Cybersecurity Skills: Infosec4TC Essentials
Cyber security skills infosec4tc – Cybersecurity skills: Infosec4TC – in today’s digital world, where data breaches and cyberattacks are becoming increasingly common, mastering cybersecurity skills is no longer optional. It’s a necessity for individuals and organizations alike. From protecting personal information to safeguarding sensitive business data, the importance of cybersecurity cannot be overstated.
The Infosec4TC domain encompasses a wide range of cybersecurity expertise, from network security and application security to incident response and threat intelligence. This guide will delve into the essential skills needed for Infosec4TC, explore career paths within this field, and provide a roadmap for individuals looking to develop their cybersecurity expertise.
The Importance of Cybersecurity Skills
In today’s digital age, where nearly every aspect of our lives is interconnected, cybersecurity skills have become indispensable. From personal data protection to safeguarding critical infrastructure, the importance of cybersecurity cannot be overstated.
Consequences of Cybersecurity Breaches
Cybersecurity breaches can have devastating consequences for both individuals and organizations.
- Financial Loss:Cybercriminals can steal financial information, leading to identity theft, fraudulent transactions, and significant financial losses.
- Reputation Damage:Data breaches can severely damage an organization’s reputation, eroding customer trust and impacting brand value.
- Legal and Regulatory Penalties:Organizations that fail to adequately protect sensitive data may face hefty fines and legal repercussions.
- Disruption of Operations:Cyberattacks can disrupt critical business operations, leading to downtime, lost productivity, and financial losses.
- Loss of Intellectual Property:Cybercriminals can steal valuable intellectual property, such as trade secrets, designs, and research data, giving competitors an unfair advantage.
Real-World Examples of Cyberattacks
- The Equifax Data Breach (2017):This massive breach exposed the personal information of over 147 million individuals, including Social Security numbers, credit card details, and addresses.
- The WannaCry Ransomware Attack (2017):This global ransomware attack infected hundreds of thousands of computers worldwide, encrypting data and demanding ransom payments.
- The NotPetya Ransomware Attack (2017):This attack, initially believed to be ransomware, caused widespread disruption to businesses and critical infrastructure, with estimated losses exceeding $10 billion.
Essential Cybersecurity Skills for Infosec4TC
The Infosec4TC domain demands a diverse skillset to safeguard critical infrastructure and ensure operational resilience. These skills are crucial for effectively mitigating threats, responding to incidents, and maintaining the integrity and availability of essential systems.
Network Security
Network security forms the bedrock of any robust cybersecurity posture. It involves understanding and securing the network infrastructure, including physical and virtual networks, devices, and protocols.
- Network Segmentation: Dividing the network into smaller, isolated segments reduces the impact of a compromise, limiting the attacker’s ability to spread laterally. Implementing network segmentation with firewalls, VLANs, and other security controls is essential.
- Firewall Management: Firewalls act as a barrier, filtering traffic based on predefined rules. Understanding firewall rules, configuration, and troubleshooting are crucial for effective network security.
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity, alerting administrators to potential threats and blocking malicious traffic. Knowledge of IDS/IPS deployment, configuration, and rule tuning is essential.
- Wireless Security: Securely configuring and managing wireless networks, including WPA2/3 encryption and access control mechanisms, is crucial to prevent unauthorized access.
- Network Forensics: Investigating network security incidents involves analyzing network traffic, logs, and other data to identify the source, scope, and impact of the attack. This requires expertise in network protocols, packet analysis tools, and forensic methodologies.
Application Security, Cyber security skills infosec4tc
Protecting applications from vulnerabilities and attacks is paramount. This involves understanding application development practices, identifying security flaws, and implementing security measures throughout the software development lifecycle.
- Secure Coding Practices: Developers must adhere to secure coding principles to minimize vulnerabilities in applications. This includes input validation, output encoding, secure authentication, and authorization mechanisms.
- Vulnerability Scanning: Automated tools scan applications for known vulnerabilities and weaknesses. Understanding vulnerability scanning methodologies, interpreting reports, and prioritizing remediation efforts are critical.
- Web Application Firewalls (WAFs): WAFs protect web applications from common attacks by filtering malicious traffic and enforcing security policies. Configuring and managing WAFs effectively is essential for web application security.
