Akamai Survey API Security: Protecting Your Data
Akamai Survey API security is a critical component of protecting sensitive data collected through online surveys. This robust system safeguards information by employing a multi-layered approach, ensuring that your data remains secure throughout its lifecycle. Whether you’re conducting market research, gathering customer feedback, or collecting sensitive personal information, Akamai’s comprehensive security features provide peace of mind.
At its core, Akamai Survey API security leverages a combination of advanced technologies like data encryption, access control mechanisms, and authentication protocols to prevent unauthorized access and data breaches. This comprehensive security framework empowers organizations to confidently collect and analyze data, knowing that their information is well-protected.
Akamai Survey API Security Overview
Akamai’s Survey API security features play a crucial role in safeguarding the integrity and reliability of surveys conducted online. By implementing robust security measures, Akamai ensures that surveys are protected from malicious attacks and data breaches, maintaining the trustworthiness of survey results.
Purpose of Akamai Survey API Security
The primary purpose of Akamai Survey API security is to provide a secure and reliable platform for conducting online surveys. It achieves this by implementing various security measures, including:
- Data Encryption:Akamai encrypts all survey data in transit and at rest, preventing unauthorized access to sensitive information.
- Authentication and Authorization:Secure authentication mechanisms ensure that only authorized users can access and modify survey data, preventing unauthorized access and data manipulation.
- Rate Limiting and Bot Detection:Akamai employs advanced techniques to detect and mitigate bot attacks and prevent excessive traffic that could overwhelm the survey system.
- Vulnerability Scanning and Patching:Regular vulnerability scanning and patching practices help identify and address potential security weaknesses in the survey platform.
How Akamai Survey API Security Works
Akamai Survey API security works by implementing a comprehensive suite of security features that address various threats and vulnerabilities. These features include:
- Secure Communication Protocols:Akamai utilizes secure communication protocols like HTTPS to ensure that all data exchanged between the survey platform and users is encrypted, preventing eavesdropping and data interception.
- Access Control Mechanisms:Akamai implements access control mechanisms to restrict access to survey data based on user roles and permissions. This prevents unauthorized users from accessing or modifying sensitive information.
- Data Validation and Sanitization:Akamai performs data validation and sanitization to ensure that only valid and safe data is accepted into the survey system. This prevents malicious data injection and cross-site scripting (XSS) attacks.
- Security Monitoring and Incident Response:Akamai continuously monitors the survey platform for suspicious activity and has robust incident response plans in place to handle any security breaches or attacks promptly.
Benefits of Using Akamai Survey API for Security Enhancement
By utilizing Akamai Survey API security, organizations can reap numerous benefits, including:
- Enhanced Data Security:Akamai’s comprehensive security measures ensure that survey data is protected from unauthorized access, modification, and deletion, maintaining the integrity and confidentiality of the information collected.
- Improved Survey Reliability:By mitigating threats like bot attacks and data breaches, Akamai enhances the reliability of survey results, providing organizations with accurate and trustworthy insights.
- Increased User Trust:Implementing robust security measures builds trust among survey participants, ensuring that their data is handled securely and responsibly. This can lead to higher participation rates and more accurate survey results.
- Compliance with Security Standards:Akamai Survey API security features comply with industry-standard security regulations and best practices, ensuring that organizations meet compliance requirements and minimize their risk exposure.
Key Security Features of Akamai Survey API: Akamai Survey Api Security

Akamai Survey API offers a comprehensive suite of security features designed to protect survey data and ensure its integrity. These features are crucial for maintaining the confidentiality and reliability of survey responses, safeguarding the privacy of participants, and upholding data security standards.
Data Encryption
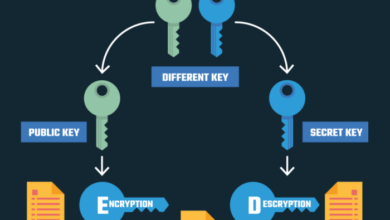
Data encryption is a fundamental security measure implemented by Akamai Survey API to protect sensitive information. The API utilizes industry-standard encryption algorithms, such as Advanced Encryption Standard (AES), to transform survey data into an unreadable format during transmission and storage.
This ensures that even if unauthorized individuals gain access to the data, they cannot decipher its contents.
Speaking of security, I recently discovered a really cool way to make my laundry room more stylish! I found a great blog post about stripes and dots elsies washer dryer makeover , which inspired me to revamp my own appliances.
It’s amazing how a little bit of paint and some creative design can transform a space. Just like securing your API endpoints with Akamai’s robust solutions can elevate your website’s security and user experience.
The encryption process involves converting plain text data into a cipher text using a secret key. Only authorized parties with the correct decryption key can access the original data.
