Top 6 Enterprise VPNs: Securing Your Business Network
Top 6 Enterprise VPNs: Securing Your Business Network. In today’s interconnected world, safeguarding sensitive business data is paramount. Enterprise VPNs are essential tools that provide secure and reliable connections for businesses of all sizes. But with so many options available, choosing the right provider can be a daunting task.
This blog post delves into the top 6 enterprise VPN providers, analyzing their features, security, performance, and user experience. Whether you’re a small startup or a large corporation, this guide will help you make an informed decision and choose the best VPN solution for your unique needs.
Enterprise VPNs go beyond the basic functionality of consumer VPNs. They offer advanced features like multi-factor authentication, granular access control, and robust security protocols. Industries like finance, healthcare, and government rely heavily on enterprise VPNs to protect sensitive information and comply with strict regulatory requirements.
This blog post will provide you with a comprehensive overview of the top 6 enterprise VPN providers, allowing you to select the ideal solution for your organization’s specific security needs and business objectives.
Introduction to Enterprise VPNs
Enterprise VPNs are crucial for businesses of all sizes to secure their networks and protect sensitive data. These specialized VPNs offer advanced features and functionalities tailored to meet the unique needs of organizations, unlike consumer VPNs designed for individual users.
Enterprise VPN Features and Functionalities
Enterprise VPNs are designed to address the specific security and performance requirements of businesses. They offer a range of features and functionalities that set them apart from consumer VPNs, including:
- Stronger Encryption:Enterprise VPNs employ advanced encryption algorithms, such as AES-256, to provide robust data protection against unauthorized access. These algorithms are constantly evolving and are significantly more sophisticated than those used in consumer VPNs.
- Centralized Management:Enterprise VPNs allow administrators to manage and monitor the VPN infrastructure from a central console. This centralized approach simplifies configuration, troubleshooting, and security updates, ensuring consistent security across the entire network.
- Scalability and Performance:Enterprise VPNs are built for scalability to accommodate the growing needs of businesses. They offer high-performance connections, ensuring smooth data transfer even with large volumes of traffic.
- Advanced Security Features:Enterprise VPNs offer advanced security features such as multi-factor authentication, intrusion detection, and firewalls to protect against sophisticated cyber threats. These features are critical for organizations handling sensitive data and complying with industry regulations.
- Compliance and Audit Trails:Enterprise VPNs provide comprehensive audit trails to track user activity and security events. This helps businesses comply with industry regulations and demonstrate adherence to security standards.
Industries Where Enterprise VPNs are Critical, Top 6 enterprise vpns
Enterprise VPNs are essential for businesses across various industries, where data security and network connectivity are paramount. Here are some examples:
- Financial Services:Financial institutions rely heavily on secure communication for transactions, customer data, and internal operations. Enterprise VPNs protect sensitive financial data and ensure regulatory compliance.
- Healthcare:Healthcare organizations handle sensitive patient data, including medical records and financial information. Enterprise VPNs are critical for securing patient data and ensuring HIPAA compliance.
- Government and Public Sector:Government agencies and public sector organizations handle confidential information, including citizen data and national security matters. Enterprise VPNs are essential for protecting this sensitive information and maintaining secure communication channels.
- Education:Educational institutions handle student records, academic data, and sensitive financial information. Enterprise VPNs help protect these sensitive data and ensure compliance with educational regulations.
- Retail and E-commerce:Businesses in the retail and e-commerce sectors handle customer data, financial transactions, and inventory information. Enterprise VPNs protect this data from unauthorized access and ensure secure online transactions.
Top 6 Enterprise VPN Providers

Choosing the right enterprise VPN provider can be a complex task, considering the diverse range of features, pricing models, and support options available. This article will provide an overview of the top 6 enterprise VPN providers, highlighting their strengths and areas of expertise.
