Microsoft Secure Future Initiative Report: Shaping a Safer Digital World
The Microsoft Secure Future Initiative Report delves into the ever-evolving landscape of cybersecurity, highlighting the crucial role technology plays in safeguarding our digital lives. This report isn’t just a collection of statistics and technical jargon; it’s a roadmap for building a more secure future, one that addresses the growing threat of cyberattacks and empowers individuals and organizations to navigate the digital world with confidence.
The report examines the initiative’s key components, focusing on the collaborative efforts of Microsoft and its partners to develop innovative solutions and raise awareness about cybersecurity best practices. It analyzes emerging threats and their potential impact, providing insights into how the initiative is tackling these challenges head-on.
The report also Artikels the initiative’s implementation strategies, including the metrics used to measure its success, and explores future directions for continued growth and development.
Microsoft Secure Future Initiative: Microsoft Secure Future Initiative Report
The Microsoft Secure Future Initiative is a comprehensive program aimed at enhancing cybersecurity across various sectors and promoting a more secure digital environment. This initiative recognizes the ever-evolving nature of cyber threats and the need for proactive measures to protect individuals, organizations, and critical infrastructure.
Purpose and Goals
The Microsoft Secure Future Initiative seeks to achieve several key objectives:
- Promote a Secure Digital Environment:The initiative aims to create a safer online environment by fostering collaboration among stakeholders, including governments, industry leaders, and individuals. This includes developing and promoting best practices, standards, and technologies to mitigate cyber risks.
- Empower Individuals and Organizations:The initiative empowers individuals and organizations to take ownership of their cybersecurity posture by providing access to resources, training, and tools. This includes education programs on cybersecurity awareness, best practices for secure online behavior, and technical guidance for implementing robust security measures.
- Drive Innovation in Cybersecurity:The initiative encourages innovation in cybersecurity by supporting research and development of new technologies and solutions. This includes exploring emerging technologies like artificial intelligence (AI) and machine learning (ML) for threat detection and response, as well as developing novel approaches to secure critical infrastructure and data.
Key Areas of Focus
The Microsoft Secure Future Initiative focuses on several key areas:
- Cybersecurity Education and Awareness:The initiative emphasizes the importance of cybersecurity education and awareness for individuals, organizations, and governments. This includes promoting programs that teach cybersecurity basics, best practices for online safety, and the importance of strong passwords and multi-factor authentication.
- Threat Intelligence and Response:The initiative promotes the sharing of threat intelligence and best practices for responding to cyber incidents. This includes developing tools and platforms for collaborative threat analysis, as well as fostering partnerships between security researchers, government agencies, and private companies.
- Secure Software Development:The initiative emphasizes the importance of secure software development practices. This includes promoting the use of secure coding techniques, vulnerability scanning tools, and secure development lifecycle (SDL) methodologies.
- Critical Infrastructure Protection:The initiative focuses on protecting critical infrastructure from cyberattacks. This includes developing and promoting security standards for critical infrastructure systems, as well as supporting research and development of technologies for enhanced security.
- Data Privacy and Protection:The initiative emphasizes the importance of data privacy and protection. This includes promoting the use of privacy-enhancing technologies, as well as supporting the development of regulations and policies that protect personal data.
Target Audience, Microsoft secure future initiative report
The Microsoft Secure Future Initiative targets a wide range of stakeholders, including:
- Individuals:The initiative aims to empower individuals to protect themselves from cyber threats by providing access to resources, education, and tools.
- Organizations:The initiative aims to help organizations improve their cybersecurity posture by providing guidance, resources, and tools for implementing robust security measures.
- Governments:The initiative aims to collaborate with governments to develop and implement effective cybersecurity policies and regulations.
- Industry Leaders:The initiative aims to engage industry leaders in promoting best practices, developing new technologies, and fostering collaboration on cybersecurity initiatives.
- Researchers and Academics:The initiative aims to support research and development of new technologies and solutions for enhancing cybersecurity.
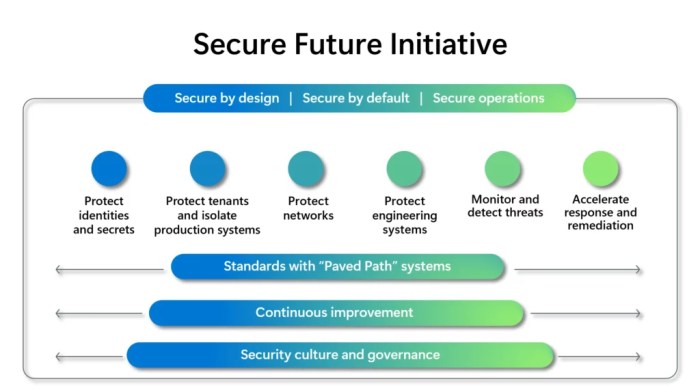
Key Components of the Initiative
The Microsoft Secure Future Initiative is a multifaceted endeavor that aims to empower individuals and organizations to build a more secure digital world. This initiative encompasses a range of key components, each playing a crucial role in achieving its objectives.