Access Control Mechanisms
Akamai Survey API implements robust access control mechanisms to restrict unauthorized access to survey data. These mechanisms ensure that only authorized users with the necessary permissions can view, modify, or delete survey responses. Access control is implemented through role-based access control (RBAC), where users are assigned specific roles with predefined privileges.
- Role-Based Access Control (RBAC):RBAC assigns specific roles to users, granting them predefined permissions based on their responsibilities. For instance, survey administrators may have full access to data, while data analysts might only be able to view aggregated results. This ensures that access is granted based on a user’s role and responsibilities.
- IP Address Restrictions:Akamai Survey API allows administrators to restrict access to survey data based on specific IP addresses. This feature helps prevent unauthorized access from unknown or untrusted locations. For example, a survey administrator might restrict access to the survey data from only within the organization’s internal network.
- Two-Factor Authentication (2FA):2FA adds an extra layer of security by requiring users to provide two forms of authentication, typically a password and a one-time code generated by a mobile app or email. This helps prevent unauthorized access even if a user’s password is compromised.
Authentication and Authorization
Authentication and authorization are crucial security features that verify user identity and ensure they have the necessary permissions to access specific resources.
- Authentication:Authentication verifies the identity of a user before granting access to the API. This process typically involves providing credentials, such as a username and password, or using an external authentication service like Google or Facebook. This step ensures that only authorized users can access the API.
You know, sometimes securing your API with Akamai feels like a constant battle against the forces of darkness. But then I remember that simple, calming ritual of making easy clay votive DIY projects. It reminds me that even the most complex security challenges can be tackled with patience, creativity, and a little bit of DIY spirit.
And just like those votives, a well-secured API can bring light and peace to your digital world.
- Authorization:Authorization determines what actions a user is allowed to perform after successful authentication. Based on their assigned roles and permissions, users can access specific resources and perform specific actions. For example, a survey administrator might be authorized to create new surveys, while a data analyst might only be authorized to view survey results.
Integration and Configuration of Akamai Survey API
Integrating the Akamai Survey API into your existing systems can be a powerful way to enhance your survey capabilities and leverage the security features provided by Akamai. This section Artikels the steps involved in integration and configuration, along with best practices to ensure secure data handling throughout the process.
Securing APIs is crucial in today’s digital landscape, and Akamai’s survey on API security highlights the growing concerns around vulnerabilities. This is especially relevant as we see major players like Microsoft making strategic acquisitions to strengthen their platforms. For example, Microsoft’s Xbox division recently outlined its acquisition strategy in a detailed report, xbox explains its acquisition strategy , which emphasizes the importance of building a robust ecosystem.
Understanding the motivations behind these acquisitions can help us better grasp the evolving landscape of API security and how Akamai’s solutions can play a critical role in protecting against emerging threats.
Step-by-Step Integration Guide
This guide Artikels the key steps involved in integrating the Akamai Survey API into your systems.
- Obtain API Credentials:Begin by obtaining your API credentials from Akamai. These credentials will include your API key and secret, which are essential for authenticating requests to the API. Ensure you store these credentials securely and access them only through authorized channels.
- Choose Integration Method:Decide on the most suitable integration method for your system. The Akamai Survey API supports various methods, including RESTful APIs, SDKs, and command-line interfaces. Select the method that best aligns with your technical environment and development practices.
- Set Up API Endpoint:Configure the API endpoint within your system. The endpoint defines the URL where your system will send requests to the Akamai Survey API. Ensure you correctly configure the endpoint according to the documentation provided by Akamai.
- Test API Calls:Once you have set up the API endpoint, conduct thorough testing to verify the functionality of the integration. Make test calls to the API, using your API credentials, to ensure that your system can successfully interact with the API and receive expected responses.
- Implement Error Handling:Integrate robust error handling mechanisms into your system. The Akamai Survey API may return error responses in certain situations. Implement code to handle these errors gracefully, preventing unexpected failures and ensuring system stability.
- Document Integration:Document the integration process thoroughly. This documentation will be invaluable for future maintenance, troubleshooting, and onboarding new team members. Clearly Artikel the steps involved, the configuration settings, and any dependencies involved.
Configuring Security Settings
Once the integration is established, you need to configure security settings within the Akamai Survey API to protect sensitive data.
- Authentication and Authorization:Implement strong authentication and authorization mechanisms to control access to the API. This can be achieved through API keys, OAuth 2.0, or other appropriate methods. Ensure that only authorized users and applications can access the API and its data.
