Data Recovery: Defending Against Data Breaches with Rubrik
Data recovery data breaches rubrik takes center stage in today’s digital landscape, where the threat of data breaches looms large. Organizations are constantly striving to protect their sensitive information from malicious actors, and data recovery plays a crucial role in mitigating the impact of a successful attack.
Rubrik, a leading data recovery platform, offers a comprehensive solution for organizations looking to recover data quickly and efficiently after a breach.
This blog post will delve into the importance of data recovery in the context of data breaches, explore the features and benefits of Rubrik, and discuss how it can help organizations minimize downtime and data loss. We’ll also examine the future of data recovery and the role of Rubrik in addressing emerging threats.
Data Recovery in the Context of Data Breaches: Data Recovery Data Breaches Rubrik

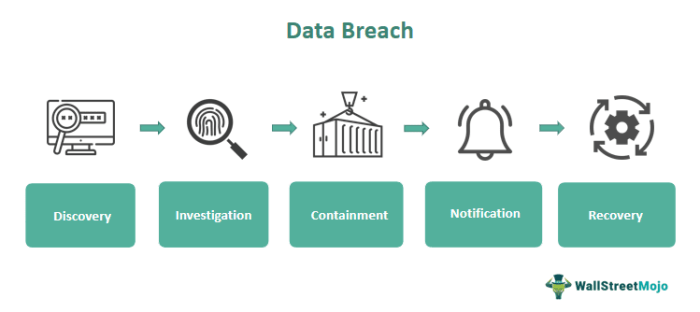
In today’s digital landscape, data breaches are a growing concern for organizations of all sizes. The consequences of a data breach can be severe, including financial losses, reputational damage, and legal liabilities. In the aftermath of a breach, data recovery becomes crucial to minimize the impact and restore normal operations.Data recovery is the process of retrieving lost or inaccessible data from storage devices, including servers, databases, and backups.
In the context of a data breach, data recovery plays a vital role in mitigating the damage and restoring the organization’s critical data.
Types of Data Breaches and Their Impact
Data breaches can occur through various means, each with its unique impact on an organization.
- Malware Attacks:These attacks involve malicious software that can steal, encrypt, or delete data. Examples include ransomware attacks, where attackers encrypt data and demand payment for decryption.
- Phishing Attacks:These attacks use deceptive emails or messages to trick users into revealing sensitive information, such as login credentials or financial data.
- Insider Threats:These breaches involve unauthorized access or misuse of data by employees or contractors. This can occur through negligence, malicious intent, or accidental data leaks.
- Data Leakage:This refers to the unintentional or unauthorized disclosure of sensitive data, such as through misconfigured cloud storage or accidental sharing of confidential files.
The impact of a data breach can be far-reaching, including:
- Financial Losses:Organizations may incur costs associated with incident response, data recovery, legal fees, and regulatory fines.
- Reputational Damage:A data breach can damage an organization’s reputation, leading to loss of customer trust and confidence.
- Legal Liabilities:Organizations may face legal actions from affected individuals or regulatory bodies.
- Business Disruption:Data breaches can disrupt business operations, leading to downtime and lost productivity.
Real-World Data Breaches and Data Recovery Efforts
Numerous real-world data breaches have highlighted the importance of data recovery.
“In 2017, Equifax, a credit reporting agency, suffered a massive data breach that exposed the personal information of over 147 million individuals. The breach resulted in significant financial losses, regulatory fines, and reputational damage. Equifax implemented a data recovery plan to restore the affected data and prevent future breaches.”
“In 2020, SolarWinds, a software company, was targeted by a sophisticated supply chain attack that compromised its software updates. This attack allowed hackers to access the networks of numerous organizations, including government agencies and businesses. Data recovery efforts involved identifying the compromised systems, removing the malware, and restoring data from backups.”
These examples demonstrate the critical role of data recovery in mitigating the impact of data breaches and restoring normal operations.
Data recovery is a crucial aspect of cybersecurity, especially when dealing with data breaches. Companies like Rubrik specialize in data protection and recovery solutions, ensuring businesses can bounce back from attacks. Speaking of leaks, it seems a new version of the Beats Solo headphones just got accidentally revealed in the latest version of iOS – you can check it out here: a new version of the beats solo headphones just got accidentally revealed in the latest version of ios.
