Complete Cyber Security Expert Certification Training Bundle: Your Path to a Secure Future
The Complete Cyber Security Expert Certification Training Bundle is more than just a collection of courses; it’s your passport to a world where safeguarding digital assets is paramount. Imagine yourself equipped with the knowledge and skills to navigate the complex landscape of cyber threats, becoming a trusted guardian of sensitive information.
This comprehensive bundle is your gateway to unlocking the potential of a rewarding career in cybersecurity, opening doors to exciting opportunities and a sense of accomplishment.
This bundle is designed to provide a comprehensive understanding of cybersecurity, covering key domains like network security, ethical hacking, incident response, and more. You’ll delve into the latest threats, vulnerabilities, and best practices, learning to identify and mitigate risks effectively.
The training is tailored to suit individuals at all levels, from beginners seeking a solid foundation to experienced professionals looking to enhance their expertise.
What is a Complete Cyber Security Expert Certification Training Bundle?

A complete cyber security expert certification training bundle is a comprehensive program designed to equip individuals with the knowledge, skills, and credentials needed to excel in the field of cybersecurity. These bundles typically cover a wide range of cybersecurity domains, providing a holistic understanding of the subject matter.
Components and Modules of a Complete Cyber Security Expert Certification Training Bundle
The content of a complete cyber security expert certification training bundle is structured to provide a comprehensive understanding of cybersecurity principles and practices. Here are some common components and modules:
- Fundamentals of Cybersecurity: This module introduces the core concepts of cybersecurity, including its history, importance, and key principles. It covers topics such as threat modeling, risk assessment, and security policies.
- Network Security: This module delves into the security of computer networks, covering topics such as firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs). It explores methods for securing network infrastructure and preventing unauthorized access.
- Operating System Security: This module focuses on securing operating systems, including Windows, Linux, and macOS. It covers topics such as user account management, file system permissions, and hardening techniques.
- Cryptography: This module explores the principles and practices of cryptography, including encryption algorithms, digital signatures, and hashing functions. It teaches how to secure data and communications using cryptographic methods.
- Web Security: This module covers the security of web applications, including topics such as cross-site scripting (XSS), SQL injection, and authentication vulnerabilities. It explores methods for developing secure web applications and mitigating web-based attacks.
- Cloud Security: This module focuses on the security of cloud computing environments, including topics such as cloud infrastructure security, data security in the cloud, and cloud security compliance.
- Incident Response and Forensics: This module covers the process of responding to security incidents, including incident identification, containment, eradication, and recovery. It also explores the techniques used in digital forensics to investigate security breaches.
- Ethical Hacking and Penetration Testing: This module teaches ethical hacking techniques and penetration testing methodologies. It provides hands-on experience in identifying and exploiting vulnerabilities in systems and networks.
- Cybersecurity Laws and Regulations: This module covers the legal and regulatory framework surrounding cybersecurity, including data protection laws, privacy regulations, and cybersecurity standards.
Target Audience and Skills Gained
Complete cyber security expert certification training bundles are designed for a diverse audience, including:
- Aspiring Cybersecurity Professionals: Individuals seeking to enter the cybersecurity field can gain the necessary skills and knowledge through these bundles.
- IT Professionals: IT professionals looking to expand their skillset and specialize in cybersecurity can benefit from these training programs.
- Business Professionals: Business professionals responsible for cybersecurity within their organizations can enhance their understanding of cybersecurity risks and mitigation strategies.
- Students: Students pursuing degrees in computer science, information technology, or related fields can gain practical knowledge and industry-recognized certifications.
These bundles provide participants with a comprehensive understanding of cybersecurity concepts, principles, and practices. Upon completion, individuals gain valuable skills such as:
- Threat Identification and Analysis: The ability to identify and assess potential cybersecurity threats.
- Vulnerability Assessment and Exploitation: The ability to identify and exploit vulnerabilities in systems and networks.
- Security Policy Development and Implementation: The ability to develop and implement effective security policies and procedures.
- Incident Response and Forensics: The ability to respond to security incidents and conduct digital forensics investigations.
