Critical National Infrastructure Email Security: A Vital Defense
Critical national infrastructure email security is a critical concern in today’s interconnected world. From power grids to transportation systems, these vital networks are increasingly vulnerable to cyberattacks, and email has become a primary attack vector. Phishing scams, malware delivery, and data breaches pose significant threats to the stability and functionality of these essential services.
Understanding the vulnerabilities and implementing robust security measures is paramount to protecting critical infrastructure from cyber threats. This article will explore the importance of email security in safeguarding these vital systems, examining best practices, emerging trends, and the critical role of collaboration.
Emerging Trends and Future Challenges: Critical National Infrastructure Email Security
The cyber threat landscape is constantly evolving, and critical infrastructure is increasingly vulnerable to sophisticated attacks. As new technologies emerge and attackers become more innovative, it’s crucial to understand the evolving threats and adapt email security strategies accordingly.
Emerging Cyber Threats, Critical national infrastructure email security
The evolving threat landscape poses significant challenges to email security. These emerging threats require proactive measures to ensure the resilience of critical infrastructure.
- Advanced Persistent Threats (APTs):Highly sophisticated and targeted attacks often conducted by nation-states or well-funded criminal organizations. APTs employ advanced techniques to bypass traditional security measures, steal sensitive data, and disrupt operations.
- Ransomware:Malware that encrypts data and demands a ransom payment for its decryption. Ransomware attacks can cripple critical infrastructure, leading to significant financial losses and operational disruptions.
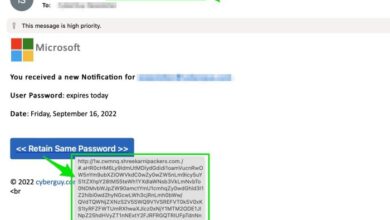
- Social Engineering:Techniques that exploit human psychology to gain access to sensitive information or systems. Phishing emails, spear phishing, and pretexting are common social engineering tactics used to compromise email accounts and steal credentials.
- Zero-Day Exploits:Exploits that target vulnerabilities in software before patches are available. These exploits can be highly effective, as they take advantage of unknown weaknesses in systems.
- IoT and OT Security:The increasing adoption of Internet of Things (IoT) devices and operational technology (OT) systems in critical infrastructure introduces new vulnerabilities. Attackers can target these devices to disrupt operations, steal data, or launch denial-of-service attacks.
Impact of New Technologies
New technologies, such as artificial intelligence (AI) and cloud computing, can significantly impact email security.
- AI-Powered Attacks:AI can be used to create more sophisticated phishing attacks, generate convincing spam emails, and automate the discovery and exploitation of vulnerabilities.
- Cloud Migration:Organizations are increasingly migrating to cloud-based email services, which presents new security challenges. Cloud-based email services require robust security measures to protect data and prevent unauthorized access.
- AI-Enhanced Security:AI can also be used to enhance email security by automating threat detection, analyzing email content for malicious activity, and adapting security measures in real-time.
Adapting Email Security Strategies
To meet future challenges, critical infrastructure organizations need to adapt their email security strategies.
- Proactive Threat Intelligence:Stay informed about emerging threats and vulnerabilities by monitoring threat intelligence feeds and industry reports.
- Multi-Layered Security:Implement a multi-layered approach to email security, including spam filtering, phishing detection, email authentication, and data loss prevention.
- Employee Training:Train employees on how to identify and avoid phishing emails, recognize social engineering tactics, and follow secure email practices.
- Incident Response Planning:Develop a comprehensive incident response plan that Artikels steps to be taken in case of a security breach.
- Regular Security Assessments:Conduct regular security assessments to identify vulnerabilities and ensure that security measures are effective.
- Collaboration and Information Sharing:Collaborate with industry partners and government agencies to share threat intelligence and best practices.
It’s amazing how crucial email security is for critical national infrastructure, especially when you consider the potential impact of a breach. Just like crafting a spooky easy yarn tassel ghost garland for Halloween, securing our digital systems requires careful attention to detail and a commitment to robust security measures.
After all, a single email phishing attack could have far-reaching consequences, disrupting essential services and potentially putting lives at risk.
Keeping critical national infrastructure safe from cyberattacks is a constant challenge, and securing email communication is a vital part of the defense. It’s amazing how much creativity can be channeled into projects like diy colorful geometric necklaces , but that same ingenuity can be used for malicious purposes.
That’s why staying vigilant about phishing scams and implementing strong email security measures is crucial for protecting our essential systems.
Keeping our critical national infrastructure safe from cyberattacks is a top priority, and securing email communication is a crucial part of that effort. It’s easy to feel overwhelmed by the constant stream of threats, but sometimes the simplest solutions are the most effective.
For example, did you know that you can use Siri to find your lost iPhone? Check out this handy trick: fed up of losing your iphone around your home this siri trick will blow your mind. Just like a misplaced phone, vulnerabilities in email security can lead to disastrous consequences, so it’s essential to implement robust security measures to protect our vital systems.