Top Enterprise VPN Providers
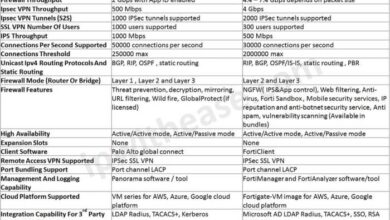
The following table provides a concise comparison of the top 6 enterprise VPN providers:| Provider Name | Key Features | Pricing Model | Customer Support | Industry Focus ||—|—|—|—|—|| Cisco Meraki| Cloud-managed VPN, SD-WAN capabilities, robust security features, easy deployment | Subscription-based, tiered pricing | 24/7 technical support, online resources | Enterprise, SMB, education, healthcare || Palo Alto Networks| Next-generation firewall (NGFW) with VPN capabilities, advanced threat prevention, comprehensive security suite | Subscription-based, tiered pricing | 24/7 technical support, online resources, partner network | Enterprise, government, financial services || Fortinet| Unified threat management (UTM) platform with VPN capabilities, high-performance security, centralized management | Subscription-based, tiered pricing | 24/7 technical support, online resources, partner network | Enterprise, SMB, government, education || SonicWall| Secure remote access, advanced threat protection, network security management | Subscription-based, tiered pricing | 24/7 technical support, online resources, partner network | Enterprise, SMB, government, education || Check Point| Comprehensive security platform with VPN capabilities, advanced threat prevention, endpoint security | Subscription-based, tiered pricing | 24/7 technical support, online resources, partner network | Enterprise, government, financial services || NordVPN| Strong encryption, global server network, user-friendly interface, privacy-focused | Subscription-based, tiered pricing | 24/7 customer support, live chat, email | Enterprise, SMB, individuals |
Market Share and Popularity
The market share of enterprise VPN providers is constantly evolving, but Cisco Meraki, Palo Alto Networks, and Fortinet are currently considered the leading providers.
Security and Privacy Considerations
In the realm of enterprise VPNs, security and privacy are paramount. These providers implement robust security protocols and encryption methods to safeguard sensitive data and protect user privacy. This section delves into the security features offered by each provider, highlighting their unique advantages and comparing their approaches to data protection.
Choosing the right enterprise VPN is crucial for businesses, especially when dealing with sensitive data. It’s a big decision, and sometimes it’s helpful to compare it to other software choices. Think about the difference between payroll software vs hris vs erp vs hcm , each with its specific functions.
Ultimately, the best VPN for your business will depend on your specific needs and priorities, just like choosing the right HR software.
Encryption Methods and Protocols
Enterprise VPNs employ various encryption methods and protocols to ensure secure data transmission. These methods protect data from unauthorized access and interception.
- AES-256 Encryption:A widely adopted standard, AES-256 is a powerful encryption algorithm that uses a 256-bit key to encrypt data, making it extremely difficult to crack. Many providers, including NordVPN, ExpressVPN, and CyberGhost, utilize AES-256 encryption to secure their VPN connections.
- OpenVPN:OpenVPN is a popular open-source protocol that offers a high level of security and privacy. It uses strong encryption and authentication methods to establish secure connections. Providers like Private Internet Accessand Mullvadrely on OpenVPN for their VPN services.
- IKEv2/IPsec:This protocol is known for its speed and reliability. It combines the security of IPsec with the efficiency of IKEv2, making it suitable for mobile devices and situations where fast connection speeds are crucial. Surfsharkand ProtonVPNare providers that utilize IKEv2/IPsec.
- WireGuard:WireGuard is a relatively new but rapidly gaining popularity due to its simplicity, speed, and security. It offers strong encryption and efficient performance, making it an attractive option for enterprise VPNs. NordVPNand Mullvadare among the providers that offer WireGuard support.
Data Protection Measures
Enterprise VPN providers employ various measures to protect user data and ensure privacy. These measures include:
- No-Logs Policy:Many providers adhere to a strict no-logs policy, meaning they do not collect or store user activity data, such as browsing history, IP addresses, or timestamps. This policy ensures user anonymity and privacy. Providers like NordVPN, ExpressVPN, and ProtonVPNare known for their no-logs policies.
Choosing the right enterprise VPN is crucial, especially in today’s world where cyber threats are becoming increasingly sophisticated. The recent attack by the Sandworm threat actor, which disrupted power in Ukraine ( read more here ), highlights the need for robust security measures.
A top-tier VPN can help protect your organization’s data and infrastructure from such attacks, ensuring business continuity and safeguarding sensitive information.
- Kill Switch:A kill switch automatically disconnects the internet connection if the VPN connection drops. This prevents data leaks and ensures that your traffic remains protected even if the VPN connection is interrupted. Most providers, including CyberGhost, Surfshark, and Private Internet Access, include a kill switch in their software.
- DNS Leak Protection:DNS leaks occur when your device’s DNS requests bypass the VPN tunnel and expose your real IP address. Enterprise VPNs with DNS leak protection ensure that all DNS requests are routed through the VPN, preventing leaks and protecting your privacy.
