Cybersecurity
-

Censys Research: Uncovering Open Directory Vulnerabilities
Censys research open directories delve into the world of online security, exposing vulnerabilities that can leave organizations vulnerable to data…
Read More » -

Critical National Infrastructure Email Security: A Vital Defense
Critical national infrastructure email security is a critical concern in today’s interconnected world. From power grids to transportation systems, these…
Read More » -
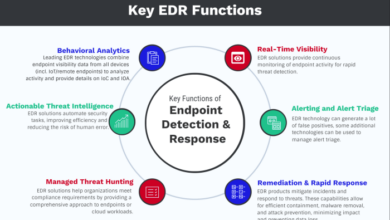
Endpoint Security Tools Report: A Comprehensive Guide
Endpoint security tools report is a must-read for anyone concerned about safeguarding their digital assets. In today’s interconnected world, endpoint…
Read More » -

Cisco Talos Year-End Report: Cybersecurity Insights
Cisco talos year end report – The Cisco Talos Year-End Report provides a comprehensive look at the cybersecurity landscape, analyzing…
Read More » -

Microsoft Cyber Attacks UK AI: A Threat to National Security
Microsoft Cyber Attacks UK AI: A Threat to National Security – Imagine a world where critical infrastructure, from power grids…
Read More » -

Tenable Research: 26,500 Cyber Vulnerabilities Threaten Southeast Asian Banks
Tenable research 26500 cyber vulnerabilities risk se asia banks – Tenable Research: 26,500 Cyber Vulnerabilities Threaten Southeast Asian Banks. This…
Read More » -

ASEAN Cybersecurity Trends: Jason Steer Interview
Asean cybersecurity trends jason steer interview – ASEAN Cybersecurity Trends: Jason Steer Interview – In an increasingly interconnected world, cybersecurity…
Read More » -

Checkpoint Hackers: USB Drives as a Gateway
Check point hackers usb – Checkpoint Hackers: USB Drives as a Gateway – The world of cybersecurity is constantly evolving,…
Read More » -
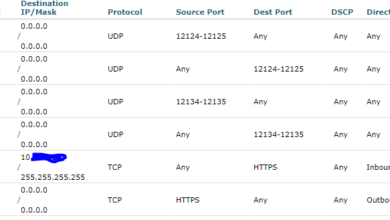
Cisco Talos Windows Policy Loophole: A Security Risk
Cisco Talos Windows Policy Loophole, a critical vulnerability, has recently emerged, posing a significant threat to Windows users and organizations…
Read More » -

Zero Day MoveIt Vulnerability: A Critical Threat
Zero Day MoveIt Vulnerability: a name that strikes fear into the hearts of cybersecurity professionals and businesses alike. This critical…
Read More »