- Ethical Hacking and Penetration Testing: The ability to perform ethical hacking and penetration testing to identify and mitigate security weaknesses.
- Cybersecurity Compliance and Governance: The ability to ensure compliance with relevant cybersecurity laws and regulations.
Benefits of Obtaining Cyber Security Certifications

Cybersecurity certifications are highly valued in the industry, offering numerous benefits to professionals seeking to advance their careers and enhance their skills. Obtaining these credentials demonstrates a commitment to professional development, validates knowledge and expertise, and opens doors to exciting opportunities.
Career Advancement and Earning Potential
Certifications play a significant role in career progression and salary expectations within the cybersecurity domain. Employers often prioritize candidates with relevant certifications, recognizing their value in mitigating risks and safeguarding sensitive information.
“According to a 2023 study by (Source), cybersecurity professionals with certifications earn an average of (Percentage) more than their uncertified counterparts.”
- Increased Job Opportunities:Certifications enhance your resume, making you a more attractive candidate for a wider range of cybersecurity roles. Many job postings specifically require or prefer certified professionals, expanding your career options.
- Higher Salary Potential:Certified cybersecurity professionals often command higher salaries than their uncertified peers.
The demand for skilled cybersecurity professionals is high, and certifications demonstrate your expertise, justifying a higher compensation package.
- Faster Career Advancement:Certifications can accelerate your career progression. By demonstrating your commitment to professional development, you can gain recognition within your organization and qualify for promotions or leadership roles.
Learning about cyber security is a serious business, but sometimes it’s good to take a break and get creative! I recently found myself making Instagram stickers at home , which was a fun way to de-stress after a long day of studying for my Complete Cyber Security Expert Certification Training Bundle.
It’s important to find balance between learning and leisure, and I’m finding that a little creativity goes a long way in keeping me motivated to keep learning about cybersecurity.
Enhanced Skills and Knowledge
Cybersecurity certifications provide a structured framework for acquiring and validating essential skills and knowledge. These programs cover a wide range of topics, from ethical hacking and penetration testing to risk management and incident response.
- Comprehensive Training:Certification programs offer comprehensive training materials, including online courses, workshops, and practical exercises, allowing you to develop a deep understanding of cybersecurity principles and best practices.
- Hands-on Experience:Many certifications include hands-on exercises and simulations, providing you with practical experience in applying your knowledge to real-world scenarios.
- Industry-Recognized Standards:Certifications are based on industry-recognized standards, ensuring that your knowledge and skills are aligned with current best practices and security frameworks.
Increased Credibility and Recognition
Certifications serve as a tangible proof of your cybersecurity expertise, enhancing your credibility and recognition within the industry. Employers, clients, and peers value certifications as a measure of your competence and commitment to the field.
- Industry-Wide Recognition:Certifications from reputable organizations like (List of organizations) are widely recognized and respected within the cybersecurity community.
- Enhanced Trust and Confidence:Certifications build trust and confidence among clients and stakeholders, demonstrating your ability to handle sensitive information and protect their assets.
- Networking Opportunities:Certification programs often provide networking opportunities with other cybersecurity professionals, expanding your professional connections and knowledge base.
Key Cybersecurity Domains Covered in Training Bundles
Cybersecurity training bundles encompass a wide range of domains, equipping professionals with the comprehensive knowledge and skills needed to address the ever-evolving threat landscape. These bundles are designed to cover the fundamental principles and advanced techniques required for effective cybersecurity practices.These domains are interconnected and often overlap, creating a holistic understanding of the cybersecurity ecosystem.
Earning a complete cyber security expert certification training bundle is a serious commitment, requiring dedicated study and practice. But even the most intense learning sessions can be brightened by a little creative flair. Why not design some custom mail stickers, like those you can find at make your own custom mail stickers , to add a personal touch to your study materials?
This small act of self-expression can make the journey to becoming a certified cyber security expert a little more enjoyable.
By mastering these domains, cybersecurity professionals can effectively protect organizations and individuals from various cyber threats.
