Spear Phishing vs Phishing: Whats the Difference?
Spear phishing vs phishing – two terms that often get thrown around together, but are they really the same thing? While both involve attempts to steal your personal information, there’s a crucial distinction that separates them. Spear phishing is a more targeted and sophisticated attack, aiming to exploit specific individuals or organizations, while traditional phishing casts a wider net, hoping to catch unsuspecting victims.
Understanding the differences between these two malicious tactics is essential for protecting yourself and your data.
In this blog post, we’ll dive deeper into the world of spear phishing and phishing, exploring their techniques, impact, and how to stay safe. Get ready to arm yourself with knowledge and learn how to spot these cyber threats before they strike.
Definitions and Concepts: Spear Phishing Vs Phishing
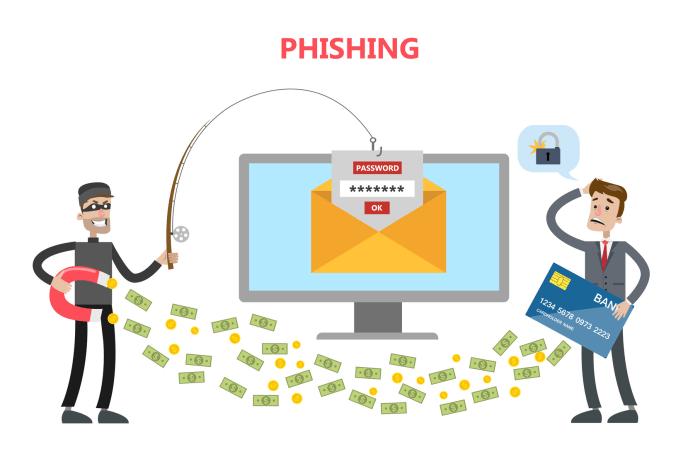
Phishing and spear phishing are cyberattacks designed to steal sensitive information, such as login credentials, financial data, or personal details. Both tactics rely on social engineering to trick victims into revealing their information, but they differ in their approach and target audience.
Spear phishing is a more targeted form of phishing, focusing on specific individuals or organizations. While both can be devastating, it’s crucial to protect your company from both. Choosing the right payroll software is essential for managing employee data and ensuring accurate payments.
For a comprehensive guide to the best payroll software for UK businesses, check out this article. By securing your payroll system and educating your employees on phishing threats, you can significantly reduce the risk of falling victim to these cyberattacks.
Defining Phishing
Phishing is a broad term encompassing various cyberattacks where attackers impersonate legitimate entities, like banks, government agencies, or popular brands, to lure victims into providing sensitive information. These attacks typically employ email, SMS messages, or websites designed to mimic legitimate sources.
Victims are often tricked into clicking malicious links or opening attachments that lead to the installation of malware or the theft of their data.
Defining Spear Phishing
Spear phishing is a highly targeted form of phishing that focuses on specific individuals or organizations. Attackers conduct thorough research to gather information about their targets, such as their job titles, interests, or recent activities. This personalized approach allows attackers to craft highly convincing and tailored phishing emails or messages that exploit vulnerabilities specific to their victims.
Spear phishing attacks are often more successful than general phishing campaigns because they are tailored to the target’s specific interests and perceived needs.
Targeting in Phishing and Spear Phishing
The key difference between phishing and spear phishing lies in their targeting strategies. Phishing attacks employ a broad approach, casting a wide net to catch as many victims as possible. They typically use generic messages that target a large audience with common themes like password resets, account verification, or prize notifications.
On the other hand, spear phishing attacks are highly specific and target individuals or organizations with specific goals in mind. Attackers may target high-profile executives, employees with access to sensitive information, or organizations with valuable data.
Techniques and Tactics

Phishing and spear phishing rely on various techniques to deceive victims and gain unauthorized access to sensitive information. Understanding these tactics is crucial to recognizing and mitigating these threats.
Common Phishing Techniques
Phishing attacks employ various techniques to trick users into revealing confidential data. Here are some common tactics:
- Email Spoofing:Phishers create emails that appear to be from legitimate sources, such as banks, online retailers, or government agencies. They mimic the sender’s email address, logo, and layout to make the email look authentic.
- Social Engineering:This technique involves manipulating people into performing actions that compromise their security. Phishers use psychological tactics, such as creating a sense of urgency or fear, to convince victims to click on malicious links or download attachments.
- Website Impersonation:Phishers create fake websites that mimic the appearance of legitimate websites, such as online banking portals or social media platforms. They then lure victims to these fake websites and steal their login credentials or financial information.
Spear Phishing Techniques
Spear phishing attacks are more targeted and personalized than general phishing attacks. They often exploit specific information about the victim, making them more likely to fall for the scam.
Spear phishing is a more targeted form of phishing, aiming to trick specific individuals by personalizing the attack. It’s like a well-crafted marketing campaign, but instead of selling products, it’s trying to steal your data. Think about how much information your Apple Watch collects – your location, heart rate, even your sleep patterns.