The Microsoft Secure Future Initiative Report dives into the complexities of safeguarding data in a rapidly evolving digital landscape. One of the key areas explored is the potential impact of generative AI chatbots on company data, particularly in light of the recent advancements from Google, as detailed in this article google generative ai chatbots company data.
The report emphasizes the need for robust security measures to protect sensitive information from unauthorized access and misuse, especially as AI technologies continue to advance at an unprecedented pace.
Technology’s Role in Securing the Future
Technology is the cornerstone of the Microsoft Secure Future Initiative. The initiative leverages cutting-edge technologies to enhance security and privacy across various aspects of the digital landscape. This includes:
- Advanced Threat Detection and Response:Microsoft employs sophisticated AI-powered security solutions to proactively identify and respond to emerging threats, including zero-day attacks and advanced persistent threats (APTs). This includes real-time threat intelligence, behavioral analysis, and automated incident response capabilities.
- Zero Trust Security:The initiative embraces the Zero Trust security model, which assumes that no user or device can be implicitly trusted. This approach involves verifying every access request and enforcing least privilege access policies, minimizing the impact of potential security breaches.
- Data Privacy and Compliance:Microsoft prioritizes data privacy and compliance by offering robust data encryption, access controls, and compliance frameworks such as GDPR and HIPAA. This ensures that sensitive data is protected and used responsibly.
- Secure Software Development:The initiative emphasizes secure software development practices to mitigate vulnerabilities throughout the software development lifecycle. This includes secure coding standards, automated code analysis, and penetration testing.
Collaboration and Partnerships
Collaboration and partnerships are integral to the success of the Microsoft Secure Future Initiative. Microsoft recognizes that a secure future requires a collective effort, involving governments, industry leaders, and academic institutions.
- Industry Partnerships:Microsoft actively collaborates with leading technology companies, security vendors, and research institutions to share best practices, develop joint solutions, and advance security research. These partnerships foster innovation and accelerate the development of more secure technologies.
- Government Collaboration:Microsoft engages with governments worldwide to address cybersecurity challenges and promote responsible cybersecurity policies. This includes collaborating on initiatives to combat cybercrime, enhance cyber resilience, and foster international cybersecurity cooperation.
- Community Engagement:The initiative encourages community engagement by providing resources, training programs, and forums for cybersecurity professionals, researchers, and the general public. This fosters knowledge sharing, promotes awareness, and empowers individuals to take ownership of their digital security.
Security Threats and Challenges

The Microsoft Secure Future Initiative recognizes the ever-evolving landscape of cybersecurity threats and the increasing complexity of challenges faced by individuals, organizations, and society. The initiative aims to address these threats proactively by developing and implementing innovative solutions, fostering collaboration, and promoting responsible security practices.
The Microsoft Secure Future Initiative report highlights the critical role of data security in today’s digital landscape. As organizations grapple with evolving threats, the demand for skilled professionals like data modelers is skyrocketing. A data modeler, as defined in this data modeler job description , plays a crucial role in designing and implementing secure data architectures, ensuring that sensitive information remains protected.
The Microsoft report emphasizes the importance of investing in talent development to address this growing need, ensuring a future where data security remains a top priority.
Emerging Security Threats
The digital landscape is constantly evolving, giving rise to new security threats that demand a comprehensive and adaptive approach. These threats exploit vulnerabilities in technology, human behavior, and organizational structures, posing significant risks to individuals, organizations, and society.
- Advanced Persistent Threats (APTs):These sophisticated and persistent attacks are often carried out by nation-state actors or highly organized criminal groups, targeting sensitive data and critical infrastructure. They employ a variety of techniques, including malware, phishing, and social engineering, to gain unauthorized access and maintain a long-term presence in compromised systems.
The Microsoft Secure Future Initiative report paints a compelling picture of the evolving cyber landscape, highlighting the need for robust security measures. However, amidst these concerns, news of the iPhone SE 4’s leaked specs, as reported in this article , might have some rethinking their recent iPhone 15 purchases.
Ultimately, the report’s recommendations on strengthening security infrastructure are crucial for safeguarding our digital world, even as consumer technology continues to evolve at a rapid pace.
- Ransomware:This type of malware encrypts a victim’s data and demands payment for its decryption. Ransomware attacks have become increasingly common, targeting individuals, businesses, and even government agencies, causing significant financial losses and operational disruptions.