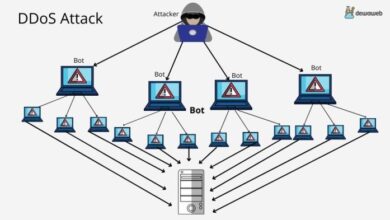
Network Security
Network security is a crucial domain that focuses on securing computer networks and the data they transmit. This domain involves implementing security measures to protect networks from unauthorized access, data breaches, and other cyberattacks.Key skills and knowledge in network security include:
- Understanding network protocols and architectures
- Implementing firewalls and intrusion detection/prevention systems (IDS/IPS)
- Configuring network segmentation and access control lists (ACLs)
- Performing network vulnerability assessments and penetration testing
- Managing network security incidents and responding to attacks
Security Operations
Security operations involve the day-to-day activities of monitoring, analyzing, and responding to security events and incidents. This domain focuses on ensuring the continuous protection of systems and data through proactive and reactive measures.Key skills and knowledge in security operations include:
- Understanding security monitoring tools and techniques
- Analyzing security logs and identifying suspicious activities
- Responding to security incidents and conducting investigations
- Implementing security incident response plans and procedures
- Maintaining security awareness and training programs
Cybersecurity Compliance
Cybersecurity compliance involves adhering to industry standards, regulations, and legal frameworks to ensure the protection of sensitive information. This domain ensures organizations meet specific security requirements and demonstrate compliance with relevant laws and regulations.Key skills and knowledge in cybersecurity compliance include:
- Understanding relevant cybersecurity laws and regulations (e.g., GDPR, HIPAA, PCI DSS)
- Conducting compliance audits and assessments
- Implementing and maintaining security policies and procedures
- Managing risk assessments and security controls
- Documenting compliance activities and evidence
Ethical Hacking and Penetration Testing
Ethical hacking and penetration testing involve simulating real-world cyberattacks to identify vulnerabilities and weaknesses in systems and applications. This domain provides a valuable perspective on how attackers might exploit security flaws and helps organizations strengthen their defenses.Key skills and knowledge in ethical hacking and penetration testing include:
- Understanding hacking methodologies and attack vectors
- Performing vulnerability scans and penetration tests
- Analyzing security risks and recommending remediation strategies
- Using ethical hacking tools and techniques
- Reporting vulnerabilities and findings to stakeholders
Cloud Security
Cloud security focuses on securing data and applications hosted in cloud environments. This domain addresses the unique challenges of cloud computing, including data privacy, access control, and infrastructure security.Key skills and knowledge in cloud security include:
- Understanding cloud computing models (e.g., IaaS, PaaS, SaaS)
- Implementing security controls in cloud environments
- Managing cloud security risks and vulnerabilities
- Securing cloud applications and data
- Using cloud security tools and services
Data Security
Data security is concerned with protecting sensitive information from unauthorized access, disclosure, modification, or destruction. This domain focuses on safeguarding data throughout its lifecycle, from creation to disposal.Key skills and knowledge in data security include:
- Understanding data security principles and best practices
- Implementing data encryption and access control mechanisms
- Managing data backups and recovery procedures
- Conducting data loss prevention (DLP) and data governance
- Responding to data breaches and incidents
Mobile Security
Mobile security focuses on protecting mobile devices, applications, and data from cyber threats. This domain addresses the unique vulnerabilities of mobile platforms and the increasing reliance on mobile devices for both personal and professional use.Key skills and knowledge in mobile security include:
- Understanding mobile operating systems and application security
- Implementing mobile device management (MDM) solutions
- Securing mobile applications and data
- Protecting mobile devices from malware and attacks
- Conducting mobile security assessments and penetration testing
Security Awareness and Training
Security awareness and training are essential for promoting a culture of cybersecurity within organizations. This domain focuses on educating employees and users about cybersecurity risks, best practices, and incident response procedures.Key skills and knowledge in security awareness and training include:
- Developing and delivering security awareness training programs
- Promoting a culture of security within the organization
- Raising awareness of phishing attacks and social engineering
- Educating users on secure password practices and data handling
- Encouraging reporting of suspicious activities and security incidents
Key Cybersecurity Domains, Importance, and Certifications
