Microsoft News: Business Email Compromise Attacks & Phishing
Microsoft news business email compromise attacks phishing – Microsoft News: Business Email Compromise Attacks & Phishing – The digital landscape is a battlefield where cybercriminals are constantly evolving their tactics to exploit vulnerabilities. One of the most concerning threats is the business email compromise (BEC) attack, a sophisticated phishing scheme that targets businesses and individuals.
BEC attacks often involve impersonating legitimate entities, such as Microsoft, to trick victims into divulging sensitive information or transferring funds.
BEC attacks are becoming increasingly prevalent, causing significant financial losses and reputational damage for businesses. This article delves into the complexities of BEC attacks, highlighting how they exploit vulnerabilities in Microsoft products and services, and exploring the impact they have on users.
We’ll examine the tactics employed by attackers, discuss mitigation strategies, and explore the evolving landscape of BEC attacks in the digital age.
Microsoft’s Role in Business Email Compromise Attacks: Microsoft News Business Email Compromise Attacks Phishing
Business email compromise (BEC) attacks are a growing threat to businesses of all sizes. These attacks often target high-level executives and use social engineering techniques to trick them into transferring money or sensitive information to the attacker. Microsoft, as a major provider of email and productivity software, plays a significant role in both facilitating and mitigating these attacks.
Microsoft’s Efforts to Combat BEC Attacks
Microsoft has implemented various security features and partnered with other organizations to combat BEC attacks.
- Advanced Threat Protection (ATP):ATP is a suite of security features that helps protect against malware, phishing, and other threats. It includes features like email filtering, sandboxing, and real-time threat intelligence. ATP can help detect and block malicious emails that are designed to trick users into clicking on malicious links or opening attachments.
It’s a scary world out there, with Microsoft news constantly reporting on business email compromise attacks and phishing scams. Sometimes, I just need a creative outlet to de-stress. That’s when I turn to watercolor painting! Learning a few simple techniques can be so relaxing, like the ones outlined in this great article on 5 easy watercolor techniques.
After a few hours of painting, I feel refreshed and ready to tackle those phishing emails with renewed confidence!
- Security Awareness Training:Microsoft offers security awareness training programs that educate users about the dangers of BEC attacks and how to identify and avoid them. These programs can help users develop the skills they need to spot suspicious emails and avoid falling victim to these attacks.
It’s crazy how quickly these Microsoft news stories about business email compromise attacks and phishing scams pop up. I’m starting to feel like I need to build a fortress around my inbox! Maybe I should try those cool DIY diamond-shaped book shelves I saw online, and just stack my important documents in there instead.
I’m not sure if that’s the most practical solution, but it might give me some peace of mind. The truth is, we all need to be more vigilant when it comes to cybersecurity, and that includes being aware of the latest scams and phishing attempts.
- Partnerships with Law Enforcement:Microsoft collaborates with law enforcement agencies to combat cybercrime, including BEC attacks. These partnerships help Microsoft share threat intelligence and coordinate investigations to disrupt criminal activity.
- Industry Collaboration:Microsoft participates in industry groups and initiatives to address BEC attacks. These groups provide a platform for sharing best practices, coordinating responses, and developing new security technologies.
Vulnerabilities of Microsoft Products and Services to BEC Attacks
While Microsoft has implemented security measures, its products and services can still be vulnerable to BEC attacks.
- Spoofed Emails:Attackers can easily spoof emails from legitimate senders, making it difficult for users to distinguish between real and fake emails. This can be achieved by forging email headers or using domain names that closely resemble legitimate ones.
- Social Engineering:Attackers can use social engineering techniques to manipulate users into performing actions that compromise their security. For example, attackers might impersonate a trusted individual or use a sense of urgency to pressure users into making hasty decisions.
- Compromised Accounts:Attackers can compromise user accounts through phishing attacks or other methods. Once they have access to an account, they can send emails that appear to be legitimate but are actually malicious.
- Misconfigured Security Settings:Misconfigured security settings can make it easier for attackers to exploit vulnerabilities in Microsoft products and services. For example, if a user’s email account is not properly secured, an attacker could gain access to the account and send emails on their behalf.
Examples of BEC Attacks Targeting Microsoft Users
There have been numerous BEC attacks targeting Microsoft users, resulting in significant financial losses.
