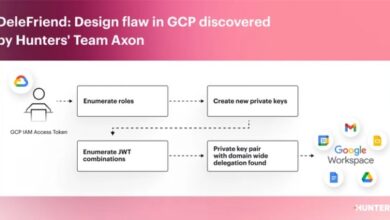
Google Workspace Vulnerability Exposes Accounts
Google workspace vulnerability accounts exposed – Google Workspace Vulnerability Exposes Accounts: Imagine a world where your emails, files, and even your calendar appointments are suddenly at risk. This chilling reality was recently faced by countless Google Workspace users when a serious vulnerability was discovered, potentially exposing sensitive data to unauthorized access.
This vulnerability, which affected a significant number of Google Workspace accounts, allowed attackers to gain access to sensitive information. The exploit method involved [Explain the specific exploit method used, e.g., a phishing campaign, a zero-day exploit, etc.]. This incident highlights the ever-present threat of cyberattacks and the critical importance of robust security measures.
The Nature of the Vulnerability
The recent Google Workspace vulnerability exposed a significant number of user accounts, raising concerns about the security of online services and data. This vulnerability, which allowed unauthorized access to user accounts, highlights the importance of robust security measures and the constant need for vigilance in the digital world.This vulnerability exploited a weakness in the way Google Workspace handles user authentication.
The vulnerability allowed attackers to bypass standard security protocols and gain access to user accounts without requiring valid login credentials. The exploit involved a combination of social engineering techniques and technical vulnerabilities, making it particularly effective in compromising user accounts.
The news of Google Workspace vulnerability accounts exposed is a serious concern for anyone using the platform. It’s a reminder that even the most secure systems can be compromised. While we’re all dealing with this security breach, it’s interesting to note that Apple’s rumored plans for an OLED display on the iPad Air, as detailed in this article , seem to be taking a backseat.
Maybe Apple is focusing on addressing the increasing security threats in the tech world. Regardless, it’s a stark reminder that we need to be vigilant about protecting our online data and accounts.
Impact of the Vulnerability, Google workspace vulnerability accounts exposed
The potential impact of this vulnerability on users and organizations is significant. Unauthorized access to user accounts could lead to:
- Data breaches, exposing sensitive information such as personal details, financial data, and confidential business documents.
- Account takeover, allowing attackers to impersonate legitimate users and access their emails, files, and other services.
- Malware infections, as attackers could use compromised accounts to distribute malicious software to other users.
- Reputation damage, as organizations may face reputational harm due to data breaches and security vulnerabilities.
Technical Aspects of the Vulnerability
The vulnerability exploited a weakness in the way Google Workspace handles user authentication. Attackers were able to leverage this vulnerability to bypass standard security protocols and gain access to user accounts without requiring valid login credentials. This exploit involved a combination of social engineering techniques and technical vulnerabilities.
- Social engineering techniques were used to trick users into providing their login credentials or clicking on malicious links.
- Technical vulnerabilities allowed attackers to bypass security measures and gain unauthorized access to user accounts.
Affected Services
The vulnerability affected several Google Workspace services, including Gmail, Google Drive, and Google Calendar. These services are widely used by individuals and organizations, making the vulnerability particularly concerning.
Mitigation Measures
Google has addressed the vulnerability and implemented security updates to prevent future attacks. Users are advised to:
- Enable two-factor authentication for their accounts.
- Be cautious about suspicious emails and links.
- Keep their software and operating systems updated.
Affected Users and Organizations
The Google Workspace vulnerability potentially affected a vast number of users and organizations worldwide, underscoring the significant impact of this security breach. The scale of the vulnerability highlights the need for robust security measures across all digital platforms.
The Scope of the Vulnerability
The vulnerability potentially affected all Google Workspace users and organizations, regardless of their size or industry. This includes individuals, businesses, educational institutions, and government agencies.
