data security
-
Cybersecurity

Spear Phishing vs Phishing: Whats the Difference?
Spear phishing vs phishing – two terms that often get thrown around together, but are they really the same thing?…
Read More » -
Cybersecurity
Zero Trust Security: A Cheat Sheet
Zero trust security a cheat sheet – Zero Trust Security: A Cheat Sheet sets the stage for this enthralling narrative,…
Read More » -
Cybersecurity

Generative AI Ransomware Threats UK: A Growing Concern
Generative AI ransomware threats UK are a growing concern, as the UK’s reliance on AI technologies increases. Imagine a world…
Read More » -
Cybersecurity

Massive Ransomware Operation Targets VMware ESXi
Massive ransomware operation targets VMware ESXi, a chilling headline that sent shockwaves through the tech world. This attack wasn’t just…
Read More » -
Technology
EDM Cloud Data Management Report: A Comprehensive Guide
The EDM cloud data management report is a critical resource for businesses seeking to leverage the power of cloud technology…
Read More » -
Data Management
Top Data Governance Tools: Mastering Your Data Landscape
Top data governance tools are essential in today’s data-driven world, where organizations are grappling with increasing volumes and complexities of…
Read More » -
AI & Machine Learning
Data Governance for AI Systems: Ensuring Responsible Use
Data governance ai systems – Data governance for AI systems is no longer a niche concern but a fundamental requirement…
Read More » -
Cybersecurity
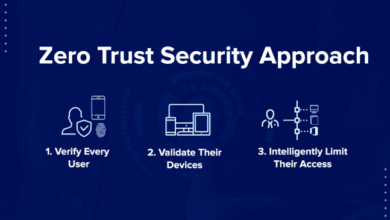
Zero Trust Security Tips: Protecting Your Digital Assets
Zero Trust security tips are essential in today’s digital landscape, where threats are constantly evolving. The traditional perimeter-based security model…
Read More » -
Data Science

Data Literacy Risks & Informatica Interview Prep
Data literacy risks informatica interview – it’s a phrase that might make you think of a job interview gone wrong.…
Read More » -
Cybersecurity

Kaspersky Report: Top Cyber Threats Facing SMBs
Kaspersky report top cyber threats smbs – Kaspersky Report: Top Cyber Threats Facing SMBs reveals a sobering reality: small and…
Read More »


