New EvilProxy Phishing Attack Targets Executives
New evilproxy phishing attack targets executives – New EvilProxy phishing attacks targeting executives have emerged as a serious threat to businesses worldwide. This sophisticated attack leverages social engineering tactics and advanced technology to gain access to sensitive information, potentially causing significant financial and reputational damage. The attackers behind EvilProxy are highly motivated, often seeking to exploit vulnerabilities in email security protocols and human behavior to gain access to executive inboxes.
Understanding the methods employed by EvilProxy is crucial for organizations to implement effective prevention and mitigation strategies. This includes recognizing the signs of a phishing attack, educating employees about email security best practices, and utilizing advanced security software to detect and block malicious emails.
The Rise of EvilProxy: New Evilproxy Phishing Attack Targets Executives
The cyber threat landscape is constantly evolving, with new and sophisticated attacks emerging regularly. One such threat is the EvilProxy phishing attack, a highly targeted and insidious form of social engineering that leverages compromised legitimate websites to deceive unsuspecting victims.
EvilProxy attacks are unique in their ability to bypass traditional security measures and exploit trust, making them particularly dangerous.
It’s a wild world out there, especially for executives facing the latest evilproxy phishing attacks. But let’s take a break from the serious stuff for a moment and indulge in some fashion fun with the Barbie x Missguided collaboration , a reminder that even in the midst of cybersecurity threats, a little bit of pink and sparkle can go a long way.
Back to the serious stuff, those evilproxy attacks are nothing to joke about, so be sure to stay vigilant and protect your data.
Targeting Executives
EvilProxy attacks are often specifically tailored to target high-level executives, as they hold significant power and access to sensitive information within organizations. Attackers exploit the trust and authority associated with these individuals to gain access to valuable data and assets.
The new EvilProxy phishing attacks targeting executives are a serious threat, especially when you consider the sensitive information they often handle. This is why it’s crucial to implement robust security measures, and even consider adopting tools like enterprise project management software that can help manage access to sensitive data and track project progress securely.
These attacks are becoming increasingly sophisticated, so staying vigilant and implementing strong security practices is paramount.
Motivations Behind the Attacks
The motivations behind EvilProxy attacks are varied, but often involve financial gain, espionage, or disruption. Attackers may seek to:
- Steal confidential information, such as trade secrets, financial data, or intellectual property.
- Gain access to corporate networks and systems to launch further attacks or deploy malware.
- Disrupt business operations and cause financial losses.
- Influence business decisions or manipulate market movements.
Attack Methods and Techniques

EvilProxy, a sophisticated phishing attack, targets high-profile individuals, particularly executives, by leveraging a combination of social engineering tactics and advanced technical methods to gain access to their email accounts. These attacks are meticulously crafted to appear legitimate, exploiting vulnerabilities in human psychology and organizational security measures.
The news about the new EvilProxy phishing attack targeting executives is concerning, especially as it exploits vulnerabilities in commonly used communication channels. While I’m trying to stay informed about cybersecurity threats, I’m also taking a break to refresh my home decor by looking at some inspiring before-and-after photos of green and white main bedrooms, like this one on ExploreInsights.
After all, a peaceful home environment can help you stay focused and vigilant against online threats.
Social Engineering Tactics
Attackers employ a range of social engineering techniques to manipulate their victims into revealing sensitive information or granting access to their accounts.
- Impersonation:Attackers create convincing fake accounts that mimic the identity of trusted individuals, such as colleagues, superiors, or even CEOs. These accounts are used to send phishing emails that appear to be from a familiar source, increasing the likelihood of a response.
- Urgency and Scarcity:Phishing emails often create a sense of urgency or scarcity, urging recipients to act quickly without carefully scrutinizing the message. This tactic plays on the fear of missing out or jeopardizing important opportunities, prompting immediate action.
- Authority and Trust:Attackers may leverage authority figures or organizations to lend legitimacy to their phishing campaigns. For instance, emails may claim to be from a reputable financial institution or a government agency, demanding immediate action from the recipient.
- Curiosity and Interest:Attackers may exploit curiosity by using enticing subject lines or intriguing content to lure recipients into clicking on malicious links. These emails may promise exclusive information, valuable insights, or exciting opportunities, triggering the recipient’s desire to learn more.
Phishing Email Examples
- “Urgent Payment Request”:This email, often sent from an impersonated account, requests an immediate payment for a critical business transaction. The email may include a fabricated invoice or a link to a fake payment portal.
