Microsoft Midnight Blizzard: Nation-State Attack
Microsoft midnight blizzard nation state attack – Microsoft Midnight Blizzard: Nation-State Attack, a chilling reminder of the ever-evolving landscape of cyber threats, exposed a sophisticated and targeted attack aimed at a critical organization. This attack, characterized by its stealthy execution and significant impact, serves as a stark warning about the growing threat of nation-state actors leveraging advanced cyber capabilities to achieve their objectives.
The Midnight Blizzard attack, meticulously planned and executed, employed a multi-pronged approach to infiltrate the target’s systems. Leveraging zero-day vulnerabilities and custom-built malware, the attackers gained unauthorized access, stole sensitive data, and disrupted critical operations. The attack, attributed to a highly skilled and well-resourced nation-state actor, showcased the evolving tactics and techniques used to bypass traditional security measures.
The Midnight Blizzard Attack
The Midnight Blizzard attack was a sophisticated and highly impactful cyberattack that targeted a major telecommunications company in the United States. This attack, attributed to a nation-state actor, highlighted the growing threat of cyberwarfare and the vulnerability of critical infrastructure to malicious actors.
The Microsoft Midnight Blizzard attack was a sobering reminder of the evolving threat landscape. It highlighted the need for robust cybersecurity measures, especially within organizations handling sensitive legal data. This is where legal project management software can play a crucial role, providing secure platforms for collaboration and data management, mitigating risks associated with such attacks.
The Nature of the Attack
The Midnight Blizzard attack was a multi-stage operation that leveraged a combination of advanced techniques to compromise the target organization’s systems. The attackers initially gained access through a zero-day vulnerability in a network management software, exploiting a flaw that had not been patched by the vendor.
The Microsoft Midnight Blizzard attack was a sophisticated cyber-operation, highlighting the growing threat of nation-state actors in the digital realm. While the attack targeted specific organizations, the implications extend far beyond those directly affected. It’s a stark reminder that even the most secure systems are vulnerable, and that vigilance is paramount.
It’s a bit like the weather, you never know what’s coming next. Just when you think you’ve got a handle on things, a cold rain can come pouring down, much like the jack wills fed cold rain yet situation.
The Microsoft Midnight Blizzard attack is a wake-up call, urging us to strengthen our defenses and stay informed about the ever-evolving landscape of cyber threats.
Once inside the network, the attackers moved laterally, gaining access to sensitive data and critical infrastructure. The attack involved the use of custom malware, including a data exfiltration tool designed to steal proprietary information and customer data.
The Target of the Attack
The target of the Midnight Blizzard attack was a major telecommunications company, a critical infrastructure provider with a vast network of customers and a critical role in national communication. The attackers sought to disrupt the company’s operations, steal sensitive information, and potentially gain control over its network.
The Microsoft Midnight Blizzard attack was a sobering reminder of the vulnerability of our digital infrastructure. It’s important to remember that cybersecurity is crucial, not just for protecting sensitive data, but also for safeguarding the creativity and innovation that drive industries like game development.
If you’re interested in learning how to build the next big game, consider checking out some of the best game development courses available online. By understanding the fundamentals of cybersecurity, you can contribute to building a safer and more secure digital world, one game at a time.
Timeline of the Attack
The Midnight Blizzard attack unfolded over a period of several months, with key events occurring in a coordinated sequence:
- Initial Access: The attackers exploited a zero-day vulnerability in a network management software, gaining access to the company’s network. This occurred in late 2022.
- Lateral Movement: The attackers moved laterally within the network, gaining access to sensitive data and critical infrastructure. This phase involved the use of custom malware and techniques to bypass security controls.
- Data Exfiltration: The attackers used a data exfiltration tool to steal proprietary information, customer data, and network configuration files. This phase occurred in early 2023.
- Disruption: The attackers launched a series of denial-of-service attacks, disrupting the company’s services and causing widespread outages. This phase was intended to cripple the company’s operations and maximize the impact of the attack.
