Secure IoT: Protecting Sensors with Microsoft Defender for IoT
Secure iot microsoft defender iot sensors – Secure IoT: Protecting Sensors with Microsoft Defender for IoT takes center stage as the Internet of Things (IoT) continues to expand, bringing with it a wave of connected devices and the inherent security risks that come with them. Microsoft Defender for IoT emerges as a crucial tool for safeguarding this burgeoning landscape, offering a comprehensive security platform designed to protect your IoT environment from a myriad of threats.
The need for robust security solutions has never been more critical. With the ever-increasing number of connected devices, the attack surface for malicious actors has expanded exponentially. Microsoft Defender for IoT addresses these challenges head-on, providing a powerful suite of features that encompass threat detection, vulnerability assessment, and device management.
This comprehensive approach ensures that your IoT infrastructure is fortified against the latest security threats, enabling you to confidently embrace the transformative potential of the connected world.
Introduction to Secure IoT with Microsoft Defender for IoT
The Internet of Things (IoT) is rapidly transforming the way we live, work, and interact with the world around us. Connected devices are becoming increasingly ubiquitous, ranging from smart homes and wearables to industrial automation and critical infrastructure. This interconnectedness offers immense potential for innovation and efficiency, but it also introduces significant security challenges.
IoT devices are often designed with limited security features and can be vulnerable to various threats, including malware, data breaches, and denial-of-service attacks. The consequences of such attacks can be severe, ranging from financial losses and privacy violations to disruption of critical services and even physical harm.
Microsoft Defender for IoT is a comprehensive security platform designed to address the unique security needs of IoT environments. It provides a range of capabilities to protect connected devices, networks, and data from emerging threats.
Key Features of Microsoft Defender for IoT
Microsoft Defender for IoT offers a robust suite of security features to safeguard IoT environments. Here are some key capabilities:
- Device Discovery and Inventory:Microsoft Defender for IoT automatically discovers and inventories all connected devices on your network, providing visibility into your IoT ecosystem. This enables you to identify and manage all devices, regardless of their manufacturer or operating system.
- Vulnerability Assessment:The platform continuously assesses the security posture of your IoT devices, identifying vulnerabilities and providing remediation guidance. It helps you proactively address security weaknesses and prevent exploitation by attackers.
- Anomaly Detection and Threat Intelligence:Microsoft Defender for IoT uses advanced machine learning algorithms to detect suspicious activity and anomalies in your IoT environment. It correlates data from multiple sources to identify potential threats and provides real-time alerts to security teams.
- Network Segmentation and Access Control:The platform allows you to segment your network and control access to sensitive devices and data. This helps to limit the impact of security breaches by isolating vulnerable devices and preventing unauthorized access.
- Security Policy Enforcement:Microsoft Defender for IoT enforces security policies across your IoT environment, ensuring that devices comply with your organization’s security standards. This helps to prevent unauthorized configuration changes and maintain a secure operating environment.
Key Features of Microsoft Defender for IoT

Microsoft Defender for IoT is a comprehensive security solution designed to protect your Internet of Things (IoT) devices and infrastructure from various threats. It offers a range of features that work together to provide robust security, including threat detection, vulnerability assessment, and device management.
Threat Detection
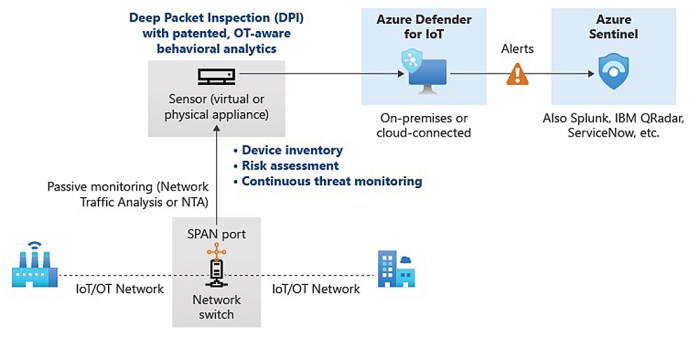
Microsoft Defender for IoT uses a combination of sensors, data analysis, and machine learning (ML) to detect suspicious activities and potential threats across your IoT environment. Sensors collect real-time data from devices, networks, and applications, providing valuable insights into the behavior of your IoT infrastructure.
