AI vs AI Phishing Wars: The New Cyber Battlefield
AI vs AI phishing wars: it sounds like something out of a sci-fi movie, right? But this isn’t fiction. It’s the reality of the modern cybersecurity landscape. Phishing attacks, once a simple tactic, have evolved into sophisticated, AI-powered campaigns that can fool even the most tech-savvy individuals.
This new era of cybercrime has sparked an arms race between AI attackers and AI defenders, each pushing the boundaries of what’s possible.
Imagine emails crafted to perfectly mimic your boss’s writing style, or websites designed to look exactly like your bank’s online portal. This is the reality of AI-powered phishing. The attackers use AI to analyze your behavior, learn your preferences, and tailor their attacks to your individual vulnerabilities.
They’re constantly evolving, finding new ways to bypass security measures and exploit human weaknesses.
The Rise of AI Phishing
Phishing attacks have evolved significantly, transitioning from simple, easily detectable attempts to highly sophisticated campaigns leveraging the power of artificial intelligence (AI). AI’s ability to analyze vast amounts of data, learn patterns, and adapt to new situations has made it a formidable tool for cybercriminals.
This has led to a new era of AI-powered phishing, posing a significant threat to individuals and organizations alike.
AI-Powered Phishing Techniques
AI has revolutionized the way phishing attacks are crafted and executed. AI algorithms can analyze massive datasets of emails, websites, and user behavior to identify patterns and vulnerabilities. This information is then used to create highly personalized and convincing phishing emails and websites that are more likely to deceive unsuspecting victims.
- Natural Language Processing (NLP):AI-powered NLP tools can generate realistic and grammatically correct phishing emails that mimic legitimate communication. They can analyze the writing style of specific organizations and create emails that appear to come from trusted sources.
- Machine Learning (ML):ML algorithms can be trained on large datasets of phishing emails to identify patterns and predict successful attack vectors. This enables cybercriminals to target specific individuals or organizations with tailored phishing campaigns.
- Deep Learning (DL):DL algorithms can analyze complex relationships within data, allowing them to create highly sophisticated phishing websites that closely resemble legitimate websites. They can even generate dynamic content that changes based on user interactions, further enhancing the illusion of authenticity.
Real-World AI Phishing Campaigns, Ai vs ai phishing wars
The use of AI in phishing attacks is not a theoretical concept; it is already a reality. Several high-profile AI-powered phishing campaigns have been documented, demonstrating the effectiveness of these techniques.
- The “CEO Fraud” Scam:This scam involves using AI-powered tools to impersonate company executives and send emails requesting large wire transfers. The emails are often crafted to appear legitimate, and the urgency of the request can pressure employees into acting quickly without proper verification.
This scam has resulted in millions of dollars in losses for businesses worldwide.
- AI-Powered Phishing Websites:Cybercriminals are increasingly using AI to create highly convincing phishing websites that mimic legitimate online services. These websites can be used to steal sensitive information, such as login credentials, credit card details, or personal data.
Impact of AI Phishing
The rise of AI-powered phishing attacks has significantly increased the threat landscape for individuals and organizations. These attacks are more sophisticated, targeted, and difficult to detect, making them more effective at deceiving victims. The impact of successful AI phishing attacks can be devastating, leading to:
- Financial losses:Victims can lose money through fraudulent transactions, account takeovers, or identity theft.
- Data breaches:Sensitive information, such as personal data, financial records, and intellectual property, can be compromised.
- Reputation damage:Organizations can suffer reputational damage if their customers or partners fall victim to AI phishing attacks.
- Increased cybersecurity costs:Organizations need to invest in more advanced security solutions to protect against AI-powered phishing attacks.
AI vs. AI
The emergence of AI phishing has ignited an arms race in the cybersecurity realm, pitting AI-powered security systems against AI-powered attackers. This battleground is characterized by constant innovation and adaptation, as both sides leverage the power of artificial intelligence to outmaneuver each other.
The AI vs AI phishing wars are getting increasingly sophisticated, with each side constantly evolving to outsmart the other. It’s fascinating to see how these battles play out in real-time, and you can find some incredible stories about the latest developments on botbeat top bot stories.
These stories offer valuable insights into the strategies employed by both sides, helping us understand the ever-changing landscape of online security.
