Top Security Risks Industrial IoT: Protecting Connected Factories
Top security risks industrial IoT are a growing concern as industries increasingly rely on connected devices and data. This trend, while beneficial for productivity and efficiency, creates a vulnerable landscape for cyberattacks. Imagine a scenario where a hacker disrupts a critical manufacturing process, causing significant financial losses and operational downtime.
This isn’t a far-fetched idea; it’s a reality that demands our attention.
The IIoT ecosystem is susceptible to various threats, including data breaches, device hijacking, network intrusions, and attacks on critical infrastructure. These risks can have devastating consequences, ranging from data theft and financial losses to physical damage and safety hazards. Understanding these threats and implementing robust security measures is paramount for ensuring the safety, reliability, and integrity of industrial operations.
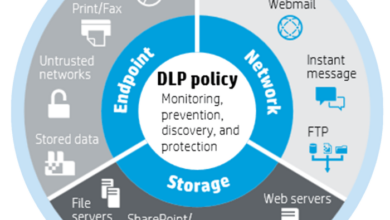
Data Security and Privacy

The Industrial Internet of Things (IIoT) brings immense benefits to industrial operations, but it also introduces new and significant security risks. One of the most critical concerns is the protection of sensitive industrial data. Data breaches and unauthorized access to this information can lead to severe consequences, including financial losses, operational disruptions, reputational damage, and even safety hazards.
Data Breaches and Unauthorized Access
Data breaches in IIoT environments can compromise sensitive information such as production data, control system configurations, and intellectual property. This information can be used by attackers to disrupt operations, steal valuable data, or even cause physical damage. Unauthorized access can occur through various means, including exploiting vulnerabilities in software, using stolen credentials, or employing social engineering techniques.
Vulnerabilities in Data Transmission Protocols and Storage Mechanisms
IIoT systems rely on various data transmission protocols and storage mechanisms, each with its own vulnerabilities. * Data Transmission Protocols:Common protocols like Modbus, OPC UA, and MQTT are often designed for efficiency rather than security. Attackers can exploit weaknesses in these protocols to intercept or modify data in transit.
Storage Mechanisms
Industrial data is often stored in databases or file systems. These systems can be vulnerable to attacks such as SQL injection, data exfiltration, and ransomware.
Data Security Best Practices for IIoT Deployments
Implementing robust data security measures is crucial for protecting IIoT systems from breaches and unauthorized access. * Secure Network Segmentation:Isolate industrial networks from public networks and implement strong firewalls to restrict access.
Strong Authentication and Authorization
Use multi-factor authentication and role-based access control to restrict access to sensitive data and resources.
Data Encryption
Encrypt data at rest and in transit to protect it from unauthorized access.
Regular Security Updates and Patching
Ensure that all devices and software are kept up-to-date with the latest security patches.
Security Monitoring and Threat Detection
Implement intrusion detection and prevention systems (IDS/IPS) to monitor network traffic for suspicious activity and respond to threats promptly.
Data Backup and Recovery
Regularly back up critical data and implement disaster recovery plans to ensure business continuity in case of a data breach.
Device Security and Integrity

The security of IIoT devices is critical to the overall security of an industrial network. IIoT devices are often deployed in harsh environments and are often not as well-secured as traditional IT systems. This makes them vulnerable to a variety of attacks, including device hijacking, data manipulation, and denial-of-service attacks.
Common Vulnerabilities in IIoT Devices
These vulnerabilities can be exploited by attackers to gain unauthorized access to devices, steal data, or disrupt operations.
- Firmware Flaws:Firmware is the software that controls the operation of an IIoT device. Firmware flaws can allow attackers to gain unauthorized access to a device, or even to take control of it.
- Weak Authentication Mechanisms:Many IIoT devices use weak authentication mechanisms, such as default passwords or easily guessable usernames and passwords.
The rise of Industrial IoT (IIoT) brings immense potential, but also exposes vulnerabilities. From unauthorized access to data breaches, safeguarding sensitive information is paramount. Choosing the right project management tool can play a vital role in this security landscape.
For instance, when comparing monday.com vs Smartsheet , their security features and compliance certifications are crucial factors to consider. Ultimately, a robust IIoT security strategy requires a multi-layered approach, incorporating secure infrastructure, strong authentication, and ongoing monitoring to mitigate these risks.
This makes it easy for attackers to gain access to devices.
Device Hijacking and Manipulation
Attackers can hijack IIoT devices and manipulate them for malicious purposes, such as:
- Data Theft:Attackers can use hijacked devices to steal sensitive data, such as production data, process control data, or intellectual property.