- In 2018, a BEC attack targeting a Microsoft customer resulted in the theft of $1.2 million.The attacker impersonated a high-level executive and sent an email requesting a wire transfer to a fraudulent account.
- In 2019, a BEC attack targeting a Microsoft partner resulted in the theft of $500,000.The attacker sent an email that appeared to be from a legitimate customer requesting a payment. The partner, believing the email to be authentic, transferred the money to the attacker’s account.
Phishing Tactics Used in BEC Attacks
Business Email Compromise (BEC) attacks are a growing threat, and phishing is a key tactic used by attackers to gain access to sensitive information and financial assets. Phishing attacks exploit social engineering and user trust to trick victims into divulging sensitive data or performing actions that benefit the attacker.
Phishing Email Examples
Phishing emails used in BEC attacks are often carefully crafted to appear legitimate and trustworthy. Attackers may impersonate executives, employees, or even external vendors to gain access to confidential information or convince victims to transfer funds. Here are some common examples of phishing emails used in BEC attacks targeting Microsoft users:
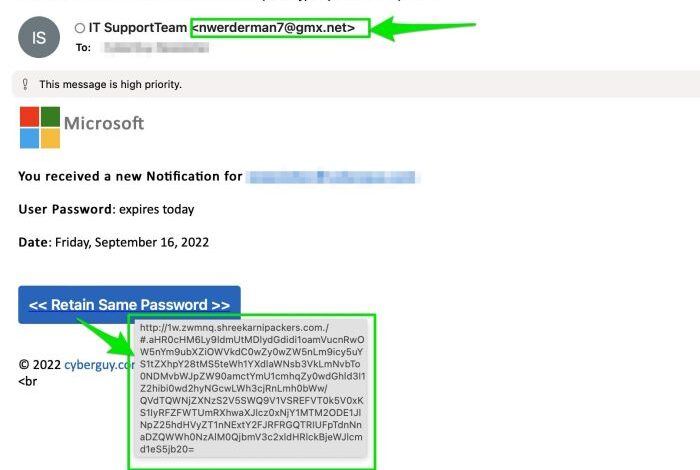
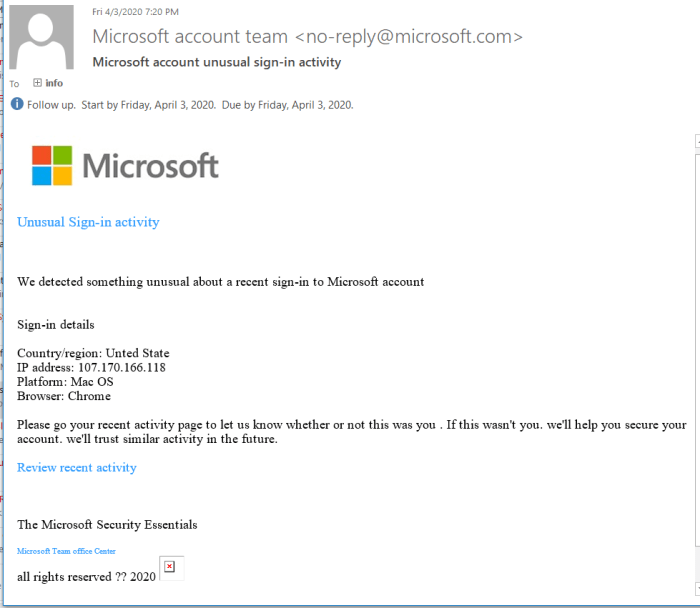
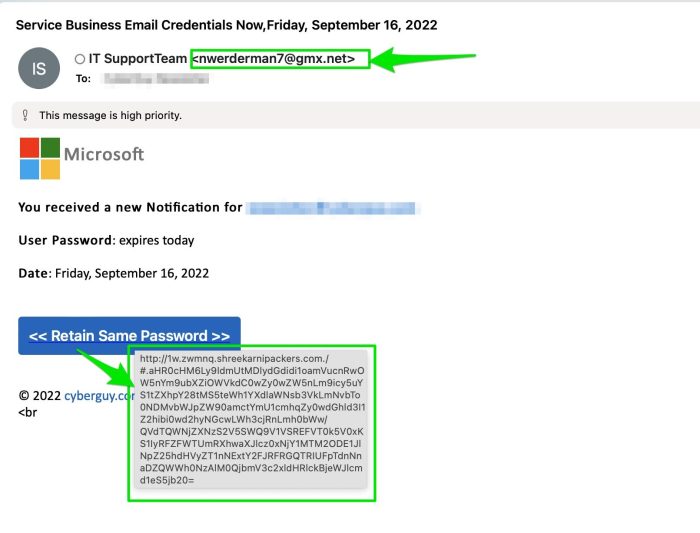
- Emails impersonating Microsoft Support:Attackers may send emails that appear to be from Microsoft Support, claiming that there is a security issue with the victim’s account or that they need to update their software. These emails may contain links to malicious websites or attachments that install malware on the victim’s computer.