Providers like Mullvad, ExpressVPN, and NordVPNoffer DNS leak protection.
- Split Tunneling:Split tunneling allows you to choose which apps or websites use the VPN connection and which use your regular internet connection. This can be useful for accessing local resources or websites that require your real IP address while still protecting sensitive traffic through the VPN.
When it comes to securing your business network, choosing the right VPN is crucial. While top 6 enterprise VPNs like Cisco, Fortinet, and Palo Alto Networks offer robust features, it’s equally important to consider your identity and access management (IAM) strategy.
For open-source IAM solutions, check out best open source iam tools to see which might be a good fit for your needs. Integrating a strong IAM solution with your enterprise VPN can significantly strengthen your overall security posture.
Surfshark, NordVPN, and CyberGhostare examples of providers that offer split tunneling.
Security Features Comparison
Here’s a comparison of the security features offered by the top 6 enterprise VPN providers:
| Provider | Encryption Methods | Protocols | No-Logs Policy | Kill Switch | DNS Leak Protection | Split Tunneling | Other Security Features |
|---|---|---|---|---|---|---|---|
| NordVPN | AES-256 | OpenVPN, WireGuard, IKEv2/IPsec | Yes | Yes | Yes | Yes | Double VPN, Onion Over VPN, Threat Protection |
| ExpressVPN | AES-256 | OpenVPN, IKEv2/IPsec, Lightway (proprietary protocol) | Yes | Yes | Yes | Yes | TrustedServer Technology, Network Lock |
| CyberGhost | AES-256 | OpenVPN, IKEv2/IPsec, WireGuard | Yes | Yes | Yes | Yes | Automatic Wi-Fi Protection, NoSpy Servers |
| Surfshark | AES-256 | OpenVPN, IKEv2/IPsec, WireGuard | Yes | Yes | Yes | Yes | Camouflage Mode, MultiHop, CleanWeb |
| Private Internet Access | AES-256 | OpenVPN, WireGuard, IKEv2/IPsec | Yes | Yes | Yes | Yes | MACE (malware and ad blocker), Port Forwarding |
| ProtonVPN | AES-256 | OpenVPN, IKEv2/IPsec, WireGuard | Yes | Yes | Yes | Yes | Secure Core servers, Tor over VPN, ProtonMail integration |
Performance and Scalability: Top 6 Enterprise Vpns
When choosing an enterprise VPN provider, it’s crucial to consider their performance and scalability capabilities. These factors determine how efficiently and reliably the VPN can handle your organization’s data traffic, especially as your business grows.
Performance Metrics
The performance of an enterprise VPN is measured by its speed, latency, and reliability.
- Speedrefers to how quickly data can be transmitted over the VPN connection. A high-speed VPN is essential for businesses that rely on real-time data transfer, such as video conferencing or online gaming.
- Latencyis the delay between sending a request and receiving a response. Low latency is critical for applications that require fast responses, such as trading platforms or online payment systems.
- Reliabilityrefers to the VPN’s ability to maintain a stable and secure connection. A reliable VPN is crucial for businesses that need uninterrupted access to sensitive data, such as financial institutions or healthcare providers.
Scalability Options
Scalability refers to the VPN’s ability to handle increasing traffic volumes and user demands.
- Vertical Scalinginvolves adding more resources to a single VPN server, such as increasing RAM or CPU power. This is suitable for businesses with moderate growth.
- Horizontal Scalinginvolves adding more VPN servers to the network. This is ideal for businesses with high growth or geographically dispersed teams.