- Supply Chain Attacks:These attacks target the software development and distribution processes, compromising the integrity of software products and allowing attackers to gain access to sensitive information or disrupt operations. The SolarWinds attack, which targeted the software supply chain, is a prominent example of this threat.
- Data Breaches:The theft or unauthorized access to sensitive data, such as personal information, financial records, or intellectual property, can have severe consequences for individuals and organizations, leading to identity theft, financial fraud, and reputational damage.
- Zero-Day Exploits:These exploits target vulnerabilities in software that are unknown to developers and have not yet been patched. They are highly effective and can be used to gain unauthorized access to systems before security measures can be implemented.
- Social Engineering:Attackers use deception and manipulation to trick individuals into revealing sensitive information or granting access to systems. Phishing emails, fake websites, and social media scams are common examples of social engineering tactics.
- Artificial Intelligence (AI) and Machine Learning (ML) in Cybersecurity:While AI and ML offer significant opportunities to enhance cybersecurity, they also pose new challenges. Attackers can use AI to automate attacks, create more sophisticated malware, and evade traditional security measures. Conversely, defenders can use AI to detect and respond to threats more effectively.
Impact of Security Threats
The impact of security threats can be far-reaching, affecting individuals, organizations, and society as a whole.
- Individuals:Security threats can lead to identity theft, financial losses, reputational damage, and privacy violations. For example, a data breach at a healthcare provider could expose sensitive medical information, leading to identity theft and financial fraud.
- Organizations:Organizations face significant financial losses, operational disruptions, reputational damage, and legal consequences as a result of security breaches. For example, a ransomware attack could shut down critical systems, leading to production downtime and financial losses. Data breaches can also damage an organization’s reputation and erode customer trust.
- Society:Security threats can undermine trust in digital systems, hinder innovation, and disrupt critical infrastructure. For example, a cyberattack on a power grid could cause widespread blackouts, impacting essential services and economic activity.
Solutions Proposed by the Initiative
The Microsoft Secure Future Initiative aims to address the evolving security landscape by promoting a comprehensive and collaborative approach to cybersecurity.
| Security Threat | Potential Impact | Proposed Solutions |
|---|---|---|
| Advanced Persistent Threats (APTs) | Data theft, espionage, disruption of critical infrastructure | Enhanced threat intelligence, advanced threat detection and response, security automation |
| Ransomware | Data loss, financial losses, operational disruptions | Data backup and recovery, endpoint protection, security awareness training |
| Supply Chain Attacks | Compromised software, data breaches, operational disruptions | Secure software development practices, supply chain security assessments, vulnerability management |
| Data Breaches | Identity theft, financial fraud, reputational damage | Data encryption, access control, data loss prevention, incident response |
| Zero-Day Exploits | Unauthorized access, data theft, system compromise | Vulnerability management, rapid patch deployment, security updates |
| Social Engineering | Data theft, unauthorized access, system compromise | Security awareness training, multi-factor authentication, phishing detection |
| AI and ML in Cybersecurity | Automated attacks, sophisticated malware, evasion of traditional security measures | AI-powered threat detection and response, ethical development of AI in cybersecurity |
Implementation and Impact
The Microsoft Secure Future Initiative is designed to be a continuous, evolving process, with implementation strategies and timelines tailored to specific needs and challenges. The initiative’s success will be measured by its impact on cybersecurity and digital trust, and the key metrics used to track progress will provide insights into its effectiveness.
Implementation Strategies and Timelines
The initiative’s implementation involves a multi-faceted approach that leverages Microsoft’s expertise in security, technology, and partnerships. Key implementation strategies include:
- Technology Development and Deployment:Continuous development and deployment of advanced security technologies, including AI-powered threat detection, zero-trust security frameworks, and enhanced threat intelligence capabilities.
- Security Training and Education:Comprehensive training programs for customers, partners, and employees to enhance their cybersecurity awareness, skills, and knowledge.
- Industry Collaboration and Partnerships:Building strong partnerships with industry leaders, government agencies, and research institutions to foster collaboration, share best practices, and drive innovation in cybersecurity.
- Policy Advocacy and Standard Setting:Engaging in policy discussions and advocating for regulations that promote responsible cybersecurity practices and digital trust.
Timelines for the implementation of specific initiatives will vary depending on their complexity and scope. For example, the development and deployment of new security technologies may have a longer timeline compared to the implementation of training programs.
Key Metrics for Measuring Impact
The initiative’s impact will be measured through various key metrics, including:
- Reduction in Security Incidents:Tracking the number and severity of security incidents reported by customers and partners. A significant reduction in these incidents would indicate the initiative’s effectiveness in enhancing security posture.
- Improved Threat Detection and Response Times:Measuring the time it takes to detect and respond to security threats. Faster detection and response times are crucial for minimizing the impact of attacks.