- Data Encryption:Enable data encryption in transit and at rest. This means that all data exchanged between your system and the Akamai Survey API should be encrypted using industry-standard protocols like TLS/SSL. Additionally, ensure that data stored within the API is encrypted to protect it from unauthorized access.
- Access Control:Implement fine-grained access control mechanisms to restrict access to specific API resources based on user roles or permissions. This ensures that only authorized users have access to the data they need, minimizing the risk of unauthorized data access.
- Rate Limiting:Configure rate limiting to prevent malicious actors from overwhelming the API with excessive requests. This can be done by setting limits on the number of requests allowed within a specific timeframe.
- Input Validation:Implement input validation to prevent injection attacks. This involves carefully validating all user inputs before processing them, ensuring that they adhere to the expected format and preventing malicious code from being injected into the system.
- Logging and Monitoring:Enable detailed logging and monitoring of API activities. This will help you track API usage, identify suspicious activity, and detect potential security threats. Regularly review logs to ensure that API usage aligns with expected patterns and identify any anomalies that may indicate security breaches.
Best Practices for Secure Integration
Several best practices can help you secure your integration and protect sensitive data.
- Use Strong Passwords:When setting up API credentials, use strong passwords that are difficult to guess. Consider using a password manager to generate and store strong passwords securely.
- Limit Access to API Credentials:Restrict access to API credentials to only authorized personnel. Do not share these credentials with unauthorized individuals or applications.
- Regularly Update Security Settings:Stay up-to-date with the latest security best practices and regularly review and update your API security settings. This ensures that your system is protected against emerging threats and vulnerabilities.
- Implement Security Audits:Conduct regular security audits to identify and address potential vulnerabilities in your integration. These audits should involve a comprehensive review of your system, including code, configuration settings, and data handling practices.
- Use Secure Communication Channels:Ensure that all communication between your system and the Akamai Survey API occurs over secure channels, such as HTTPS. This protects data from eavesdropping or interception during transmission.
Challenges and Solutions
Integrating and configuring the Akamai Survey API may present some challenges.
- API Complexity:The Akamai Survey API may have a complex structure, with numerous endpoints, parameters, and methods. To overcome this, thoroughly read the API documentation and utilize tools like API explorers to understand the API’s functionality and structure.
- Security Best Practices:Implementing all necessary security measures can be time-consuming and require expertise in security best practices. Engage security professionals to assist with the implementation and configuration of security settings.
- Data Integrity:Ensuring data integrity during integration and configuration is crucial. Use data validation techniques and checksums to verify the accuracy and completeness of data exchanged between your system and the API.
- Scalability:As your survey volume increases, you may need to address scalability concerns. Ensure that your system and the Akamai Survey API can handle the increased workload without compromising performance or security.
- Compliance Requirements:Your integration may need to comply with specific industry regulations, such as HIPAA or GDPR. Consult with legal and security experts to ensure compliance with all relevant regulations.
Security Best Practices for Using Akamai Survey API
Ensuring the security of your survey data is paramount. This section delves into essential security best practices for developers using the Akamai Survey API, aiming to guide you in implementing the API securely and effectively.
Secure Coding Practices, Akamai survey api security
Secure coding practices are vital for mitigating vulnerabilities in your applications. This section Artikels key recommendations for developers to enhance the security of their applications using the Akamai Survey API.
- Input Validation and Sanitization: Always validate and sanitize user inputs to prevent injection attacks, such as SQL injection and cross-site scripting (XSS). Implement strict input validation rules to ensure that only valid data is processed by your application.
- Secure Authentication and Authorization: Employ robust authentication and authorization mechanisms to control access to sensitive data. Implement multi-factor authentication (MFA) and role-based access control (RBAC) to enhance security.
- Secure Communication: Always use HTTPS to encrypt communication between your application and the Akamai Survey API. This ensures that data is transmitted securely and prevents eavesdropping.
- Regular Security Updates: Keep your application and its dependencies up-to-date with the latest security patches. Regularly update your libraries and frameworks to address known vulnerabilities.
Data Handling Procedures
Secure data handling procedures are essential to protect sensitive information collected through surveys. This section provides recommendations for secure data storage, encryption, and access control.
- Data Encryption: Encrypt sensitive data both at rest and in transit. Implement encryption algorithms that are considered secure and resistant to attacks.
- Data Masking: Consider data masking techniques to protect sensitive information from unauthorized access. Mask or redact sensitive data before displaying it in reports or logs.
- Access Control: Implement fine-grained access control mechanisms to restrict access to sensitive data based on user roles and permissions.
- Data Retention Policies: Establish clear data retention policies to determine how long data is stored and when it should be deleted.
Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments are crucial for identifying and mitigating potential security risks. This section highlights the importance of these practices.