AI-Powered Security Systems: Defensive Strategies
AI security systems employ a range of defensive strategies to combat AI phishing attacks. These strategies are designed to detect and prevent malicious activity, while minimizing false positives and ensuring the smooth operation of legitimate activities.
- Behavioral Analysis:AI systems can analyze user behavior patterns to identify anomalies that might indicate phishing attempts. This includes monitoring mouse movements, keystrokes, and website navigation patterns.
- Machine Learning Models:AI security systems use machine learning algorithms to learn from past phishing attacks and identify new patterns. These models can detect suspicious emails, websites, and other phishing tactics based on their similarity to known attacks.
- Natural Language Processing (NLP):NLP techniques are used to analyze the content of emails, websites, and other communications for signs of phishing. AI systems can identify subtle variations in language, grammar, and syntax that might indicate a phishing attempt.
- Sandboxing:Suspicious files and links are isolated in a sandbox environment to analyze their behavior without exposing the user’s system to potential harm. This allows AI systems to detect malicious code and prevent its execution.
Comparison of Techniques: Attackers vs. Defenders
AI phishing attackers and AI security systems utilize distinct techniques in their ongoing battle. While attackers focus on exploiting vulnerabilities and deceiving users, defenders aim to identify and neutralize threats.
| Technique | Attackers | Defenders |
|---|---|---|
| Email Spoofing | AI-powered tools can generate realistic email headers and sender names to mimic legitimate sources. | AI systems can analyze email headers, sender reputation, and content to identify spoofed emails. |
| Social Engineering | AI attackers can craft personalized phishing messages that exploit social engineering techniques, such as urgency or fear, to manipulate users into revealing sensitive information. | AI security systems can analyze the language, tone, and context of messages to identify social engineering tactics. |
| Website Cloning | AI can be used to create near-perfect replicas of legitimate websites to deceive users into entering their credentials. | AI systems can detect website cloning by analyzing the website’s code, domain registration, and SSL certificates. |
The Ongoing Battle: AI Attackers vs. AI Defenders
The cybersecurity landscape is a constant battleground, where AI attackers and AI defenders engage in a continuous arms race. As attackers develop new techniques, defenders must adapt and innovate to stay ahead.
“The future of cybersecurity will be defined by the ability of defenders to leverage AI to outmaneuver attackers. This requires a proactive approach, where security systems are constantly learning and evolving to counter emerging threats.”
[Expert Name, Security Research Firm]
The Impact of AI Phishing on Users
The rise of AI in phishing attacks poses a significant threat to users, as these attacks become increasingly sophisticated and difficult to detect. AI-powered phishing campaigns leverage advanced techniques to bypass traditional security measures and exploit human vulnerabilities, making them more effective and dangerous than ever before.
Vulnerabilities of Users
AI phishing attacks exploit various vulnerabilities of users, including:
- Lack of awareness:Many users are unaware of the evolving nature of phishing attacks and are not equipped to identify and avoid them. AI-powered phishing campaigns can easily mimic legitimate websites and communications, making them more convincing and harder to distinguish from genuine sources.
- Overconfidence:Users may be overconfident in their ability to recognize phishing attacks, leading them to fall prey to sophisticated AI-powered phishing tactics. The increasing sophistication of AI phishing attacks can easily trick even tech-savvy individuals.
- Social engineering:AI phishing attacks often employ social engineering techniques to manipulate users’ emotions and create a sense of urgency, making them more likely to click on malicious links or provide sensitive information. AI can analyze user data and tailor phishing messages to their specific interests and vulnerabilities.
Psychological Factors
AI phishing attacks leverage psychological factors to manipulate users’ behavior and increase their susceptibility to phishing tactics. Some of these factors include:
- Fear and urgency:AI-powered phishing attacks often create a sense of urgency and fear by claiming that the user’s account is compromised or that they need to take immediate action. This can lead users to act impulsively and make decisions without careful consideration.
It’s fascinating to watch the AI vs AI phishing wars unfold, like a digital arms race. One minute you’re seeing sophisticated techniques to bypass security, and the next you’re witnessing new defenses being erected. It reminds me of the intricate detail we achieve with our own creative projects, like the ones featured in our favorite stamped stenciled projects , where each layer of paint and stencil adds to the overall complexity and beauty.
In the end, it’s all about finding that perfect balance between artistry and security, both in the digital and physical world.