- Security Testing: Penetration testing, code reviews, and other security testing methodologies help identify vulnerabilities and weaknesses in applications. Understanding these techniques and their application is crucial for ensuring application security.
Incident Response
Prompt and effective incident response is crucial for minimizing the impact of security incidents. This involves identifying, analyzing, containing, and recovering from security breaches.
- Incident Response Planning: Developing and maintaining a comprehensive incident response plan, including roles and responsibilities, communication protocols, and escalation procedures, is essential for a coordinated and effective response.
- Incident Detection and Analysis: Recognizing and analyzing security incidents, including identifying the nature, scope, and impact of the attack, is crucial for an informed response. This involves monitoring logs, security alerts, and network traffic for suspicious activity.
- Containment and Remediation: Isolating the compromised system or network segment and taking steps to prevent further damage is critical. This may involve disconnecting infected systems, blocking malicious traffic, or implementing temporary security measures.
- Recovery and Lessons Learned: Restoring systems and data to their pre-incident state and conducting a thorough post-incident analysis to identify lessons learned and improve future response capabilities is essential.
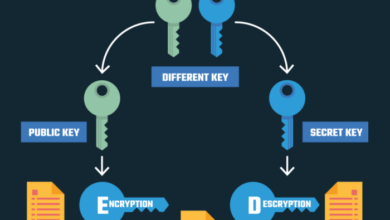
Cryptography
Cryptography plays a vital role in securing data and communications, protecting sensitive information from unauthorized access and manipulation.
- Encryption Algorithms: Understanding various encryption algorithms, including symmetric and asymmetric encryption, and their strengths and weaknesses is crucial for selecting appropriate encryption methods.
- Digital Signatures: Digital signatures ensure message authenticity and integrity, verifying the sender’s identity and preventing message tampering.
- Key Management: Securely generating, storing, and managing encryption keys is critical for maintaining the effectiveness of cryptographic solutions.
- Cryptographic Protocols: Understanding and implementing cryptographic protocols, such as TLS/SSL for secure communication, is essential for securing data transmission.
Security Operations
Security operations teams are responsible for monitoring, managing, and responding to security threats on a continuous basis.
- Security Information and Event Management (SIEM): SIEM systems aggregate and analyze security data from various sources, providing a comprehensive view of security events and enabling proactive threat detection.
- Log Analysis: Understanding and analyzing security logs is crucial for identifying suspicious activity, tracking security events, and investigating security incidents.
- Threat Intelligence: Gathering and analyzing threat intelligence, including information on emerging threats, attack trends, and adversary tactics, is essential for staying ahead of attackers.
- Vulnerability Management: Identifying, prioritizing, and remediating vulnerabilities in systems and applications is crucial for reducing the attack surface and improving overall security posture.
Compliance and Governance
Ensuring compliance with relevant regulations and industry standards is crucial for maintaining a secure environment and managing risk.
- Security Policies and Standards: Establishing and enforcing clear security policies and standards, including access control, data handling, and incident response procedures, is essential for maintaining a secure environment.
- Compliance Audits: Regularly conducting compliance audits to assess adherence to security policies, regulations, and industry standards is essential for identifying gaps and improving security posture.
- Risk Management: Implementing a robust risk management framework to identify, assess, and mitigate security risks is crucial for making informed security decisions.
Developing Cybersecurity Skills
Embarking on a cybersecurity career path requires a strategic approach to skill development. A well-structured roadmap can guide individuals through the necessary steps, ensuring they acquire the knowledge and expertise needed to thrive in this dynamic field.
Roadmap for Cybersecurity Skills Development
A comprehensive roadmap for cybersecurity skills development should encompass various aspects, including foundational knowledge, practical experience, and continuous learning. This roadmap serves as a framework for individuals to prioritize their learning journey.
- Foundation in IT Fundamentals:A solid understanding of fundamental IT concepts is crucial. This includes networking, operating systems, programming, and databases. Individuals can acquire this knowledge through online courses, tutorials, and self-study resources.
- Cybersecurity Fundamentals:Building upon IT fundamentals, individuals should delve into the core principles of cybersecurity. This includes topics such as cryptography, risk management, security policies, and ethical hacking. Online courses, boot camps, and university programs offer comprehensive cybersecurity fundamentals training.
