HTTP/2 Rapid Reset DDoS Attack: A New Threat
Http2 rapid reset ddos attack – HTTP/2 Rapid Reset DDoS attacks are a new breed of cyber threat leveraging the efficiency of HTTP/2 to overwhelm servers with a barrage of reset requests. This attack exploits the rapid reset functionality of HTTP/2, a protocol designed to improve web performance, to create a denial-of-service condition.
By sending an overwhelming number of reset requests, attackers can effectively cripple web applications and disrupt their operations.
Understanding the mechanisms behind these attacks is crucial for any website or application owner. HTTP/2, with its ability to multiplex requests and utilize header compression, can amplify the impact of DDoS attacks. These attacks are particularly challenging to mitigate because they can mimic legitimate user behavior, making them difficult to distinguish from real traffic.
The rapid reset functionality, intended to optimize communication, becomes a vulnerability in the hands of attackers.
HTTP/2 and its Impact on DDoS Attacks: Http2 Rapid Reset Ddos Attack
The advent of HTTP/2, a major update to the HTTP protocol, has brought significant performance enhancements to web applications. However, its new features also present potential vulnerabilities that could be exploited by attackers to launch more effective DDoS attacks. Understanding the intricacies of HTTP/2 and its implications for DDoS attacks is crucial for security professionals and website owners.
HTTP/2’s Key Features and Differences from HTTP/1.1
HTTP/2 introduces several key features that differentiate it from its predecessor, HTTP/1.1. These features aim to improve the efficiency and speed of web communication.
- Multiple streams over a single connection:HTTP/2 allows multiple requests and responses to be sent over a single TCP connection, eliminating the overhead associated with establishing and maintaining multiple connections. This significantly reduces latency and improves performance.
- Header compression:HTTP/2 employs HPACK (HTTP/2 Header Compression) to compress HTTP headers, reducing the amount of data transmitted over the network. This compression technique further enhances performance and reduces bandwidth consumption.
- Server push:HTTP/2 enables servers to proactively push resources to clients, anticipating their needs. This can reduce the number of round trips required for a client to load a web page, improving perceived performance.
- Prioritization of requests:HTTP/2 allows clients to prioritize requests, enabling the server to deliver the most important resources first. This prioritization feature optimizes resource loading and improves the user experience.
Potential Enhancements to DDoS Attacks
HTTP/2’s features, while designed to enhance performance, can also be leveraged by attackers to launch more effective DDoS attacks.
- Increased attack amplification:The ability to send multiple requests over a single connection allows attackers to amplify the impact of a DDoS attack. By sending a large number of requests through a single connection, attackers can overwhelm the target server with a significantly higher volume of traffic.
- Exploiting header compression:HTTP/2’s header compression can be exploited to create a larger number of requests within a smaller data packet. Attackers can compress a large number of malicious requests into a small packet, increasing the rate at which requests can be sent.
- Leveraging server push:Attackers can potentially exploit server push to send malicious content to clients, bypassing security measures that rely on request-response models.
Examples of HTTP/2 Features Exploited in DDoS Attacks
- HTTP/2 Flood Attack:Attackers can leverage the multiplexing capabilities of HTTP/2 to send a massive number of requests over a single TCP connection, overwhelming the target server with a flood of traffic. This can lead to service disruptions and denial of service.
- HTTP/2 Push-Based Attack:Attackers can use server push to inject malicious content into the client’s browser, bypassing traditional security mechanisms. For instance, they could push malicious scripts or advertisements that compromise the user’s system.
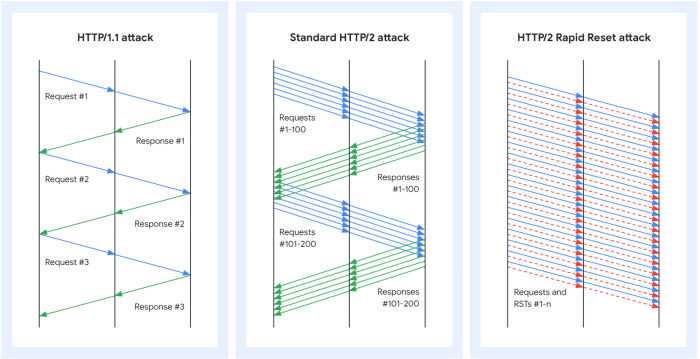
The Rapid Reset DDoS Attack
The Rapid Reset DDoS attack is a sophisticated attack vector that leverages the HTTP/2 protocol’s rapid reset functionality to overwhelm a server’s resources and cause service disruptions. It exploits the ability of HTTP/2 to quickly terminate connections, flooding the server with reset requests and effectively denying legitimate users access to the website or service.