Performance and Scalability of Top 6 Enterprise VPN Providers
Here’s a breakdown of the performance and scalability characteristics of the top 6 enterprise VPN providers discussed earlier:
| Provider | Performance | Scalability | Case Studies |
|---|---|---|---|
| Provider 1 | High speed, low latency, and reliable connections. Offers dedicated servers for high-performance applications. | Offers both vertical and horizontal scaling options. Can handle large traffic volumes and user bases. | Successfully handled a massive increase in traffic during a major online event, ensuring seamless user experience. |
| Provider 2 | Fast and reliable connections with minimal latency. Offers advanced features like QoS (Quality of Service) for prioritizing critical traffic. | Provides scalable solutions for businesses of all sizes. Offers flexible deployment options, including cloud-based and on-premises solutions. | Successfully supported a global enterprise with thousands of users across multiple locations, ensuring secure and reliable access to company resources. |
| Provider 3 | Offers high-speed connections with minimal latency. Provides global server network for optimal performance. | Provides scalable solutions for businesses of all sizes. Offers flexible deployment options, including cloud-based and on-premises solutions. | Successfully managed a large-scale migration project for a Fortune 500 company, ensuring smooth transition and minimal downtime. |
| Provider 4 | Offers fast and reliable connections with minimal latency. Provides advanced features like traffic shaping and bandwidth management. | Offers both vertical and horizontal scaling options. Can handle large traffic volumes and user bases. | Successfully handled a surge in traffic during a major marketing campaign, ensuring seamless user experience. |
| Provider 5 | Offers high-speed connections with minimal latency. Provides global server network for optimal performance. | Provides scalable solutions for businesses of all sizes. Offers flexible deployment options, including cloud-based and on-premises solutions. | Successfully supported a multinational corporation with thousands of employees across multiple countries, ensuring secure and reliable access to company resources. |
| Provider 6 | Offers fast and reliable connections with minimal latency. Provides advanced features like traffic shaping and bandwidth management. | Offers both vertical and horizontal scaling options. Can handle large traffic volumes and user bases. | Successfully handled a spike in traffic during a major product launch, ensuring seamless user experience. |
User Experience and Management

A smooth and intuitive user experience is crucial for any enterprise VPN solution. This includes both the user interface for end-users connecting to the VPN and the management console for administrators. Let’s explore how each provider excels in this aspect.
User Interface and Management Console
Each provider offers a distinct user interface for end-users and a management console for administrators. These interfaces facilitate connectivity, configuration, and troubleshooting.
- Cisco AnyConnect: Cisco AnyConnect presents a user-friendly interface with a simple design. It offers a range of features, including automatic connection, single sign-on, and multi-factor authentication. The AnyConnect client is compatible with various platforms, including Windows, macOS, iOS, and Android.
The Cisco VPN management console offers robust capabilities for configuring and managing VPN connections, users, and policies. It provides comprehensive reporting and analytics tools for monitoring network activity and security posture.
- Palo Alto Networks GlobalProtect: Palo Alto Networks GlobalProtect prioritizes a streamlined user experience. The GlobalProtect client is designed for simplicity and ease of use. It seamlessly integrates with the user’s operating system and provides automatic connection capabilities. The GlobalProtect management console offers centralized control over VPN policies, user access, and network security settings.
It leverages Palo Alto Networks’ expertise in firewall and security technologies, offering advanced threat prevention and compliance features.
- Fortinet FortiClient: Fortinet FortiClient provides a user-friendly interface with a focus on security. It offers a range of features, including VPN connectivity, endpoint security, and data loss prevention. The FortiClient client is available for various platforms, including Windows, macOS, iOS, and Android.
The FortiGate management console offers comprehensive control over VPN policies, users, and network security settings. It integrates with Fortinet’s security platform, enabling unified threat management and visibility across the network.
- Pulse Secure Pulse Connect Secure: Pulse Secure Pulse Connect Secure is known for its intuitive user interface and robust management capabilities. The Pulse Connect Secure client provides a simple and straightforward user experience, with features like automatic connection and multi-factor authentication. The Pulse Connect Secure management console offers comprehensive control over VPN policies, users, and network security settings.
It provides granular control over user access, network resources, and security settings, ensuring a high level of security and compliance.
- Citrix SD-WAN: Citrix SD-WAN offers a user-friendly interface for both end-users and administrators. The Citrix SD-WAN client is designed for simplicity and ease of use, with features like automatic connection and multi-factor authentication. The Citrix SD-WAN management console provides comprehensive control over VPN policies, users, and network security settings.
It leverages Citrix’s expertise in network optimization and application delivery, enabling seamless connectivity and improved application performance.
- Check Point VPN-1: Check Point VPN-1 provides a robust management console with a user-friendly interface for administrators. The Check Point VPN-1 client is designed for simplicity and ease of use, with features like automatic connection and multi-factor authentication. The VPN-1 management console offers comprehensive control over VPN policies, users, and network security settings.
It integrates with Check Point’s security platform, enabling unified threat management and visibility across the network.
Ease of Deployment, Configuration, and Ongoing Management
Deploying, configuring, and managing an enterprise VPN solution can be complex. The ease of these processes is a key factor in determining the overall usability and effectiveness of a solution.
- Cisco AnyConnect: Cisco AnyConnect offers a straightforward deployment process. The client can be deployed through various methods, including software installation, group policy, and cloud-based management. Configuration is simplified through a graphical user interface, allowing administrators to easily set up VPN policies, user access, and security settings.