- Disruption of Operations:Attackers can manipulate hijacked devices to disrupt operations, such as by causing equipment to malfunction or by shutting down production lines.
- Ransomware Attacks:Attackers can use hijacked devices to launch ransomware attacks, encrypting data and demanding payment for its release.
Best Practices for Securing IIoT Devices
There are a number of best practices that can be used to secure IIoT devices:
- Secure Boot:Secure boot is a process that verifies the authenticity of the firmware that is loaded onto a device. This helps to prevent attackers from loading malicious firmware onto devices.
- Firmware Updates:Firmware updates can patch security vulnerabilities and improve the security of IIoT devices.
The top security risks in industrial IoT are a constant worry, and just like the intricate layers of a DIY quilted modern art piece, these vulnerabilities can be complex and interconnected. From data breaches to denial-of-service attacks, the potential for disruption and damage is significant.
Addressing these risks is crucial for the safe and reliable operation of industrial systems.
It is important to ensure that devices are running the latest firmware versions.
- Access Control:Access control mechanisms should be implemented to restrict access to IIoT devices. This includes using strong passwords, multi-factor authentication, and role-based access control.
- Network Segmentation:Network segmentation can help to isolate IIoT devices from other parts of the network.
This can help to prevent attackers from spreading from one device to another.
- Security Monitoring:Security monitoring tools can be used to detect suspicious activity on IIoT devices. This can help to identify and respond to attacks in a timely manner.
Network Security
Industrial control systems (ICS) networks, often used in IIoT environments, are inherently vulnerable due to their legacy design and focus on operational efficiency over security. These networks are typically built with a “flat” architecture, meaning that devices are directly connected to each other and to the internet, making them susceptible to a range of attacks.
Vulnerabilities and Impact
The interconnected nature of ICS networks creates a domino effect, where a compromise of one device can cascade throughout the entire system. This vulnerability is exacerbated by the use of outdated protocols, insecure configurations, and a lack of robust security measures.
For instance, a denial-of-service (DoS) attack can disrupt critical operations by overwhelming a system with traffic, rendering it unresponsive. This can lead to production downtime, financial losses, and safety hazards. Network intrusions, where attackers gain unauthorized access to the network, can lead to data theft, manipulation of control systems, and sabotage.
Lateral movement, the ability of attackers to move from one compromised device to another, allows them to gain deeper access to the network and expand their attack surface.
Network Security Measures
To mitigate these risks, various network security measures can be implemented:
- Firewalls: Firewalls act as a barrier between the ICS network and the external world, blocking unauthorized access and filtering incoming and outgoing traffic. They can be deployed at various levels, including perimeter firewalls, network firewalls, and host-based firewalls.
- Intrusion Detection Systems (IDS): IDS continuously monitor network traffic for malicious activity and alert security personnel when suspicious patterns are detected. They can identify potential attacks, including DoS attacks, network intrusions, and lateral movement.
- Network Segmentation: This involves dividing the ICS network into smaller, isolated segments, limiting the impact of a compromise to a single segment. By isolating critical control systems from less sensitive areas, network segmentation reduces the attack surface and prevents attackers from spreading laterally.
Operational Technology (OT) Security
The convergence of IT and OT systems in IIoT environments presents unique security challenges, demanding a comprehensive approach to safeguarding critical infrastructure.
Integrating IT and OT Systems
The integration of IT and OT systems in IIoT environments creates a complex and interconnected ecosystem. This convergence brings numerous benefits, such as enhanced efficiency, data-driven decision-making, and remote monitoring capabilities. However, it also introduces significant security risks, as vulnerabilities in one system can potentially compromise the other.
Risks of Attacks Targeting Critical Infrastructure
Attacks targeting critical infrastructure, including power grids, manufacturing processes, and transportation systems, can have devastating consequences. Cybercriminals and nation-state actors may exploit vulnerabilities in OT systems to disrupt operations, cause physical damage, or steal sensitive data. The potential impacts include:
- Service disruptions: Disrupting essential services like power generation, water treatment, or transportation networks, leading to widespread outages and economic losses.
- Physical damage: Compromising industrial control systems (ICS) to manipulate equipment, potentially causing physical damage to machinery, infrastructure, or even endangering human lives.
- Data theft: Stealing sensitive information, such as proprietary designs, manufacturing processes, or customer data, compromising intellectual property and business operations.
- Financial losses: Causing significant financial losses through production downtime, equipment damage, and reputational damage.
