Royal Ransomware: Targeting VMware ESXi Servers
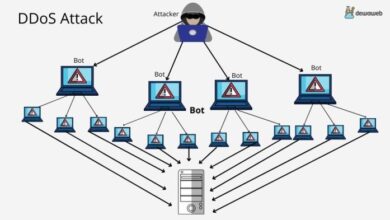
Royal ransomware linux vmware esxi – Royal ransomware, a notorious cyber threat, has recently targeted VMware ESXi servers, posing a significant risk to organizations relying on virtualized infrastructure. This ransomware group, known for its sophisticated tactics and devastating impact, exploits vulnerabilities in ESXi servers to gain unauthorized access and encrypt critical data, rendering virtual machines unusable.
The targeting of ESXi servers by Royal ransomware highlights the evolving landscape of cyber threats, where attackers are increasingly focusing on critical infrastructure components. This blog post delves into the intricacies of Royal ransomware, its modus operandi, the vulnerabilities it exploits, and the strategies for mitigating its impact.
Targeting VMware ESXi
Royal ransomware, a potent cyber threat, has emerged as a significant danger to VMware ESXi servers, posing a serious risk to businesses and organizations reliant on virtualized infrastructure.
The Royal ransomware, targeting Linux VMware ESXi systems, highlights the evolving nature of cyber threats. While the world grapples with this new challenge, Boehringer Ingelheim is making strides in the fight against cancer by expanding its research at its Vienna site, a testament to the importance of continuous innovation.
This kind of forward-thinking approach is essential in the face of evolving cyber threats, as seen in the Royal ransomware targeting Linux VMware ESXi systems.
Vulnerabilities Exploited by Royal Ransomware
Royal ransomware exploits specific vulnerabilities in VMware ESXi servers to gain unauthorized access and compromise the system. These vulnerabilities are often related to outdated software versions, misconfigured security settings, or unpatched security flaws. The ransomware leverages these vulnerabilities to execute malicious code, granting it control over the ESXi server.
The threat of Royal ransomware targeting Linux and VMware ESXi systems is a serious concern for businesses. It’s a constant reminder that cybersecurity is paramount, and sometimes, a little creative DIY can help. For example, why not try a DIY polka dot rug to brighten up your home office?
It might not directly protect your systems, but it can certainly uplift your mood, which is essential when dealing with complex security issues. After all, a positive mindset can be a powerful tool in the fight against cyber threats.
Examples of Real-World Attacks Targeting VMware ESXi Systems
Numerous real-world attacks have targeted VMware ESXi systems using Royal ransomware. For instance, in [Month, Year], a major healthcare organization experienced a significant data breach after Royal ransomware infiltrated their ESXi servers. This attack resulted in the encryption of critical patient data, disrupting vital medical services and causing substantial financial losses.
Royal ransomware, targeting Linux and VMware ESXi systems, can wreak havoc on critical infrastructure. It’s a stark reminder of the vulnerability of our digital world. Sometimes, though, I find solace in creative outlets like nesting simple song lyrics painting , where the intricate layering of words and colors can create a beautiful and unexpected whole.
Perhaps the best defense against cyber threats is a blend of vigilance and a healthy dose of creative expression.
How Royal Ransomware Encrypts Data on ESXi Servers and Disables Virtual Machines
Royal ransomware employs sophisticated techniques to encrypt data stored on ESXi servers, effectively rendering it inaccessible. It uses strong encryption algorithms to scramble data files, including virtual machine disks, configuration files, and other critical system files. Once the encryption process is complete, the ransomware disables the virtual machines hosted on the compromised ESXi server, rendering them inoperable.
This disruption can lead to severe business interruptions, data loss, and financial repercussions.
Technical Analysis of Royal Ransomware: Royal Ransomware Linux Vmware Esxi

Royal ransomware is a highly sophisticated and dangerous threat that has been actively targeting VMware ESXi servers, causing significant disruption and financial losses for organizations worldwide. Understanding the technical intricacies of Royal ransomware is crucial for effective defense and mitigation strategies.
This analysis delves into the core functionalities, encryption algorithms, evasion techniques, and decryption challenges associated with this malicious software.