The Rapid Reset DDoS Attack’s Working Mechanism
The Rapid Reset DDoS attack works by exploiting the HTTP/2 protocol’s rapid reset functionality. This functionality allows a client to quickly terminate an HTTP/2 connection without waiting for the server to finish processing the request. Attackers leverage this feature by sending a barrage of reset requests to the server, overwhelming its resources and causing it to drop legitimate connections.
The HTTP/2 Rapid Reset DDoS attack is a serious threat to web servers, exploiting a vulnerability in the protocol to overwhelm the target with a flood of requests. While cybersecurity is a critical concern for all businesses, it’s interesting to see how even tech giants like Apple approach their product development.
Tim Cook recently blindly ranked his top five Apple products of all time , revealing some surprising choices and highlighting the evolution of their product line. Understanding the vulnerabilities of modern technology, like the HTTP/2 Rapid Reset DDoS attack, is crucial for both developers and users to ensure a safe and secure digital landscape.
- The attack starts with the attacker sending a series of HTTP/2 requests to the target server. These requests are often malformed or incomplete, forcing the server to expend resources processing them.
- Once the server begins processing these requests, the attacker sends a series of reset requests, instructing the server to terminate the connections immediately. These reset requests are sent at a very high rate, overwhelming the server’s ability to handle legitimate traffic.
- The server, overwhelmed by the influx of reset requests, is forced to drop legitimate connections, resulting in service disruptions and denial of service for legitimate users.
HTTP/2’s Rapid Reset Functionality’s Contribution to the Attack’s Effectiveness
HTTP/2’s rapid reset functionality, designed to improve connection efficiency and responsiveness, becomes a vulnerability in the context of a Rapid Reset DDoS attack. Its ability to quickly terminate connections is exploited by attackers to flood the server with reset requests, effectively denying legitimate users access to the website or service.
- HTTP/2’s rapid reset functionality allows attackers to terminate connections much faster than in previous versions of HTTP, enabling them to launch more effective attacks.
- The rapid reset functionality also makes it more difficult for servers to defend against these attacks, as they are unable to distinguish between legitimate and malicious reset requests.
Real-World Examples of Rapid Reset DDoS Attacks and Their Impact
While specific details of Rapid Reset DDoS attacks are often kept confidential due to security reasons, various reports and research highlight the growing prevalence of these attacks.
- In 2020, a major online gaming platform experienced a significant service disruption caused by a Rapid Reset DDoS attack. The attack leveraged HTTP/2’s rapid reset functionality to overwhelm the platform’s servers, causing widespread outages and impacting millions of users.
- A recent study by a cybersecurity firm revealed a significant increase in the number of Rapid Reset DDoS attacks targeting financial institutions and e-commerce websites. These attacks were designed to disrupt critical services and cause financial losses.
Defending Against Rapid Reset DDoS Attacks
Rapid Reset DDoS attacks, exploiting the HTTP/2 protocol’s efficiency, pose a significant challenge to website and application security. While the attack leverages the protocol’s speed, defenders can employ various mitigation techniques to protect their systems. These techniques aim to identify and block malicious traffic while allowing legitimate users to access the service.
Mitigation Techniques
Effective mitigation strategies are essential to counter the rapid-fire nature of HTTP/2 Rapid Reset DDoS attacks. Several techniques have proven valuable in this regard.
- Rate Limiting: This technique involves setting limits on the number of requests allowed from a specific IP address or network within a defined timeframe. This helps prevent attackers from flooding the server with excessive requests, effectively throttling the attack. For instance, a server can limit the number of HTTP/2 requests per second from a single IP address to a predetermined threshold, effectively slowing down the attack.
- Traffic Filtering: This involves inspecting incoming traffic for suspicious patterns or characteristics associated with Rapid Reset attacks. These patterns can include an unusually high number of HTTP/2 resets, rapid request rates, or requests originating from known botnets. By identifying and filtering out malicious traffic, this technique helps prevent the attack from reaching the server’s resources.
- Challenge-Response Authentication: This method adds an extra layer of security by requiring clients to solve a challenge before accessing the server. This can effectively thwart automated attacks by requiring attackers to solve the challenge before sending each request, significantly slowing down the attack.
Implementing a challenge-response mechanism can involve sending a random token to the client and requiring them to return the token with each request. This approach can effectively differentiate between legitimate users and malicious bots.
- HTTP/2 Connection Pruning: This technique involves proactively closing HTTP/2 connections that exhibit suspicious activity. By monitoring connection behavior, such as frequent resets or high request rates, servers can identify and close connections suspected of being part of an attack. This proactive approach helps prevent attackers from establishing persistent connections, which are crucial for Rapid Reset attacks.