Securing OT Systems
Securing OT systems requires a multifaceted approach that addresses the unique characteristics of these environments.
Asset Inventory Management
A comprehensive asset inventory is crucial for understanding the OT environment’s scope and identifying potential vulnerabilities. This inventory should include:
- Device types: Identifying all devices connected to the OT network, including sensors, actuators, controllers, and PLCs.
- Software versions: Tracking software versions used on each device to identify outdated or vulnerable software.
- Network configuration: Mapping the network topology and identifying critical network segments and devices.
- Security controls: Documenting the security controls implemented on each device, including firewalls, intrusion detection systems (IDS), and access control mechanisms.
Vulnerability Assessments
Regular vulnerability assessments are essential for identifying and mitigating potential security weaknesses. These assessments should include:
- Network scanning: Identifying open ports, services, and vulnerabilities on network devices.
- Device scanning: Identifying vulnerabilities in OT devices, including firmware flaws, software bugs, and misconfigurations.
- Penetration testing: Simulating real-world attacks to assess the effectiveness of security controls and identify potential attack vectors.
Incident Response Plans
A robust incident response plan is critical for minimizing the impact of security incidents. The plan should Artikel:
- Detection: Establishing clear procedures for detecting security incidents, including monitoring logs, alerts, and unusual activity.
- Containment: Defining steps to isolate the affected systems and prevent further damage or data loss.
- Recovery: Developing procedures for restoring affected systems and data to their operational state.
- Communication: Establishing communication channels for informing stakeholders, including management, IT security teams, and relevant authorities.
Human Factors and Security Awareness
The human element plays a crucial role in IIoT security, as it’s often the weakest link in the chain. Human error and social engineering attacks can easily exploit vulnerabilities, leading to significant security breaches. It is crucial to implement robust security awareness training programs and cultivate a strong security culture within industrial organizations.
The top security risks for industrial IoT are often related to vulnerabilities in device firmware and network infrastructure. One approach to securing these systems is to implement robust database solutions, and in this context, it’s interesting to consider the benefits of what are low code databases.
These databases offer a faster development cycle, which can be critical for addressing security vulnerabilities in a timely manner. Ultimately, securing industrial IoT systems requires a multi-layered approach, including strong database security practices.
Importance of Security Awareness Training, Top security risks industrial iot
Security awareness training is essential for employees and contractors to understand their role in maintaining IIoT security. This training should cover various aspects, including:
- Identifying and reporting suspicious activities.
- Understanding common attack vectors, such as phishing emails and malicious software.
- Following best practices for secure password management and data handling.
- Recognizing the importance of physical security measures.
Best Practices for Promoting a Strong Security Culture
Creating a strong security culture requires a multi-faceted approach. Here are some best practices to consider:
- Leadership buy-in:Senior management must champion security awareness and make it a top priority.
- Regular training and education:Continuous training programs should be implemented to keep employees informed about emerging threats and best practices.
- Clear security policies and procedures:Organizations should develop and communicate clear security policies and procedures, ensuring employees understand their responsibilities.
- Incentivize security awareness:Reward employees for reporting security vulnerabilities or following best practices.
- Promote open communication:Encourage employees to report security concerns without fear of retribution.
- Regular security assessments:Conduct regular security assessments to identify vulnerabilities and ensure that security controls are effective.
Emerging Threats and Mitigation Strategies
The IIoT landscape is constantly evolving, bringing with it new security challenges. As devices become more interconnected and sophisticated, attackers are finding innovative ways to exploit vulnerabilities. This section delves into some of the most concerning emerging threats and explores effective mitigation strategies to ensure the resilience of IIoT systems.
Ransomware Attacks
Ransomware attacks pose a significant threat to IIoT systems, potentially disrupting critical operations and causing substantial financial losses. Attackers encrypt sensitive data and demand payment for its decryption. The impact of ransomware on IIoT systems can be devastating, as it can lead to production downtime, data loss, and reputational damage.
Challenges in Detecting and Mitigating Ransomware
- Lateral Movement:Ransomware can spread rapidly across interconnected devices, making it difficult to contain the infection.
- Sophisticated Techniques:Attackers are employing advanced techniques to evade detection, such as using encrypted communication channels and exploiting vulnerabilities in network protocols.
- Limited Visibility:Traditional security solutions may not be effective in detecting and mitigating ransomware attacks on IIoT systems due to the unique characteristics of these environments.
Mitigation Strategies
- Network Segmentation:Isolating critical systems from the broader network can prevent ransomware from spreading laterally.
