DDoS Attacks Dominate Verizon Report
DDoS Attacks Dominate Verizon Report, painting a stark picture of the ever-growing threat these attacks pose to businesses and organizations. Verizon’s recent report delves into the alarming prevalence and impact of DDoS attacks, highlighting the increasing sophistication of these cyber threats and the vulnerabilities they exploit.
The report provides a comprehensive overview of DDoS attacks, including their types, targets, and the devastating consequences they can have.
From financial losses and reputational damage to service disruptions and critical infrastructure vulnerabilities, the impact of DDoS attacks is far-reaching. The report sheds light on the latest trends in DDoS attacks, examining the motives behind these malicious acts and the strategies attackers employ to disrupt businesses and individuals.
With a focus on mitigation strategies, the report offers valuable insights and guidance for organizations to protect themselves against these evolving threats.
Verizon’s Report on DDoS Attacks
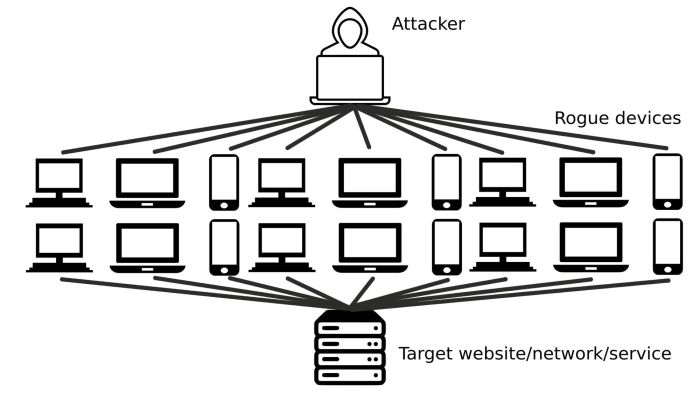
Verizon’s annual Data Breach Investigations Report (DBIR) provides valuable insights into the evolving landscape of cyber threats, including DDoS attacks. The report analyzes a vast dataset of real-world security incidents, offering a comprehensive understanding of the prevalence, impact, and trends of DDoS attacks.
Prevalence and Impact of DDoS Attacks
DDoS attacks remain a significant threat, with Verizon’s report highlighting their widespread prevalence and substantial impact. The report reveals that DDoS attacks are increasingly common, targeting various industries and organizations across the globe. The impact of these attacks can be severe, disrupting critical services, causing financial losses, and damaging reputations.
Types of DDoS Attacks
Verizon’s report identifies various types of DDoS attacks, each with unique characteristics and attack vectors.
- Volume-based attacks:These attacks overwhelm target systems with massive amounts of traffic, flooding them with requests that they cannot handle. Examples include UDP floods, SYN floods, and HTTP floods.
- Protocol attacks:These attacks exploit vulnerabilities in network protocols to disrupt communication and cause service outages. Examples include DNS amplification attacks, NTP reflection attacks, and SSDP amplification attacks.
- Application-layer attacks:These attacks target specific applications and services, exploiting vulnerabilities to disrupt their functionality. Examples include Slowloris attacks, HTTP flood attacks, and application-specific attacks like SQL injection.
Industries and Organizations Targeted by DDoS Attacks
Verizon’s report highlights that various industries and organizations are vulnerable to DDoS attacks.
It’s been a wild week in the cybersecurity world, with DDoS attacks dominating headlines, especially against Verizon. But hey, at least I’m finally making progress on my DIY project – painting the bookshelves! Check out this amazing progress report painted book shelves I found online for some inspiration.
Hopefully, I can get it done before the next wave of DDoS attacks hits!
- Financial institutions:Banks, credit card companies, and other financial institutions are prime targets for DDoS attacks due to the sensitive data they handle and the potential for financial losses.
- E-commerce companies:Online retailers are vulnerable to DDoS attacks, which can disrupt their websites and prevent customers from making purchases. Examples include Amazon, eBay, and Alibaba.
- Government agencies:Government agencies, especially those involved in national security or critical infrastructure, are frequent targets of DDoS attacks.
- Healthcare organizations:Hospitals, clinics, and other healthcare providers are increasingly targeted by DDoS attacks, which can disrupt patient care and compromise sensitive medical data.
Trends in DDoS Attacks: Ddos Attacks Dominate Verizon
DDoS attacks continue to evolve, becoming more sophisticated and challenging to defend against. Verizon’s 2023 Data Breach Investigations Report provides insights into the latest trends, highlighting the increasing use of advanced techniques and the diverse motives behind these attacks.
