Black Hat CrowdStrike Threat Hunting: A Deep Dive
Black Hat CrowdStrike Threat Hunting: It sounds like something out of a spy thriller, right? But the reality is that cybercrime is a serious threat, and organizations are constantly looking for ways to stay ahead of the bad guys.
CrowdStrike is a leading cybersecurity company that provides a range of solutions to help businesses protect themselves from attacks, and their threat hunting capabilities are a crucial part of that strategy.
Think of it like this: CrowdStrike’s threat hunters are like cybersecurity detectives. They use their expertise and cutting-edge tools to sift through massive amounts of data, searching for signs of malicious activity. They’re not just waiting for attacks to happen; they’re actively seeking them out before they can cause damage.
Black Hat Tactics and CrowdStrike Threat Hunting

In the ever-evolving landscape of cybersecurity, black hat actors employ a range of sophisticated tactics to compromise systems and steal sensitive data. CrowdStrike, a leading cybersecurity company, offers a comprehensive suite of threat hunting capabilities to proactively identify and prevent these attacks.
This article explores common black hat tactics, how CrowdStrike’s solutions can effectively counter them, and provides real-world examples of successful mitigations.
Malware Distribution
Malware distribution is a primary method used by black hat actors to infiltrate systems. This involves spreading malicious software, such as viruses, ransomware, and spyware, through various channels.
- Email attachments:Malicious files are often disguised as legitimate documents or attachments in phishing emails, tricking unsuspecting users into opening them.
- Exploit kits:These kits exploit vulnerabilities in software to automatically install malware on compromised systems without user interaction.
- Drive-by downloads:Users can unknowingly download malware by visiting compromised websites or clicking on malicious links.
- Software vulnerabilities:Attackers exploit known software vulnerabilities to gain unauthorized access and install malware.
CrowdStrike’s Falcon platform utilizes advanced endpoint detection and response (EDR) capabilities to detect and prevent malware distribution. Its real-time monitoring, behavioral analysis, and machine learning algorithms identify suspicious activities and block malicious payloads.
CrowdStrike’s Falcon platform leverages a unique “sensorless” architecture, enabling it to monitor and protect endpoints without requiring the installation of agents on every device.
This eliminates the risk of malware tampering with the agent, ensuring continuous and effective protection.
Phishing
Phishing is a common social engineering tactic used to trick users into revealing sensitive information, such as login credentials, credit card details, or personal data.
- Spear phishing:Highly targeted emails that impersonate legitimate organizations or individuals, often containing personalized information to increase credibility.
- Whaling:Phishing attacks specifically targeting high-profile executives or senior management, aiming to exploit their authority and access sensitive information.
- Smishing:Phishing attacks conducted via SMS messages, often mimicking legitimate organizations or services to steal personal data.
CrowdStrike’s Falcon platform incorporates advanced threat intelligence and anti-phishing capabilities to detect and prevent phishing attacks. It analyzes email content, URL patterns, and sender reputation to identify suspicious emails and block malicious links.
Social Engineering, Black hat crowdstrike threat hunting
Social engineering involves manipulating individuals into performing actions that compromise their security or reveal sensitive information.
- Pretexting:Attackers create a false scenario to gain access to information or systems by impersonating someone with authority or using fabricated information.
- Baiting:Attackers offer enticing rewards or incentives to lure users into clicking on malicious links or downloading infected files.
- Scareware:Attackers use scare tactics, such as fake security warnings or malware alerts, to pressure users into installing malicious software.
CrowdStrike’s Falcon platform incorporates user behavior analysis and security awareness training to mitigate social engineering attacks. It monitors user activities, detects unusual patterns, and provides real-time alerts to prevent malicious actions.
Exploit Kits
Exploit kits are automated tools used by attackers to exploit vulnerabilities in software, such as web browsers, operating systems, and applications.