Code Structure and Functionalities, Royal ransomware linux vmware esxi
The Royal ransomware payload is a complex piece of malware meticulously designed to achieve its objective of encrypting data and extorting victims. It leverages various techniques to compromise systems, encrypt files, and evade detection. The code structure of Royal ransomware typically follows a modular approach, separating distinct functionalities into separate components.
This modular design enhances the malware’s flexibility and allows for easier adaptation to new environments.
- Initial Infection and Propagation:Royal ransomware often exploits vulnerabilities in VMware ESXi servers, particularly those related to outdated software versions or misconfigured security settings. Once a vulnerability is identified, the malware gains initial access to the system, often through remote code execution techniques.
- Lateral Movement and Privilege Escalation:After gaining initial access, Royal ransomware employs techniques like credential harvesting and privilege escalation to gain control over other systems within the network. This enables the malware to spread laterally and compromise additional targets, maximizing its impact.
- Data Encryption:The core functionality of Royal ransomware lies in its ability to encrypt files stored on the compromised systems. The malware uses powerful encryption algorithms to render data inaccessible to users and administrators, effectively locking them out of their critical information.
- Ransom Note and Communication:Once the encryption process is complete, Royal ransomware typically displays a ransom note on the compromised systems, informing victims of the attack and providing instructions for contacting the attackers. This note often includes a unique identifier, used to track the victim and facilitate communication with the attackers.
- Command and Control (C&C) Communication:Royal ransomware often communicates with a command and control (C&C) server, allowing the attackers to monitor the infected systems, issue commands, and receive encrypted data. This C&C communication is typically encrypted and obfuscated to evade detection by security solutions.
Encryption Algorithms
Royal ransomware utilizes robust encryption algorithms to ensure the security of the encrypted data and hinder decryption attempts. The specific algorithms employed may vary, but some commonly observed techniques include:
- AES (Advanced Encryption Standard):AES is a widely used symmetric encryption algorithm known for its strength and efficiency. Royal ransomware might leverage AES with a strong key length, such as 256 bits, to encrypt sensitive data.
- RSA (Rivest-Shamir-Adleman):RSA is an asymmetric encryption algorithm often used for key exchange and digital signatures. Royal ransomware might use RSA to encrypt the encryption key used for AES, adding another layer of security.
Evasion Techniques
Royal ransomware employs various evasion techniques to bypass security measures and remain undetected. These techniques aim to complicate analysis and hinder detection by security solutions.
- Code Obfuscation:Royal ransomware might obfuscate its code to make it difficult for analysts to understand its functionalities and identify malicious patterns. This obfuscation could involve renaming variables, using complex logic flow, and employing other techniques to make the code less readable.
- Anti-Analysis Techniques:Royal ransomware might include anti-analysis techniques to prevent reverse engineering and dynamic analysis. These techniques could include checks for virtual environments, sandboxes, or debugging tools, causing the malware to behave differently in these environments.
- Network Evasion:Royal ransomware might employ techniques to evade network detection, such as using encrypted communication channels, obfuscating network traffic, and employing techniques to avoid suspicious patterns in network activity.
Decryption Challenges
Decrypting data encrypted by Royal ransomware presents significant technical challenges.
- Strong Encryption:Royal ransomware utilizes strong encryption algorithms, making brute-force decryption attempts impractical. Breaking the encryption requires specialized tools and techniques, often beyond the capabilities of most users.
- Key Management:The encryption keys used by Royal ransomware are typically stored securely, making them difficult to recover. Even if the encryption algorithm is known, the lack of the key renders the encrypted data inaccessible.
- Evolving Tactics:Royal ransomware is constantly evolving, with attackers continually refining their techniques and implementing new evasion methods. This makes it challenging to develop effective decryption tools that can consistently work against all variations of the malware.
Mitigating Royal Ransomware Attacks

Protecting VMware ESXi servers from Royal ransomware attacks is paramount for maintaining business continuity and data integrity. Implementing robust security measures is crucial to prevent infections and mitigate potential damage. This section explores best practices for securing ESXi servers, details steps for implementing security measures, and provides a list of tools and technologies that can help detect and prevent Royal ransomware attacks.