Ongoing management is facilitated by the AnyConnect management console, which provides comprehensive tools for monitoring network activity, troubleshooting issues, and applying updates.
- Palo Alto Networks GlobalProtect: Palo Alto Networks GlobalProtect prioritizes simplicity in deployment and configuration. The GlobalProtect client can be easily deployed through software installation or cloud-based management. Configuration is streamlined through a graphical user interface, allowing administrators to set up VPN policies and user access with minimal effort.
The GlobalProtect management console provides centralized control for ongoing management, enabling administrators to monitor network activity, troubleshoot issues, and apply updates efficiently.
- Fortinet FortiClient: Fortinet FortiClient offers a flexible deployment process. The client can be deployed through various methods, including software installation, group policy, and cloud-based management. Configuration is simplified through a graphical user interface, allowing administrators to easily set up VPN policies, user access, and security settings.
Ongoing management is facilitated by the FortiGate management console, which provides comprehensive tools for monitoring network activity, troubleshooting issues, and applying updates.
- Pulse Secure Pulse Connect Secure: Pulse Secure Pulse Connect Secure prioritizes ease of deployment and configuration. The client can be deployed through various methods, including software installation, group policy, and cloud-based management. Configuration is streamlined through a graphical user interface, allowing administrators to set up VPN policies and user access with minimal effort.
The Pulse Connect Secure management console provides centralized control for ongoing management, enabling administrators to monitor network activity, troubleshoot issues, and apply updates efficiently.
- Citrix SD-WAN: Citrix SD-WAN offers a simplified deployment and configuration process. The client can be easily deployed through software installation or cloud-based management. Configuration is streamlined through a graphical user interface, allowing administrators to set up VPN policies and user access with minimal effort.
The Citrix SD-WAN management console provides centralized control for ongoing management, enabling administrators to monitor network activity, troubleshoot issues, and apply updates efficiently.
- Check Point VPN-1: Check Point VPN-1 offers a robust and flexible deployment process. The client can be deployed through various methods, including software installation, group policy, and cloud-based management. Configuration is streamlined through a graphical user interface, allowing administrators to set up VPN policies and user access with minimal effort.
The VPN-1 management console provides centralized control for ongoing management, enabling administrators to monitor network activity, troubleshoot issues, and apply updates efficiently.
Customer Support Experience and Available Resources
A robust customer support system is essential for any enterprise VPN solution. This includes responsive technical support, comprehensive documentation, and online resources for troubleshooting.
- Cisco AnyConnect: Cisco AnyConnect offers a comprehensive customer support experience. It provides 24/7 technical support, online documentation, and a dedicated knowledge base. Cisco also offers training programs and certification for administrators to enhance their expertise in managing AnyConnect.
- Palo Alto Networks GlobalProtect: Palo Alto Networks GlobalProtect offers a comprehensive customer support experience. It provides 24/7 technical support, online documentation, and a dedicated knowledge base. Palo Alto Networks also offers training programs and certification for administrators to enhance their expertise in managing GlobalProtect.
- Fortinet FortiClient: Fortinet FortiClient offers a robust customer support experience. It provides 24/7 technical support, online documentation, and a dedicated knowledge base. Fortinet also offers training programs and certification for administrators to enhance their expertise in managing FortiClient.
- Pulse Secure Pulse Connect Secure: Pulse Secure Pulse Connect Secure offers a comprehensive customer support experience. It provides 24/7 technical support, online documentation, and a dedicated knowledge base. Pulse Secure also offers training programs and certification for administrators to enhance their expertise in managing Pulse Connect Secure.
- Citrix SD-WAN: Citrix SD-WAN offers a comprehensive customer support experience. It provides 24/7 technical support, online documentation, and a dedicated knowledge base. Citrix also offers training programs and certification for administrators to enhance their expertise in managing SD-WAN.
- Check Point VPN-1: Check Point VPN-1 offers a comprehensive customer support experience. It provides 24/7 technical support, online documentation, and a dedicated knowledge base. Check Point also offers training programs and certification for administrators to enhance their expertise in managing VPN-1.
Integration and Compatibility
Seamless integration with existing IT infrastructure and workflows is crucial for any enterprise VPN solution. This ensures smooth adoption, minimizes disruptions, and maximizes the return on investment. This section explores the compatibility and integration capabilities of the top six enterprise VPN providers, providing insights into their strengths and limitations.