| Domain | Importance | Certifications | Explanation |
|---|---|---|---|
| Network Security | Protecting network infrastructure and data from unauthorized access and cyberattacks. | CompTIA Security+, Cisco CCNA Security, CISSP | Covers network protocols, firewalls, intrusion detection/prevention, and network security best practices. |
| Security Operations | Monitoring, analyzing, and responding to security events and incidents to ensure continuous protection. | GIAC Security Essentials Certification (GSEC), Certified Information Systems Security Professional (CISSP) | Focuses on security monitoring, incident response, log analysis, and security operations best practices. |
| Cybersecurity Compliance | Adhering to industry standards, regulations, and legal frameworks to ensure the protection of sensitive information. | Certified Information Systems Auditor (CISA), Certified Information Privacy Professional (CIPP), ISO 27001 Lead Implementer | Covers compliance audits, risk assessments, security policies, and data privacy regulations. |
| Ethical Hacking and Penetration Testing | Identifying vulnerabilities and weaknesses in systems and applications through simulated cyberattacks. | Certified Ethical Hacker (CEH), Offensive Security Certified Professional (OSCP), GIAC Penetration Tester (GPEN) | Focuses on hacking methodologies, vulnerability assessment, penetration testing, and reporting vulnerabilities. |
| Cloud Security | Securing data and applications hosted in cloud environments, addressing unique challenges of cloud computing. | AWS Certified Security
A complete cyber security expert certification training bundle can equip you with the knowledge and skills to secure your digital world, and it’s a valuable investment in your future. However, it’s also important to be mindful of financial management, especially if you’re taking on debt to finance the training. Learning about units for debt settlement can be helpful if you find yourself in a situation where you need to manage your debt responsibly. Ultimately, investing in your cyber security expertise can open doors to exciting career opportunities, but it’s crucial to make informed financial decisions along the way.
|
Covers cloud security principles, cloud infrastructure security, cloud application security, and cloud compliance. |
| Data Security | Protecting sensitive information from unauthorized access, disclosure, modification, or destruction throughout its lifecycle. | Certified Information Systems Security Professional (CISSP), Certified Information Privacy Professional (CIPP), Data Security and Privacy Professional (DSPP) | Covers data encryption, access control, data governance, data loss prevention, and data breach response. |
| Mobile Security | Protecting mobile devices, applications, and data from cyber threats, addressing unique vulnerabilities of mobile platforms. | Mobile Application Security Professional (MASP), Certified Information Systems Security Professional (CISSP), GIAC Mobile Device Security (GMOB) | Covers mobile operating systems, application security, mobile device management, and mobile security best practices. |
| Security Awareness and Training | Promoting a culture of cybersecurity within organizations through education and training programs. | Security Awareness Champion, Certified Information Systems Security Professional (CISSP), GIAC Security Awareness (GSAN) | Focuses on security awareness training, phishing awareness, social engineering prevention, and promoting a security culture. |
Choosing the Right Training Bundle
Navigating the vast landscape of cybersecurity training bundles can be daunting, especially for beginners. The key is to find a bundle that aligns with your specific needs and goals, ensuring a rewarding and effective learning experience.
Evaluating Your Needs and Goals
Before diving into the world of training bundles, it’s crucial to assess your current experience level, career aspirations, and budget constraints. This self-assessment will guide you towards the most appropriate training option.
- Experience Level:Are you a complete novice or have you already gained some experience in cybersecurity? This will determine the complexity and depth of the training you require. Beginners should opt for foundational courses that cover core cybersecurity concepts, while those with experience can delve into specialized areas like penetration testing or incident response.
- Career Aspirations:What are your career goals? Do you aim to become a security analyst, ethical hacker, or cybersecurity manager? Your aspirations will dictate the specific skills and certifications you need to pursue. For instance, a security analyst might prioritize certifications like CISSP or CISM, while an ethical hacker might focus on CEH or OSCP.
- Budget Constraints:Cybersecurity training bundles can range significantly in price, so it’s important to consider your budget. Some bundles offer affordable options, while others can be quite expensive. Explore various providers and compare their pricing structures to find a suitable fit.