- Specialization:As individuals gain foundational knowledge, they can choose a specialization within cybersecurity. This could include areas like network security, application security, cloud security, or digital forensics. Specialization allows for in-depth knowledge and expertise in a specific area.
- Practical Experience:Hands-on experience is invaluable in cybersecurity. Individuals can gain practical experience through internships, volunteering opportunities, and personal projects.
- Certifications:Industry-recognized certifications validate cybersecurity skills and demonstrate expertise to potential employers. Popular certifications include CompTIA Security+, Certified Ethical Hacker (CEH), and Certified Information Systems Security Professional (CISSP).
- Continuous Learning:Cybersecurity is an ever-evolving field. Individuals must commit to continuous learning to stay abreast of emerging threats, technologies, and best practices.
Educational Resources and Training Programs
Numerous educational resources and training programs cater to individuals seeking to develop cybersecurity skills.
- Online Courses:Platforms like Coursera, Udemy, and edX offer a wide range of cybersecurity courses, from introductory to advanced levels. These courses are often taught by industry experts and provide flexible learning options.
- Boot Camps:Cybersecurity boot camps provide immersive and accelerated training programs, typically lasting a few weeks or months. These programs focus on practical skills and prepare individuals for entry-level cybersecurity roles.
- University Programs:Universities offer bachelor’s and master’s degrees in cybersecurity, providing a comprehensive education in the field. These programs cover theoretical concepts, practical skills, and research opportunities.
- Professional Organizations:Organizations like the Information Systems Audit and Control Association (ISACA) and the International Information Systems Security Certification Consortium (ISC)² offer training programs, certifications, and networking opportunities for cybersecurity professionals.
Hands-on Experience and Practical Projects
Hands-on experience is essential for developing practical cybersecurity skills.
- Capture the Flag (CTF) Competitions:CTF competitions simulate real-world cybersecurity scenarios, challenging participants to solve puzzles and exploit vulnerabilities. These competitions provide a valuable platform for learning and practicing cybersecurity skills.
- Personal Projects:Individuals can create their own cybersecurity projects, such as building a web application with security features or setting up a home network with security measures.
- Open Source Contributions:Contributing to open-source cybersecurity projects allows individuals to learn from experienced developers and contribute to real-world security solutions.
Cybersecurity Tools and Technologies
In the Infosec4TC domain, cybersecurity tools and technologies play a pivotal role in safeguarding sensitive data and systems. These tools provide a range of functionalities to detect, prevent, and respond to cybersecurity threats.
Popular Cybersecurity Tools and Technologies
The following table showcases some popular cybersecurity tools and technologies used in Infosec4TC:
| Tool/Technology | Description | Functionality |
|---|---|---|
| Intrusion Detection System (IDS) | An IDS monitors network traffic for suspicious activity and alerts administrators to potential threats. | Detects network intrusions, analyzes traffic patterns, generates alerts, and provides logs for investigation. |
| Intrusion Prevention System (IPS) | An IPS goes beyond detection and actively blocks malicious traffic based on predefined rules. | Identifies and blocks known threats, enforces security policies, and provides real-time protection. |
| Firewall | A firewall acts as a barrier between a network and external threats, controlling incoming and outgoing traffic. | Filters network traffic, blocks unauthorized access, enforces security policies, and protects against malicious attacks. |
| Antivirus Software | Antivirus software scans for and removes malware from devices, protecting against known threats. | Detects and removes viruses, worms, Trojans, and other malware, provides real-time protection, and updates signature databases. |
| Endpoint Detection and Response (EDR) | EDR solutions provide comprehensive visibility and control over endpoints, enabling threat detection and response. | Monitors endpoint activity, detects malicious behavior, provides incident response capabilities, and integrates with other security tools. |
| Security Information and Event Management (SIEM) | SIEM systems centralize security data from multiple sources, providing comprehensive threat analysis and incident response. | Collects and analyzes security logs, correlates events, identifies security incidents, and provides dashboards for threat intelligence. |
| Vulnerability Scanner | Vulnerability scanners identify security weaknesses in systems and applications, allowing for remediation. | Scans systems and applications for vulnerabilities, provides detailed reports, and recommends mitigation strategies. |
| Penetration Testing | Penetration testing simulates real-world attacks to identify security flaws and vulnerabilities. | Conducts simulated attacks, assesses security controls, identifies vulnerabilities, and provides recommendations for improvement. |
Advantages and Disadvantages of Using Different Tools
Each cybersecurity tool and technology has its own advantages and disadvantages, depending on the specific requirements and context.* Intrusion Detection Systems (IDS)
Advantages
Real-time threat detection, comprehensive network visibility, and proactive security monitoring.
