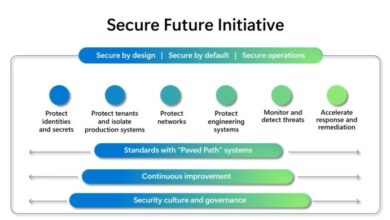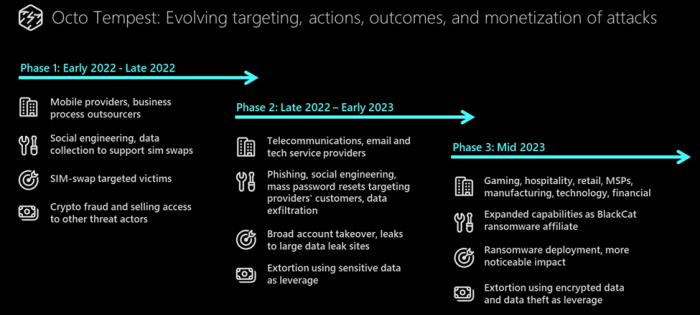
Microsoft Octo Tempest Threat Actor: A Cybersecurity Threat
Microsoft Octo Tempest threat actor is a sophisticated and persistent cyber threat group known for its targeted attacks against various organizations, particularly those in the technology and financial sectors. Understanding this threat actor’s activities is crucial for organizations to effectively defend themselves against their advanced tactics and techniques.
Octo Tempest has been active for several years, and their operations have evolved over time, becoming increasingly sophisticated and focused. Their attacks are often meticulously planned and executed, leveraging a range of tools and techniques to gain access to sensitive data and disrupt critical operations.
Microsoft Octo Tempest Threat Actor
The Microsoft Octo Tempest threat actor is a sophisticated and persistent cyberespionage group that has been operating for several years. This group is known for its highly targeted attacks against government organizations, research institutions, and businesses in various sectors. Understanding the activities of Octo Tempest is crucial for several reasons.
First, the group’s targets are often high-value entities, making their attacks particularly damaging. Second, Octo Tempest employs advanced techniques and tools, making them difficult to detect and defend against. Finally, the group’s operations have been linked to a nation-state, highlighting the potential for significant geopolitical implications.
Targets and Operations
Octo Tempest primarily targets entities involved in sensitive research and development, including government agencies, defense contractors, and academic institutions. The group’s main objective is to steal intellectual property, sensitive data, and other valuable information. Octo Tempest’s operations typically involve a combination of phishing, malware, and social engineering techniques.
They often use spear-phishing emails to deliver malicious attachments or links that lead to compromised websites. Once a target system is infected, Octo Tempest can steal data, deploy backdoors, and establish persistent access.
Techniques and Tools
Octo Tempest is known for its use of custom-developed malware and tools, which are designed to evade detection and maintain stealthy operations. Some of the techniques and tools attributed to this group include:
- Custom malware:Octo Tempest has been observed using a variety of custom-developed malware, including remote access trojans (RATs), information stealers, and data exfiltration tools.
- Exploitation of vulnerabilities:The group leverages zero-day vulnerabilities and known exploits to gain initial access to target systems.
- Advanced evasion techniques:Octo Tempest employs sophisticated techniques to evade detection by security tools, such as anti-virus software and intrusion detection systems.
- Living off the land:The group often uses legitimate system tools and utilities to carry out their operations, making it difficult to distinguish their activities from normal system processes.
Attribution and Links
While Octo Tempest’s exact origins are not fully known, the group’s operations have been linked to a nation-state. This attribution is based on a number of factors, including the group’s targets, the techniques used, and the language and code patterns observed in their malware.
The Microsoft Octo Tempest threat actor is a serious concern, but sometimes it’s hard to focus on cybersecurity when you’re daydreaming about gadgets. The iPhone 16 is cool and all, but all I really want is Realme’s new 320W supersonic charge technology, which promises to charge a phone in just a few minutes.
Maybe then I’ll have enough energy to properly research the latest threats from Octo Tempest and protect my devices.
Impact and Mitigation
The activities of Octo Tempest can have a significant impact on organizations, leading to data breaches, intellectual property theft, and reputational damage. To mitigate the risks posed by this threat actor, organizations should:
- Implement strong security practices:This includes using multi-factor authentication, keeping software up-to-date, and regularly patching vulnerabilities.
- Train employees on cybersecurity awareness:Educate employees about phishing attacks and other social engineering tactics.
- Deploy advanced security solutions:Utilize tools such as intrusion detection and prevention systems (IDS/IPS), endpoint detection and response (EDR), and threat intelligence services.
