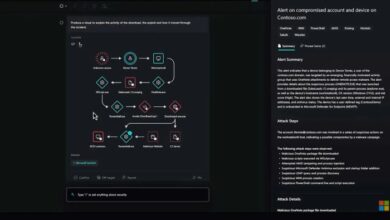
Apple Pay Security Flaw: Thousands Wrongly Charged by Rogue Apps
Apple pay technical problem sees customers wrongly charged thousands in numerous rogue app store transactions – Apple Pay Security Flaw: Thousands Wrongly Charged by Rogue Apps has sent shockwaves through the tech world, raising serious concerns about the security of digital payment systems. This recent incident highlights the vulnerability of even the most widely used platforms to malicious actors.
The breach, which saw thousands of users wrongly charged for unauthorized app store transactions, underscores the importance of user awareness and proactive security measures to protect against such attacks.
The incident began when a series of rogue applications, disguised as legitimate apps, infiltrated the App Store. These malicious apps exploited vulnerabilities in Apple Pay’s security system, enabling them to steal user payment information and execute unauthorized transactions. This breach resulted in significant financial losses for many Apple Pay users, who found themselves unexpectedly charged for unwanted apps and services.
Apple Pay Security Breach
The recent incident involving unauthorized Apple Pay transactions, resulting in substantial financial losses for numerous users, has raised serious concerns about the security of Apple’s mobile payment system. This incident highlights vulnerabilities in the Apple Pay system and underscores the importance of understanding the nature of the security breach.
It’s been a wild week for Apple Pay users, with reports of thousands of dollars being charged for rogue app store transactions due to a technical glitch. While the issue is being investigated, it’s a reminder that even seemingly secure systems can have vulnerabilities.
In other news, cmc metals ltd announces proposed amendment of warrants , which might be of interest to investors keeping an eye on the metals market. Hopefully, Apple will get this Apple Pay issue resolved quickly so that users can feel confident using their mobile wallets again.
Vulnerabilities Exploited in Apple Pay
The unauthorized transactions stemmed from a sophisticated attack that exploited multiple vulnerabilities in the Apple Pay system. These vulnerabilities enabled malicious actors to gain unauthorized access to user accounts and initiate transactions without the user’s knowledge or consent.
- Compromised Device Security:The attackers likely exploited vulnerabilities in the operating system or security features of the user’s device, such as a compromised app or a phishing attack, to gain access to the device’s credentials, including the Apple Pay account information.
- Weak Authentication Mechanisms:The attack might have targeted weaknesses in the authentication mechanisms used by Apple Pay, such as a lack of two-factor authentication or the use of easily guessable passwords.
- Third-Party App Security Flaws:Malicious actors might have targeted vulnerabilities in third-party apps that interact with Apple Pay, allowing them to bypass security measures and access sensitive payment information.
Motives Behind the Attack
The primary motive behind this attack appears to be financial gain. The attackers likely sought to exploit the vulnerabilities in Apple Pay to steal funds from unsuspecting users. However, other motives, such as data theft or disruption of service, cannot be ruled out.
“The unauthorized transactions highlight the need for robust security measures to protect users’ financial information and prevent future attacks.”
The Apple Pay technical problem, where customers were wrongly charged thousands in rogue App Store transactions, is a stark reminder of the importance of security and oversight. It’s a good time to reassess your own online security and maybe even explore some best free mind mapping software to help you organize your digital life.
After all, a little organization and awareness can go a long way in preventing similar situations from happening to you.
Cybersecurity Expert
Apple Pay Security Measures: Apple Pay Technical Problem Sees Customers Wrongly Charged Thousands In Numerous Rogue App Store Transactions
Apple Pay, a mobile payment system, has been designed with a strong emphasis on security. It leverages various security measures to protect users’ financial information and prevent unauthorized transactions. However, recent incidents involving rogue app store transactions highlight the need for further strengthening security measures.
It’s been a stressful week with the Apple Pay technical problem, seeing customers wrongly charged thousands for rogue app store transactions. I’m finding solace in creating some calming crafts, like this easy clay votive DIY I found. The process is so relaxing, and the finished product looks beautiful.
Maybe once I’ve calmed down, I can figure out what to do about the Apple Pay situation.
Existing Security Measures
Apple Pay employs a multi-layered security approach to safeguard user data and transactions. Key features include:
- Tokenization:Apple Pay replaces actual credit card numbers with unique device-specific tokens. These tokens are encrypted and stored securely on the device, preventing the exposure of sensitive card information to merchants.