This data is then analyzed using advanced algorithms to identify anomalies and potential threats that might otherwise go unnoticed.
Vulnerability Assessment
Microsoft Defender for IoT performs continuous vulnerability assessments to identify weaknesses in your IoT devices and infrastructure. These assessments can detect vulnerabilities that could be exploited by attackers, allowing you to prioritize remediation efforts and strengthen your overall security posture.
The platform leverages a comprehensive database of known vulnerabilities and security best practices to conduct these assessments effectively.
Device Management
Microsoft Defender for IoT offers centralized device management capabilities, allowing you to control and monitor your IoT devices effectively. This includes features for device inventory management, access control, firmware updates, and configuration management. By managing your IoT devices centrally, you can ensure that they are properly configured, up-to-date with the latest security patches, and protected against unauthorized access.
Implementing Microsoft Defender for IoT: Secure Iot Microsoft Defender Iot Sensors
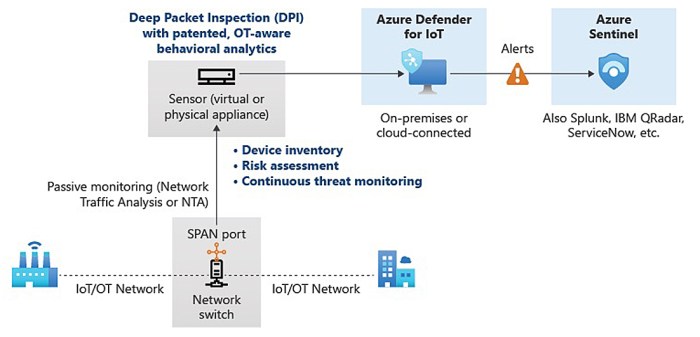
Implementing Microsoft Defender for IoT involves a strategic approach to bolstering security in your IoT environment. This process entails deploying and configuring the solution, integrating it seamlessly with your existing infrastructure, and establishing comprehensive security policies to safeguard your connected devices and data.
Deployment and Configuration
The initial step in implementing Microsoft Defender for IoT is deployment and configuration. This involves setting up the solution in your network and customizing it to meet your specific security needs.
- Installation and Configuration:Microsoft Defender for IoT can be deployed as a cloud-based service or as a virtual appliance on-premises. The deployment process involves installing the necessary software and configuring the solution to connect to your IoT network. This includes specifying the network segments, devices, and protocols you want to monitor.
- Agent Deployment:For enhanced visibility and control, you can deploy agents on your IoT devices. These agents collect data on device activity, network traffic, and security events, providing a comprehensive view of your IoT environment. Agent deployment can be automated or manual, depending on your infrastructure and device types.
- Policy Configuration:Microsoft Defender for IoT offers flexible policy configuration options to tailor security rules to your specific requirements. You can define security policies to control access to devices, enforce data protection rules, and detect suspicious activities. These policies can be based on predefined templates or customized to match your unique IoT environment.
Integration with Existing IoT Infrastructure
Integrating Microsoft Defender for IoT with your existing IoT infrastructure is crucial for achieving a unified security posture. This integration ensures seamless data flow and consistent monitoring across your connected devices.
- Network Integration:Microsoft Defender for IoT supports various network protocols, including TCP/IP, UDP, and MQTT, allowing it to integrate seamlessly with your existing network infrastructure. The solution can monitor network traffic and detect anomalies, providing insights into potential threats.