Cybersecurity skills are in high demand, and Infosec4TC is a great resource for learning about the latest trends and best practices. But sometimes, after a long day of studying firewalls and encryption, you just need a creative outlet. Why not try making some DIY glitter photo frames to brighten up your workspace?
It’s a fun way to relax and de-stress, and it’s a great reminder that even in the world of cybersecurity, there’s always room for a little bit of sparkle.
Disadvantages
High false positive rates, limited ability to block threats, and potential performance impact.
Intrusion Prevention Systems (IPS)
Advantages
Cybersecurity skills are crucial in today’s digital world, and Infosec4TC offers excellent training to help you develop these skills. But while you’re learning to protect your data, don’t forget to take care of your physical well-being! Now’s a great time to kickstart your fitness tracking journey with a new Apple Watch this Prime Day, as the Series 9 reaches a new lowest price over the summer sales event.
After all, a healthy mind needs a healthy body to function at its best. So, get your cybersecurity skills in tip-top shape and invest in your health too!
Proactive threat prevention, reduced risk of security breaches, and improved network security.
Disadvantages
Potential for false positives, potential performance impact, and reliance on predefined rules.
Firewalls
Advantages
Effective control over network traffic, protection against unauthorized access, and enforcement of security policies.
Disadvantages
Potential for configuration errors, limited visibility into encrypted traffic, and reliance on static rules.
Antivirus Software
Advantages
Protection against known threats, real-time monitoring, and regular updates.
Cybersecurity skills are more crucial than ever, especially as the digital landscape evolves rapidly. The recent economic news, with Chinese stocks soaring after a stimulus blitz , highlights the interconnectedness of global markets. As technology advances, so do the threats, making cybersecurity professionals essential in navigating these complex and dynamic times.
Disadvantages
Limited protection against zero-day attacks, potential performance impact, and reliance on signature databases.
Endpoint Detection and Response (EDR)
Advantages
Comprehensive endpoint visibility, threat detection and response capabilities, and integration with other security tools.
Disadvantages
Potential for performance impact, reliance on data analysis, and complexity of implementation.
Security Information and Event Management (SIEM)
Advantages
Centralized security data, comprehensive threat analysis, and incident response capabilities.
Disadvantages
High complexity, data storage and management challenges, and potential for false positives.
Vulnerability Scanners
Advantages
Identification of security weaknesses, proactive remediation, and improved security posture.
Disadvantages
Potential for false positives, reliance on predefined vulnerabilities, and limited ability to assess complex vulnerabilities.
Penetration Testing
Advantages
Realistic assessment of security controls, identification of exploitable vulnerabilities, and actionable recommendations for improvement.
Disadvantages
High cost, potential for disruption to operations, and reliance on skilled penetration testers.
Emerging Trends in Cybersecurity
The cybersecurity landscape is constantly evolving, driven by technological advancements and the increasing sophistication of cyberattacks. Understanding emerging trends is crucial for organizations and individuals to stay ahead of the curve and protect themselves from evolving threats. This section explores some of the most significant trends shaping the future of cybersecurity.
The Impact of Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are transforming cybersecurity by automating tasks, improving threat detection, and enhancing response capabilities.
- Threat Detection and Prevention:AI-powered security tools can analyze vast amounts of data to identify suspicious patterns and anomalies that might indicate a cyberattack. These tools can also learn from past attacks and adapt to new threats, making them more effective at preventing future breaches.
- Security Operations Automation:AI can automate repetitive tasks such as incident response, vulnerability assessment, and log analysis, freeing up security professionals to focus on more strategic activities.
- Fraud Detection:AI is used in financial institutions to detect fraudulent transactions in real-time, protecting both customers and organizations from financial losses.