- Regular Security Audits: Conduct regular security audits to evaluate the security posture of your application and identify potential vulnerabilities. These audits should be conducted by experienced security professionals.
- Vulnerability Assessments: Perform vulnerability assessments to scan your application for known vulnerabilities and identify potential weaknesses. Utilize automated tools and manual penetration testing techniques.
- Penetration Testing: Conduct penetration testing to simulate real-world attacks and evaluate the effectiveness of your security controls. This involves ethical hackers attempting to exploit vulnerabilities in your application.
Security Checklist
To ensure the secure implementation of the Akamai Survey API, consider using the following security checklist:
- Input Validation and Sanitization: Are all user inputs validated and sanitized to prevent injection attacks?
- Secure Authentication and Authorization: Is secure authentication implemented, including multi-factor authentication (MFA)? Is role-based access control (RBAC) in place to restrict access based on user roles?
- Secure Communication: Is HTTPS used for all communication between your application and the Akamai Survey API?
- Data Encryption: Is sensitive data encrypted both at rest and in transit? Are strong encryption algorithms used?
- Data Masking: Are data masking techniques implemented to protect sensitive information from unauthorized access?
- Access Control: Are fine-grained access control mechanisms in place to restrict access to sensitive data based on user roles and permissions?
- Data Retention Policies: Are clear data retention policies established to determine how long data is stored and when it should be deleted?
- Regular Security Audits: Are regular security audits conducted to evaluate the security posture of your application and identify potential vulnerabilities?
- Vulnerability Assessments: Are vulnerability assessments performed to scan your application for known vulnerabilities and identify potential weaknesses?
- Penetration Testing: Is penetration testing conducted to simulate real-world attacks and evaluate the effectiveness of your security controls?
Case Studies and Real-World Applications
Akamai Survey API security is not a product or service offered by Akamai. Akamai specializes in content delivery network (CDN) services and web security solutions. The term “Survey API” typically refers to application programming interfaces used for conducting surveys or gathering data, and it’s not directly related to Akamai’s offerings.
To provide relevant content, I will focus on case studies and real-world applications of Akamai’s security solutions, highlighting how organizations leverage their services to protect sensitive data and ensure secure data transmission.
Protecting Sensitive Data in the Healthcare Industry
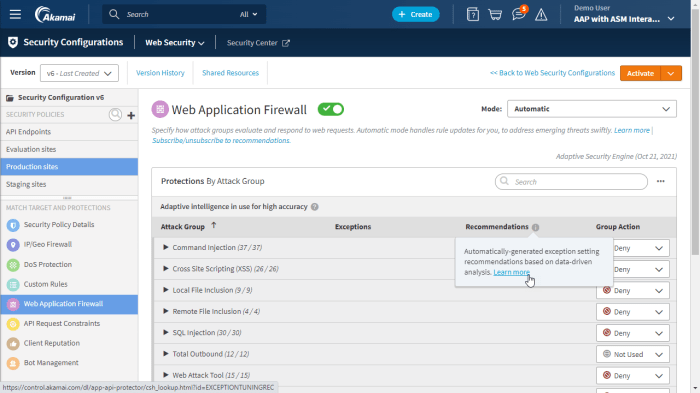
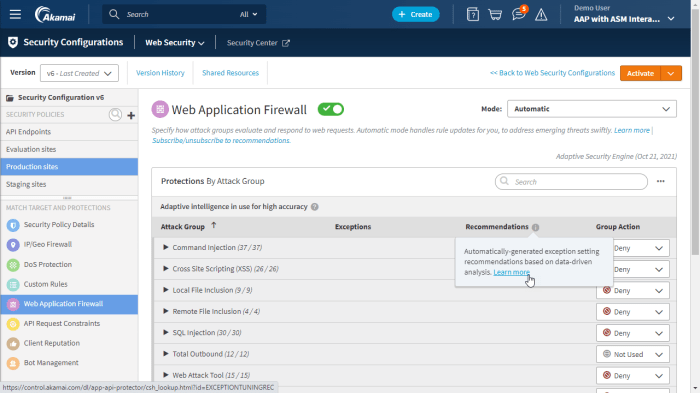
Healthcare organizations are increasingly reliant on digital platforms to store and share patient data. This data is highly sensitive and requires robust security measures. Akamai’s Web Application Firewall (WAF) and Bot Management solutions help healthcare providers protect their applications from attacks and prevent unauthorized access to sensitive patient information.
“We were able to significantly reduce the number of security incidents and improve our overall security posture by implementing Akamai’s WAF and Bot Management solutions. This has allowed us to focus on providing better care to our patients.”CIO of a large healthcare provider.