Increasing Sophistication of DDoS Attacks
The sophistication of DDoS attacks is increasing, driven by the availability of readily accessible tools and services. Attackers are utilizing new techniques and leveraging multiple attack vectors to overwhelm targets with traffic.
- Multi-vector attacks: Attackers combine multiple attack vectors, such as volumetric, application-layer, and protocol-based attacks, to maximize the impact on the target. This makes it harder for organizations to defend against the attacks, as they need to have multiple security solutions in place to mitigate the different types of attacks.
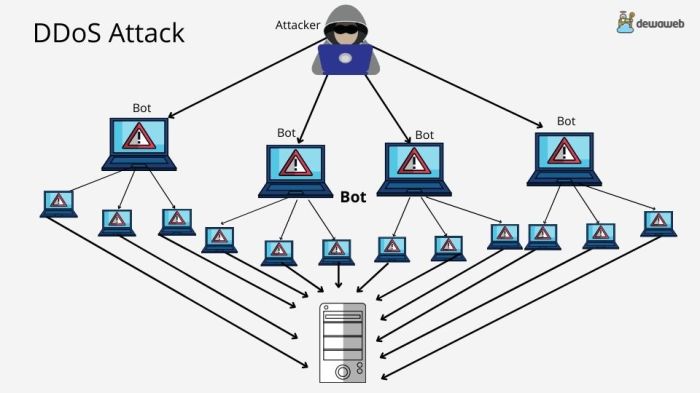
- Botnets: Attackers use botnets, networks of compromised computers, to launch DDoS attacks. Botnets can be easily rented or purchased on the dark web, making it easier for attackers to launch large-scale attacks.
- DDoS-as-a-Service (DDoSaaS): DDoSaaS platforms provide attackers with the tools and infrastructure needed to launch DDoS attacks without having to develop their own tools or manage their own botnets. These platforms make it easier for anyone to launch a DDoS attack, regardless of their technical expertise.
It’s crazy how Verizon is getting hit with so many DDoS attacks lately. Maybe I should take a break from worrying about network security and try a fun project like building an easy rope coaster diy. At least that way I can feel like I’m creating something instead of just reacting to cyber threats all the time.
I guess it’s important to find a balance, even when the world feels like it’s under constant attack.
- Zero-day exploits: Attackers are using zero-day exploits to bypass security measures and launch DDoS attacks. These exploits target vulnerabilities in software or hardware that are not yet known to security vendors, making it difficult for organizations to protect themselves.
Motives Behind DDoS Attacks
The motives behind DDoS attacks are diverse, ranging from financial gain to political activism. Attackers may target organizations for a variety of reasons, including:
- Extortion: Attackers may demand ransom payments from organizations to stop DDoS attacks. This is becoming increasingly common, as attackers can easily launch large-scale attacks using DDoSaaS platforms.
- Competitor sabotage: Attackers may launch DDoS attacks against competitors to disrupt their business operations and gain a competitive advantage.
- Political activism: Attackers may launch DDoS attacks to protest against government policies or corporate practices.
- Cyberwarfare: Nation-state actors may launch DDoS attacks to disrupt critical infrastructure or destabilize governments.
Impact of DDoS Attacks
DDoS attacks, while seemingly simple in concept, can have devastating consequences for organizations and individuals alike. The disruption of services, financial losses, and reputational damage caused by these attacks can be substantial, impacting businesses, critical infrastructure, and even everyday lives.
Financial Losses
DDoS attacks can result in significant financial losses for organizations.
The news about DDoS attacks dominating Verizon is certainly concerning, but it’s a good reminder that even in the face of digital threats, we can still find joy in the simple things. If you’re looking for a fun and easy way to celebrate Halloween, check out these 5 easy clean beauty Halloween looks for a spooky yet sustainable approach.
While we may be navigating a complex digital landscape, a little creativity and self-expression can go a long way in brightening our spirits. After all, a good scare can sometimes be the perfect antidote to the stress of a DDoS attack!
- Downtime Costs:Organizations lose revenue during periods of downtime, as customers are unable to access services or make purchases. The longer the attack lasts, the more substantial the financial impact.
- Repair and Recovery Costs:Recovering from a DDoS attack can be costly, requiring technical expertise to mitigate the attack, restore systems, and implement security measures to prevent future attacks.
- Reputation Damage Costs:Damaged reputation can lead to lost customers and reduced trust, impacting future revenue and business opportunities.
- Legal Costs:Organizations may face legal consequences for failing to protect their systems and data from DDoS attacks, particularly if sensitive information is compromised.
Reputational Damage
DDoS attacks can severely damage an organization’s reputation.