- Device Integration:Microsoft Defender for IoT can integrate with a wide range of IoT devices, including sensors, actuators, and gateways. This integration enables the solution to collect data from devices, monitor their activity, and enforce security policies.
- Third-Party Integration:Microsoft Defender for IoT offers integration with various third-party security tools and platforms, allowing you to extend its capabilities and enhance your overall security posture. This includes integrations with SIEM systems, threat intelligence feeds, and other security solutions.
Security Policies and Rules, Secure iot microsoft defender iot sensors
Implementing robust security policies and rules is fundamental to protecting your IoT environment. These policies define access control, data protection measures, and security guidelines to safeguard your connected devices and data.
- Access Control:Microsoft Defender for IoT allows you to define granular access control policies to regulate device connectivity and communication. You can specify which devices are allowed to communicate with each other, limiting potential attack vectors and unauthorized access.
- Data Protection:Data protection is paramount in IoT environments. Microsoft Defender for IoT enables you to enforce data encryption policies, ensuring that sensitive data is protected during transmission and storage. You can also configure policies to prevent unauthorized data access and manipulation.
- Security Monitoring and Response:Microsoft Defender for IoT provides comprehensive security monitoring and response capabilities. You can configure alerts and notifications to be triggered when suspicious activities are detected, allowing you to respond promptly to potential threats. This includes real-time threat detection, incident investigation, and remediation actions.
Securing your IoT devices is crucial, and Microsoft Defender for IoT offers a comprehensive solution for managing and protecting your connected sensors. But even with robust security measures, you still need to protect the credentials used to access these systems.
That’s where tools like password managers built for teams come in handy, ensuring secure storage and management of sensitive login information. By implementing a layered approach that combines Microsoft Defender for IoT with a reliable password manager, you can significantly enhance the overall security posture of your IoT ecosystem.
Protecting IoT Sensors with Microsoft Defender for IoT
Protecting IoT sensors from cyberattacks is paramount, as they are often the gateway to critical infrastructure and sensitive data. Microsoft Defender for IoT provides a comprehensive suite of security measures designed to safeguard these vital components.
Keeping your IoT devices secure is more important than ever, and Microsoft Defender for IoT is a great tool for managing and protecting your sensors. It’s interesting to see how regulations can influence product design, though, like with the recent Apple iPad Pro not including a charger in some countries.
While it’s great to see a focus on reducing e-waste, it does highlight the need for manufacturers to consider the full user experience when making these decisions. In the context of IoT security, it’s important to ensure that devices are designed with security in mind from the start, and that users have the resources they need to keep their devices safe.
Sensor Data Integrity and Availability
Microsoft Defender for IoT utilizes various techniques to ensure the integrity and availability of sensor data. This includes:
- Anomaly Detection:By analyzing sensor data patterns, Microsoft Defender for IoT can identify anomalies that might indicate malicious activity. For example, unusual sensor readings or sudden changes in data transmission frequency could trigger alerts. This allows for early detection of attacks aimed at manipulating sensor data.
- Data Validation:Microsoft Defender for IoT can verify the authenticity and integrity of sensor data by checking for inconsistencies or discrepancies. This involves comparing received data with expected values, verifying data signatures, and checking for tampering. This helps prevent attackers from injecting false data or altering existing sensor readings.
Securing your IoT devices is crucial, especially when they collect sensitive data. Microsoft Defender for IoT provides a comprehensive solution, monitoring your sensors and network for suspicious activity. But before you can connect your devices, you’ll need to create a new access point name on your Android device, which can be done by following the steps outlined in this helpful guide: create a new access point name on your android device.
Once your network is set up, you can confidently integrate your IoT sensors and leverage Microsoft Defender for IoT’s powerful security features.
- Secure Communication Channels:Microsoft Defender for IoT enforces secure communication protocols between sensors and the cloud platform. This includes using encryption, authentication, and authorization mechanisms to protect data in transit. This prevents unauthorized access to sensor data and ensures that only legitimate devices can communicate with the platform.