While this might be a fun tech leak, it underscores the importance of data security, which Rubrik and other companies work tirelessly to protect.
Rubrik
Rubrik is a data recovery platform that helps organizations protect their data from a variety of threats, including data breaches. It’s a comprehensive solution that provides backup, recovery, and data management capabilities. Rubrik’s technology is designed to make data recovery fast and efficient, even in the event of a major incident.
Rubrik’s Key Features
Rubrik offers a range of features that contribute to its effectiveness as a data recovery solution. Here are some of its key capabilities:
- Instant Recovery:Rubrik enables near-instant recovery of data, minimizing downtime and disruption to business operations. This is achieved through its ability to create and maintain immutable snapshots of data, allowing for rapid restoration.
- Air Gap Protection:Rubrik offers air-gapped backups, meaning that copies of data are stored offline and physically isolated from the network. This provides an additional layer of protection against ransomware attacks and other threats that can compromise online data.
- Data Deduplication and Compression:Rubrik leverages data deduplication and compression techniques to optimize storage space and reduce backup and recovery times. This is particularly valuable for organizations with large data sets.
- Cloud Integration:Rubrik seamlessly integrates with major cloud providers, enabling organizations to leverage the cloud for backup, recovery, and data management purposes. This provides flexibility and scalability for data protection.
How Rubrik Helps Organizations Recover from Data Breaches
Rubrik’s technology is designed to help organizations recover from data breaches quickly and efficiently. Here’s how it works:
- Rapid Data Restoration:In the event of a data breach, Rubrik allows organizations to restore data from a clean, immutable snapshot that predates the breach. This ensures that the restored data is free from any malicious modifications or deletions.
- Automated Recovery Processes:Rubrik automates the data recovery process, simplifying the task for IT teams and minimizing the risk of human error. This is crucial in a crisis situation where time is of the essence.
- Security and Compliance:Rubrik helps organizations meet security and compliance requirements by providing features such as data encryption, access control, and auditing. This helps to protect sensitive data and ensure compliance with regulations.
Case Study: A Financial Institution’s Successful Recovery
A large financial institution experienced a ransomware attack that encrypted critical data on their servers. The attack caused significant disruption to their operations, and they were unable to access their data. Fortunately, the institution had implemented Rubrik for data protection.
Using Rubrik, they were able to recover their data from a clean snapshot that predated the attack. This allowed them to restore their systems and resume operations within a few hours.The institution’s successful recovery demonstrates the power of Rubrik in helping organizations overcome data breaches.
Rubrik’s ability to provide rapid data restoration, automated recovery processes, and strong security measures made it possible for the institution to minimize the impact of the attack and quickly restore their operations.
Data Recovery Strategies with Rubrik
Rubrik provides a comprehensive suite of data recovery strategies designed to minimize downtime and data loss in the event of a data breach or other disaster. These strategies leverage Rubrik’s powerful data protection capabilities, enabling organizations to quickly recover critical data and restore operations.
Data recovery is a crucial aspect of cybersecurity, especially in the wake of data breaches. Tools like Rubrik are essential for ensuring data integrity and swift recovery. But vulnerabilities like the one found in the blastradius vulnerability radius protocol highlight the importance of proactive security measures.
By understanding these vulnerabilities, we can better protect our data and systems from potential breaches, ultimately strengthening our data recovery strategies.
Data Recovery Options with Rubrik
Rubrik offers several data recovery options, each tailored to different recovery scenarios and needs.
- Instant Recovery:This option allows for immediate recovery of data from Rubrik’s local or cloud-based storage. This is ideal for recovering individual files or applications quickly, minimizing downtime.
- Recovery to a New Location:This strategy allows for data recovery to a new location, such as a different data center or cloud environment. This is useful for disaster recovery scenarios or when migrating to a new infrastructure.
- Recovery to a Previous Point in Time:This option enables organizations to restore data to a specific point in time, effectively reversing the impact of a data breach or accidental data deletion. Rubrik’s granular recovery capabilities allow users to restore individual files or entire systems to a specific point in time.
Rubrik’s Data Recovery Features for Minimizing Downtime and Data Loss
Rubrik’s data recovery features are designed to minimize downtime and data loss during a data breach.