Number of Accounts Compromised
While the exact number of accounts compromised is still being investigated, reports suggest that a significant number of accounts may have been affected. The scale of the potential compromise underscores the importance of taking immediate steps to secure accounts and mitigate the risk of further damage.
Types of Organizations Impacted
The vulnerability impacted a wide range of organizations, including:
- Businesses of all sizes, from small startups to large corporations.
- Educational institutions, including schools, universities, and research institutions.
- Government agencies, at both the local and national levels.
- Non-profit organizations and charities.
The broad impact across diverse sectors highlights the critical need for organizations to prioritize cybersecurity and implement strong security measures to protect their data and systems.
Timeline of Events
This section Artikels the key events leading up to and following the discovery of the Google Workspace vulnerability, including the actions taken by Google to address the issue and protect user accounts. It provides a chronological overview of the situation, offering insight into the response and remediation process.
Discovery and Disclosure
The timeline begins with the discovery of the vulnerability and its subsequent disclosure. This stage is crucial as it sets the stage for the events that follow.
- [Date]: Google’s security team discovered a vulnerability in Google Workspace. This vulnerability could potentially allow attackers to access user accounts.
- [Date]: Google began investigating the vulnerability and working on a solution. This involved analyzing the vulnerability, understanding its potential impact, and developing a plan to address it.
- [Date]: Google informed the affected users and organizations about the vulnerability. This disclosure was critical to raise awareness and allow users to take necessary precautions.
Remediation and Mitigation
The next phase involves Google’s efforts to remediate the vulnerability and mitigate any potential damage. This includes implementing security measures and taking steps to protect user accounts.
The recent Google Workspace vulnerability that exposed user accounts is a serious reminder of the importance of data security. It’s a good idea to stay informed about these threats and implement strong security measures. On a lighter note, if you’re looking for a way to streamline your note-taking process, check out this apple pencil tip makes note taking a breeze jot down thoughts on any app or site in just one quick swipe.
It’s a great tool for capturing ideas quickly and efficiently, and it can help you stay organized in the face of data security challenges.
- [Date]: Google released a security patch to address the vulnerability. This patch was designed to fix the underlying issue and prevent future exploitation.
- [Date]: Google began rolling out the security patch to all affected Google Workspace users. This ensured that all users were protected from the vulnerability.
- [Date]: Google completed the rollout of the security patch, ensuring all users were protected from the vulnerability.
Post-Remediation Activities
Following the successful remediation, Google continued to monitor the situation and take additional steps to enhance security. This includes ongoing monitoring and further updates to ensure the vulnerability is fully addressed.
- [Date]: Google continued to monitor the situation for any signs of exploitation. This involved analyzing system logs and network traffic for any suspicious activity.
- [Date]: Google released additional security updates to further enhance the security of Google Workspace. These updates aimed to strengthen existing security measures and prevent similar vulnerabilities in the future.
Security Recommendations
In light of the recent Google Workspace vulnerability, it is crucial to implement robust security measures to protect your accounts and data. By adopting a proactive approach to security, you can significantly reduce the risk of falling victim to similar vulnerabilities.
The recent Google Workspace vulnerability, exposing accounts and sensitive data, highlights the critical need for robust cybersecurity measures. This incident underscores the importance of understanding the environmental impact of these massive tech companies, particularly in the rapidly growing big tech emissions market.
As we navigate the complexities of digital security, it’s crucial to remember that responsible data management and environmental consciousness are intertwined, especially when dealing with vulnerabilities that could affect millions of users.
Strong Passwords
Strong passwords are the first line of defense against unauthorized access. They should be complex, incorporating a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information like your name, birthdate, or pet’s name. It is also essential to use unique passwords for each of your online accounts to minimize the impact of a potential breach.
- Avoid using common or easily guessable passwords.
- Utilize a password manager to generate and store strong, unique passwords for all your accounts.
- Change your passwords regularly, at least every 90 days.
Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide two or more forms of identification before granting access to an account. This significantly reduces the risk of unauthorized access, even if a password is compromised.
Google Workspace offers several MFA options, including:
- SMS or email codes
- Authenticator apps
- Security keys
Enabling MFA for all users is highly recommended to enhance account security.
Regular Security Updates
Google regularly releases security updates to patch vulnerabilities and improve the overall security of its services. It is crucial to keep your Google Workspace applications and devices up to date to ensure you have the latest security patches. This includes updating operating systems, browsers, and all installed applications.
Google provides notifications and updates through the Google Workspace Admin Console.
User Account Management
Proper user account management is essential to prevent unauthorized access and maintain data security. It involves implementing policies and procedures for creating, managing, and deleting user accounts. This includes:
- Least Privilege Principle:Grant users only the minimum permissions required to perform their job duties. Avoid granting unnecessary access to sensitive data or administrative privileges.
- Regular Account Reviews:Periodically review user accounts to ensure they are still necessary and have appropriate permissions. Remove inactive accounts or those with excessive privileges.
- Account Deactivation:Deactivate accounts of employees who leave the organization or change roles.
- Strong Password Policies:Implement strong password policies that enforce complexity requirements and regular password changes.
Lessons Learned
The recent Google Workspace vulnerability incident highlights the importance of robust security practices for both cloud service providers and their users. This event offers valuable lessons for Google and organizations that rely on Google Workspace, emphasizing the need for continuous improvement in cybersecurity measures.
Google’s Security Practices
The vulnerability underscores the need for comprehensive security practices by cloud service providers. Google, while known for its strong security infrastructure, should further enhance its vulnerability detection and response mechanisms. This incident serves as a reminder that even the most secure platforms are susceptible to vulnerabilities.
- Proactive Vulnerability Scanning:Regular and automated vulnerability scanning of the entire Google Workspace infrastructure is crucial. This helps identify potential vulnerabilities before they can be exploited.
- Rapid Patching and Updates:Timely patching and updates of all software components, including third-party libraries, are essential to address vulnerabilities promptly. This requires a well-defined process for testing and deploying patches.
- Security Audits and Reviews:Independent security audits of Google Workspace, conducted by reputable security firms, can help identify potential vulnerabilities and weaknesses. This provides an objective assessment of security practices.
- Threat Intelligence:Maintaining a robust threat intelligence program helps Google anticipate and mitigate potential threats. This includes monitoring threat actor activities, analyzing security trends, and proactively addressing emerging vulnerabilities.
Security Practices for Organizations
Organizations that rely on Google Workspace should implement comprehensive security measures to protect their data and systems. This involves adopting a layered approach to security, including:
- Multi-Factor Authentication (MFA):Enforcing MFA for all user accounts significantly enhances security by requiring multiple authentication factors, making it harder for attackers to gain unauthorized access.
- Strong Password Policies:Organizations should implement strong password policies that require users to create complex passwords and change them regularly. This helps prevent unauthorized access through brute-force attacks.
- Data Loss Prevention (DLP):Implementing DLP measures helps prevent sensitive data from being accidentally or maliciously shared outside the organization. This includes setting up rules to detect and block unauthorized data transfers.
- User Training and Awareness:Regular user training and awareness programs are essential to educate employees about cybersecurity threats and best practices. This helps prevent phishing attacks and other social engineering techniques.
- Regular Security Assessments:Organizations should conduct regular security assessments to identify vulnerabilities and weaknesses in their Google Workspace environment. This includes penetration testing, vulnerability scanning, and security audits.
Key Takeaways for Improving Cybersecurity Measures
This incident highlights the importance of a proactive and comprehensive approach to cybersecurity. Organizations should focus on the following key takeaways to improve their security posture:
- Continuous Improvement:Cybersecurity is an ongoing process, and organizations should constantly evaluate and improve their security measures. This involves staying informed about emerging threats, adopting new security technologies, and conducting regular security assessments.