- Real-Time Monitoring and Alerting:Microsoft Defender for IoT continuously monitors sensor data and communication patterns for suspicious activities. When anomalies or security breaches are detected, it generates real-time alerts to security teams. This allows for prompt response and mitigation of threats before they cause significant damage.
Securing Sensor Communication Channels
- Encryption:Implementing encryption for all sensor data communication ensures that even if data is intercepted, it remains unreadable to unauthorized parties. Microsoft Defender for IoT supports various encryption protocols, including TLS/SSL, to protect sensitive sensor data in transit.
- Authentication and Authorization:Microsoft Defender for IoT uses strong authentication mechanisms to verify the identity of devices and users accessing sensor data. This prevents unauthorized access and ensures that only legitimate entities can communicate with sensors. It also implements granular access control to limit access to sensor data based on user roles and permissions.
- Secure Tunneling:Creating secure tunnels between sensors and the cloud platform provides an encrypted and isolated communication channel. This protects sensor data from eavesdropping or man-in-the-middle attacks, ensuring secure and reliable data transmission.
Protecting Sensitive Sensor Data
- Data Segmentation:Implementing data segmentation isolates sensor data based on sensitivity levels. This ensures that only authorized users and applications have access to specific data sets. This prevents unauthorized access to sensitive data and minimizes the impact of potential breaches.
- Data Masking and Tokenization:Microsoft Defender for IoT allows for data masking and tokenization to protect sensitive information. This involves replacing sensitive data with random characters or tokens, making it unreadable to unauthorized parties while maintaining data integrity and functionality.
- Access Control Lists (ACLs):Implementing ACLs on sensors and network devices limits access to sensor data based on specific rules. This allows for granular control over who can access what data, enhancing data security and preventing unauthorized access.
Real-World Use Cases of Microsoft Defender for IoT
Microsoft Defender for IoT is a powerful security solution that helps organizations protect their IoT devices and infrastructure from cyberattacks. The platform offers a comprehensive suite of features that enable organizations to detect, investigate, and respond to threats in real time.
In this section, we’ll explore some real-world use cases of Microsoft Defender for IoT, showcasing how the platform has been successfully implemented in various industries.
Securing Critical Infrastructure
The increasing reliance on IoT devices in critical infrastructure sectors, such as energy, transportation, and healthcare, has raised concerns about security vulnerabilities. Microsoft Defender for IoT helps address these concerns by providing a robust security solution for critical infrastructure environments.
“Microsoft Defender for IoT helps us protect our critical infrastructure from cyberattacks by providing real-time visibility into our network and devices. We can now quickly identify and respond to threats, ensuring the safety and reliability of our operations.”
CIO of a major energy company.
Protecting Industrial Control Systems
Industrial control systems (ICS) are often targeted by attackers due to their critical role in industrial processes. Microsoft Defender for IoT provides comprehensive protection for ICS environments, helping organizations to mitigate the risk of cyberattacks.
“Microsoft Defender for IoT has been instrumental in improving the security of our ICS environment. The platform provides us with the insights and tools we need to identify and respond to threats, ensuring the safety and continuity of our operations.”
Security Manager of a manufacturing company.
Securing Smart Devices
Smart devices are becoming increasingly popular in homes, businesses, and cities. However, these devices are often vulnerable to security threats. Microsoft Defender for IoT helps secure smart devices by providing a comprehensive security solution that protects against malware, vulnerabilities, and other threats.
“Microsoft Defender for IoT has enabled us to secure our smart devices and protect our customers’ privacy. The platform provides us with the tools and insights we need to identify and respond to threats, ensuring the safety and reliability of our devices.”
CEO of a smart home technology company.
Future Trends in Secure IoT
The landscape of secure IoT is constantly evolving, driven by technological advancements, changing security threats, and growing adoption across industries. Emerging trends are shaping the future of secure IoT, paving the way for more robust, resilient, and intelligent systems.
