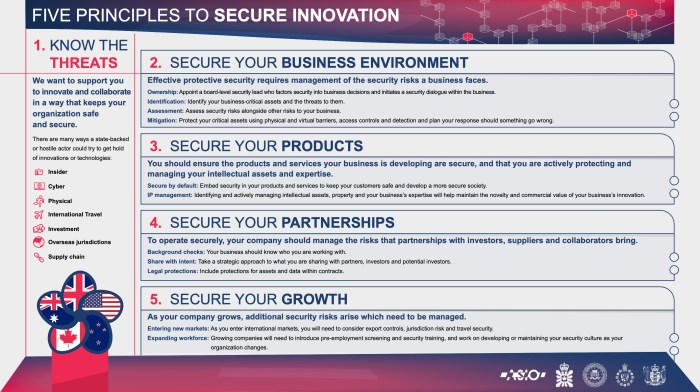
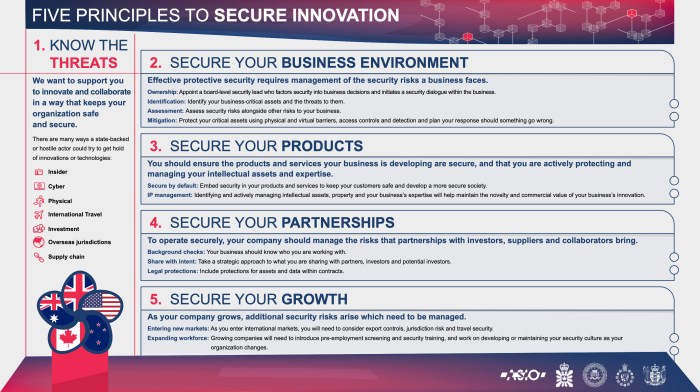
The Five Principles of Secure Innovation
The Five Principles of Secure Innovation provide a framework for organizations to design, develop, and deploy technology while prioritizing security. These principles encourage a proactive approach to security, integrating it into the core of innovation processes rather than treating it as an afterthought.
The “Five Eyes” agreement emphasizes secure innovation, a principle that’s crucial for ensuring the safety and privacy of our data. While we navigate the complex world of cybersecurity, it’s important to remember the simple joys of life, like showing appreciation for the amazing mothers in our lives.
This Mother’s Day, why not explore our favorite mail order gifts for mothers day and find the perfect way to express your love? After all, fostering strong relationships is a vital part of a secure and thriving society, one that’s built on the foundation of trust and open communication, just like the “Five Eyes” agreement aims to achieve.
The Five Principles
The Five Principles of Secure Innovation are:
- Design for Security:Security should be considered from the very beginning of the design process, rather than as an afterthought. This involves incorporating security features and controls into the design of systems, applications, and products.
- Build Security In:This principle emphasizes the importance of building security into every stage of the development lifecycle, from coding and testing to deployment and ongoing operations.
The Five Eyes Five Principles for Secure Innovation are crucial for fostering a safe and trusted environment for technological advancement. Just like ensuring a safe and functional electrical system, understanding the principles of secure innovation is vital. For example, learning how to properly how to hardwire a light fixture is essential for any DIY project, and similarly, adhering to the Five Eyes principles can help prevent vulnerabilities in our digital infrastructure.
By applying these principles, we can build a more secure and resilient future for all.
This requires implementing secure development practices and tools.
- Verify Security:Continuous verification of security measures is crucial. This involves regularly testing and auditing systems to identify vulnerabilities and ensure that security controls are effective.
- Respond to Security Threats:Organizations must be prepared to respond effectively to security threats.
This involves having a comprehensive incident response plan, as well as processes for detecting, containing, and mitigating security incidents.
- Foster Security Culture:A strong security culture is essential for successful secure innovation. This involves promoting security awareness among all employees, fostering a culture of responsibility, and encouraging the reporting of security concerns.
Applications of the Five Principles
These principles can be applied across various industries and sectors. For example, in the healthcare industry, the principles can be used to secure sensitive patient data, while in the financial sector, they can be used to protect customer financial information.
The principles are also relevant in the automotive industry, where they can be used to secure connected vehicles and prevent cyberattacks.
Challenges and Opportunities, Five eyes five principles secure innovation
Implementing these principles can present challenges, such as:
- Cultural Shift:Adopting a security-first mindset can require a significant cultural shift within an organization. This involves educating employees about security risks and best practices.
- Technical Expertise:Implementing secure innovation principles requires specialized technical expertise, including knowledge of security tools, techniques, and best practices.
- Resource Constraints:Implementing security measures can be resource-intensive, requiring investments in personnel, technology, and training.
However, there are also significant opportunities associated with implementing these principles:
- Enhanced Security:By adopting these principles, organizations can significantly enhance their security posture, reducing the risk of data breaches and other security incidents.
- Increased Trust:A strong security track record can build trust with customers, partners, and regulators, leading to greater confidence in an organization’s products and services.
- Competitive Advantage:Organizations that prioritize security can gain a competitive advantage by demonstrating their commitment to protecting sensitive information.
Secure Innovation in the Five Eyes Context

The Five Eyes alliance, comprising Australia, Canada, New Zealand, the United Kingdom, and the United States, has a profound impact on the landscape of secure innovation. This impact stems from the shared intelligence and security interests of these nations, which influence their approaches to technological development and data protection.