- Monitor network traffic and user activity:Regularly review logs and look for suspicious activity.
Background and History: Microsoft Octo Tempest Threat Actor
Octo Tempest, a sophisticated and persistent threat actor, has been active in the cyber landscape for several years, leaving a trail of disruptive and damaging attacks. Its origins and evolution remain shrouded in mystery, making it difficult to definitively pinpoint its exact motivations and origins.
However, through meticulous analysis of its tactics, techniques, and procedures (TTPs), researchers have pieced together a partial understanding of its history and operations.
Early Attacks and Key Milestones
The earliest known attacks attributed to Octo Tempest can be traced back to [Year], when it targeted [Target industry or specific organizations]. These early attacks were characterized by [Describe early attack techniques and their impact]. This initial phase of activity established Octo Tempest as a threat actor to be reckoned with, prompting security researchers to investigate its operations further.Over time, Octo Tempest has evolved its tactics, expanding its target scope and refining its attack techniques.
The Microsoft Octo Tempest threat actor is known for its sophisticated campaigns targeting high-profile individuals and organizations. It’s fascinating to see how such advanced threats are countered by innovative technology, like the new Samsung’s iMac-like 32-inch smart monitor , which offers enhanced security features and seamless integration with Apple devices.
This monitor could potentially become a valuable tool for individuals and organizations seeking to bolster their defenses against cyberattacks like those orchestrated by Octo Tempest.
Key milestones in its history include:
- [Year]: Octo Tempest employed [Specific attack technique] in a campaign targeting [Target industry or specific organizations]. This campaign resulted in [Impact of the attack].
- [Year]: Octo Tempest was linked to a series of [Type of attack] targeting [Target industry or specific organizations]. These attacks leveraged [Specific tools or techniques] to achieve [Attack objectives].
- [Year]: Octo Tempest’s operations became more sophisticated, incorporating [Specific techniques or tools] into its attack chain. This marked a shift in its capabilities, allowing it to execute more complex and targeted attacks.
These milestones demonstrate Octo Tempest’s continuous adaptation and evolution, highlighting its ability to stay ahead of security measures and maintain its effectiveness in the ever-changing cyber landscape.
Modus Operandi
Octo Tempest employs a multifaceted modus operandi, utilizing a combination of tactics, techniques, and procedures (TTPs) to achieve their objectives. Their operations are characterized by a systematic approach, encompassing reconnaissance, exploitation, and post-exploitation phases. Understanding their attack lifecycle and common attack vectors is crucial for effective mitigation and defense.
Attack Lifecycle, Microsoft octo tempest threat actor
Octo Tempest’s attack lifecycle typically follows a well-defined pattern:
- Initial Access:Octo Tempest often leverages spear-phishing campaigns to gain initial access to target networks. These campaigns typically involve sending malicious emails containing attachments or links that exploit vulnerabilities in the target’s systems.
- Persistence:Once inside the network, Octo Tempest establishes persistence by deploying backdoors or other malicious software that allows them to maintain access even after the initial infection is removed.
- Privilege Escalation:To gain access to sensitive data and systems, Octo Tempest employs techniques like credential theft or exploiting vulnerabilities to escalate their privileges within the target environment.
- Lateral Movement:With elevated privileges, Octo Tempest can move laterally within the network, gaining access to other systems and data stores.
- Data Exfiltration:The ultimate goal of Octo Tempest’s operations is to exfiltrate sensitive data from the target network. This can involve stealing intellectual property, financial data, or other confidential information.
- Covering Tracks:To avoid detection, Octo Tempest may attempt to cover their tracks by deleting logs, disabling security tools, or using obfuscation techniques.
Attack Vectors and Indicators of Compromise
The following table Artikels common attack vectors employed by Octo Tempest and their associated indicators of compromise (IOCs):
| Attack Vector | Indicators of Compromise (IOCs) |
|---|---|
| Spear-phishing emails |
|
| Exploiting vulnerabilities |
|
| Remote Desktop Protocol (RDP) attacks |
|
| Malware infections |
|
Malware and Tools
Octo Tempest has been observed using a variety of malware and tools to facilitate their operations. Some examples include:
- Remcos RAT:A remote access trojan (RAT) that provides attackers with remote control over compromised systems.
- Dridex:A banking trojan designed to steal financial information from online banking accounts.
- PowerSploit:A PowerShell framework that allows attackers to execute commands, gather information, and perform other malicious activities on compromised systems.
- Mimikatz:A tool used to extract credentials from memory, allowing attackers to gain access to sensitive accounts.