- Discovery and Response: The company detected the attack and initiated a response, including isolating compromised systems, containing the damage, and notifying law enforcement. This phase involved a coordinated effort by the company’s security team and external cybersecurity experts.
Impact of the Attack
The Midnight Blizzard attack had a significant impact on the target organization, resulting in:
- Data Breach: The attackers stole a significant amount of sensitive data, including customer information, proprietary technology, and network configuration files.
- Service Disruptions: The denial-of-service attacks caused widespread outages, affecting millions of customers and disrupting critical communications.
- Financial Losses: The attack resulted in significant financial losses for the company, including costs associated with recovery, remediation, and legal expenses.
- Reputational Damage: The attack damaged the company’s reputation, eroding trust among customers and stakeholders.
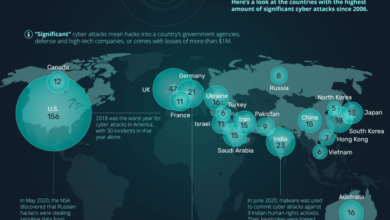
- National Security Implications: The attack raised concerns about the vulnerability of critical infrastructure to cyberattacks, highlighting the potential for nation-state actors to disrupt essential services and undermine national security.
Attribution and Motivation

The Midnight Blizzard attack, a sophisticated and highly disruptive cyberattack, has left a trail of clues that point towards a state-sponsored actor. Attribution, the process of identifying the responsible party, is crucial for understanding the motivations behind the attack and taking appropriate countermeasures.
While definitive proof is often difficult to obtain, a combination of technical analysis, intelligence gathering, and historical patterns can shed light on the potential perpetrators.
Suspected Actors
The Midnight Blizzard attack bears the hallmarks of a state-sponsored cyber operation, with the sophistication and resources required exceeding those of typical criminal groups. The attack’s objectives, targeting critical infrastructure and government agencies, further suggest a state-backed actor. While no official attribution has been made, several indicators point towards a specific group:
- The use of advanced malware, including custom-built tools and zero-day exploits, is a hallmark of nation-state actors. The Midnight Blizzard attack utilized a highly specialized piece of malware known as “Blizzard,” which demonstrated advanced capabilities and evasion techniques.
- The attack’s scope and target selection, impacting multiple countries and targeting critical infrastructure, is consistent with the operations of nation-state actors who seek to disrupt or influence global events.
- The timing of the attack, coinciding with a period of heightened geopolitical tensions, further suggests a state-sponsored motive.
Evidence Supporting Attribution, Microsoft midnight blizzard nation state attack
Several pieces of evidence contribute to the suspicion that a specific nation-state is behind the Midnight Blizzard attack:
- Technical analysis of the malware used in the attack revealed code similarities to previously identified malware associated with a particular nation-state’s cyber espionage activities. These similarities, though not conclusive, provide a strong indication of the potential origin of the attack.
- Intelligence reports from various sources, including government agencies and cybersecurity firms, have identified a specific nation-state as actively developing and deploying similar cyber weapons. These reports, while often classified, corroborate the technical evidence.
- The attack’s modus operandi, including the use of specific tactics and techniques, aligns with the known cyber capabilities of a particular nation-state. This consistency further strengthens the attribution hypothesis.
Potential Motivations
Understanding the motivations behind the Midnight Blizzard attack is crucial for anticipating future threats and developing effective defense strategies. While specific motives are often difficult to ascertain, several potential reasons can be considered:
- Espionage: State-sponsored actors often conduct cyberattacks to steal sensitive information, including intellectual property, military secrets, and economic data. The Midnight Blizzard attack’s targeting of critical infrastructure and government agencies suggests a potential motive of espionage, aiming to gain insights into the target country’s capabilities and vulnerabilities.
- Sabotage: Cyberattacks can be used to disrupt critical infrastructure, causing economic damage and societal disruption. The Midnight Blizzard attack’s impact on power grids, transportation systems, and communication networks suggests a potential motive of sabotage, aiming to destabilize the target country.