- Emails requesting urgent payments:Attackers may send emails that appear to be from a trusted vendor or supplier, requesting an urgent payment. These emails may contain a fake invoice or a link to a malicious website where the victim is asked to enter their payment information.
- Emails containing malicious attachments:Attackers may send emails with attachments that appear to be legitimate documents, such as invoices, contracts, or expense reports. These attachments may actually contain malware that can steal sensitive information or take control of the victim’s computer.
Exploiting Social Engineering and User Trust
Phishing attacks often rely on social engineering to exploit user trust and manipulate them into taking actions that benefit the attacker. Attackers may use a variety of tactics to build trust, including:
- Creating a sense of urgency:Attackers may use phrases like “urgent,” “immediate action required,” or “time-sensitive” to pressure victims into taking action without thinking critically.
- Using authority:Attackers may impersonate high-ranking executives or other authority figures to make their requests seem more legitimate.
- Leveraging social connections:Attackers may target victims by sending emails that appear to be from a friend, colleague, or family member.
- Creating a sense of fear or guilt:Attackers may use threats or appeals to emotion to manipulate victims into taking action.
Impact of BEC Attacks on Microsoft Users
Business email compromise (BEC) attacks pose a significant threat to Microsoft users, inflicting both financial and reputational damage on individuals and organizations. These attacks exploit trust and manipulate communication channels, leading to substantial losses and eroding confidence in digital interactions.
It’s crazy how easily hackers can compromise business emails these days, especially with phishing attacks. I was reading about a recent case involving Microsoft, and it really made me think about the importance of cybersecurity. But on a lighter note, I’ve been wanting to make my own knit cat bed for my furry friend, and I found this great tutorial on how to make your own knit cat bed.
I guess it’s a good reminder that even though we’re constantly bombarded with news about cyberattacks, there’s still room for some creative DIY projects too!
Financial Losses
BEC attacks result in significant financial losses for victims. These attacks can lead to:
- Wire Transfers:Attackers often impersonate executives or other authorized individuals to convince employees to transfer funds to fraudulent accounts. For instance, in 2021, a BEC attack on a U.S. manufacturing company resulted in a loss of $10 million.
- Invoice Fraud:Attackers can manipulate invoices, requesting payment to fraudulent accounts or inflating the amount due. A study by the FBI revealed that BEC attacks resulted in over $2.3 billion in losses from 2016 to 2019.
- Account Takeovers:Attackers can gain access to sensitive accounts, including bank accounts, email accounts, and social media profiles, leading to financial losses and identity theft.
Reputational Damage
Beyond financial losses, BEC attacks can significantly damage a company’s reputation. These attacks can:
- Erode Trust:BEC attacks can erode trust in a company’s internal controls and its ability to protect sensitive information. This can damage relationships with customers, partners, and investors.
- Damage Brand Image:High-profile BEC attacks can negatively impact a company’s brand image, making it appear vulnerable and unreliable. This can lead to a decline in customer loyalty and sales.
- Legal Consequences:BEC attacks can result in legal liabilities, including lawsuits from victims and regulatory investigations. For example, a 2020 lawsuit against a major retailer alleged that the company’s lax security practices contributed to a BEC attack that resulted in millions of dollars in losses.
Mitigation Strategies for BEC Attacks
Business email compromise (BEC) attacks are a growing threat to organizations of all sizes. These attacks often target high-level executives and can result in significant financial losses. Fortunately, there are a number of steps that organizations can take to mitigate their risk of BEC attacks.
