Syxsense: A Novel Unified Endpoint Management Strategy
Syxsense novel unified endpoint management strategy – Syxsense: A Novel Unified Endpoint Management Strategy presents a fresh approach to tackling the complexities of managing diverse endpoints in today’s dynamic IT environment. Imagine a world where you can seamlessly manage every device, from laptops and desktops to mobile phones and IoT devices, all from a single, centralized console.
Syxsense makes this vision a reality by offering a comprehensive solution that streamlines security, compliance, and productivity across your entire IT landscape.
In a world where security threats are constantly evolving and the number of endpoints continues to grow, a unified approach to endpoint management is no longer a luxury but a necessity. Syxsense’s platform is designed to meet these challenges head-on, offering features like advanced threat detection and response, automated patch management, and granular access control.
By simplifying the management of your endpoints, Syxsense empowers you to focus on what matters most: driving your business forward.
The Need for Unified Endpoint Management
The modern IT landscape is characterized by a diverse array of devices, applications, and operating systems. This diversity presents significant challenges for IT teams tasked with managing and securing these endpoints.
Challenges of Managing Diverse Endpoints
The increasing complexity of modern IT environments, coupled with the rise of remote work and the adoption of cloud services, has made it increasingly difficult for IT teams to effectively manage diverse endpoints. Some key challenges include:
- Device Heterogeneity:IT teams must manage a wide range of devices, including laptops, desktops, smartphones, tablets, and IoT devices, each with its own unique operating system, hardware specifications, and software requirements. This heterogeneity makes it difficult to apply consistent security policies and manage updates across all devices.
- Application Proliferation:The increasing use of cloud-based applications and software-as-a-service (SaaS) solutions has led to a proliferation of applications on endpoints. This can make it difficult to track and manage application usage, security risks, and performance issues.
- Remote Work:The rise of remote work has created new challenges for endpoint management, as IT teams must ensure that remote employees have access to the resources they need while maintaining security and compliance. This requires robust remote access solutions and secure endpoint management tools.
- Security Threats:The increasing sophistication of cyberattacks and the growing number of vulnerabilities in endpoint devices have made it more challenging than ever to protect sensitive data. IT teams need to implement comprehensive security measures, including endpoint protection, vulnerability management, and data loss prevention.
Syxsense’s novel unified endpoint management strategy offers a streamlined approach to managing devices across your organization, but sometimes you just need a little escape from the technical world. If you’re looking for a dose of fashion inspiration, check out the Lisa Tan x Coast dresses at Debenhams collection.
It’s the perfect way to refresh your wardrobe while you strategize your next move with Syxsense.
Security Threats and Vulnerabilities
Endpoint devices are a prime target for cyberattacks due to their vulnerability to malware, phishing scams, and other threats. Some common security threats and vulnerabilities specific to endpoints include:
- Malware:Malicious software, such as viruses, worms, and ransomware, can infect endpoint devices and compromise sensitive data, disrupt operations, and steal credentials. This can be spread through email attachments, infected websites, or malicious downloads.
- Phishing Attacks:Phishing emails and websites attempt to trick users into revealing sensitive information, such as login credentials or financial details, by impersonating legitimate entities. These attacks can be highly effective, especially when targeting employees who may not be aware of the risks.
- Unpatched Vulnerabilities:Software vulnerabilities can be exploited by attackers to gain unauthorized access to endpoint devices. These vulnerabilities often exist in operating systems, applications, and other software components. Regular security updates are essential to patch these vulnerabilities and prevent attacks.
- Data Loss:Sensitive data stored on endpoint devices can be lost or stolen due to theft, accidental deletion, or unauthorized access. Implementing data loss prevention (DLP) solutions can help prevent this by monitoring and controlling data transfer and access.
Impact of Endpoint Management on Productivity and Efficiency
Effective endpoint management is essential for maintaining productivity and efficiency in modern IT environments. Poorly managed endpoints can lead to:
- Security Breaches:Unsecured endpoints can be a major source of security breaches, leading to data loss, financial losses, and reputational damage.
- Downtime:Endpoint devices that are not properly maintained or updated can experience downtime, disrupting operations and reducing productivity. This can result in lost revenue and customer dissatisfaction.
- IT Support Costs:Managing diverse endpoints manually can be time-consuming and resource-intensive. This can lead to increased IT support costs and reduced efficiency.
- Compliance Risks:Organizations are increasingly subject to regulatory requirements and compliance standards related to data security and privacy. Effective endpoint management is essential for meeting these requirements and mitigating compliance risks.
Syxsense’s Approach to Endpoint Management: Syxsense Novel Unified Endpoint Management Strategy

Syxsense takes a comprehensive approach to endpoint management, aiming to simplify and streamline the process while providing robust security and control. Their platform is designed to be user-friendly and scalable, catering to businesses of all sizes.