This is why the new features on the apple watch series 9 and apple watch ultra 2 are particularly important for security. They’re designed to protect your data and make it harder for spear phishers to get their hooks in.
So, while those shiny new watch features are tempting, it’s essential to stay vigilant about the ever-evolving threat of spear phishing.
- CEO Fraud:In this technique, phishers impersonate a company’s CEO or other high-ranking executives and send emails requesting immediate financial transactions or wire transfers. They often leverage a sense of urgency and authority to convince employees to comply with their requests.
- Whaling:This type of spear phishing attack targets high-profile individuals, such as CEOs, CFOs, and other executives. Phishers often use sophisticated social engineering tactics to gain access to sensitive information or influence decision-making.
- Targeted Social Media Attacks:Phishers may use social media platforms to gather information about their targets and craft personalized messages that exploit their interests or relationships. They may send private messages, post targeted content, or use social media advertising to reach their victims.
Impact and Consequences

Phishing and spear phishing attacks can have devastating consequences for individuals, organizations, and even entire economies. The impact of these attacks extends beyond immediate financial losses, encompassing reputational damage, legal ramifications, and even personal safety.
Financial Risks
Financial losses are the most immediate and tangible consequence of successful phishing attacks. The financial impact can be categorized into direct and indirect losses:
- Direct Losses: Direct losses include the theft of funds, credit card information, and other sensitive financial data. Phishing attacks can lead to unauthorized transactions, account closures, and identity theft, resulting in significant financial burdens for victims.
- Indirect Losses: Indirect losses can be equally substantial and may include expenses incurred to mitigate the damage caused by a phishing attack.
These costs may include:
- Hiring security experts to investigate the attack and restore compromised systems.
- Replacing stolen or compromised devices.
- Recovering lost data and restoring business operations.
- Legal fees associated with handling legal repercussions and notifying affected parties.
Reputational Damage
Beyond financial losses, phishing attacks can severely damage an organization’s reputation. The public perception of a company that has been targeted by a phishing attack can be negatively impacted, leading to:
- Loss of customer trust: Customers may lose faith in a company’s ability to protect their data and information, potentially leading to a decline in sales and market share.
- Negative media coverage: News of a successful phishing attack can damage an organization’s image and attract negative media attention, further impacting its reputation.
Spear phishing targets specific individuals with personalized messages, while phishing casts a wider net with generic emails. Both aim to trick you into giving up sensitive information, so staying vigilant is crucial. Speaking of security, I recently had to figure out the best cell plans for our Apple Watch family setup, which can be a bit of a maze! You can check out my research on best cell plans apple watch family setup , and hopefully, it’ll help you avoid any phishing scams too!
- Reduced investor confidence: Investors may lose confidence in a company’s ability to manage security risks, potentially leading to a decline in stock value.
Legal Implications
Phishing attacks can have significant legal implications, both for individuals and organizations. In many jurisdictions, phishing is considered a criminal offense, and perpetrators can face severe penalties, including:
- Criminal charges: Individuals involved in phishing attacks can face criminal charges, such as fraud, identity theft, and computer crime.
- Civil lawsuits: Victims of phishing attacks may file civil lawsuits against perpetrators to recover financial losses and damages.
- Regulatory fines: Organizations that fail to implement adequate security measures to prevent phishing attacks may face regulatory fines and penalties.
Prevention and Mitigation Strategies
Phishing attacks are a constant threat to individuals and organizations alike. However, by implementing a combination of best practices, security measures, and awareness training, it is possible to significantly reduce the risk of falling victim to these malicious schemes.
Best Practices for Individuals
Individuals play a crucial role in preventing phishing attacks. Here are some essential best practices:
- Be cautious of suspicious emails and links:Hover over links before clicking to verify their legitimacy. Look for misspellings, grammatical errors, or unusual formatting in the email. Avoid clicking on links from unknown senders or those that seem too good to be true.
- Verify the sender’s identity:If you are unsure about the sender’s identity, contact them directly through a known phone number or email address to confirm the message’s authenticity.
- Enable two-factor authentication:Two-factor authentication adds an extra layer of security by requiring a second form of verification, such as a code sent to your phone, in addition to your password. This makes it much harder for attackers to gain access to your accounts.
- Keep your software updated:Software updates often include security patches that fix vulnerabilities that attackers can exploit. Regularly update your operating system, web browser, and other software to ensure you are protected against the latest threats.
- Use strong passwords and avoid reusing them:Create unique and complex passwords for each of your online accounts. Avoid using personal information or common phrases that can be easily guessed. Consider using a password manager to help you generate and store strong passwords securely.
- Report suspicious emails:If you receive a suspicious email, report it to the sender’s organization or to your IT department. This helps to prevent others from falling victim to the same scam.
Security Measures for Organizations
Organizations have a responsibility to protect their employees and customers from phishing attacks. Here are some security measures they can implement:
- Implement email filtering and spam detection:Email filtering and spam detection tools can help to block phishing emails before they reach employees’ inboxes. These tools use various techniques, such as analyzing email content, sender reputation, and email headers, to identify and quarantine suspicious emails.