Best Practices for Mitigating BEC Attack Risks, Microsoft news business email compromise attacks phishing
Organizations should implement a comprehensive security strategy that includes the following best practices:
- Implement strong password policies:Encourage employees to use strong, unique passwords for all accounts, and require them to change their passwords regularly.
- Enable multi-factor authentication (MFA):MFA adds an extra layer of security by requiring users to provide two or more forms of identification before granting access to an account.
- Train employees on BEC attack tactics:Educate employees about the different types of BEC attacks and how to identify them. This training should include examples of phishing emails and other social engineering techniques.
- Implement email security solutions:Use email security solutions that can help to block phishing emails and other malicious content.
These solutions should include features such as spam filtering, malware detection, and email authentication.
- Review and verify wire transfer requests:Establish a process for verifying wire transfer requests, including contacting the intended recipient by phone to confirm the request.
- Use email filtering and spam detection tools:Implement email filtering and spam detection tools to help prevent malicious emails from reaching employees’ inboxes.
- Regularly review and update security policies:Regularly review and update security policies to ensure they are effective in protecting against BEC attacks.
Multi-Factor Authentication and Email Security Solutions
Multi-factor authentication (MFA) and email security solutions are two of the most important tools for preventing BEC attacks.
- Multi-Factor Authentication (MFA):MFA is a security measure that requires users to provide two or more forms of identification before granting access to an account. This can help to prevent unauthorized access to accounts, even if a hacker has obtained a user’s password.
- Email Security Solutions:Email security solutions can help to block phishing emails and other malicious content. These solutions should include features such as spam filtering, malware detection, and email authentication.
Security Measures to Combat BEC Attacks
Here is a table outlining some security measures that organizations can implement to combat BEC attacks:
| Security Measure | Description | Benefits |
|---|---|---|
| Multi-factor Authentication (MFA) | Requires users to provide two or more forms of identification before granting access to an account. | Reduces the risk of unauthorized access to accounts, even if a hacker has obtained a user’s password. |
| Email Security Solutions | Helps to block phishing emails and other malicious content. | Reduces the risk of employees falling victim to phishing attacks. |
| Employee Training | Educates employees about the different types of BEC attacks and how to identify them. | Increases employee awareness of BEC threats and helps them to avoid falling victim to attacks. |
| Security Policies | Defines the organization’s security procedures and guidelines. | Provides a framework for protecting the organization’s data and systems. |
| Incident Response Plan | Artikels the organization’s response to security incidents. | Helps to ensure that the organization can quickly and effectively respond to BEC attacks. |
User Education Resources
Organizations should provide employees with access to user education resources to raise awareness about BEC threats. These resources should include:
- Phishing simulation exercises:These exercises can help employees to learn how to identify phishing emails and other social engineering techniques.
- Security awareness training:This training should cover topics such as BEC attacks, phishing, malware, and social engineering.
- Online resources:There are a number of online resources that provide information about BEC attacks and other cybersecurity threats.
- Security newsletters:Organizations can send out security newsletters to keep employees informed about the latest security threats and best practices.
Future Trends in BEC Attacks
Business email compromise (BEC) attacks are constantly evolving, becoming more sophisticated and harder to detect. Attackers are leveraging new technologies and exploiting vulnerabilities in Microsoft’s products and services to target users. Understanding these emerging trends is crucial for businesses to stay ahead of the curve and protect themselves.
The Role of AI and Machine Learning in BEC Attacks
AI and machine learning are playing an increasingly important role in BEC attacks. Attackers are using these technologies to automate various aspects of their campaigns, making them more efficient and effective. For example:
- Automated phishing email generation:AI can be used to create highly convincing phishing emails that mimic legitimate communications. These emails can be tailored to specific individuals or organizations, making them even more difficult to spot.
- Targeted social engineering:AI can analyze vast amounts of data about individuals and organizations to identify potential vulnerabilities. This information can be used to craft highly personalized social engineering attacks that are more likely to succeed.
- Real-time attack optimization:AI can monitor the success of BEC attacks in real-time and adjust the attack strategy accordingly. This allows attackers to quickly identify and exploit vulnerabilities that emerge during the attack.