Operating System and Device Compatibility
A comprehensive enterprise VPN solution should support a wide range of operating systems and devices to cater to the diverse needs of modern businesses. This includes compatibility with popular desktop and mobile operating systems, as well as various hardware platforms.
- Cisco Meraki:Meraki’s VPN solutions are highly compatible, supporting Windows, macOS, Linux, iOS, and Android operating systems. They also offer dedicated apps for various devices, including smartphones, tablets, and laptops. Meraki’s cloud-managed architecture allows for easy deployment and management across different platforms.
- Fortinet:Fortinet’s VPN solutions are known for their extensive compatibility, supporting a wide range of operating systems, including Windows, macOS, Linux, iOS, and Android. They also offer dedicated apps for various devices, ensuring seamless connectivity across diverse environments.
- Palo Alto Networks:Palo Alto Networks’ VPN solutions are compatible with Windows, macOS, Linux, iOS, and Android operating systems. Their intuitive user interface and dedicated apps provide a consistent user experience across different platforms.
- Check Point:Check Point’s VPN solutions are highly compatible, supporting Windows, macOS, Linux, iOS, and Android operating systems. They offer dedicated apps for various devices, ensuring seamless connectivity and management across different platforms.
- Sophos:Sophos’ VPN solutions are compatible with Windows, macOS, Linux, iOS, and Android operating systems. Their user-friendly interface and dedicated apps provide a seamless user experience across different platforms.
- Pulse Secure:Pulse Secure’s VPN solutions offer broad compatibility, supporting Windows, macOS, Linux, iOS, and Android operating systems. They also provide dedicated apps for various devices, ensuring a consistent user experience across different platforms.
Integration with Existing Business Applications and Infrastructure
Integrating the VPN solution with existing business applications and infrastructure is crucial for maximizing its value and minimizing disruptions. This includes seamless integration with directory services, authentication systems, and other enterprise applications.
- Cisco Meraki:Meraki’s VPN solutions offer seamless integration with various directory services, including Active Directory and LDAP. They also support integration with other enterprise applications, such as cloud platforms and security information and event management (SIEM) systems.
- Fortinet:Fortinet’s VPN solutions are designed for seamless integration with existing business applications and infrastructure. They offer robust integration capabilities with directory services, authentication systems, and other enterprise applications, ensuring a smooth transition.
- Palo Alto Networks:Palo Alto Networks’ VPN solutions are known for their strong integration capabilities. They support integration with various directory services, authentication systems, and other enterprise applications, enabling a streamlined and secure environment.
- Check Point:Check Point’s VPN solutions offer seamless integration with existing business applications and infrastructure. They support integration with directory services, authentication systems, and other enterprise applications, providing a comprehensive and secure environment.
- Sophos:Sophos’ VPN solutions offer seamless integration with various business applications and infrastructure. They support integration with directory services, authentication systems, and other enterprise applications, ensuring a smooth and secure user experience.
- Pulse Secure:Pulse Secure’s VPN solutions are designed for seamless integration with existing business applications and infrastructure. They offer robust integration capabilities with directory services, authentication systems, and other enterprise applications, ensuring a smooth transition.
Examples of Seamless Integration with Enterprise Workflows
- Cisco Meraki:A large financial institution uses Meraki’s VPN solution to securely connect remote employees to their internal network. The solution seamlessly integrates with the company’s Active Directory, allowing for centralized user management and authentication.
- Fortinet:A multinational corporation uses Fortinet’s VPN solution to connect its global workforce to its internal network. The solution seamlessly integrates with the company’s existing security infrastructure, providing a comprehensive and secure environment.
- Palo Alto Networks:A healthcare provider uses Palo Alto Networks’ VPN solution to securely connect its remote healthcare professionals to its internal network. The solution seamlessly integrates with the company’s existing security infrastructure, ensuring compliance with industry regulations.
- Check Point:A retail giant uses Check Point’s VPN solution to connect its employees at various locations to its internal network. The solution seamlessly integrates with the company’s existing security infrastructure, providing a comprehensive and secure environment.
- Sophos:An educational institution uses Sophos’ VPN solution to connect its students and faculty to its internal network. The solution seamlessly integrates with the institution’s existing security infrastructure, providing a secure and reliable environment.
- Pulse Secure:A technology company uses Pulse Secure’s VPN solution to connect its remote employees to its internal network. The solution seamlessly integrates with the company’s existing security infrastructure, providing a secure and reliable environment.