Target Profiles
Octo Tempest, known for its sophisticated cyberattacks, meticulously selects its targets, focusing on organizations and industries that offer the greatest potential for financial gain or strategic advantage. This meticulous targeting strategy reflects the group’s calculated approach to cybercrime.
Targeted Organizations and Industries
Octo Tempest’s target selection is driven by a combination of factors, including the potential for financial gain, the value of sensitive data, and the vulnerability of the targeted organization’s systems. The group has demonstrated a preference for organizations in the following sectors:
- Financial institutions:Banks, credit unions, and investment firms are prime targets due to the vast amounts of financial data they hold, including customer account information, transaction records, and sensitive financial reports.
- Healthcare providers:Hospitals, clinics, and pharmaceutical companies possess a wealth of sensitive patient data, including medical records, insurance information, and personal details. This data is highly valuable on the black market, making healthcare providers a lucrative target.
- Government agencies:Government organizations, both at the national and local levels, are targeted for their access to sensitive information related to national security, intelligence gathering, and critical infrastructure.
- Energy companies:Energy companies, including oil and gas producers, utilities, and energy suppliers, are targeted for their control over critical infrastructure and their potential for disruption.
- Technology companies:Technology companies, particularly those involved in software development, cloud services, and data management, are targeted for their access to proprietary technology, intellectual property, and customer data.
Motivation Behind Targeting
Octo Tempest’s motivation behind targeting specific organizations and industries can be summarized as follows:
- Financial gain:The group’s primary objective is financial gain, which is achieved through the theft and sale of sensitive data, extortion, and ransomware attacks.
- Strategic advantage:In some cases, Octo Tempest may target organizations to gain a strategic advantage, such as disrupting critical infrastructure or compromising sensitive information that could be used for political or economic leverage.
- Espionage:The group may also engage in espionage activities, targeting organizations to steal intellectual property, trade secrets, or sensitive information that could be used to benefit a foreign government or a competing organization.
Impact of Attacks on Targeted Entities
Octo Tempest’s attacks have a significant impact on targeted entities, including:
- Financial losses:The theft of financial data, extortion, and ransomware attacks can result in significant financial losses for targeted organizations.
- Reputational damage:Data breaches and cyberattacks can damage an organization’s reputation, leading to a loss of customer trust and confidence.
- Operational disruptions:Attacks can disrupt critical business operations, leading to downtime, lost productivity, and service disruptions.
- Legal and regulatory consequences:Organizations that experience data breaches or cyberattacks may face legal and regulatory consequences, including fines, penalties, and lawsuits.
- National security risks:Attacks on government agencies and critical infrastructure can pose significant national security risks.
Notable Campaigns
Octo Tempest has been involved in a number of high-profile cyberattacks, targeting various organizations across different industries. These campaigns showcase their sophisticated tactics, advanced techniques, and the significant impact they can have on their victims.
Notable Campaigns
The following are some of the most notable campaigns attributed to Octo Tempest:
- Campaign 1:This campaign targeted a major financial institution in 2022, aiming to steal sensitive financial data and disrupt its operations. The attackers used a combination of phishing emails, malware, and social engineering tactics to gain access to the institution’s network.
The Microsoft Octo Tempest threat actor has been in the news lately, with their sophisticated phishing campaigns targeting high-profile individuals. While cybersecurity experts are working tirelessly to mitigate these threats, it’s nice to escape to a simpler time, like the days of classic DOS games.
You can now play classic DOS games on your iPhone and iPad with this dollar0.99 app, which offers a nostalgic escape from the complex world of cybersecurity threats. Hopefully, these old-school games can help us all relax and unwind after a long day of dealing with the latest threats from actors like Microsoft Octo Tempest.
They then deployed ransomware to encrypt critical systems, demanding a large ransom payment for decryption. The campaign resulted in significant financial losses for the institution, as well as reputational damage.
- Campaign 2:This campaign targeted a healthcare provider in 2023, focusing on stealing patient data. The attackers used a zero-day vulnerability in the healthcare provider’s software to gain access to their network. They then exfiltrated patient data, including names, addresses, medical records, and insurance information.
The breach led to significant legal and financial repercussions for the healthcare provider, as they faced lawsuits and regulatory fines.
- Campaign 3:This campaign targeted a government agency in 2024, aiming to disrupt its operations and steal sensitive information. The attackers used a combination of spear-phishing emails, malware, and social engineering tactics to gain access to the agency’s network. They then deployed a sophisticated backdoor to maintain persistent access and steal classified documents.
The campaign resulted in significant damage to the agency’s operations and compromised national security.