Impact of the Five Eyes Alliance on Secure Innovation Practices
The Five Eyes alliance fosters a collaborative environment for secure innovation by encouraging information sharing and joint research initiatives. This collaboration enables the development of best practices and standards for secure technology, ultimately enhancing the overall security posture of member nations.
The alliance’s influence is evident in the development of cybersecurity frameworks, encryption standards, and regulations that promote secure innovation.
Comparison of Secure Innovation Approaches within the Five Eyes Countries
Secure innovation approaches within the Five Eyes countries exhibit both similarities and differences. All members prioritize data privacy and security, but their specific regulations and policies may vary. For instance, the European Union’s General Data Protection Regulation (GDPR), which has influenced data protection laws in the UK, emphasizes individual rights and data control, while the United States’ approach is more focused on balancing privacy with national security.
Despite these differences, the Five Eyes countries share a common goal of fostering a secure and trusted digital environment for innovation.
Role of Technology and Data Security in Fostering Secure Innovation
Technology plays a crucial role in driving secure innovation. Advanced technologies like artificial intelligence (AI), blockchain, and quantum computing offer immense potential for innovation, but they also introduce new security challenges. Data security is paramount in this context. The Five Eyes countries recognize the need for robust data protection mechanisms to safeguard sensitive information and maintain public trust.
This includes implementing strong encryption protocols, data anonymization techniques, and secure data storage solutions. Furthermore, the alliance encourages the development of technologies that enhance security and privacy by design. Examples include homomorphic encryption, which allows computations on encrypted data without decrypting it, and differential privacy, which protects individual data while enabling statistical analysis.
Case Studies of Secure Innovation in Five Eyes Nations: Five Eyes Five Principles Secure Innovation
The Five Eyes nations have a long history of collaboration in intelligence sharing and security. In recent years, this collaboration has extended to the realm of secure innovation, with each country developing and implementing initiatives to promote secure and trustworthy technologies.
This section will explore successful case studies of secure innovation initiatives within the Five Eyes countries, highlighting the key features and impact of these projects.
Successful Case Studies of Secure Innovation Initiatives in Five Eyes Nations
These case studies showcase the diverse approaches and successful outcomes of secure innovation initiatives across the Five Eyes countries:
| Country | Initiative | Key Features | Impact |
|---|---|---|---|
| United States | National Institute of Standards and Technology (NIST) Cybersecurity Framework | Provides a voluntary framework for organizations to manage and reduce cybersecurity risks. | Increased awareness and adoption of cybersecurity best practices across various sectors. |
| United Kingdom | Cyber Security Information Sharing Partnership (CISSP) | A collaborative platform for sharing cyber threat intelligence and best practices among businesses and government agencies. | Enhanced threat detection and response capabilities, leading to a more resilient cyber ecosystem. |
| Canada | Cyber Security Strategy for Canada | A comprehensive strategy that Artikels the government’s approach to protecting critical infrastructure and promoting cybersecurity innovation. | Increased investment in cybersecurity research and development, fostering a vibrant ecosystem of cybersecurity startups and innovators. |
| Australia | Australian Cyber Security Centre (ACSC) | A national cybersecurity agency that provides guidance, support, and resources to organizations and individuals. | Improved cybersecurity awareness and preparedness among Australian citizens and businesses. |
| New Zealand | New Zealand Cyber Security Strategy | A national strategy that aims to build a more secure and resilient cyber environment. | Increased investment in cybersecurity education and training, empowering individuals and organizations to better protect themselves from cyber threats. |
The case studies demonstrate that secure innovation initiatives in Five Eyes nations are characterized by a strong emphasis on collaboration, information sharing, and a commitment to promoting a secure and trustworthy digital environment.
The Future of Secure Innovation in the Five Eyes Alliance
The Five Eyes alliance, formed in the post-World War II era, has played a crucial role in safeguarding national security and promoting global stability. However, the digital age presents new challenges and opportunities for the alliance, demanding a forward-looking approach to secure innovation.
As technology evolves at an unprecedented pace, the alliance must adapt to ensure its effectiveness in protecting its citizens and interests.
Evolving Threats and Challenges to Secure Innovation in the Digital Age
The digital landscape is characterized by rapid technological advancements, increased interconnectedness, and evolving threat actors. These factors pose significant challenges to secure innovation within the Five Eyes framework. The increasing sophistication of cyberattacks, the proliferation of new technologies like artificial intelligence (AI) and quantum computing, and the blurring lines between the physical and digital worlds necessitate a comprehensive approach to secure innovation.
- Cyberattacks:The frequency and severity of cyberattacks are escalating, targeting critical infrastructure, government institutions, and private companies. Advanced persistent threats (APTs) and ransomware attacks pose significant risks to national security and economic stability.
- Emerging Technologies:The rapid development and adoption of AI, quantum computing, and other disruptive technologies present both opportunities and challenges. While these technologies can enhance innovation and economic growth, they also create new vulnerabilities and potential for misuse.
- Data Privacy and Security:The increasing volume and sensitivity of data generated and shared in the digital age raise concerns about privacy and security. Balancing the need for data access with the protection of individual privacy is a key challenge for secure innovation.
- Supply Chain Security:The interconnectedness of global supply chains makes them vulnerable to disruptions and malicious actors. Ensuring the security of software, hardware, and other components used in critical systems is essential for secure innovation.