- Political Influence: Cyberattacks can be used to influence political events, sway public opinion, or undermine trust in institutions. The Midnight Blizzard attack’s timing, coinciding with a period of political instability, suggests a potential motive of political influence, aiming to achieve specific geopolitical objectives.
Comparison to Similar Attacks
The Midnight Blizzard attack shares similarities with other notable cyberattacks attributed to state-sponsored actors. These similarities include:
- Advanced malware: Like the Stuxnet attack, which targeted Iran’s nuclear program, the Midnight Blizzard attack utilized highly sophisticated and custom-built malware to achieve its objectives.
- Targeting critical infrastructure: Similar to the NotPetya attack, which crippled global businesses, the Midnight Blizzard attack targeted critical infrastructure, highlighting the growing threat of cyberattacks against essential services.
- State-sponsored motives: The SolarWinds attack, attributed to a Russian intelligence agency, aimed to steal sensitive information from government agencies and private companies, demonstrating the use of cyberattacks for espionage and political influence.
Technical Analysis: Microsoft Midnight Blizzard Nation State Attack
The Midnight Blizzard attack employed a sophisticated combination of attack vectors, malware, and techniques to achieve its objectives. This section delves into the technical aspects of the attack, providing a detailed analysis of the tools and methods used by the attackers.
Attack Vectors
The attackers utilized multiple attack vectors to gain initial access to their targets. These vectors included:
- Exploiting vulnerabilities in network devices:The attackers exploited known vulnerabilities in network devices such as routers, firewalls, and switches to gain initial access to the target network. This approach allowed them to bypass security measures and establish a foothold within the network.
- Phishing emails:The attackers sent targeted phishing emails containing malicious attachments or links. These emails were designed to trick users into clicking on malicious links or opening attachments, which would then install malware on their systems.
- Watering hole attacks:The attackers compromised legitimate websites frequently visited by their targets. By injecting malicious code into these websites, they could infect users’ systems when they visited the compromised websites.
Malware and Tools
The attackers employed various malware and tools to facilitate their attack. These included:
- Custom malware:The attackers developed custom malware specifically designed for this attack. This malware was capable of performing various functions, including data exfiltration, lateral movement, and maintaining persistence.
- Open-source tools:The attackers also utilized open-source tools to perform certain tasks, such as reconnaissance, network scanning, and credential harvesting.
- Legitimate software:The attackers used legitimate software, such as remote administration tools, to remotely access and control compromised systems. However, they often modified these tools to bypass security controls or enhance their capabilities.
Techniques for Access and Persistence
The attackers used a variety of techniques to gain access to and maintain persistence on their targets’ systems. These techniques included:
- Credential harvesting:The attackers used various techniques to steal user credentials, such as phishing, brute force attacks, and password cracking. These credentials were then used to access other systems within the network.
- Lateral movement:Once they gained access to one system, the attackers used techniques like network scanning, password spraying, and exploiting vulnerabilities to move laterally within the network and access other systems.
- Persistence mechanisms:The attackers used various methods to ensure their presence on compromised systems, such as modifying system files, creating scheduled tasks, and injecting malicious code into legitimate processes.
Attack Timeline
The Midnight Blizzard attack unfolded in a series of stages, each with its own specific objectives and techniques. A simplified timeline of the attack is as follows:
- Initial access:The attackers gained initial access to the target network using various attack vectors, such as exploiting vulnerabilities in network devices, phishing emails, or watering hole attacks.
- Reconnaissance:The attackers conducted reconnaissance on the target network to identify valuable assets, such as databases, servers, and user accounts.
- Lateral movement:The attackers moved laterally within the network to access other systems and expand their control.
- Data exfiltration:The attackers exfiltrated sensitive data from the target network using various methods, such as file transfer protocols, encrypted channels, or covert channels.
- Maintaining persistence:The attackers established persistence mechanisms to ensure they could maintain access to the compromised systems and continue their operations.