The Role of Edge Computing
Edge computing is a crucial component of secure IoT, enabling data processing and analysis closer to the source. By offloading processing tasks from the cloud to edge devices, edge computing reduces latency, enhances real-time decision-making, and improves data privacy. Edge computing enables secure IoT by:
- Reduced Latency and Improved Responsiveness:Edge computing minimizes the time it takes for data to travel to the cloud and back, resulting in faster response times and more efficient operations. This is critical for applications that require real-time data analysis, such as autonomous vehicles or industrial automation.
- Enhanced Data Privacy and Security:By processing data at the edge, sensitive information remains closer to the source, reducing the risk of data breaches during transmission. This is particularly important for industries with strict data privacy regulations, such as healthcare or finance.
- Improved Resilience and Fault Tolerance:Edge computing distributes processing power across multiple devices, making the system more resilient to failures. If one device fails, other edge devices can take over, ensuring continued operation.
Blockchain for Secure IoT
Blockchain technology offers a decentralized and transparent ledger system that can enhance security in IoT environments. Blockchain enables secure IoT by:
- Immutable Data Records:Blockchain’s decentralized nature ensures that data is immutable, meaning it cannot be altered or deleted after it is recorded. This provides a tamper-proof record of all transactions and events within the IoT ecosystem, fostering trust and accountability.
- Secure Data Sharing and Collaboration:Blockchain facilitates secure data sharing between multiple parties without the need for a central authority. This enables collaborative efforts in IoT projects while maintaining data integrity and privacy.
- Improved Device Authentication and Access Control:Blockchain can be used to authenticate devices and establish secure access control mechanisms. This prevents unauthorized access to sensitive data and resources, enhancing the overall security of the IoT network.
Zero-Trust Security Models
Zero-trust security models are becoming increasingly relevant in the context of secure IoT. This approach assumes that no device or user can be trusted by default, requiring strict verification and authorization before granting access to network resources. Zero-trust security models enhance secure IoT by:
- Enhanced Device Authentication and Authorization:Zero-trust models enforce rigorous authentication and authorization protocols for all devices and users accessing the network. This prevents unauthorized access and data breaches, even if a device is compromised.
- Continuous Monitoring and Threat Detection:Zero-trust models continuously monitor network traffic and user behavior, detecting anomalies and suspicious activities. This proactive approach helps identify and mitigate threats before they can cause significant damage.
- Segmentation and Isolation:Zero-trust models segment the network into smaller, isolated zones, limiting the impact of a breach to a specific area. This prevents attackers from gaining access to critical data and systems by moving laterally within the network.
Regulatory Frameworks and Industry Standards
Regulatory frameworks and industry standards play a crucial role in promoting secure IoT development and deployment. These guidelines provide a common set of principles and best practices to ensure the security and privacy of IoT devices and data. Examples of key regulatory frameworks and industry standards include:
- General Data Protection Regulation (GDPR):This European Union regulation sets strict guidelines for the collection, processing, and storage of personal data, including data collected by IoT devices. GDPR mandates data minimization, consent, and transparency, promoting data privacy and security in IoT applications.
- California Consumer Privacy Act (CCPA):Similar to GDPR, CCPA provides California residents with greater control over their personal data, including data collected by IoT devices. It requires businesses to provide consumers with clear information about how their data is collected, used, and shared.
- NIST Cybersecurity Framework (CSF):Developed by the National Institute of Standards and Technology (NIST), CSF provides a framework for organizations to manage cybersecurity risks across their operations, including IoT deployments. It offers a structured approach to identifying, assessing, and mitigating security vulnerabilities.
- ISO/IEC 27001:This international standard specifies requirements for an information security management system (ISMS). It provides a comprehensive framework for organizations to establish, implement, maintain, and continuously improve their information security practices, ensuring the security of IoT devices and data.