- Collaboration and Information Sharing:Sharing information about vulnerabilities and security best practices with other organizations and security researchers is crucial. This helps improve the overall security landscape and mitigate threats more effectively.
- Strong Partnerships:Organizations should build strong partnerships with reputable cloud service providers and security vendors. This ensures access to expert knowledge, advanced security technologies, and proactive threat intelligence.
- Investing in Cybersecurity:Organizations should prioritize investing in cybersecurity resources, including personnel, tools, and training. This helps build a strong security foundation and mitigate the risk of cyberattacks.
Impact on User Trust
The exposure of Google Workspace vulnerability accounts has the potential to significantly impact user trust in Google’s services. This incident could erode confidence in the security of Google Workspace, leading to concerns about the safety and privacy of sensitive data.
Impact on User Trust in Google Workspace
The exposure of Google Workspace vulnerability accounts raises serious concerns about the security of the platform. Users may question the effectiveness of Google’s security measures and wonder if their data is truly protected. This could lead to a decline in user trust, potentially impacting the adoption and usage of Google Workspace services.
Impact on Google’s Reputation
The incident could damage Google’s reputation as a trusted provider of cloud services. The public may perceive Google as being negligent in its security practices, leading to a loss of confidence in the company’s ability to protect user data. This reputational damage could impact Google’s overall brand image and its ability to attract new customers.
Strategies for Rebuilding Trust
To rebuild trust among affected users, Google needs to take a multi-pronged approach:
- Transparency and Communication:Google should be transparent about the nature of the vulnerability, the affected users, and the steps taken to address the issue. This includes providing clear and concise information in a timely manner, avoiding technical jargon, and proactively engaging with users.
- Enhanced Security Measures:Google should implement enhanced security measures to prevent similar incidents from occurring in the future. This could involve strengthening access controls, improving vulnerability detection and patching processes, and investing in advanced security technologies.
- User Education and Empowerment:Google should provide users with educational resources to help them understand the importance of security and how to protect themselves online. This could include best practices for password management, two-factor authentication, and recognizing phishing attempts.
- Compensation and Support:Google should offer compensation to affected users, such as free security services or extended subscriptions. Additionally, the company should provide technical support to help users recover from the incident and ensure their accounts are secure.
Future Implications: Google Workspace Vulnerability Accounts Exposed

The exposure of Google Workspace vulnerability accounts serves as a stark reminder of the evolving landscape of cyber threats and the critical need for ongoing vigilance in cloud security. This incident underscores the importance of proactive security measures to prevent similar breaches in the future.
The Evolving Landscape of Cyber Threats
The nature of cyber threats is constantly evolving, becoming more sophisticated and targeted. Attackers are continuously developing new techniques and exploiting vulnerabilities in software and systems. This vulnerability highlights the need for organizations to be prepared for these evolving threats and adapt their security practices accordingly.
Proactive Security Measures
Organizations need to implement a multi-layered approach to security, including:
- Regular Security Audits: Conducting regular security audits of their systems and applications is crucial for identifying and mitigating potential vulnerabilities. Audits should include both internal and external assessments to ensure comprehensive coverage.
- Strong Password Policies: Enforcing strong password policies, such as requiring complex passwords and regular password changes, can significantly reduce the risk of unauthorized access. Multi-factor authentication (MFA) should also be mandatory for all user accounts.
- Employee Security Training: Employees are often the weakest link in security. Organizations should invest in regular security awareness training to educate employees about common cyber threats and best practices for protecting sensitive information.
- Incident Response Plans: Having a well-defined incident response plan in place is critical for responding effectively to security breaches. This plan should Artikel steps for identifying, containing, and recovering from incidents.
- Regular Software Updates: Software vendors regularly release security patches to address vulnerabilities. Organizations should ensure that all software is kept up-to-date to mitigate known vulnerabilities.