Syxsense Platform Features and Capabilities
Syxsense’s platform is built on a foundation of key features and capabilities designed to empower IT administrators to manage endpoints effectively. These features include:
- Unified Management Console:A single, intuitive dashboard provides a centralized view of all endpoints, their status, and any potential issues. This console simplifies management by eliminating the need to switch between multiple tools.
- Endpoint Security:Syxsense offers comprehensive endpoint security features, including antivirus, anti-malware, firewall management, and intrusion detection and prevention systems. These features help protect endpoints from a wide range of threats.
- Patch Management:Automated patch management ensures that all endpoints are up-to-date with the latest security patches and software updates, reducing vulnerabilities and improving system stability.
- Software Deployment:Syxsense facilitates efficient software deployment to endpoints, simplifying the process of distributing applications and updates across the network.
- Asset Management:Detailed asset inventory allows IT administrators to track hardware and software assets, enabling efficient resource allocation and license management.
- Remote Control and Support:Remote access and control capabilities enable IT staff to troubleshoot and resolve issues on endpoints remotely, minimizing downtime and improving support efficiency.
- Reporting and Analytics:Comprehensive reporting and analytics provide insights into endpoint health, security posture, and user activity, allowing administrators to identify trends and make informed decisions.
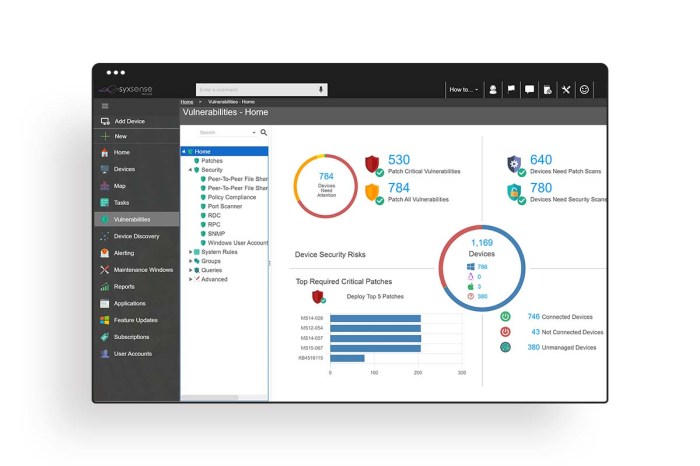
Unified Management Console
The Syxsense unified management console is a central hub for managing all endpoints. It provides a single interface for configuring policies, monitoring endpoint status, and troubleshooting issues. The console’s key features include:
- Dashboard:A customizable dashboard provides a high-level overview of endpoint health, security status, and key performance indicators (KPIs). Administrators can quickly identify potential issues and prioritize actions.
- Endpoint Inventory:A comprehensive inventory lists all managed endpoints, including hardware and software details, allowing administrators to track assets and manage licenses effectively.
- Policy Management:Centralized policy management allows administrators to define and enforce security and compliance policies across all endpoints. This ensures consistent security practices and reduces configuration complexity.
- Task Automation:Automated tasks, such as software deployments, patch updates, and script execution, streamline routine operations and improve efficiency.
- Reporting and Analytics:Customizable reports and dashboards provide insights into endpoint performance, security posture, and user activity. These reports help administrators identify trends, optimize resource allocation, and make informed decisions.
Comparison with Other Endpoint Management Solutions
Syxsense distinguishes itself from other endpoint management solutions through its focus on:
- Unified Management:Unlike solutions that require multiple tools for different tasks, Syxsense provides a single, integrated platform for managing all aspects of endpoint lifecycle.
- Ease of Use:The platform is designed to be user-friendly, with an intuitive interface and simplified workflows, making it accessible to IT professionals of all skill levels.
- Scalability:Syxsense’s platform is designed to scale with growing business needs, supporting large numbers of endpoints without compromising performance.
- Cost-Effectiveness:Syxsense offers flexible pricing options and a comprehensive feature set, making it a cost-effective solution for businesses of all sizes.
Benefits of a Unified Endpoint Management Strategy

A unified endpoint management strategy offers numerous advantages that extend beyond basic device control. By integrating various management functions into a single platform, organizations can streamline operations, enhance security, and optimize resource utilization.
Improved Security
A unified approach to endpoint management significantly enhances security by providing a comprehensive view of all devices and their configurations. This visibility allows organizations to identify potential vulnerabilities, implement consistent security policies, and respond effectively to threats.
- Centralized Patch Management:Unified endpoint management platforms automate the process of patching vulnerabilities, ensuring that all devices are updated with the latest security fixes. This eliminates the risk of unpatched systems becoming targets for malware and exploits. For example, a unified platform can identify outdated software on all endpoints and automatically deploy the necessary patches, minimizing the window of vulnerability and reducing the risk of security breaches.