- Loss of Customer Trust:Frequent or prolonged outages caused by DDoS attacks can erode customer trust, leading to a decline in loyalty and customer satisfaction.
- Negative Media Coverage:DDoS attacks often attract negative media attention, further damaging an organization’s reputation and making it difficult to regain customer trust.
- Brand Value Decline:Damaged reputation can significantly reduce an organization’s brand value, impacting its ability to attract investors and partners.
Service Disruptions
DDoS attacks can disrupt essential services, impacting individuals and organizations alike.
- Business Operations:DDoS attacks can disrupt critical business processes, impacting productivity, efficiency, and revenue generation.
- Online Services:Websites, online banking platforms, and other online services can be rendered inaccessible, hindering individuals’ ability to access essential information and services.
- Critical Infrastructure:DDoS attacks on critical infrastructure, such as power grids, transportation systems, and communication networks, can have widespread and devastating consequences, potentially leading to power outages, transportation disruptions, and communication failures.
Impact on Critical Infrastructure
DDoS attacks pose a significant threat to critical infrastructure, potentially causing widespread disruption and damage.
- Vulnerabilities:Critical infrastructure systems are often interconnected and rely on vulnerable components, making them susceptible to DDoS attacks.
- Cascading Effects:A DDoS attack on one part of a critical infrastructure system can trigger cascading failures, impacting other interconnected systems and causing widespread disruption.
- Safety and Security Risks:Disruptions to critical infrastructure can compromise safety and security, potentially leading to accidents, injuries, and loss of life.
Real-World Examples, Ddos attacks dominate verizon
- Dyn DDoS Attack (2016):A massive DDoS attack targeting Dyn, a DNS service provider, disrupted access to numerous websites, including Twitter, Netflix, and Spotify, causing widespread service outages and impacting millions of users.
- Mirai Botnet Attacks (2016):The Mirai botnet, composed of compromised IoT devices, launched a series of DDoS attacks targeting various organizations, including the US-based Domain Name System provider Dyn, causing significant service disruptions.
- Code Red Worm (2001):The Code Red worm exploited a vulnerability in Microsoft’s IIS web server, launching a DDoS attack that overwhelmed numerous websites and servers, causing significant service disruptions and financial losses.
Mitigation Strategies
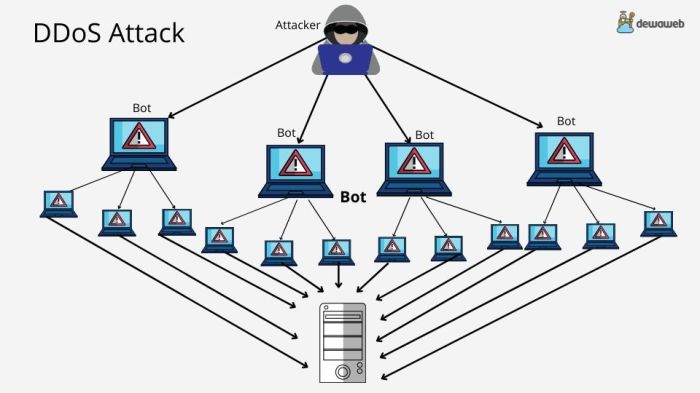
DDoS attacks can cripple businesses, leaving them vulnerable and unable to operate. Organizations must proactively implement comprehensive mitigation strategies to protect themselves from these devastating attacks. This guide provides a roadmap for designing and implementing effective DDoS mitigation strategies, encompassing preventive measures and response strategies.
Preventive Measures
Proactive security measures are essential to deter DDoS attacks and minimize their impact. Organizations must take a multi-layered approach to security, encompassing network, application, and infrastructure hardening.
- Network Segmentation:Divide the network into smaller segments, limiting the impact of a DDoS attack on critical systems. This approach isolates vulnerable services and reduces the attack surface.
- Firewall Configuration:Implement robust firewall rules to block malicious traffic and prevent unauthorized access to sensitive resources. Firewalls should be configured to detect and block suspicious traffic patterns.
- Intrusion Detection and Prevention Systems (IDPS):Deploy IDPS solutions to monitor network traffic for malicious activities and block potential attacks. These systems can detect and block various attack vectors, including DDoS attacks.
- Rate Limiting:Limit the number of requests per second (RPS) allowed from a single IP address or source. This technique prevents attackers from overwhelming servers with excessive requests.
- Access Control Lists (ACLs):Create ACLs to restrict access to sensitive resources based on IP address, port, or other criteria. ACLs can be used to block known malicious IP addresses or sources.