- Fast Recovery Times:Rubrik’s instant recovery capabilities allow for rapid data restoration, minimizing the impact of a data breach on business operations.
- Automated Recovery:Rubrik’s automation features streamline the recovery process, reducing the need for manual intervention and minimizing the risk of human error.
- Comprehensive Data Protection:Rubrik’s data protection capabilities extend beyond backups, including data replication, immutability, and ransomware protection, ensuring data integrity and availability even in the face of a data breach.
Comparison of Rubrik’s Data Recovery Strategies with Other Solutions
Compared to traditional backup and recovery solutions, Rubrik offers several advantages in terms of data recovery:
- Faster Recovery Times:Rubrik’s instant recovery capabilities are significantly faster than traditional backup and recovery solutions, which often involve lengthy restore processes.
- Simplified Management:Rubrik’s intuitive interface and automation features simplify data recovery management, reducing the need for specialized skills and expertise.
- Enhanced Data Protection:Rubrik’s data protection capabilities, including immutability and ransomware protection, provide a higher level of data security compared to traditional backup solutions.
Data Protection and Security with Rubrik
Data protection and security are paramount in today’s digital landscape, where cyber threats are constantly evolving. Organizations need robust solutions to safeguard their valuable data from breaches, ransomware attacks, and other vulnerabilities. Rubrik, a leading data management and protection platform, offers a comprehensive approach to data protection and security, enabling organizations to achieve their security goals and maintain data integrity.
Encryption
Rubrik utilizes advanced encryption techniques to protect data at rest and in transit, ensuring that sensitive information is always secure.
Data recovery is a critical aspect of cybersecurity, especially in the face of data breaches. Robust solutions like Rubrik are essential for mitigating the impact of such incidents. It’s interesting to note that Google Domains, a platform for domain registration, has recently been acquired by Squarespace, as reported in this article.
This acquisition could have implications for data recovery strategies as well, potentially leading to new integrations and services for website owners.
- Data at rest encryption:Rubrik encrypts data stored on its appliances and in the cloud using industry-standard AES-256 encryption. This ensures that even if the physical storage devices are compromised, the data remains inaccessible to unauthorized individuals.
- Data in transit encryption:Rubrik encrypts data transmitted between its appliances and the cloud using TLS/SSL protocols, preventing eavesdropping and data interception during network transfers.
Access Control
Rubrik implements robust access control mechanisms to restrict unauthorized access to data and ensure that only authorized personnel can access and manage sensitive information.
- Role-based access control (RBAC):Rubrik allows administrators to define roles with specific permissions, ensuring that users can only access the data and perform the actions authorized for their roles.
- Multi-factor authentication (MFA):Rubrik supports MFA, requiring users to provide multiple forms of authentication before gaining access to sensitive data, enhancing security and preventing unauthorized access.
Data Privacy Compliance
Rubrik helps organizations comply with various data privacy regulations, such as GDPR and HIPAA, by providing features and functionalities that ensure data security and privacy.
- Data retention policies:Rubrik allows organizations to define data retention policies that comply with regulatory requirements, ensuring that data is retained for the appropriate duration and then securely deleted.
- Data masking and anonymization:Rubrik offers data masking and anonymization features that can be used to protect sensitive data by replacing it with non-sensitive values, allowing for data analysis and testing without compromising privacy.
- Data sovereignty:Rubrik supports data sovereignty by allowing organizations to store their data in specific regions, ensuring compliance with local data privacy regulations.
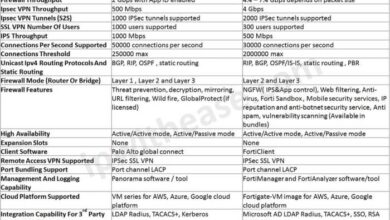
Integration and Deployment of Rubrik
Rubrik seamlessly integrates with various IT systems and environments, simplifying data protection and recovery processes. This integration allows Rubrik to effectively manage data across different platforms and applications, enhancing its overall efficiency and effectiveness.
Integration with IT Systems and Environments
Rubrik’s integration capabilities enable it to work harmoniously with diverse IT systems and environments, streamlining data protection and recovery operations. Rubrik integrates with popular cloud platforms like AWS, Azure, and Google Cloud, allowing users to protect and recover data stored in these environments.