- Increased Cybersecurity Awareness and Skills:Assessing the improvement in cybersecurity awareness and skills among customers, partners, and employees through surveys, training completion rates, and other relevant metrics.
- Enhanced Digital Trust and Reputation:Monitoring the perception of Microsoft’s security capabilities and digital trust among customers, partners, and industry stakeholders.
Positive Impact on Cybersecurity and Digital Trust
The Microsoft Secure Future Initiative is expected to have a significant positive impact on cybersecurity and digital trust. The initiative will contribute to:
- Strengthening Cybersecurity Posture:By implementing advanced security technologies, enhancing threat intelligence capabilities, and providing comprehensive security training, the initiative will help organizations strengthen their cybersecurity posture and mitigate risks.
- Building a More Secure Digital Ecosystem:The initiative’s focus on industry collaboration and partnership will foster a more secure digital ecosystem where organizations can share best practices, collaborate on threat intelligence, and work together to address emerging cybersecurity challenges.
- Promoting Digital Trust and Confidence:By demonstrating a strong commitment to security and digital trust, the initiative will help build confidence among customers, partners, and the wider digital community. This will be crucial for fostering a thriving digital economy.
Future Directions and Recommendations
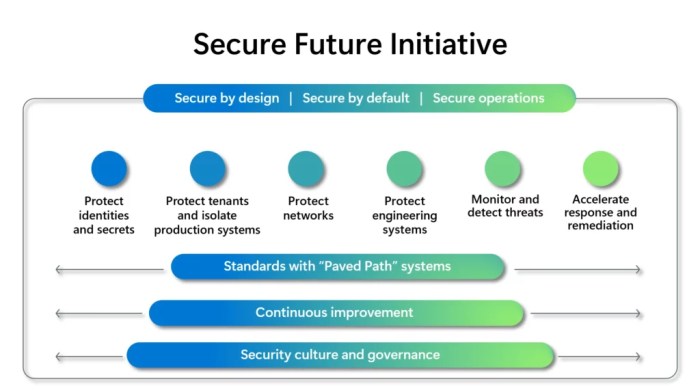
The Microsoft Secure Future Initiative has made significant strides in enhancing cybersecurity practices and fostering a more secure digital landscape. However, the ever-evolving threat landscape necessitates continuous innovation and adaptation. This section explores potential future directions for the initiative, highlighting key recommendations to further enhance its effectiveness and impact.
Expanding the Initiative’s Scope
The initiative can be expanded to encompass a broader range of stakeholders and address emerging security challenges. This expansion can include:
- Extending the initiative’s reach to smaller businesses and organizations: Smaller businesses often lack the resources and expertise to implement robust cybersecurity measures. The initiative can provide tailored guidance, tools, and resources to empower these organizations to strengthen their security posture.
- Addressing the growing threat of supply chain attacks: The initiative can collaborate with industry partners to develop best practices and tools for securing supply chains, ensuring the integrity and security of software and hardware throughout the development and distribution process.
- Integrating cybersecurity into the education system: The initiative can play a vital role in educating future generations about cybersecurity best practices, fostering a more security-conscious workforce. This can be achieved through partnerships with educational institutions, development of cybersecurity curriculum, and initiatives to promote STEM education.
Enhancing the Initiative’s Impact
To maximize the impact of the initiative, several recommendations can be implemented:
- Strengthening collaboration and partnerships: Collaboration with government agencies, industry organizations, and research institutions can enhance the initiative’s reach and impact. Joint efforts can lead to the development of shared standards, best practices, and resources.
- Promoting awareness and education: Raising public awareness about cybersecurity threats and best practices is crucial. The initiative can leverage various communication channels, including social media, online resources, and public events, to disseminate information and empower individuals to take proactive measures to protect themselves online.
- Investing in research and development: Continuous investment in research and development is essential to stay ahead of evolving threats. The initiative can support research into emerging technologies, security vulnerabilities, and innovative solutions for safeguarding digital assets.
Roadmap for Future Development
A roadmap for future development can guide the initiative’s evolution and ensure its continued success:
- Phase 1: Expansion and Outreach: Focus on expanding the initiative’s reach to smaller businesses and organizations, providing tailored guidance and resources. This phase also includes strengthening collaboration with industry partners and promoting public awareness.
- Phase 2: Deepening Impact: Invest in research and development to address emerging threats, develop new technologies, and enhance the initiative’s effectiveness. This phase also involves fostering a culture of security through education and training programs.
- Phase 3: Sustainability and Integration: Ensure the long-term sustainability of the initiative through ongoing funding, partnerships, and collaboration. This phase also focuses on integrating cybersecurity best practices into existing policies and procedures across various sectors.