- “Sensitive Information Leak”:This email warns of a potential data breach, claiming that the recipient’s personal information has been compromised. It then directs the recipient to a malicious website to “verify” their information, capturing login credentials in the process.
- “Company Announcement”:This email, disguised as a legitimate company announcement, contains a malicious link that leads to a fake website designed to steal login credentials or download malware.
Technical Methods
EvilProxy employs various technical methods to enhance its effectiveness and bypass security measures.
- Spoofed Emails:Attackers use sophisticated techniques to spoof email addresses, making phishing emails appear to originate from legitimate sources. This makes it difficult for recipients to discern the true sender of the message.
- Malicious Links:Phishing emails often contain malicious links that redirect users to fake websites designed to steal credentials or download malware. These websites are meticulously crafted to resemble legitimate websites, further deceiving unsuspecting users.
- Exploiting Vulnerabilities:Attackers may exploit vulnerabilities in email systems or web browsers to gain unauthorized access to accounts. This could involve exploiting known security flaws or using social engineering techniques to trick users into granting access.
- Advanced Phishing Kits:Attackers may utilize pre-built phishing kits, which provide them with the necessary tools and resources to launch sophisticated phishing campaigns. These kits often include templates, code, and instructions for creating convincing phishing emails and websites.
Impact and Consequences
A successful EvilProxy attack can have devastating consequences for organizations, impacting sensitive data, operations, and ultimately, the company’s reputation and financial stability. Understanding the potential ramifications is crucial for implementing effective security measures and mitigating the risks.
Data Breaches and Compromised Information, New evilproxy phishing attack targets executives
The primary concern with EvilProxy attacks is the potential for data breaches. These attacks target executives, who often have access to highly sensitive information, including financial records, strategic plans, customer data, and intellectual property. A successful attack could result in the theft of this valuable data, leading to significant financial losses, legal repercussions, and reputational damage.
Disruption of Operations and Business Continuity
Beyond data theft, EvilProxy attacks can disrupt critical business operations. The compromised accounts can be used to manipulate financial transactions, alter company policies, or even launch further attacks on the organization’s network. This can lead to delays in projects, lost revenue, and significant operational inefficiencies.
Financial and Reputational Damage
The financial impact of an EvilProxy attack can be substantial. Stolen data can be sold on the dark web, leading to significant financial losses. Additionally, the cost of recovering from a data breach, including forensic investigations, legal fees, and reputational damage control, can be substantial.
The reputational damage from a data breach can be equally significant, eroding trust in the organization and impacting customer relationships. This can lead to a loss of market share, reduced investment, and decreased customer loyalty.
Examples of Real-World Impact
The consequences of EvilProxy attacks are not hypothetical. Several high-profile cases have demonstrated the real-world impact of these attacks. For example, in 2021, a major multinational corporation experienced a data breach through an EvilProxy attack, leading to the theft of sensitive financial data and customer information.
This resulted in significant financial losses, regulatory investigations, and a decline in customer trust.
Mitigating the Risks
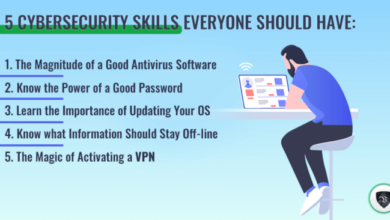
Organizations need to take proactive measures to mitigate the risks associated with EvilProxy attacks. This includes implementing robust security measures, such as multi-factor authentication, strong password policies, and regular security awareness training. Additionally, organizations should have a comprehensive incident response plan in place to address data breaches effectively.
Prevention and Mitigation

EvilProxy attacks, while sophisticated, are not insurmountable. A combination of proactive security measures and informed user behavior can significantly reduce the risk of falling victim to these phishing schemes.
Email Security Best Practices
Strong email security practices are the first line of defense against EvilProxy attacks. Implementing the following measures can help organizations protect their users and their data:
- Email Filtering and Spam Detection:Employ robust email filtering systems to block malicious emails before they reach users’ inboxes. These systems should use advanced techniques like machine learning and sandboxing to identify and quarantine suspicious emails.
- DMARC (Domain-based Message Authentication, Reporting & Conformance):DMARC is an email authentication protocol that helps prevent spoofed emails. It validates the sender’s domain and ensures that emails are sent from authorized sources.
- Email Security Awareness Training:Regularly educate employees about the dangers of phishing attacks and the common tactics used by attackers. Train them to identify suspicious emails, avoid clicking on links, and report any suspicious activity.