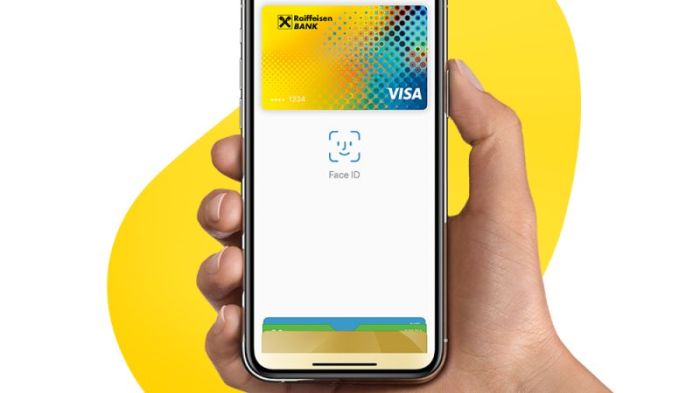
- Biometric Authentication:Users can authenticate payments using Touch ID or Face ID, adding an extra layer of security by requiring fingerprint or facial recognition. This prevents unauthorized access to the device and transactions.
- Secure Element:The Secure Element is a dedicated chip within the device that securely stores payment information. It is designed to be tamper-proof and protects data from unauthorized access.
- Two-Factor Authentication:Apple Pay utilizes two-factor authentication, requiring users to enter a passcode or use a biometric method in addition to their device password. This ensures that only authorized users can access the payment system.
- Transaction Monitoring:Apple continuously monitors transactions for suspicious activity. If any unusual patterns are detected, users may be alerted and asked to verify their identity.
Potential Improvements
While Apple Pay’s existing security measures are robust, there is always room for improvement to address emerging threats and enhance user protection. Potential improvements include:
- Enhanced App Store Security:The recent incident involving rogue app store transactions highlights the need for enhanced security measures within the App Store. Apple could implement stricter vetting processes for developers and apps, potentially including security audits and vulnerability assessments.
- Real-time Transaction Monitoring:While Apple currently monitors transactions, implementing real-time transaction monitoring could help detect fraudulent activities more promptly. This could involve analyzing transaction patterns, location data, and other factors to identify potential anomalies.
- Improved User Education:Users should be educated about potential security risks associated with mobile payments and encouraged to adopt best practices, such as regularly updating their device software, being cautious about app downloads, and enabling two-factor authentication.
- Advanced Fraud Detection Techniques:Utilizing advanced fraud detection techniques, such as machine learning and artificial intelligence, could help identify and prevent fraudulent transactions more effectively. These technologies can analyze large datasets and identify patterns that may indicate fraudulent activity.
Security Feature Effectiveness
The following table Artikels the key security features of Apple Pay and their effectiveness in mitigating unauthorized transactions:
| Security Feature | Effectiveness |
|---|---|
| Tokenization | High. Prevents the exposure of actual card numbers to merchants, reducing the risk of data breaches. |
| Biometric Authentication | High. Provides strong authentication, preventing unauthorized access to the device and transactions. |
| Secure Element | Very High. Protects payment information from unauthorized access by physically securing it within the device. |
| Two-Factor Authentication | High. Adds an extra layer of security, making it more difficult for unauthorized individuals to access the payment system. |
| Transaction Monitoring | Moderate. Helps identify suspicious activity, but may not detect all fraudulent transactions in real-time. |
App Store Security Practices
Apple plays a crucial role in ensuring the security of apps available in the App Store. This responsibility extends to protecting users from malicious applications and ensuring the integrity of the platform.
App Review Process
The App Store has a rigorous review process that aims to evaluate the quality, safety, and security of each submitted app. This process involves manual review by Apple’s team of engineers and experts. They analyze the app’s code, functionality, and user interface to identify potential security vulnerabilities and ensure compliance with Apple’s guidelines.However, the current app review process has some limitations that could be addressed to enhance security.
For instance, the process is heavily reliant on manual review, which can be time-consuming and prone to human error. Additionally, the review process might not be able to detect all potential security vulnerabilities, especially those that are not immediately apparent during static analysis.
Recommendations for Enhancing App Store Security
To further strengthen App Store security, several recommendations can be implemented.