Black hat threat hunting is a dangerous game, and CrowdStrike is a force to be reckoned with. They’re constantly on the lookout for new ways to exploit vulnerabilities, and one area they’re particularly interested in is cloud misconfigurations. A recent study research eyes misconfiguration issues at google amazon and microsoft cloud found that many organizations are leaving their cloud environments open to attack, and CrowdStrike is sure to be taking advantage of these weaknesses.
It’s a constant battle, but CrowdStrike is determined to stay ahead of the black hats.
- Zero-day exploits:Attackers exploit previously unknown vulnerabilities in software before patches are available, giving them an advantage over security solutions.
- Drive-by downloads:Users can unknowingly download malware by visiting compromised websites or clicking on malicious links.
- Malvertising:Attackers use malicious advertisements on legitimate websites to redirect users to compromised sites or deliver malware.
CrowdStrike’s Falcon platform utilizes advanced threat intelligence, vulnerability scanning, and patching capabilities to detect and prevent exploit kits. It identifies known vulnerabilities, patches software in real-time, and blocks malicious websites and advertisements.
Black hat threat hunting is a dangerous game, and CrowdStrike is a formidable opponent. They’re constantly innovating to stay ahead of the curve, and their AI-powered tools are truly impressive. To counter their efforts, we need to be just as smart, and that’s where apple intelligence 5 ai powered things you should do immediately comes in.
By staying on top of the latest AI advancements, we can develop new strategies to outsmart CrowdStrike and protect our systems. The battle for cybersecurity is a constant race, and we need to be prepared for whatever comes next.
Real-World Examples
CrowdStrike has successfully mitigated numerous real-world black hat attacks, demonstrating the effectiveness of its solutions.
- The NotPetya ransomware attack:In 2017, NotPetya, a destructive ransomware attack, targeted businesses worldwide, causing billions of dollars in damages. CrowdStrike’s Falcon platform detected and blocked the attack, preventing widespread disruption and data loss for many organizations.
- The WannaCry ransomware attack:In 2017, WannaCry, another devastating ransomware attack, exploited a vulnerability in Microsoft Windows to encrypt data and demand ransom payments. CrowdStrike’s Falcon platform detected and prevented the attack, protecting numerous organizations from falling victim to this threat.
- The SolarWinds hack:In 2020, the SolarWinds hack involved the compromise of the SolarWinds Orion software, allowing attackers to gain access to numerous government and private sector organizations. CrowdStrike’s Falcon platform identified suspicious activities and helped organizations detect and contain the attack.
CrowdStrike’s proactive threat hunting capabilities, combined with its advanced endpoint protection solutions, play a crucial role in mitigating black hat attacks and safeguarding organizations from cyber threats.
The Threat Landscape and CrowdStrike’s Role
The cyber threat landscape is constantly evolving, becoming more sophisticated and aggressive. Attackers are leveraging advanced techniques, exploiting vulnerabilities, and targeting organizations of all sizes. CrowdStrike plays a critical role in helping organizations understand and mitigate these threats.
CrowdStrike’s Threat Intelligence and Research
CrowdStrike’s threat intelligence and research teams are dedicated to analyzing the latest threats and providing actionable insights to customers. They use a combination of data analysis, machine learning, and human expertise to stay ahead of the curve. This intelligence is essential for organizations to proactively identify and respond to emerging threats.
CrowdStrike’s Technology and Services
CrowdStrike offers a comprehensive suite of security solutions designed to protect organizations from a wide range of threats. These solutions include:
- Endpoint Protection and Response (EDR):CrowdStrike’s EDR platform provides real-time visibility into endpoint activity, enabling rapid detection and response to threats. It leverages cloud-native architecture, machine learning, and threat intelligence to identify and stop attacks.
- Threat Intelligence:CrowdStrike’s threat intelligence platform provides access to a vast database of threat indicators, including malware signatures, attack patterns, and adversary tactics. This intelligence helps organizations proactively identify and mitigate threats.
- Managed Detection and Response (MDR):CrowdStrike’s MDR service provides 24/7 threat hunting and incident response capabilities, allowing organizations to focus on their core business while CrowdStrike experts handle security operations.
