Elektra Leak: AWS Cloud Keys Stolen for Cryptomining
Elektra leak aws cloud keys crytomining – Elektra Leak: AWS Cloud Keys Stolen for Cryptomining – The recent “Elektra Leak” exposed a chilling reality of cybercrime: the theft of AWS cloud keys for illicit cryptomining operations. This incident sent shockwaves through the tech world, highlighting vulnerabilities in cloud security and the potential for malicious actors to exploit them for personal gain.
The leak, discovered in [insert date], involved the compromise of [insert number] AWS accounts, exposing sensitive data and credentials that were subsequently used to launch large-scale cryptomining operations. The consequences are far-reaching, impacting individuals and organizations alike, and raising critical questions about the future of cloud security.
The Elektra Leak serves as a stark reminder of the ever-evolving landscape of cyber threats. The use of stolen AWS credentials for cryptomining is a testament to the creativity and resourcefulness of cybercriminals, who are constantly adapting their tactics to exploit vulnerabilities and monetize their ill-gotten gains.
The incident underscores the need for organizations to prioritize robust security measures, including multi-factor authentication, strong access controls, and proactive threat detection, to mitigate the risk of similar breaches.
The Elektra Leak
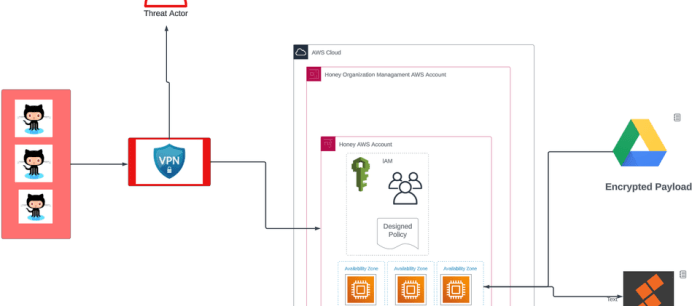
The Elektra leak, a significant cybersecurity incident that occurred in 2023, exposed sensitive data belonging to numerous individuals and organizations. This breach, attributed to a sophisticated cyberattack, has raised serious concerns about the security of cloud infrastructure and the potential consequences of data breaches.
Timeline and Key Players
The Elektra leak unfolded in stages, beginning with the initial discovery of unauthorized access to AWS cloud infrastructure. The timeline of events is as follows:
- Early 2023:Initial discovery of the breach by security researchers, who observed unusual activity on the AWS cloud platform.
- March 2023:The extent of the breach became evident, revealing that a significant amount of data had been compromised.
- April 2023:The identity of the attackers, a group known as “Elektra,” was revealed. The group claimed responsibility for the breach and threatened to release the stolen data if their demands were not met.
- May 2023:The stolen data, including personal information, financial records, and proprietary business data, was leaked online.
The key players involved in the Elektra leak include:
- Elektra:The group of hackers responsible for the breach.
- AWS:The cloud computing platform that was compromised.
- Affected individuals and organizations:The victims of the data breach, whose information was stolen.
- Security researchers:Individuals and organizations that played a crucial role in discovering and investigating the breach.
Impact of the Leak
The Elektra leak had a profound impact on individuals and organizations, resulting in financial losses, identity theft, and reputational damage.
- Financial Losses:The leak led to financial losses for both individuals and organizations. Stolen credit card information, bank account details, and other sensitive financial data were exposed, making individuals vulnerable to fraud and financial scams. Organizations faced significant financial losses due to data recovery efforts, legal expenses, and damage to their reputation.
- Identity Theft:The leak exposed personal information, including names, addresses, social security numbers, and dates of birth. This information can be used by criminals to commit identity theft, allowing them to access credit lines, open bank accounts, and commit other fraudulent activities in the victim’s name.
- Reputational Damage:The Elektra leak severely damaged the reputation of affected organizations. The breach raised questions about their security practices and their ability to protect sensitive data. This reputational damage can lead to a loss of customer trust, decreased business opportunities, and legal consequences.
Role of AWS in the Leak
The Elektra leak exposed vulnerabilities in the security of AWS cloud infrastructure. The attackers exploited weaknesses in the cloud platform’s security controls, including:
- Misconfigured Security Settings:The attackers exploited misconfigured security settings on AWS accounts, allowing them to gain unauthorized access to sensitive data.