Comparing Training Providers and Offerings
Once you’ve identified your needs and goals, it’s time to compare different training providers and their offerings. Consider factors like:
- Reputation and Accreditation:Look for providers with a strong reputation in the cybersecurity industry. Check if their training programs are accredited by reputable organizations like ISC 2or CompTIA, as this adds credibility and value to your certifications.
- Course Content and Structure:Review the curriculum of each bundle to ensure it covers the topics relevant to your career goals. Look for comprehensive training that includes practical exercises, simulations, and real-world case studies to enhance your learning experience.
- Instructor Expertise and Support:Experienced and knowledgeable instructors can make a significant difference in your learning journey. Look for providers with instructors who have real-world experience in cybersecurity and can provide guidance and support throughout your training.
- Learning Format and Flexibility:Choose a bundle that offers a learning format that suits your preferences and schedule. Options include online courses, self-paced learning, instructor-led training, and bootcamps. Consider factors like the availability of study materials, online forums, and support resources.
Additional Factors to Consider, Complete cyber security expert certification training bundle
- Certification Exams:Some training bundles include exam vouchers for specific certifications. This can save you money and time, as you won’t have to purchase separate exam vouchers.
- Career Support:Some providers offer career support services, such as job placement assistance, resume writing, and interview preparation. These services can be valuable in transitioning to a cybersecurity career.
- Community and Networking:Look for training bundles that provide opportunities for networking with other cybersecurity professionals. This can be beneficial for career advancement and professional development.
Preparing for and Passing Certification Exams: Complete Cyber Security Expert Certification Training Bundle

Passing a cybersecurity certification exam requires a dedicated and strategic approach. It’s not just about memorizing facts; it’s about demonstrating a deep understanding of cybersecurity principles and applying them to real-world scenarios.
Understanding Exam Objectives
Understanding the exam objectives is crucial for effective preparation. These objectives Artikel the specific knowledge, skills, and abilities that the exam assesses. By thoroughly reviewing the objectives, you can identify the key concepts and topics that will be covered on the exam.
Most certification bodies provide detailed exam Artikels that describe the specific areas of knowledge tested.
Developing a Study Plan
Once you understand the exam objectives, create a study plan that covers all the necessary topics. Allocate sufficient time for each subject area and prioritize topics that you find challenging. Break down your study plan into manageable chunks and set realistic goals for each study session.
Regular review and practice are essential to solidify your understanding.
Utilizing Study Materials
A variety of study materials are available to help you prepare for cybersecurity certification exams. These materials can include:
- Official Study Guides:These guides are often published by the certification body and provide comprehensive coverage of the exam syllabus.
- Practice Tests:Practice tests help you familiarize yourself with the exam format, question types, and difficulty level. They also identify areas where you need further study.
- Online Courses:Online courses provide structured learning and often include interactive exercises and quizzes.
- Cybersecurity Blogs and Websites:Stay updated on the latest trends and best practices by reading cybersecurity blogs and websites.
Exam-Taking Techniques
Effective exam-taking techniques can help you maximize your performance on the day of the exam.
- Time Management:Carefully manage your time during the exam. Allocate sufficient time for each section and avoid spending too much time on any single question.
- Answering Questions:Read each question carefully and eliminate any incorrect answers before choosing the best option. If you are unsure of an answer, make an educated guess and move on.
- Stress Management:Practice relaxation techniques to manage stress and anxiety during the exam. Take deep breaths and focus on your strengths.
Mastering Key Concepts
To pass a cybersecurity certification exam, you need to master key concepts and principles. These include:
- Network Security:Understanding network protocols, firewalls, intrusion detection systems, and VPNs.
- Operating System Security:Knowing how to secure operating systems, including user accounts, permissions, and updates.
- Cryptography:Understanding encryption algorithms, hashing functions, and digital signatures.
- Vulnerability Management:Identifying and mitigating vulnerabilities in systems and applications.
- Incident Response:Developing a plan for responding to security incidents and breaches.
Practice, Practice, Practice
The more you practice, the more confident you will become. Take advantage of practice tests, online simulations, and real-world scenarios to reinforce your knowledge and skills.