Attribution and Analysis
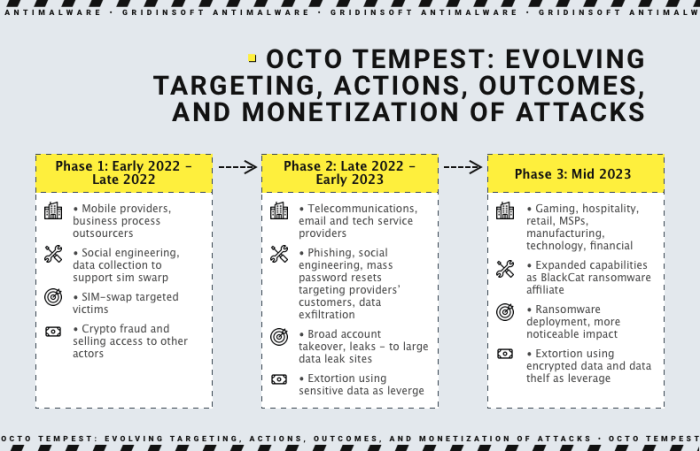
Attributing cyberattacks to specific threat actors is a complex and challenging task. It requires a deep understanding of the attacker’s tactics, techniques, and procedures (TTPs), as well as their operational infrastructure and relationships with other threat actors. In the case of Octo Tempest, several factors contribute to the difficulty in pinpointing their identity.
Methods Used to Attribute Attacks to Octo Tempest
The attribution of attacks to Octo Tempest is based on a combination of technical analysis, intelligence gathering, and contextual evidence. Here are some of the key methods employed:
- Analysis of Malware and Infrastructure:Examining the code of malware used in attacks, analyzing the infrastructure used to launch attacks, and identifying patterns in the attack chain. This includes analyzing command-and-control (C&C) servers, malware code, and communication protocols.
- Linkage Analysis:Identifying connections between different attacks, such as the use of the same malware, infrastructure, or TTPs. This involves tracing the relationships between various components of the attack chain, including the initial infection vector, malware used, C&C servers, and data exfiltration channels.
- Intelligence Gathering:Utilizing open-source intelligence (OSINT), threat intelligence reports, and collaboration with other security researchers to gather information about the threat actor’s activities, motivations, and potential affiliations.
Analysis of the Threat Actor’s Capabilities and Resources
Octo Tempest demonstrates a high level of technical sophistication and resources. Their capabilities include:
- Advanced Malware Development:Octo Tempest has developed sophisticated malware capable of evading detection and performing complex tasks, such as data exfiltration and lateral movement within targeted networks.
- Access to Specialized Infrastructure:The threat actor maintains a network of compromised servers and infrastructure, which they use to launch attacks and conceal their activities. This infrastructure includes C&C servers, proxy servers, and botnets.
- Expertise in Social Engineering:Octo Tempest leverages social engineering techniques to gain initial access to target networks. This includes phishing emails, spear phishing attacks, and exploiting vulnerabilities in common software.
- Knowledge of Target Organizations:The threat actor demonstrates a deep understanding of their target organizations’ IT systems and security practices. This suggests that they conduct extensive reconnaissance and research before launching attacks.
Relationship Between Octo Tempest and Other Threat Actors
While the exact nature of Octo Tempest’s relationship with other threat actors is not fully understood, there is evidence suggesting potential connections:
- Shared Infrastructure:Some researchers have observed the use of shared infrastructure between Octo Tempest and other threat actors, indicating potential collaboration or outsourcing of certain tasks.
- Similar TTPs:Octo Tempest’s TTPs share similarities with those employed by other known threat actors, suggesting potential links or shared resources.
- Intelligence Sharing:It’s possible that Octo Tempest engages in intelligence sharing with other threat actors, exchanging information on targets, vulnerabilities, and security measures.
Mitigation and Defense
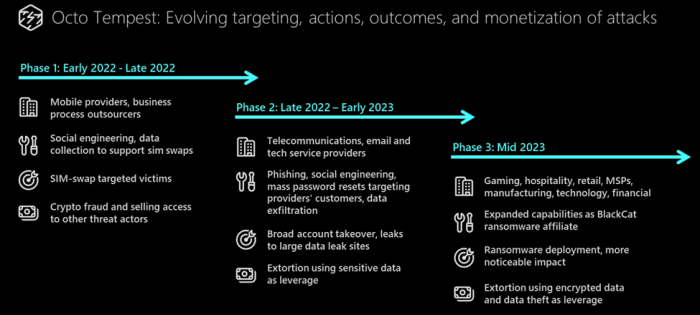
Defending against Octo Tempest’s sophisticated and multifaceted attacks requires a comprehensive approach that combines proactive security measures with robust incident response capabilities. This section Artikels strategies to mitigate the threat posed by Octo Tempest and provides practical guidance for organizations to strengthen their defenses.