These technologies are not without their challenges. AI systems can be vulnerable to adversarial attacks, and the ethical implications of using AI in cybersecurity need careful consideration. Despite these challenges, AI and ML are poised to play an increasingly significant role in the future of cybersecurity.
The Rise of Blockchain Technology
Blockchain technology is known for its decentralized and tamper-proof nature, making it a potential game-changer in cybersecurity.
- Secure Data Storage and Management:Blockchain can be used to store sensitive data securely, ensuring its integrity and preventing unauthorized access.
- Identity and Access Management:Blockchain can be used to create secure digital identities, enabling organizations to better manage access to their systems and data.
- Secure Communication:Blockchain can be used to create secure communication channels, protecting data from interception and tampering.
Blockchain is still in its early stages of adoption in cybersecurity, but its potential for enhancing security is significant. As the technology matures, we can expect to see more innovative applications in this area.
The Growing Importance of Zero Trust Security
Zero trust security is a security model that assumes no user or device can be trusted by default. This approach requires organizations to verify every user and device before granting access to their systems and data.
- Increased Security Posture:Zero trust security reduces the attack surface by eliminating implicit trust, making it more difficult for attackers to gain access to sensitive information.
- Improved Visibility and Control:Zero trust security provides organizations with better visibility into their network traffic and user activity, enabling them to identify and respond to threats more effectively.
- Enhanced Compliance:Zero trust security can help organizations meet regulatory compliance requirements, such as those related to data privacy and security.
Zero trust security is a fundamental shift in security thinking, and it is becoming increasingly important as organizations adopt cloud computing and mobile devices.
The Increasing Threat of Insider Threats
Insider threats, malicious or negligent actions by authorized users, are becoming a growing concern for organizations.
- Data Breaches:Insider threats can lead to data breaches, exposing sensitive information to unauthorized parties.
- System Disruptions:Insider threats can disrupt critical business operations, causing significant financial losses.
- Reputation Damage:Insider threats can damage an organization’s reputation, leading to loss of customer trust and confidence.
Organizations need to implement robust security measures to mitigate the risk of insider threats, including employee training, access control, and data loss prevention technologies.
The Rise of Cybersecurity as a Service (SECaaS)
SECaaS provides organizations with access to cybersecurity solutions and expertise on a subscription basis.
- Cost-Effective Security:SECaaS can be more cost-effective than building and maintaining an in-house security team, especially for small and medium-sized businesses.
- Access to Expertise:SECaaS providers offer access to a wide range of security expertise and technologies, including threat intelligence, vulnerability management, and incident response.
- Scalability and Flexibility:SECaaS solutions can be scaled up or down as needed, providing organizations with the flexibility to adapt to changing security needs.
SECaaS is becoming increasingly popular as organizations seek to enhance their security posture without incurring significant upfront costs or hiring additional staff.
Career Paths in Cybersecurity: Cyber Security Skills Infosec4tc
The field of cybersecurity offers a diverse range of career paths, each with unique responsibilities, skills, and qualifications. From protecting critical infrastructure to safeguarding personal data, cybersecurity professionals play a vital role in ensuring the safety and security of our digital world.
Understanding the different career paths within the Infosec4TC domain can help individuals identify their niche and pursue their passions.
Cybersecurity Analyst
Cybersecurity analysts are responsible for identifying, assessing, and mitigating cybersecurity risks. They play a crucial role in protecting organizations from cyber threats by monitoring network traffic, analyzing security logs, and implementing security controls. The responsibilities of a cybersecurity analyst include:
- Monitoring security systems and logs for suspicious activity
- Conducting vulnerability assessments and penetration testing
- Developing and implementing security policies and procedures
- Responding to security incidents and breaches
- Collaborating with other IT professionals to ensure overall system security
Essential skills for a cybersecurity analyst include:
- Strong understanding of networking and security concepts
- Proficiency in security tools and technologies
- Analytical and problem-solving skills
- Excellent communication and reporting skills
- Ability to work independently and as part of a team
Qualifications typically include a bachelor’s degree in computer science, information technology, or a related field. Certifications such as Certified Information Systems Security Professional (CISSP) and CompTIA Security+ can enhance career prospects.