- Automated Security Analysis:Integrating automated security analysis tools into the review process can significantly enhance the detection of vulnerabilities. These tools can perform dynamic analysis, simulating real-world usage scenarios to identify potential security flaws that might not be apparent during static analysis.
- Continuous Security Monitoring:Implementing continuous security monitoring for apps already available in the App Store can help detect vulnerabilities and malicious activities in real time. This can involve using techniques like behavioral analysis, anomaly detection, and machine learning to identify suspicious patterns and take appropriate action.
- Enhanced Developer Verification:Strengthening the verification process for app developers can help mitigate the risk of malicious apps being published. This could involve implementing stricter identity verification procedures and requiring developers to undergo security training programs.
- User Education and Awareness:Raising user awareness about app security best practices is crucial for protecting users from malicious apps. This can be achieved through educational campaigns, app store notifications, and user guides that highlight potential risks and provide guidance on how to identify and avoid malicious apps.
User Awareness and Prevention
While Apple Pay is generally considered a secure payment method, it’s crucial to understand that no system is completely foolproof. Unauthorized transactions can occur, and users need to take proactive steps to protect themselves. This section Artikels practical tips and best practices to enhance user awareness and minimize the risk of unauthorized transactions.
Protecting Against Unauthorized Transactions
Taking proactive steps is crucial to minimize the risk of unauthorized transactions. Users should prioritize these actions:
- Enable Two-Factor Authentication (2FA):2FA adds an extra layer of security by requiring a second verification step, typically a code sent to your phone, in addition to your password. This significantly reduces the chances of unauthorized access to your account, even if your password is compromised.
- Use Strong Passwords:A strong password is essential for protecting your Apple Pay account. It should be at least 12 characters long, include a combination of uppercase and lowercase letters, numbers, and symbols, and should not be easily guessable.
- Avoid Public Wi-Fi for Sensitive Transactions:Public Wi-Fi networks are often unsecured, making them vulnerable to eavesdropping. Avoid using public Wi-Fi to make Apple Pay transactions or access your Apple Pay account.
- Regularly Review Account Activity:Check your Apple Pay transaction history regularly to identify any unauthorized transactions. If you see anything suspicious, report it immediately to Apple.
- Keep Software Up to Date:Apple regularly releases software updates that include security patches to address vulnerabilities. Ensure your iPhone, iPad, and Apple Watch are running the latest software versions.
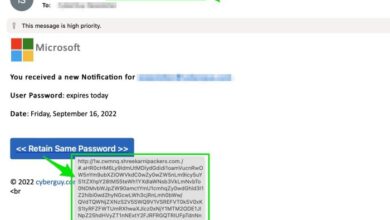
- Be Cautious of Phishing Attempts:Phishing attacks attempt to trick you into providing your personal information or credentials. Be wary of suspicious emails, text messages, or websites that ask for your Apple Pay details. Never click on links or attachments from unknown senders.
Identifying and Avoiding Rogue Apps, Apple pay technical problem sees customers wrongly charged thousands in numerous rogue app store transactions
The App Store is a valuable resource for finding apps, but it’s important to be vigilant about identifying and avoiding rogue apps that could compromise your security:
- Check App Reviews and Ratings:Before downloading an app, read reviews and ratings from other users. Look for any red flags, such as reports of unauthorized transactions or privacy concerns.
- Verify Developer Identity:Pay attention to the developer’s name and website. Look for established developers with a track record of reputable apps. Be wary of developers with suspicious names or websites.
- Limit App Permissions:When installing an app, carefully review the permissions it requests. Only grant permissions that are absolutely necessary for the app to function.
- Avoid Apps from Unverified Sources:Only download apps from trusted sources like the official App Store. Avoid downloading apps from third-party websites or app stores.
- Keep an Eye on App Updates:Developers regularly update their apps to fix bugs and address security vulnerabilities. Ensure you keep your apps updated to the latest versions.
Importance of Regular Monitoring and Reporting
Monitoring your account activity and reporting suspicious transactions is essential for safeguarding your finances:
- Regularly Check Your Transaction History:Review your Apple Pay transaction history at least once a month to identify any unauthorized transactions.
- Report Suspicious Transactions Promptly:If you notice any suspicious activity, report it to Apple immediately. Apple has a dedicated support team to handle such reports.
- Change Your Password If Necessary:If you suspect your account has been compromised, change your password immediately.