- Curiosity and trust:Users may be curious about the content of a phishing email or website, especially if it seems to be from a familiar source. This curiosity can lead them to click on malicious links or provide personal information without verifying the legitimacy of the source.
The AI vs AI phishing wars are a fascinating glimpse into the future of cybersecurity. It’s like a digital arms race, with each side constantly evolving to outsmart the other. Just as a giant snowflake light up marquee can be a beautiful and eye-catching display , these AI battles are a constant dance of deception and counter-deception, pushing the boundaries of what’s possible in the digital world.
- Social pressure:AI-powered phishing attacks can leverage social pressure by targeting users’ desire to be part of a group or community. This can lead users to share sensitive information or click on malicious links to avoid being excluded or to gain access to exclusive content.
Consequences of Successful AI Phishing Attacks
Successful AI phishing attacks can have severe consequences for individuals and organizations, including:
- Financial losses:Phishing attacks can result in financial losses due to stolen credit card information, bank account details, and other sensitive financial data. AI-powered phishing attacks can target individuals and organizations with specific financial vulnerabilities, leading to significant financial losses.
- Identity theft:Phishing attacks can lead to identity theft, where attackers steal personal information, such as Social Security numbers, driver’s licenses, and other sensitive data, to impersonate the victim and commit fraud.
- Data breaches:Phishing attacks can compromise sensitive data stored on personal devices or organizational networks. AI-powered phishing attacks can target specific organizations with valuable data, such as customer information, financial records, and proprietary research.
- Reputation damage:Successful phishing attacks can damage the reputation of individuals and organizations. This can lead to loss of trust, decreased customer loyalty, and negative publicity.
- Legal consequences:Victims of phishing attacks may face legal consequences, such as identity theft charges or fraud investigations. Organizations may also face legal action if they fail to protect sensitive data from phishing attacks.
Countermeasures and Mitigation Strategies: Ai Vs Ai Phishing Wars
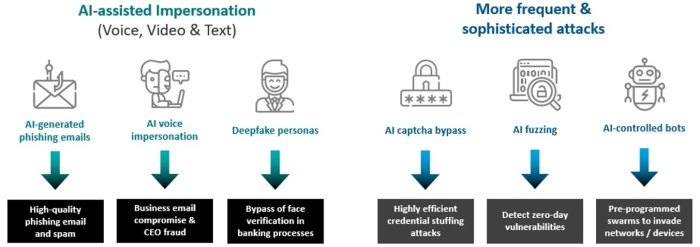
The emergence of AI-powered phishing attacks presents a significant challenge to cybersecurity. However, by implementing proactive measures and leveraging the power of AI itself, we can effectively combat this threat.
User Protection Best Practices
To protect themselves from AI phishing attacks, users should adopt a multi-layered approach that includes:
- Enhanced Phishing Awareness:Users must be educated about the evolving tactics of AI phishing, including the use of personalized content, sophisticated social engineering techniques, and realistic impersonations. This awareness can help them identify suspicious emails, messages, or websites.
- Strong Password Management:Implementing strong and unique passwords for all online accounts is crucial. Users should avoid using the same password across multiple platforms and consider using password managers to securely store and manage their credentials.
- Multi-Factor Authentication (MFA):Enabling MFA adds an extra layer of security by requiring users to provide additional verification factors, such as a code sent to their phone or email, beyond their password. This significantly reduces the risk of unauthorized access, even if a password is compromised.
- Careful Clicking and Hovering:Users should be cautious about clicking on links or attachments in emails or messages, especially if they seem suspicious or unexpected. Hovering over links before clicking can reveal the actual destination URL, helping to identify potential phishing attempts.
- Regular Software Updates:Keeping operating systems, browsers, and antivirus software up-to-date is essential to patch vulnerabilities that could be exploited by AI phishing attacks.
Organizational Mitigation Strategies
Organizations must implement a comprehensive strategy to mitigate the risk of AI phishing attacks. This strategy should include:
- AI-Powered Security Solutions:Implementing AI-driven security solutions can help detect and prevent AI phishing attacks. These solutions can analyze email traffic, identify suspicious patterns, and flag potentially malicious content.
- Employee Training and Awareness:Organizations should provide regular training to employees on AI phishing threats, best practices for identifying suspicious emails, and proper reporting procedures. This training should be tailored to specific roles and responsibilities within the organization.
