network security
-
Network Security
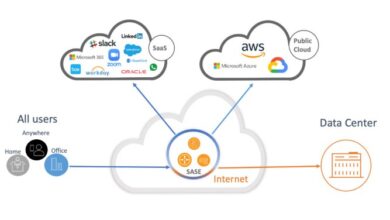
Secure Access Service Edge Platforms: The Future of Network Security
Secure Access Service Edge platforms, or SASE, are taking center stage in the ever-evolving world of network security. SASE represents…
Read More » -
Cloud Security

Gigamon Cloud Security Report: Protecting Your Digital Assets
The Gigamon Cloud Security Report delves into the critical landscape of safeguarding digital assets in today’s increasingly cloud-dependent world. As…
Read More » -
Small Business Technology

Top Network Management Software for Small Businesses
Top network management software small businesses – Top network management software for small businesses is essential for ensuring smooth operations…
Read More » -
Cybersecurity
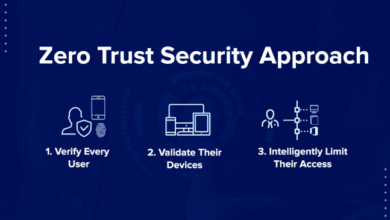
Zero Trust Security Tips: Protecting Your Digital Assets
Zero Trust security tips are essential in today’s digital landscape, where threats are constantly evolving. The traditional perimeter-based security model…
Read More » -
Cybersecurity

Blast Radius Vulnerability: Understanding the Impact and Mitigation
Blastradius vulnerability radius protocol – Blast radius vulnerability radius protocol sets the stage for this enthralling narrative, offering readers a…
Read More » -
Cybersecurity

Nine Ethical Hacking Courses: Your Path to Cybersecurity
Nine ethical hacking courses offer a gateway to the fascinating world of cybersecurity. As technology continues to evolve, the need…
Read More » -
Security
NordLayer Remote Access VPN: Securely Connect to Your Network
NordLayer remote access VPN is a powerful tool that allows you to securely access your work network from anywhere in…
Read More » -
Cybersecurity

F5 Generative AI: Cybersecurity Interview
F5 generative ai cybersecurity interview – F5 Generative AI: Cybersecurity Interview sets the stage for an exploration of how artificial…
Read More » -
Cybersecurity
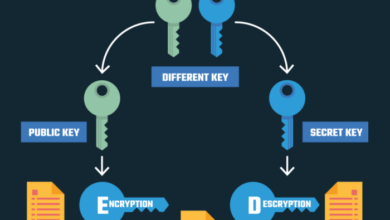
Asymmetric vs Symmetric Encryption: A Tale of Two Keys
Asymmetric vs symmetric encryption: these two seemingly complex terms hold the key to unlocking a world of secure communication and…
Read More » -
Network Security

Cisco IOS XE Software Zero-Day Vulnerability: A Critical Threat
Cisco ios xe software zero day vulnerability – Cisco IOS XE software zero-day vulnerability is a critical threat that can…
Read More »