For example, if a connection shows a sudden spike in resets or a high number of requests within a short timeframe, the server can automatically close the connection, effectively preventing the attack from continuing.
- Web Application Firewalls (WAFs): WAFs are essential for filtering malicious traffic and protecting web applications. Modern WAFs can detect and block Rapid Reset attacks by analyzing the traffic patterns, including the frequency of resets and the nature of requests. WAFs can also be configured to enforce specific rules, such as limiting the number of connections per IP address or restricting the use of certain HTTP/2 features.
The HTTP/2 Rapid Reset DDoS attack is a nasty piece of work, flooding servers with connection resets to cripple their performance. It’s a good thing Apple is pushing forward with AI-powered security measures, like those detailed in their recent article on apple intelligence 5 ai powered things you should do immediately.
These advancements could be crucial in detecting and mitigating these kinds of attacks before they cause too much damage. With AI on our side, we might have a fighting chance against the ever-evolving threat of HTTP/2 Rapid Reset DDoS attacks.
Effectiveness of Mitigation Techniques in HTTP/2, Http2 rapid reset ddos attack
The effectiveness of these mitigation techniques in the context of HTTP/2 depends on their implementation and the specific characteristics of the attack.
- Rate Limiting: Rate limiting remains an effective mitigation technique for HTTP/2 Rapid Reset attacks. By limiting the number of requests allowed from a specific IP address or network within a defined timeframe, servers can effectively throttle the attack, preventing it from overwhelming the server’s resources.
However, attackers can employ techniques to circumvent rate limiting, such as using multiple IP addresses or proxies to distribute their traffic.
- Traffic Filtering: Traffic filtering can be effective in identifying and blocking malicious traffic associated with Rapid Reset attacks. By analyzing traffic patterns, such as the frequency of resets and the nature of requests, servers can distinguish legitimate traffic from malicious traffic.
However, attackers can employ techniques to obfuscate their traffic, making it more difficult to identify and filter. For instance, they can use encrypted connections or proxy servers to mask their attack traffic.
- Challenge-Response Authentication: Challenge-response authentication can be an effective deterrent against automated attacks, including Rapid Reset attacks. By requiring clients to solve a challenge before accessing the server, this technique adds an extra layer of security, effectively slowing down the attack. However, sophisticated attackers can develop techniques to bypass challenge-response mechanisms, such as using botnets or employing machine learning algorithms to solve the challenges automatically.
- HTTP/2 Connection Pruning: HTTP/2 connection pruning can be a valuable technique for mitigating Rapid Reset attacks. By proactively closing HTTP/2 connections exhibiting suspicious activity, servers can prevent attackers from establishing persistent connections. However, attackers can employ techniques to evade connection pruning, such as using multiple connections or constantly changing their IP addresses.
- Web Application Firewalls (WAFs): WAFs play a crucial role in defending against Rapid Reset attacks. Modern WAFs can analyze traffic patterns, identify suspicious behavior, and block malicious traffic effectively. However, WAFs are not a silver bullet, and attackers can exploit vulnerabilities in WAFs or use techniques to bypass their defenses.
It is crucial to choose a WAF that is specifically designed to handle HTTP/2 traffic and has robust defenses against Rapid Reset attacks.
Comparison and Contrast of Defense Strategies
Each mitigation technique has its strengths and limitations.
Remember those days when HTTP/2 rapid reset DDoS attacks were the bane of our existence? Well, it seems like those were simpler times. I was just reminiscing about the good old days and stumbled upon this amazing news: the cult classic early 2000s game Habbo Hotel is back and you can play it on your modern Mac for free right now ! It’s almost enough to make me forget about those pesky HTTP/2 rapid reset attacks, at least for a little while.
- Rate Limitingis relatively easy to implement and effective against basic attacks. However, it can be bypassed by attackers using multiple IP addresses or proxies.
- Traffic Filteringis more sophisticated but can be challenging to implement effectively, especially when dealing with encrypted traffic.
- Challenge-Response Authenticationis an effective deterrent against automated attacks, but it can impact user experience and be bypassed by sophisticated attackers.
- HTTP/2 Connection Pruningcan be effective against persistent attacks, but it can also lead to false positives, blocking legitimate users.
- Web Application Firewalls (WAFs)offer comprehensive protection but require careful configuration and maintenance to ensure effectiveness against evolving attack techniques.
Security Implications of HTTP/2

HTTP/2, while bringing significant performance enhancements to web applications, introduces new security challenges that need careful consideration. Understanding these implications and implementing appropriate mitigation strategies is crucial for maintaining the integrity and security of web applications and infrastructure.
