Microsoft Azure Outage: A DDoS Attack Analysis
Microsoft azure outage ddos attack – Microsoft Azure Outage: A DDoS Attack Analysis – The recent Microsoft Azure outage, caused by a massive Distributed Denial of Service (DDoS) attack, sent shockwaves through the tech world. This incident highlighted the vulnerability of even the most robust cloud platforms to these sophisticated cyberattacks, leaving countless businesses and individuals grappling with disruptions to their critical services.
The attack, which began on [Start Date] and lasted for [Duration], targeted a range of Azure services, including [List of affected services]. The impact was widespread, with users experiencing [Describe the impact on users]. This event raises crucial questions about cloud security and the need for enhanced defenses against increasingly sophisticated cyber threats.
Understanding the Microsoft Azure Outage: Microsoft Azure Outage Ddos Attack
The recent Microsoft Azure outage, which occurred on [Date], was a significant event that disrupted services for numerous users worldwide. This outage, attributed to a Distributed Denial of Service (DDoS) attack, highlighted the vulnerability of cloud infrastructure to large-scale attacks and the potential impact on businesses and individuals relying on cloud services.
Impact on Users, Microsoft azure outage ddos attack
The DDoS attack resulted in widespread service disruptions across various Azure services, impacting users in diverse sectors. The outage affected users’ ability to access and utilize cloud-based applications, websites, and other digital services.
Affected Services
The outage primarily affected services within Azure’s global network, including:
- Azure Storage
- Azure SQL Database
- Azure Virtual Machines
- Azure Active Directory
- Azure Cosmos DB
These services are critical for numerous applications and businesses, and their disruption caused significant inconvenience and potential financial losses.
Timeline of the Outage
The outage began on [Start Time] and lasted for approximately [Duration]. Microsoft engineers worked tirelessly to mitigate the attack and restore service availability. The company provided regular updates on the status of the outage and the progress of the restoration process.
The Role of DDoS Attacks
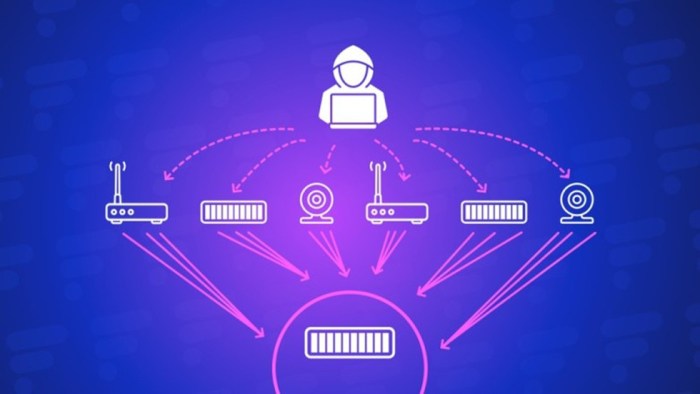
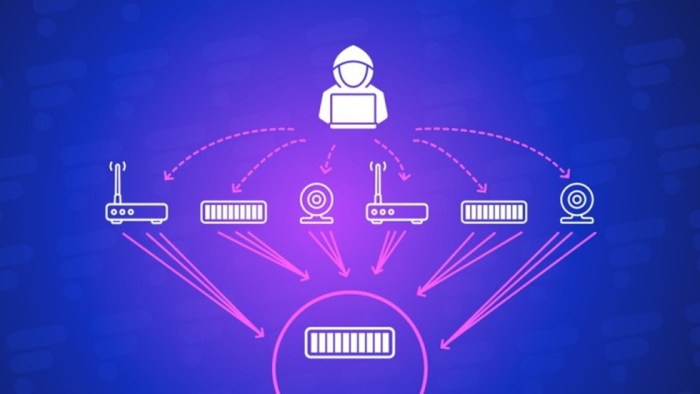
DDoS attacks, or Distributed Denial of Service attacks, are a common type of cyberattack that aims to disrupt the availability of online services. These attacks are particularly concerning in the context of cloud services like Microsoft Azure, as they can have a significant impact on businesses and individuals relying on these platforms.
Understanding DDoS Attacks
DDoS attacks work by overwhelming a target server or network with a massive amount of traffic from multiple sources. These sources, often compromised computers or devices known as “bots,” are controlled by attackers and used to flood the target with requests.
The sheer volume of traffic overwhelms the target’s resources, causing it to slow down or even crash, effectively denying legitimate users access to the service.
Motives Behind DDoS Attacks
The motives behind DDoS attacks can vary, but some common reasons include:
- Extortion:Attackers may target organizations with DDoS attacks to extort money in exchange for stopping the attack.
- Disruption:Attackers may launch DDoS attacks to disrupt the operations of a competitor or an organization they oppose.
- Cyberwarfare:Nation-states may use DDoS attacks as a tool of cyberwarfare to disrupt critical infrastructure or government services.
- Political Activism:Hacktivist groups may launch DDoS attacks to protest against a company’s policies or actions.
- Personal Vendetta:Individuals may launch DDoS attacks against individuals or organizations out of personal spite or revenge.
Impact of DDoS Attacks on Cloud Services
DDoS attacks can have a significant impact on cloud services, affecting:
- Service Availability:DDoS attacks can render cloud services unavailable to legitimate users, disrupting business operations and causing financial losses.
- Data Integrity:If the attack overwhelms the cloud service’s resources, it can lead to data loss or corruption.
- Reputation Damage:Frequent or severe DDoS attacks can damage the reputation of a cloud service provider, leading to customer loss and decreased trust.
- Security Breaches:DDoS attacks can be used as a distraction tactic to allow attackers to gain access to sensitive data or systems.
The recent Microsoft Azure outage caused by a DDoS attack highlighted the vulnerability of even the most robust cloud infrastructure. It’s a stark reminder that even the most sophisticated systems can be brought down by determined attackers. While we grapple with the consequences of these attacks, it’s also a good time to reflect on the importance of resilience and the lessons we can learn from others.
That’s why I’ve been enjoying six months of the ABM Book Club , where we delve into the latest thinking on cybersecurity and how to build more resilient systems. The insights gleaned from these discussions are invaluable in helping us navigate the ever-evolving landscape of cyber threats.
The recent Microsoft Azure outage caused by a massive DDoS attack really highlighted how vulnerable our online infrastructure can be. It’s a stark reminder that even the most sophisticated systems can be brought down by malicious actors. This got me thinking about the importance of cybersecurity, and how we can all do our part to protect ourselves.
A great resource for learning more about online safety is the blog at home with elizabeth , which offers practical tips and advice for navigating the digital world. Hopefully, by working together, we can build a more resilient and secure online environment for everyone.
The recent Microsoft Azure outage caused by a DDoS attack was a major disruption for many businesses and individuals relying on cloud services. While dealing with such technical issues, I found myself seeking a creative outlet, and stumbled upon a fascinating project – how to make a lace patterned coffee table.
It’s amazing how intricate designs can be achieved with simple materials. Just like the complex layers of a DDoS attack, the intricate lace pattern requires careful planning and execution. The resilience of our digital infrastructure, much like the durability of a well-crafted coffee table, is crucial in facing such challenges.