- Deploy anti-phishing software:Anti-phishing software can help to identify and block phishing websites, preventing employees from accessing them. This software uses various techniques, such as blacklisting known phishing sites, analyzing website content, and detecting suspicious website behavior.
- Use a strong password policy:Organizations should enforce a strong password policy that requires employees to use complex and unique passwords for all their accounts. This policy should also include password rotation requirements to prevent attackers from gaining access to accounts with compromised passwords.
- Conduct regular security audits:Regular security audits help to identify vulnerabilities in an organization’s security posture. These audits can help to identify weak points in email filtering, anti-phishing software, and other security measures.
- Implement incident response plans:Organizations should have a clear incident response plan in place to deal with phishing attacks. This plan should Artikel steps for identifying, containing, and recovering from phishing attacks.
Security Awareness Training
Security awareness training is crucial for mitigating phishing risks. Organizations should provide regular training to their employees on how to identify and avoid phishing attacks.
- Simulate phishing attacks:Organizations can simulate phishing attacks to test their employees’ awareness and ability to identify and report suspicious emails. This type of training helps employees learn by doing and reinforces the importance of being vigilant.
- Provide real-world examples:Training should include real-world examples of phishing attacks, highlighting the techniques used by attackers and the consequences of falling victim to these scams.
- Reinforce best practices:Training should reinforce the best practices for identifying and avoiding phishing attacks, such as being cautious of suspicious emails, verifying sender identities, and using strong passwords.
- Encourage reporting:Organizations should encourage employees to report any suspicious emails or websites they encounter. This helps to identify potential threats and prevent others from falling victim to the same scams.
Real-World Examples and Case Studies
The world of cybersecurity is constantly evolving, with new threats emerging daily. Phishing and spear phishing attacks are two of the most prevalent and successful cyberattacks. These attacks rely on social engineering, exploiting human vulnerabilities to gain access to sensitive information or systems.
Analyzing real-world examples and case studies helps us understand the impact of these attacks and develop effective countermeasures.
High-Profile Phishing and Spear Phishing Attacks, Spear phishing vs phishing
Real-world examples of phishing and spear phishing attacks highlight the devastating consequences these attacks can have on individuals and organizations. These attacks have targeted governments, businesses, and individuals, resulting in significant financial losses, data breaches, and reputational damage.
- In 2016, a spear phishing attack targeting the Democratic National Committee (DNC) resulted in the theft of sensitive emails and data, which were subsequently leaked to the public. This incident had a significant impact on the 2016 US presidential election, raising concerns about foreign interference in democratic processes.
- In 2017, the NotPetya ransomware attack, which spread through a spear phishing campaign, caused billions of dollars in damages worldwide. This attack targeted businesses across various industries, crippling their operations and causing significant disruptions.
- In 2020, a phishing campaign targeting individuals working from home during the COVID-19 pandemic led to a surge in credential theft and malware infections. These attacks exploited the increased reliance on remote work and the heightened anxiety surrounding the pandemic.
Case Studies: Lessons Learned
Analyzing case studies of successful phishing and spear phishing attacks provides valuable insights into the techniques used by attackers and the vulnerabilities exploited.
Case Study 1: The Sony Pictures Entertainment Hack
In 2014, Sony Pictures Entertainment suffered a massive cyberattack that resulted in the theft of sensitive data, including emails, scripts, and financial records. The attack was attributed to North Korea, who were believed to be retaliating for the release of the film “The Interview,” which satirized North Korean leader Kim Jong-un.
The attack exploited a vulnerability in Sony’s network and involved spear phishing emails targeting employees.
- Lessons Learned:The Sony Pictures Entertainment hack highlighted the importance of robust security measures, including multi-factor authentication, employee training, and regular security audits. It also demonstrated the need for organizations to be prepared for sophisticated attacks that may target specific individuals or departments.
Case Study 2: The Equifax Data Breach
In 2017, Equifax, a credit reporting agency, suffered a major data breach that exposed the personal information of over 147 million individuals. The breach was caused by a vulnerability in Equifax’s software, which was exploited by hackers through a phishing attack.
The attackers gained access to sensitive data, including Social Security numbers, birth dates, and addresses.
- Lessons Learned:The Equifax data breach highlighted the importance of patching vulnerabilities promptly and implementing strong security protocols. It also demonstrated the need for organizations to have a comprehensive incident response plan in place to minimize the impact of security breaches.
Case Study 3: The Target Data Breach
In 2013, Target, a major retailer, suffered a data breach that compromised the credit card information of over 40 million customers. The breach was attributed to a phishing attack that targeted a third-party vendor that had access to Target’s network.
The attackers used stolen credentials to gain access to Target’s systems and steal customer data.
- Lessons Learned:The Target data breach highlighted the importance of securing the supply chain and ensuring that all vendors have strong security practices in place. It also demonstrated the need for organizations to monitor their networks for suspicious activity and to have a robust incident response plan.