- Phishing Simulation Exercises:Regularly conducting phishing simulation exercises can help assess employee awareness and identify vulnerabilities in the organization’s security posture. These exercises provide valuable feedback and allow for continuous improvement in security practices.
- Data Loss Prevention (DLP) Measures:Implementing DLP measures can help prevent sensitive data from being exfiltrated by AI phishing attacks. These measures can monitor data flow, identify suspicious activities, and block unauthorized data transfers.
- Security Incident Response Plan:Organizations should have a well-defined security incident response plan to handle AI phishing attacks effectively. This plan should Artikel procedures for identifying, containing, and mitigating the impact of such attacks.
The Role of AI in Countermeasures
AI plays a crucial role in developing effective countermeasures against AI phishing attacks. This includes:
- AI-Powered Phishing Detection:AI algorithms can analyze email content, sender behavior, and other factors to identify and flag suspicious emails with high accuracy.
- Real-Time Threat Intelligence:AI can gather and analyze real-time threat intelligence from various sources, including social media, dark web forums, and phishing campaigns. This intelligence can be used to proactively identify and block emerging phishing threats.
- Adaptive Security Measures:AI can adapt to the ever-changing tactics of AI phishing attacks by constantly learning and updating security models. This allows for proactive defense against new and evolving threats.
- Automated Response Systems:AI can automate response systems to quickly detect and neutralize AI phishing attacks. This includes automatically blocking suspicious emails, quarantining infected devices, and notifying relevant personnel.
The Future of AI Phishing Wars

The escalating arms race between AI-powered phishing attacks and defenses is poised to reshape the digital landscape in profound ways. As AI continues to evolve, the future of phishing wars promises a more sophisticated and dynamic environment, demanding innovative strategies to protect users and businesses.
The Trajectory of AI Phishing Attacks
The future of AI phishing attacks is characterized by increasing sophistication, personalization, and automation. Attackers will leverage advanced AI techniques to create highly convincing phishing emails, websites, and social media profiles, making it increasingly difficult for users to discern legitimate content from malicious ones.
AI-powered phishing campaigns will likely:
- Target specific individuals and organizations:AI algorithms can analyze vast amounts of data to identify vulnerable individuals and organizations, tailoring phishing attacks to their specific interests and vulnerabilities.
- Exploit emerging technologies:As new technologies like blockchain and metaverse platforms emerge, attackers will seek to exploit vulnerabilities within these ecosystems, creating new avenues for phishing attacks.
- Automate phishing campaigns:AI will enable attackers to automate phishing campaigns, scaling their operations and reaching a wider audience with greater efficiency.
The Ethical Implications of AI-Powered Phishing
The increasing reliance on AI in both phishing attacks and defenses raises significant ethical concerns. The potential for AI to be used for malicious purposes necessitates careful consideration of the ethical implications of its development and deployment.
- Privacy concerns:The use of AI to collect and analyze personal data for phishing purposes raises serious privacy concerns. Attackers could exploit personal information obtained through AI-powered phishing campaigns to target individuals with highly personalized attacks.
- Disinformation and manipulation:AI can be used to generate realistic deepfakes and other forms of synthetic media, which can be used to spread misinformation and manipulate public opinion. This raises concerns about the potential for AI-powered phishing to be used for political or social manipulation.
- Accessibility and accountability:The availability of AI tools for both attackers and defenders raises questions about accessibility and accountability. The potential for misuse by individuals with malicious intent necessitates the development of ethical frameworks and regulations to govern the use of AI in cybersecurity.
Collaboration and Innovation in the Fight Against AI Phishing
The evolving threat of AI phishing necessitates a collaborative and innovative approach to countermeasure development. Organizations, researchers, and governments must work together to develop effective strategies for combating AI-powered phishing attacks.
- Public-private partnerships:Collaboration between government agencies, research institutions, and private sector companies is crucial to share knowledge, develop best practices, and accelerate the development of AI-based countermeasures.
- Investment in research and development:Continued investment in research and development is essential to stay ahead of the curve in the AI phishing arms race. This includes developing new AI-based detection and prevention technologies, as well as improving user education and awareness.
- International cooperation:The global nature of AI phishing necessitates international cooperation to combat the threat. Sharing information and collaborating on cross-border investigations are essential to effectively address the challenge.