- Multi-Factor Authentication (MFA):Implement MFA for all email accounts. This adds an extra layer of security by requiring users to provide additional authentication factors, such as a code sent to their phone, before they can access their accounts.
User Awareness and Education
User awareness is a crucial component of any successful security strategy. Educating users about the tactics used by EvilProxy attackers can significantly reduce their vulnerability:
- Recognize Spoofed Emails:Attackers often use techniques to make their emails appear legitimate, such as spoofing the sender’s address or using logos and branding that mimic legitimate organizations. Train users to carefully examine the sender’s address, the content of the email, and the links provided.
- Be Suspicious of Urgent Requests:EvilProxy attacks often leverage a sense of urgency to pressure users into taking immediate action. Train users to be wary of emails that demand immediate action, especially if they involve sensitive information.
- Verify Requests:If an email asks for sensitive information, encourage users to verify the request through a separate channel, such as calling the organization directly.
- Report Suspicious Activity:Encourage users to report any suspicious emails or activity to the IT security team. Prompt reporting allows organizations to take immediate action to mitigate the risk.
Role of Security Software and Threat Intelligence
Security software and threat intelligence play a vital role in detecting and mitigating EvilProxy attacks:
- Endpoint Security Software:Install and maintain robust endpoint security software on all devices to detect and block malicious software that could be used to facilitate EvilProxy attacks.
- Network Security Monitoring:Implement network security monitoring tools to detect and analyze network traffic for suspicious activity.
- Threat Intelligence Feeds:Subscribe to threat intelligence feeds to stay informed about emerging threats and attack techniques. This information can help organizations proactively configure security controls and train users about new attack vectors.
Case Studies and Examples
The threat posed by EvilProxy attacks is real and growing. Numerous high-profile cases demonstrate the devastating impact these attacks can have on organizations, highlighting the need for robust security measures. Examining these cases provides valuable insights into the tactics used by attackers, the vulnerabilities exploited, and the effectiveness of mitigation strategies.
Real-World Examples of EvilProxy Attacks
Real-world examples of EvilProxy attacks offer concrete illustrations of the threat they pose and the vulnerabilities they exploit.
- In 2022, a major multinational corporation fell victim to an EvilProxy attack targeting its CEO. The attackers used a sophisticated phishing campaign to gain access to the CEO’s email account, sending fraudulent wire transfer requests that resulted in a significant financial loss.
The attackers leveraged social engineering techniques to create a sense of urgency and legitimacy, convincing the CEO to approve the fraudulent transactions.
- A prominent technology company experienced a data breach in 2023, resulting from an EvilProxy attack that compromised the accounts of several high-level executives. The attackers used a combination of spear-phishing emails and social engineering tactics to gain access to the executives’ accounts.
The stolen data included sensitive financial information, intellectual property, and confidential customer data. The attack caused significant reputational damage and financial losses for the company.
Analysis of Successful Mitigation Strategies
Successful mitigation strategies employed in response to EvilProxy attacks involve a combination of technological and human-centric approaches.
- Multi-factor authentication (MFA)is a crucial security measure that adds an extra layer of protection to user accounts. By requiring users to provide two or more forms of authentication, MFA makes it significantly more difficult for attackers to gain unauthorized access.
- Security awareness trainingplays a vital role in preventing EvilProxy attacks. Educating employees about phishing techniques, social engineering tactics, and best practices for identifying suspicious emails can significantly reduce the risk of falling victim to these attacks.
- Threat intelligence and monitoringare essential for identifying and responding to potential EvilProxy attacks. Organizations should actively monitor their networks for suspicious activity and leverage threat intelligence feeds to stay informed about emerging attack vectors and tactics.
- Incident response planningis critical for mitigating the impact of a successful EvilProxy attack. Organizations should have a well-defined incident response plan that Artikels the steps to be taken in the event of a breach, including containment, remediation, and recovery.
Lessons Learned
Real-world examples of EvilProxy attacks provide valuable lessons for organizations seeking to protect themselves from these threats.
- The human element is crucial:Attackers often exploit human vulnerabilities to gain access to sensitive data. It is essential to prioritize security awareness training and educate employees about the dangers of phishing and social engineering attacks.
- Defense-in-depth is essential:A layered security approach that incorporates multiple security controls, including MFA, email security solutions, and intrusion detection systems, is crucial for preventing EvilProxy attacks.
- Proactive threat intelligence is critical:Organizations should stay informed about emerging threats and attack tactics to develop effective countermeasures.
- Collaboration is key:Sharing information and best practices with other organizations can help to build a collective defense against EvilProxy attacks.