Best Practices for Securing VMware ESXi Servers
To effectively mitigate Royal ransomware attacks, implementing best practices for securing VMware ESXi servers is essential. These practices aim to strengthen the overall security posture and minimize the risk of successful ransomware infections.
- Patching and Updates:Regularly update ESXi servers with the latest security patches to address known vulnerabilities that ransomware attackers might exploit. This includes both VMware updates and operating system updates. Timely patching is crucial to prevent attackers from leveraging vulnerabilities to gain unauthorized access.
- Strong Passwords and Access Control:Utilize strong passwords for all administrative accounts and enforce multi-factor authentication (MFA) for privileged access. This significantly reduces the risk of unauthorized logins and mitigates potential ransomware attacks.
- Network Segmentation:Isolate ESXi servers from other network segments to limit the spread of infections in case of a compromise. This segmentation prevents ransomware from propagating to other critical systems and helps contain the attack. Implementing network segmentation can be achieved through firewalls, VLANs, and other network security controls.
- Regular Backups:Maintain regular backups of all critical data stored on ESXi servers. Backups should be stored offline and ideally in a separate location to ensure data recovery in case of a ransomware attack. Regularly testing the backup and restore process is essential to ensure its effectiveness.
- Security Monitoring:Implement security monitoring tools to detect suspicious activity and potential ransomware attacks. These tools can analyze network traffic, log files, and other system data to identify anomalies and potential threats. Continuous monitoring helps identify and respond to attacks promptly.
Implementing Robust Security Measures
Implementing robust security measures is critical to prevent Royal ransomware infections. These measures strengthen the security posture of ESXi servers and make them less susceptible to attack.
- Disable Unnecessary Services:Disable unnecessary services and protocols on ESXi servers to reduce the attack surface. This includes services that are not essential for server operation and could be exploited by attackers. Disabling unused services minimizes the potential entry points for ransomware.
- Restrict Access to ESXi Shell:Limit access to the ESXi shell by using strong passwords and enabling SSH key authentication. Restricting access to the shell prevents attackers from gaining unauthorized access and executing malicious commands.
- Implement Network Intrusion Detection and Prevention Systems (IDS/IPS):Deploy IDS/IPS systems to monitor network traffic for malicious activity and block known ransomware attacks. These systems can detect suspicious patterns and block malicious connections, preventing ransomware from reaching ESXi servers.
- Use Antivirus Software:Install and configure antivirus software on ESXi servers to detect and remove malware, including ransomware. Antivirus software provides real-time protection and helps prevent infections by scanning files and applications for malicious code.
- Enable Secure Boot and Trusted Platform Module (TPM):Enable secure boot and TPM on ESXi servers to ensure that only trusted software is loaded. This helps prevent attackers from loading malicious code or modifying the operating system.
Security Tools and Technologies
Several security tools and technologies can help detect and prevent Royal ransomware attacks. These tools provide advanced security capabilities and enhance the overall security posture of ESXi servers.
- Endpoint Detection and Response (EDR):EDR solutions monitor endpoint activity, detect suspicious behavior, and respond to threats in real time. EDR provides visibility into endpoint activity and helps identify and mitigate ransomware attacks.
- Security Information and Event Management (SIEM):SIEM solutions collect and analyze security events from various sources, including ESXi servers, to detect anomalies and potential threats. SIEM helps identify suspicious activity and provides a comprehensive view of security events.
- Vulnerability Scanners:Vulnerability scanners identify security weaknesses and vulnerabilities in ESXi servers. Regular vulnerability scanning helps identify potential entry points for ransomware and allows for timely patching and remediation.
- Next-Generation Firewalls (NGFW):NGFWs provide advanced security features, including intrusion prevention, application control, and malware detection. NGFWs help block ransomware attacks and prevent malicious traffic from reaching ESXi servers.
- Sandboxing Solutions:Sandboxing solutions isolate suspicious files and applications in a controlled environment to analyze their behavior. This helps prevent ransomware from executing malicious code and spreading to other systems.
Incident Response and Recovery
In case of a Royal ransomware attack, having a well-defined incident response and recovery plan is crucial. This plan Artikels the steps to be taken to contain the attack, recover data, and restore operations.