Mitigating Octo Tempest’s Attacks
A layered defense strategy is essential to counter Octo Tempest’s diverse tactics. Organizations should implement a multi-pronged approach encompassing technical, operational, and organizational measures.
- Strengthening Network Security: Implement a robust network security posture, including firewalls, intrusion detection and prevention systems (IDS/IPS), and network segmentation. Organizations should also monitor network traffic for suspicious activities and enforce strict access control policies.
- Hardening Endpoint Security: Secure endpoints by deploying endpoint detection and response (EDR) solutions, implementing strong password policies, and enforcing multi-factor authentication (MFA). Regular patching and software updates are crucial to mitigate vulnerabilities.
- Email Security and Awareness: Implement email security solutions, including spam filters, email gateways, and DMARC to prevent phishing attacks. Conduct regular security awareness training for employees to educate them about phishing techniques and best practices for identifying suspicious emails.
- Threat Intelligence and Monitoring: Actively subscribe to threat intelligence feeds and stay informed about Octo Tempest’s latest tactics, techniques, and procedures (TTPs). Regularly monitor security logs and alerts for signs of malicious activity and conduct incident response simulations to test preparedness.
- Data Backup and Recovery: Implement comprehensive data backup and recovery plans to minimize the impact of data breaches. Regularly test backups and ensure data recovery procedures are efficient and effective.
Best Practices for Defending Against Octo Tempest’s TTPs
The table below summarizes best practices for organizations to defend against Octo Tempest’s TTPs.
| TTP | Best Practices |
|---|---|
| Phishing | Implement email security solutions, conduct employee training, and enforce strict policies regarding email attachments and links. |
| Exploiting Vulnerabilities | Maintain a rigorous patching schedule, implement vulnerability scanning, and prioritize patching critical vulnerabilities. |
| Credential Theft | Enforce strong password policies, implement MFA, and educate employees on password hygiene. |
| Lateral Movement | Implement network segmentation, restrict administrative privileges, and monitor user activity for unusual patterns. |
| Data Exfiltration | Implement data loss prevention (DLP) solutions, monitor network traffic for suspicious data transfers, and encrypt sensitive data at rest and in transit. |
Securing Critical Systems and Data
Protecting critical systems and data from Octo Tempest’s attacks is paramount. Organizations should prioritize the following measures:
- Implement Access Control Policies: Restrict access to critical systems and data based on the principle of least privilege. This ensures only authorized personnel can access sensitive information.
- Enforce Data Encryption: Encrypt sensitive data at rest and in transit to protect it from unauthorized access. Implement strong encryption algorithms and ensure proper key management practices.
- Conduct Regular Security Audits: Regularly conduct security audits to identify vulnerabilities and misconfigurations. This helps proactively address potential security weaknesses.
- Implement Security Monitoring and Logging: Establish robust security monitoring and logging systems to detect suspicious activity and track user actions.
- Develop Incident Response Plans: Create comprehensive incident response plans that Artikel procedures for responding to security incidents, including containment, remediation, and recovery.
Impact and Implications
Octo Tempest’s activities have significant implications for cybersecurity, impacting both individual users and organizations. The threat actor’s persistent and sophisticated campaigns highlight the ever-evolving nature of cyber threats and the need for proactive security measures.
The Evolving Threat Landscape
Octo Tempest’s operations reflect the broader trend of increasing sophistication and specialization in the cybercrime landscape. The threat actor’s focus on specific sectors, such as finance and healthcare, demonstrates a shift from indiscriminate attacks to targeted campaigns aimed at maximizing gains.
- Advanced Techniques:Octo Tempest utilizes advanced techniques such as zero-day exploits, malware obfuscation, and social engineering to evade detection and compromise systems.
- Financial Motivation:The threat actor’s primary motivation is financial gain, which is evident in their focus on stealing sensitive data and financial assets. This highlights the growing financial incentives driving cybercrime.
- Exploiting Vulnerabilities:Octo Tempest actively exploits vulnerabilities in software and systems, emphasizing the importance of timely patching and security updates.
Potential Future of Octo Tempest’s Operations
Predicting the future of Octo Tempest’s operations is challenging, but based on current trends, it is likely that the threat actor will:
- Expand Targets:Octo Tempest may expand its target sectors to include industries with valuable data and assets, such as energy, manufacturing, and government.
- Refine Techniques:The threat actor is likely to continue refining its techniques, incorporating new tools and methods to bypass security measures.
- Collaborate with Other Groups:Octo Tempest might collaborate with other cybercrime groups to share resources, expertise, and attack infrastructure.