Emerging Trends in Black Hat Activity
Attackers are constantly evolving their tactics and techniques. Some of the emerging trends in black hat activity include:
- Ransomware:Ransomware attacks are becoming increasingly common and sophisticated. Attackers are using advanced techniques to encrypt data and demand large ransoms for its release. A recent example is the REvil ransomware attack, which targeted a major meatpacking company, disrupting supply chains and causing significant financial losses.
- Supply Chain Attacks:Attackers are targeting supply chains to compromise software or hardware used by organizations. By targeting software vendors or hardware manufacturers, attackers can gain access to a large number of organizations. A notable example is the SolarWinds attack, where attackers compromised software updates from SolarWinds, gaining access to numerous government agencies and private companies.
- Zero-Day Exploits:Attackers are exploiting zero-day vulnerabilities, which are software flaws that are unknown to vendors and haven’t been patched. These exploits allow attackers to bypass security measures and gain unauthorized access to systems. The recent Log4j vulnerability, which affected a widely used Java logging library, is a prime example of a zero-day exploit that was quickly exploited by attackers.
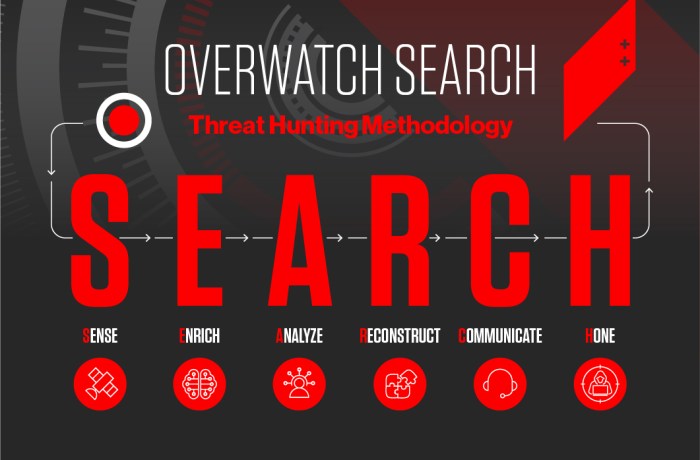
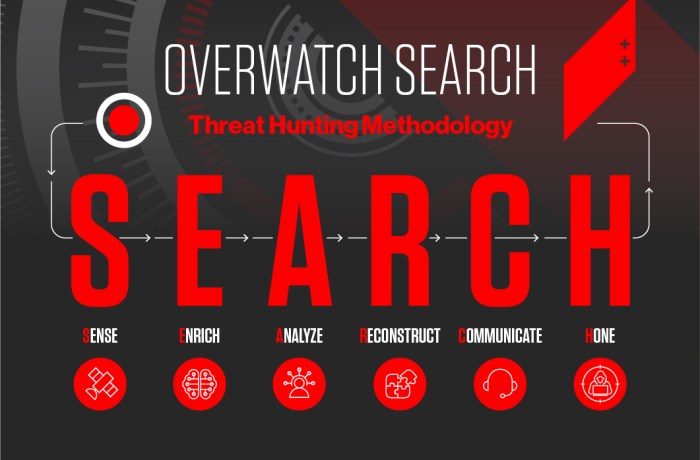
CrowdStrike’s Threat Hunting Methodology: Black Hat Crowdstrike Threat Hunting
CrowdStrike’s threat hunting methodology is a proactive approach to cybersecurity that focuses on identifying and mitigating threats before they can cause significant damage. This approach involves a systematic process of data collection, analysis, and response, leveraging advanced technologies and expertise to uncover hidden threats and vulnerabilities.
Black hat CrowdStrike threat hunting is a serious business, requiring a deep understanding of attacker tactics and the ability to think like an adversary. It’s like a game of chess, but instead of pawns and knights, we’re dealing with malware and exploits.