This integration provides a unified platform for managing data across on-premises and cloud infrastructure. Rubrik integrates with various virtualization platforms, including VMware, Hyper-V, and Nutanix, enabling protection and recovery of virtual machines and their associated data. Rubrik supports various operating systems, including Windows, Linux, and macOS, allowing for comprehensive data protection across different platforms.
Rubrik integrates with popular databases like Oracle, SQL Server, and MySQL, ensuring the protection and recovery of critical database environments. Rubrik also integrates with various applications, including Exchange, SharePoint, and Active Directory, providing comprehensive data protection for these applications.
Deployment and Configuration of Rubrik, Data recovery data breaches rubrik
Deploying and configuring Rubrik involves a series of steps that ensure its successful integration with your existing IT infrastructure.
- Installation and Configuration:Begin by installing Rubrik on a dedicated server or virtual machine. The installation process involves configuring network settings, specifying storage options, and defining user accounts.
- Data Source Discovery:Once installed, Rubrik automatically discovers data sources within your environment. This includes virtual machines, physical servers, and cloud instances.
- Policy Creation:Create policies that define data protection rules for different data sources. These policies specify backup schedules, retention periods, and recovery points.
- Backup and Recovery:Initiate backups according to the defined policies. Rubrik automatically manages the backup process, ensuring data integrity and availability. Recovery operations can be initiated from any backup point, restoring data to its original location or a different environment.
- Monitoring and Reporting:Rubrik provides comprehensive monitoring and reporting tools to track backup status, recovery operations, and overall system health.
Deployment Options and Requirements
Rubrik offers different deployment options to suit various organizational needs and infrastructure configurations.
| Rubrik Version | Deployment Options | Requirements |
|---|---|---|
| Rubrik Cloud | Cloud-based deployment, accessible through a web interface | Requires an active cloud subscription and internet connectivity |
| Rubrik Edge | On-premises deployment, suitable for smaller organizations or remote offices | Requires a physical server or virtual machine with sufficient resources |
| Rubrik Cluster | Scalable, high-availability deployment for larger enterprises | Requires multiple servers or virtual machines with shared storage |
The Future of Data Recovery and Data Breaches

The landscape of data breaches and data recovery is constantly evolving, driven by advancements in technology, increasing sophistication of cyberattacks, and the growing volume and value of data. Understanding these trends and the challenges they present is crucial for organizations to prepare for future data breach scenarios.
Challenges and Opportunities in Data Recovery
The evolving nature of data breaches poses significant challenges for data recovery. The increasing complexity of attacks, the emergence of new attack vectors, and the growing use of ransomware make it more difficult to detect, contain, and recover from breaches.
At the same time, these challenges present opportunities for organizations to enhance their data recovery strategies.
- Emerging Technologies: Artificial intelligence (AI) and machine learning (ML) are playing an increasingly important role in data recovery. AI and ML can be used to automate data recovery tasks, improve the accuracy of data recovery efforts, and detect and prevent breaches more effectively.
- Cloud-Native Solutions: Cloud-based data recovery solutions are becoming increasingly popular, offering scalability, flexibility, and cost-effectiveness. Cloud-native solutions can provide a platform for organizations to store and recover data quickly and efficiently.
- Data Immutability: Immutability ensures that data cannot be modified or deleted, even by malicious actors. This is a critical aspect of data protection, as it prevents ransomware attacks from encrypting and holding data hostage.
Rubrik’s Role in Addressing Future Data Breach Scenarios
Rubrik is a leading provider of data recovery solutions, and its platform is well-positioned to address the challenges of future data breach scenarios.
- Comprehensive Data Protection: Rubrik offers a comprehensive data protection platform that includes backup, recovery, and security capabilities. This allows organizations to protect their data from a wide range of threats.
- Automation and Orchestration: Rubrik’s platform automates many data recovery tasks, simplifying the process and reducing the time it takes to recover from a breach.
- Cloud Integration: Rubrik integrates seamlessly with leading cloud providers, allowing organizations to leverage the scalability and flexibility of the cloud for data recovery.
- Data Immutability: Rubrik offers immutability features, ensuring that data is protected from ransomware attacks.