- Traffic Filtering:Filter out malicious traffic based on various criteria, such as IP address, protocol, or port. This helps to prevent DDoS attacks from reaching critical systems.
- Vulnerability Management:Regularly scan systems for vulnerabilities and patch them promptly. This reduces the risk of attackers exploiting vulnerabilities to launch DDoS attacks.
Response Strategies
Organizations must have a well-defined response plan to handle DDoS attacks effectively. This plan should include procedures for detecting, mitigating, and recovering from attacks.
- DDoS Mitigation Services:Leverage DDoS mitigation services provided by reputable service providers. These services can help organizations identify and block DDoS attacks, ensuring business continuity.
- Traffic Scrubbing:Employ traffic scrubbing techniques to filter out malicious traffic from legitimate traffic. This helps to reduce the volume of attack traffic reaching the target systems.
- Blackholing:Block malicious traffic at the network level, preventing it from reaching the target systems. This approach can be used to mitigate large-scale DDoS attacks.
- Load Balancing:Distribute traffic across multiple servers to prevent a single server from being overwhelmed. This approach can help to mitigate the impact of DDoS attacks on critical systems.
- Incident Response Plan:Develop a comprehensive incident response plan to handle DDoS attacks effectively. This plan should include procedures for identifying, mitigating, and recovering from attacks.
Role of Technology and Service Providers
Technology and service providers play a crucial role in protecting organizations from DDoS attacks. They offer a range of solutions and services that can help organizations mitigate the risks associated with DDoS attacks.
- DDoS Mitigation Services:Service providers offer DDoS mitigation services that use advanced technologies to detect and block DDoS attacks. These services can help organizations protect their critical systems from the devastating effects of DDoS attacks.
- Network Security Appliances:Technology providers offer network security appliances that can help organizations secure their networks from DDoS attacks. These appliances can perform traffic filtering, rate limiting, and other security functions.
- Cloud Security Services:Cloud service providers offer a range of security services, including DDoS mitigation services, that can help organizations protect their cloud-based applications and data.
Best Practices for Securing Networks and Systems
Organizations must implement best practices to secure their networks and systems against DDoS attacks. These practices include:
- Regular Security Audits:Conduct regular security audits to identify vulnerabilities and weaknesses in the network and systems. This helps to identify potential attack vectors and implement appropriate security measures.
- Employee Training:Train employees on security best practices and educate them about the risks of DDoS attacks. This helps to reduce the likelihood of employees falling victim to social engineering attacks or making mistakes that could expose the organization to DDoS attacks.
- Security Monitoring:Continuously monitor network traffic for suspicious activities and anomalies. This helps to detect DDoS attacks early and respond promptly.
- Collaboration with Security Experts:Collaborate with security experts to implement best practices and stay informed about emerging threats. This helps to ensure that the organization is using the latest security measures and technologies.
Future of DDoS Attacks
The landscape of DDoS attacks is constantly evolving, driven by the emergence of new technologies and the relentless ingenuity of attackers. Understanding the future of these attacks is crucial for organizations to effectively prepare and defend against them.
Impact of Emerging Technologies
The proliferation of connected devices and the rise of 5G and IoT will significantly impact DDoS attack trends. These technologies offer unprecedented connectivity and data transfer speeds, which can be exploited by attackers to launch more powerful and sophisticated attacks.
- 5G Networks:5G networks offer significantly higher bandwidth and lower latency compared to previous generations. This increased capacity can be leveraged by attackers to launch larger and more complex DDoS attacks, potentially overwhelming network infrastructure with a massive volume of traffic.
- Internet of Things (IoT):The growing number of IoT devices, such as smart home appliances, wearables, and industrial sensors, presents a new attack surface for DDoS attacks. These devices often lack robust security measures and can be easily compromised, turning them into a botnet that can be used to launch attacks.
Role of Artificial Intelligence and Machine Learning
AI and ML are playing a crucial role in both launching and mitigating DDoS attacks. Attackers are increasingly using these technologies to automate attack processes, making them more efficient and harder to detect. However, AI and ML can also be used to enhance DDoS defense mechanisms.
- Attack Detection and Mitigation:AI and ML algorithms can analyze network traffic patterns and identify malicious activity in real-time, allowing for quicker detection and mitigation of DDoS attacks. These systems can also learn from past attacks and adapt to new attack techniques, making them more effective over time.
- Botnet Identification:AI and ML can be used to identify and isolate compromised devices within a botnet, preventing them from being used to launch attacks. This can help to reduce the impact of DDoS attacks by limiting the number of malicious nodes participating in the attack.