And just like Netflix is ditching support for older Apple TV streaming boxes upgrade before the next binge-worthy show premieres , we need to constantly adapt and evolve our techniques to stay ahead of the ever-changing threat landscape. Staying ahead of the curve in this field is crucial, as a single misstep can have devastating consequences.
Data Collection
CrowdStrike’s threat hunting methodology begins with the collection of vast amounts of data from various sources. This data includes endpoint activity logs, network traffic, and threat intelligence feeds.
- Endpoint activity logsprovide detailed information about the behavior of devices on a network, including file access, process execution, and network connections.
- Network traffic analysishelps identify suspicious patterns and anomalies in network communication, which can indicate malicious activity.
- Threat intelligence feedsprovide real-time information about known threats, including malware, phishing campaigns, and attack techniques.
Data Analysis
Once the data is collected, CrowdStrike analysts use advanced tools and techniques to analyze it for signs of malicious activity. This analysis involves identifying patterns, anomalies, and suspicious behaviors that may indicate a threat.
- Behavioral analysisexamines the actions of endpoints and users to identify deviations from normal patterns.
- Threat intelligence correlationcompares collected data against known threat indicators to identify potential matches.
- Machine learning algorithmsare used to automatically detect and classify threats based on learned patterns and anomalies.
Threat Response
When a threat is identified, CrowdStrike’s threat hunting team takes immediate action to mitigate the threat and prevent further damage.
- Incident responseinvolves containing the threat, investigating its impact, and recovering compromised systems.
- Threat remediationincludes removing malicious software, patching vulnerabilities, and implementing security controls to prevent future attacks.
- Continuous monitoringensures that the threat is fully contained and that no further malicious activity is occurring.
Tools and Technologies
CrowdStrike leverages a suite of tools and technologies to support its threat hunting methodology.
- Falcon platformis a cloud-native endpoint protection and response (EDR) platform that provides comprehensive visibility into endpoint activity and enables real-time threat detection and response.
- CrowdStrike Threat Graphis a global threat intelligence database that contains information on millions of threats and attackers, enabling analysts to identify and correlate threats across different organizations.
- CrowdStrike OverWatchis a managed threat hunting service that provides 24/7 threat hunting and incident response capabilities.
CrowdStrike’s Approach to Threat Hunting
CrowdStrike’s threat hunting methodology differs from traditional security methods in several key ways:
- Proactive approach: CrowdStrike focuses on identifying threats before they can cause damage, rather than simply reacting to incidents after they occur.
- Data-driven approach: CrowdStrike relies heavily on data analysis to identify and mitigate threats, leveraging advanced tools and techniques to analyze large volumes of data.
- Threat intelligence integration: CrowdStrike uses threat intelligence feeds to stay ahead of emerging threats and identify potential attacks.
- Automation and machine learning: CrowdStrike utilizes automation and machine learning to streamline threat hunting processes and improve efficiency.
Case Studies and Success Stories

CrowdStrike’s threat hunting capabilities have proven invaluable in helping organizations prevent and mitigate black hat attacks. By leveraging advanced technology and expert analysts, CrowdStrike has achieved remarkable results in safeguarding businesses from sophisticated cyber threats. This section will delve into real-world case studies showcasing how CrowdStrike’s solutions have made a tangible difference in organizations’ security posture and their ability to respond to incidents.
Real-World Examples of CrowdStrike’s Impact
The following table presents various case studies, highlighting the specific black hat tactics used, CrowdStrike’s response, and the outcome.