- Threat Detection and Response:By centralizing endpoint security data, organizations can gain real-time insights into potential threats and suspicious activities. This allows for proactive threat detection and response, minimizing the impact of attacks. Unified platforms often integrate with security information and event management (SIEM) systems, providing a comprehensive view of security events across the entire network.
- Data Loss Prevention:Unified endpoint management solutions often include data loss prevention (DLP) features that prevent sensitive information from leaving the organization’s network. This helps organizations comply with regulatory requirements and protect sensitive data from unauthorized access or disclosure.
Compliance and Regulatory Requirements, Syxsense novel unified endpoint management strategy
Unified endpoint management platforms simplify compliance efforts by enabling organizations to enforce consistent security policies across all devices. This ensures that organizations meet regulatory requirements and minimize the risk of fines or penalties.
- Data Privacy Regulations:Compliance with regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) requires organizations to implement robust data protection measures. Unified endpoint management platforms can help organizations meet these requirements by providing tools for data encryption, access control, and data loss prevention.
- Industry-Specific Standards:Many industries have specific security standards that organizations must adhere to. For example, the healthcare industry must comply with the Health Insurance Portability and Accountability Act (HIPAA), while the financial industry must comply with the Payment Card Industry Data Security Standard (PCI DSS).
Unified endpoint management platforms can help organizations meet these industry-specific standards by providing pre-configured policies and templates.
- Auditing and Reporting:Unified endpoint management platforms provide comprehensive auditing and reporting capabilities, allowing organizations to demonstrate compliance with regulatory requirements. This documentation can be used to support audits and investigations.
Cost Savings
A unified endpoint management strategy can significantly reduce IT operational costs by streamlining management processes and automating tasks.
- Reduced IT Staff Time:By automating tasks such as software deployment, patch management, and device configuration, unified endpoint management platforms free up IT staff to focus on more strategic initiatives. For example, a single platform can manage software updates across hundreds of devices, eliminating the need for manual intervention and reducing the time spent on routine tasks.
- Improved Efficiency:Centralized management reduces the complexity of managing multiple endpoints, improving overall efficiency and productivity. This allows IT teams to focus on resolving critical issues and providing proactive support.
- Reduced Hardware Costs:By optimizing device performance and extending the lifespan of existing hardware, unified endpoint management platforms can reduce the need for new hardware purchases. This can result in significant cost savings over time.
Implementation and Deployment Considerations
Implementing Syxsense’s unified endpoint management strategy requires careful planning and execution. The process involves evaluating your existing IT infrastructure, determining the necessary hardware and software resources, and designing a phased rollout strategy.
Step-by-Step Implementation Guide
The following steps provide a comprehensive guide for implementing Syxsense’s solution:
- Define Scope and Objectives: Clearly define the scope of the implementation, including the number of endpoints, operating systems, and applications to be managed. Establish specific objectives, such as improving security posture, reducing IT costs, or enhancing user productivity.
- Perform Infrastructure Assessment: Evaluate your existing IT infrastructure, including network connectivity, hardware resources, and existing management tools. Identify potential compatibility issues and assess the impact of Syxsense integration.
- Choose Deployment Model: Determine the deployment model that best suits your organization’s needs. Options include cloud-based, on-premises, or hybrid deployments. Consider factors such as security requirements, data sovereignty, and cost-effectiveness.
- Install and Configure Syxsense: Install the Syxsense agent on all targeted endpoints. Configure the Syxsense console with your desired settings, including policies, security profiles, and reporting preferences.
- Pilot and Test: Implement a pilot program on a limited number of endpoints to test the functionality and performance of Syxsense. Collect feedback from users and IT staff to identify any necessary adjustments.
- Phased Rollout: Gradually roll out Syxsense to the entire endpoint population, starting with a small group and gradually expanding to the entire organization. This approach allows for continuous monitoring and adjustments during the implementation process.
- Ongoing Monitoring and Optimization: Monitor Syxsense’s performance and effectiveness continuously. Analyze data from the Syxsense console to identify potential issues, optimize settings, and ensure that the solution meets your ongoing needs.