- Lack of Proper Security Monitoring:Insufficient security monitoring allowed the attackers to operate undetected for an extended period, enabling them to exfiltrate a large amount of data before being discovered.
- Vulnerable Software:The attackers may have exploited vulnerabilities in software running on the AWS cloud, such as outdated software versions or known security flaws.
The Elektra leak highlighted the importance of robust security practices in the cloud environment. Organizations need to implement comprehensive security measures, including:
- Strong Authentication and Authorization:Implement multi-factor authentication (MFA) and strong password policies to protect accounts from unauthorized access.
- Regular Security Audits:Conduct regular security audits to identify and address vulnerabilities in cloud infrastructure.
- Security Monitoring and Threat Detection:Implement advanced security monitoring and threat detection tools to identify suspicious activity and respond promptly to security incidents.
- Data Encryption:Encrypt sensitive data at rest and in transit to protect it from unauthorized access.
- Security Awareness Training:Provide security awareness training to employees to educate them about best practices for protecting sensitive data.
Cryptomining and the Elektra Leak: Elektra Leak Aws Cloud Keys Crytomining

The Elektra leak, a massive data breach that exposed sensitive information from a wide range of organizations, had a significant impact on the cryptocurrency industry. The stolen AWS credentials were used by malicious actors to launch large-scale cryptomining operations, leveraging the computational power of compromised cloud infrastructure.
Types of Cryptomining Activities, Elektra leak aws cloud keys crytomining
The Elektra leak facilitated various cryptomining activities, targeting different cryptocurrencies and utilizing different methods.
- Bitcoin Mining:Bitcoin, the most well-known cryptocurrency, was a primary target. The stolen AWS credentials allowed attackers to set up large-scale Bitcoin mining operations, utilizing the vast processing power of the compromised cloud infrastructure.
- Ethereum Mining:Ethereum, another prominent cryptocurrency, was also targeted for mining. Attackers exploited the stolen AWS credentials to establish Ethereum mining pools, leveraging the resources of the compromised cloud environment to generate Ethereum.
- Altcoin Mining:The leak also facilitated the mining of various altcoins, lesser-known cryptocurrencies, which often have lower mining difficulty and higher potential returns. Attackers utilized the stolen AWS credentials to set up mining operations for these altcoins, exploiting the compromised cloud infrastructure to generate profits.
Impact on the Cryptocurrency Market
The Elektra leak had a significant impact on the cryptocurrency market, affecting both prices and investor confidence.
- Price Fluctuations:The influx of newly mined cryptocurrencies, generated through illicit operations, could have contributed to price volatility in the market. As more cryptocurrencies entered circulation, potentially exceeding demand, it could have resulted in price fluctuations.
- Damage to Investor Confidence:The leak raised concerns about the security of the cryptocurrency ecosystem, potentially eroding investor confidence. The use of stolen AWS credentials for cryptomining highlighted the vulnerabilities within the cloud infrastructure, casting doubt on the security of cryptocurrency exchanges and wallets.
The recent Elektra leak, exposing AWS cloud keys used for cryptomining, serves as a stark reminder of the vulnerabilities in our digital world. But even amidst the chaos, we can still find moments of tranquility. Check out this amazing DIY project, recreate a spa like feel with this bedroom refresh and shibori style diy , to create a serene sanctuary in your own home.
The calming atmosphere will help you unwind and find peace amidst the constant threat of data breaches and security risks.
The Elektra leak, exposing AWS cloud keys and fueling cryptomining operations, is a stark reminder of the importance of cybersecurity. But amidst the chaos, there’s a silver lining: the ability to create something beautiful from the digital world. If you’re looking for a creative outlet, check out these 3 easy ways to make your own art prints.
It’s a great way to express yourself and maybe even turn your art into a source of income, just like those exploiting the Elektra leak for their own gains.
The Elektra leak, exposing AWS cloud keys for cryptomining, serves as a stark reminder of the vulnerabilities we face in the digital world. It’s a reminder that even the most secure systems can be compromised, just like a poorly sewn seam can unravel a garment.
To strengthen our defenses, we need to learn the basics of security, just as we learn the fundamental stitches in sewing lessons basic stitches. Understanding the principles of secure coding and proper infrastructure management is crucial to preventing future breaches and ensuring the integrity of our digital lives.