| Case Study | Black Hat Tactics | CrowdStrike’s Response | Outcome |
|---|---|---|---|
| Financial Institution | Malware infection through phishing email, aiming to steal customer data | CrowdStrike Falcon platform detected the malware and alerted the security team. Threat hunters investigated the incident and identified the compromised systems. | The attack was successfully contained, preventing data theft and financial losses. |
| Healthcare Provider | Ransomware attack targeting patient records | CrowdStrike’s EDR solution detected the ransomware activity and blocked its execution. Threat hunters analyzed the attack and provided insights for remediation. | The ransomware attack was thwarted, protecting sensitive patient information from encryption and extortion. |
| Manufacturing Company | Advanced persistent threat (APT) attempting to steal intellectual property | CrowdStrike’s threat hunting team identified the APT activity and traced its origins to a known nation-state actor. The team provided detailed intelligence and recommendations for mitigation. | The APT attack was neutralized, preventing the theft of valuable intellectual property. |
CrowdStrike’s Impact on Security Posture
CrowdStrike’s solutions have significantly improved organizations’ security posture by:* Proactive Threat Hunting:CrowdStrike’s threat hunting teams proactively search for and identify threats that may have evaded traditional security controls. This proactive approach helps organizations stay ahead of attackers and prevent breaches before they occur.
Rapid Incident Response
CrowdStrike’s EDR solution provides real-time visibility into endpoint activity, enabling security teams to detect and respond to threats quickly. This rapid response capability minimizes the impact of attacks and reduces recovery time.
Improved Security Posture
By identifying and mitigating threats before they cause harm, CrowdStrike helps organizations strengthen their security posture and reduce their overall risk.
CrowdStrike’s Role in Incident Response
CrowdStrike plays a critical role in incident response by:* Providing Real-Time Visibility:CrowdStrike’s EDR solution provides security teams with a comprehensive view of endpoint activity, allowing them to track the attacker’s actions and understand the scope of the attack.
Analyzing Attack Techniques
CrowdStrike’s threat hunters analyze the attack techniques used by the attackers, identifying the malware, tools, and tactics employed. This analysis helps organizations improve their defenses against future attacks.
Remediation and Recovery
CrowdStrike provides guidance and support to organizations during the remediation and recovery process, ensuring that the affected systems are restored to a secure state.
The Future of Black Hat Threat Hunting
The world of cybersecurity is in a constant state of flux, with adversaries constantly evolving their tactics and techniques. To effectively combat these evolving threats, CrowdStrike is committed to staying ahead of the curve by anticipating future black hat trends and developing innovative solutions.
This involves analyzing the latest attack vectors, understanding the motivations behind malicious activities, and leveraging cutting-edge technologies to enhance threat hunting capabilities.
The Role of Artificial Intelligence and Machine Learning in Threat Hunting
Artificial intelligence (AI) and machine learning (ML) are playing an increasingly significant role in modern threat hunting. CrowdStrike is actively incorporating these technologies to enhance its ability to detect and respond to threats. AI and ML algorithms can analyze vast amounts of data, identify patterns, and predict potential threats, enabling proactive threat hunting.
- Automated Threat Detection:AI-powered systems can analyze network traffic, system logs, and other data sources to identify suspicious activities and potential attacks. This automation frees up security analysts to focus on more complex investigations.
- Behavioral Analysis:ML algorithms can learn normal user behavior patterns and identify deviations that could indicate malicious activity. This enables the detection of zero-day attacks and other threats that may not have known signatures.
- Threat Intelligence Integration:AI and ML can be used to correlate threat intelligence data from various sources, providing a comprehensive understanding of the threat landscape and enabling more effective threat hunting.
CrowdStrike’s Evolving Threat Hunting Capabilities
CrowdStrike’s threat hunting capabilities are constantly evolving to stay ahead of the ever-changing threat landscape. This involves continuous innovation, research, and development, ensuring that CrowdStrike’s solutions remain effective against emerging threats.
- Advanced Threat Detection and Response:CrowdStrike is developing new techniques and technologies to detect and respond to advanced threats, such as those using sophisticated evasion tactics and exploiting vulnerabilities in complex environments.
- Threat Intelligence Sharing:CrowdStrike actively shares threat intelligence with its customers and the broader security community, fostering collaboration and enhancing collective defense against emerging threats.
- Proactive Threat Hunting:CrowdStrike’s threat hunting teams actively search for and investigate potential threats before they can cause harm. This proactive approach is crucial for staying ahead of adversaries and preventing attacks.