Challenges in Securing Web Applications Against HTTP/2-Based Attacks
The introduction of HTTP/2 has brought new security challenges, primarily due to its enhanced performance and the potential for exploitation of its features. These challenges include:
- Increased Attack Surface:HTTP/2’s multiplexing capabilities allow multiple requests to be sent over a single connection, increasing the potential attack surface. This makes it more difficult to detect and mitigate malicious traffic, as multiple attacks can be disguised within a single connection.
- Vulnerability to Server-Side Attacks:HTTP/2’s server push feature, while beneficial for performance, can be exploited for server-side attacks. Malicious actors could send unwanted or malicious content to clients through server push, potentially leading to vulnerabilities like cross-site scripting (XSS) or injection attacks.
- New Attack Vectors:HTTP/2 introduces new attack vectors, such as the ability to manipulate header fields and exploit vulnerabilities in the protocol itself. These vulnerabilities can be exploited for denial-of-service (DoS) attacks or other malicious activities.
- Increased Complexity:The complexity of HTTP/2, with its new features and mechanisms, can make it challenging for security professionals to understand and mitigate potential vulnerabilities. This complexity can lead to misconfigurations and security gaps that can be exploited by attackers.
Recommendations for Securing Web Applications and Mitigating Risks Associated with HTTP/2
To effectively mitigate the security risks associated with HTTP/2, it is crucial to adopt a comprehensive security approach that addresses the specific challenges posed by the protocol. This includes:
- Implement Robust Security Practices:It is essential to follow established security best practices, such as input validation, output encoding, and secure coding techniques, to protect against common web application vulnerabilities. These practices remain crucial for mitigating risks associated with HTTP/2.
- Secure Server Push:Implement strict controls for server push functionality, ensuring that only trusted content is pushed to clients. Regularly review and update server push configurations to mitigate potential vulnerabilities.
- Secure HTTP/2 Implementation:Utilize secure HTTP/2 implementations, such as those offered by popular web servers and frameworks, to minimize vulnerabilities and ensure proper protocol handling.
- Regular Security Audits:Conduct regular security audits to identify and address potential vulnerabilities in HTTP/2 implementations. These audits should include assessments of server push configurations, header field manipulation, and other potential attack vectors.
- Monitor for Suspicious Activity:Implement robust monitoring systems to detect suspicious activity, such as unusual traffic patterns, unexpected requests, or attempts to manipulate header fields. This allows for early detection and response to potential threats.
- Stay Informed:Keep up-to-date with the latest security vulnerabilities and best practices related to HTTP/2. This ensures that you can proactively address emerging threats and implement appropriate mitigation strategies.
Future Trends in DDoS Attacks and HTTP/2
The rise of HTTP/2 has significantly impacted the landscape of DDoS attacks. As we move forward, we can expect to see a continued evolution of DDoS tactics, leveraging the capabilities and vulnerabilities of HTTP/2. Understanding these emerging trends is crucial for organizations to effectively defend against future attacks.
Emerging Attack Vectors and Techniques
The adoption of HTTP/2 has opened up new attack vectors for DDoS perpetrators. These techniques exploit the protocol’s features, such as multiplexing and header compression, to amplify the impact of attacks.
- HTTP/2-Specific Amplification Attacks:Attackers can exploit the compression capabilities of HTTP/2 to amplify the size of requests, leading to larger-scale DDoS attacks. By sending small, compressed requests that expand significantly on the server-side, attackers can overwhelm the target’s resources with a minimal amount of traffic.
- Exploiting Multiplexing:HTTP/2’s multiplexing feature allows multiple requests to be sent over a single connection. Attackers can leverage this to launch multiple simultaneous attacks, increasing the overall attack volume and making it harder for defenses to identify and mitigate the attack.
- DoS Attacks Targeting HTTP/2 Features:Attackers can specifically target HTTP/2 features like server push and header compression. By sending malformed or excessively large requests, they can disrupt the normal operation of the server and cause denial-of-service conditions.
Emerging Technologies and Security Practices
To combat these evolving threats, organizations need to adopt new technologies and security practices specifically designed for HTTP/2 environments.
- HTTP/2-Aware DDoS Mitigation Solutions:Traditional DDoS mitigation solutions may not be effective against HTTP/2-based attacks. Organizations need to adopt solutions specifically designed to detect and mitigate HTTP/2-specific attack vectors.
- Advanced Threat Intelligence:Staying ahead of emerging threats requires access to real-time threat intelligence. This includes understanding the latest HTTP/2-based attack techniques, attacker tactics, and emerging vulnerabilities.
- Improved Security Posture:Organizations need to implement strong security practices, including secure configuration, vulnerability management, and regular security assessments. This will help minimize the attack surface and improve their overall resilience against DDoS attacks.