Required Hardware and Software Resources
Implementing Syxsense requires specific hardware and software resources. The following table Artikels the essential components:
| Resource Type | Description | Requirements |
|---|---|---|
| Server | A dedicated server to host the Syxsense console and database. |
Processor Intel Xeon or AMD equivalent with at least 4 cores RAM Syxsense’s novel unified endpoint management strategy offers a comprehensive approach to security and control, but sometimes, even the most dedicated IT professional needs a break. A refreshing cocktail in a beautifully crafted glass can be just the ticket, and the new additions to the Waterford glassware mixology collection are sure to elevate any drink. Back to business, though – Syxsense’s strategy ensures your endpoints are secure and optimized, allowing you to focus on the bigger picture, even if that includes enjoying a well-deserved cocktail. Minimum 8GB, recommended 16GB or more Storage 100GB or more of available storage space Syxsense’s novel unified endpoint management strategy is a game-changer for IT departments, streamlining security and efficiency across the board. But what happens when you need to take that management to the next level, connecting with users in a more personalized way? That’s where the “bold chatbot David Byttow secret” bold chatbot david byttow secret comes into play. By tapping into the power of AI-driven chatbots, Syxsense can enhance its platform, making it even more intuitive and user-friendly. Operating System Windows Server 2012 R2 or later |
| Database | A database to store Syxsense data, such as endpoint inventory, security logs, and policy configurations. |
|
| Network Connectivity | Secure and reliable network connectivity between the Syxsense server and managed endpoints. |
|
| Syxsense Agent | A lightweight agent that runs on each managed endpoint to provide real-time data and control. |
|
Integration with Existing IT Infrastructure
Integrating Syxsense with your existing IT infrastructure involves connecting it to your directory services, active directory, and other management tools. The following flowchart illustrates the integration process:[Image Description: A flowchart showing the integration process of Syxsense with existing IT infrastructure.
It starts with the Syxsense console and branches out to connect with Active Directory, directory services, and other management tools. The flow then converges back to the Syxsense console, indicating the successful integration of Syxsense with existing IT infrastructure.]
Real-World Examples and Case Studies
The power of Syxsense’s unified endpoint management solution is best illustrated through real-world examples. These case studies showcase how organizations across various industries have leveraged Syxsense to enhance security, optimize compliance, and boost productivity.
Improving Security Posture in a Healthcare Organization
A large healthcare organization faced the challenge of securing its vast network of endpoints, including desktops, laptops, and mobile devices. The organization was struggling to maintain consistent security policies across its diverse IT infrastructure. Syxsense was implemented to address these challenges.
The solution provided comprehensive endpoint security capabilities, including:
- Real-time threat detection and response
- Vulnerability assessment and patching
- Data loss prevention
- Endpoint encryption
Syxsense helped the organization:
- Reduce the risk of data breaches by proactively identifying and mitigating vulnerabilities.
- Ensure compliance with HIPAA regulations by enforcing strict security controls on sensitive patient data.
- Improve the overall security posture of the organization by centralizing endpoint management and monitoring.
“Syxsense has been instrumental in helping us achieve our security goals. The platform’s comprehensive capabilities and ease of use have enabled us to significantly improve our security posture and protect patient data.”
Chief Information Security Officer, Healthcare Organization.
Future Trends in Endpoint Management
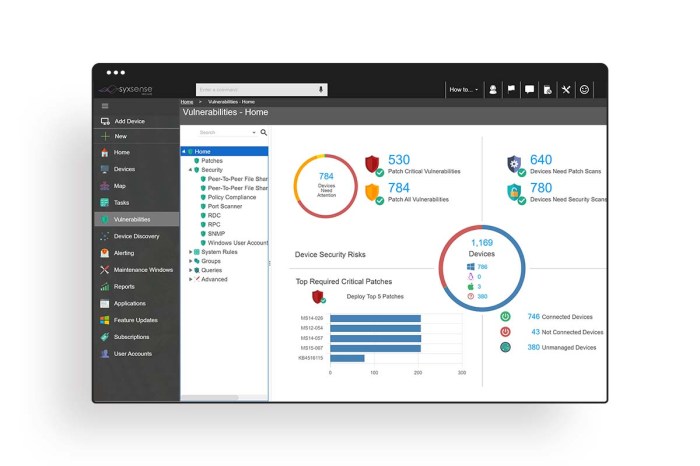
The landscape of endpoint management is constantly evolving, driven by the rapid adoption of new technologies and changing user expectations. Understanding these trends is crucial for organizations to stay ahead of the curve and ensure their endpoint management strategies remain effective and secure.
The Rise of Mobile Devices
The increasing popularity of mobile devices has significantly impacted endpoint management. Organizations now need to manage a diverse range of devices, including smartphones, tablets, and laptops, across multiple operating systems. This poses challenges for traditional endpoint management solutions, which were primarily designed for desktops.
“By 2025, the number of mobile devices in use worldwide is expected to reach 18.2 billion, with a majority of these devices being smartphones.”
Statista
This trend has led to the development of mobile device management (MDM) solutions, which provide a centralized platform for managing mobile devices, including security policies, app distribution, and data protection. MDM solutions are becoming increasingly integrated with traditional endpoint management systems, enabling organizations to manage all their devices from a single console.