- Regular Patching:Applying security patches promptly is crucial to address known vulnerabilities that attackers might exploit.
- Data Backup and Recovery:Maintaining regular backups of critical data allows for recovery in the event of a ransomware attack.
- Security Awareness Training:Educating employees about ransomware threats and best practices can help reduce the risk of human error.
Advanced Persistent Threats (APTs)
APTs are highly sophisticated and persistent attacks that target specific organizations with the aim of stealing sensitive data or disrupting operations. These attacks often involve multiple stages and can remain undetected for extended periods.
Challenges in Detecting and Mitigating APTs
- Stealthy Techniques:APTs employ covert techniques to evade detection, such as using custom malware and exploiting zero-day vulnerabilities.
- Long-Term Persistence:Attackers may remain undetected for months or even years, making it difficult to attribute the attack and identify the source.
- Targeted Attacks:APTs are often tailored to specific organizations, making it challenging to develop generic defenses.
Mitigation Strategies
- Threat Intelligence:Monitoring threat intelligence feeds can provide insights into emerging APT campaigns and help organizations proactively identify potential threats.
- Advanced Security Analytics:Implementing advanced security analytics tools can help detect unusual activity and identify potential APT attacks.
- Security Information and Event Management (SIEM):SIEM solutions can provide centralized logging and analysis of security events, enabling better visibility into potential APT activity.
- Security Orchestration, Automation, and Response (SOAR):SOAR platforms can automate security tasks, reducing the time it takes to respond to APT attacks.
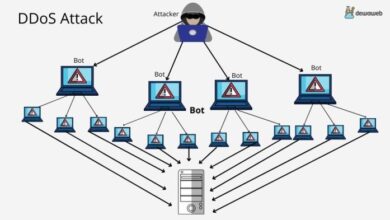
IoT Botnets
IoT botnets are networks of compromised IoT devices that are controlled by attackers. These botnets can be used for various malicious activities, such as distributed denial-of-service (DDoS) attacks, data theft, and launching ransomware attacks.
Challenges in Detecting and Mitigating IoT Botnets
- Large Scale:IoT botnets can consist of millions of compromised devices, making it challenging to identify and isolate them.
- Limited Security:Many IoT devices lack robust security features, making them easy targets for attackers.
- Distributed Nature:Botnets are often distributed across multiple locations, making it difficult to track their activity.
Mitigation Strategies
- Secure Device Configuration:Implementing strong passwords, disabling default credentials, and enabling firmware updates can help secure IoT devices.
- Network Segmentation:Isolating IoT devices from critical systems can limit the impact of botnet attacks.
- Intrusion Detection and Prevention Systems (IDS/IPS):Deploying IDS/IPS solutions can help detect and prevent botnet activity.
- Threat Intelligence:Monitoring threat intelligence feeds can provide insights into emerging botnet campaigns and help organizations identify potential threats.
Proactive Security Measures
Proactive security measures are essential for preventing and mitigating emerging threats to IIoT systems. These measures include:
- Risk Assessment:Regularly assessing the security risks to IIoT systems is crucial for identifying vulnerabilities and prioritizing mitigation efforts.
- Security Architecture Design:Implementing a secure architecture by design, including security considerations from the outset, can significantly reduce the risk of attacks.
- Secure Software Development Practices:Following secure coding practices and implementing security testing throughout the software development lifecycle can help reduce vulnerabilities in IIoT applications.
- Security Monitoring and Auditing:Continuous monitoring and regular audits can help detect suspicious activity and ensure that security controls are effective.
Incident Response Strategies
Effective incident response strategies are essential for minimizing the impact of security incidents. These strategies include:
- Incident Response Plan:Having a comprehensive incident response plan that Artikels the steps to be taken in the event of a security incident is crucial.
- Incident Response Team:Establishing a dedicated incident response team with the necessary skills and expertise can ensure a prompt and effective response to security incidents.
- Communication and Coordination:Clear communication and coordination among stakeholders, including IT security teams, operations teams, and management, are essential for a successful incident response.
- Post-Incident Review:Conducting a post-incident review to identify lessons learned and improve incident response processes is crucial for continuous improvement.
Regulatory Compliance and Standards: Top Security Risks Industrial Iot
The industrial internet of things (IIoT) brings significant benefits to organizations, but it also introduces new security risks. Adhering to industry standards and regulatory requirements is crucial for ensuring the safety, reliability, and integrity of IIoT systems. These standards provide a framework for implementing security controls and managing risks effectively.
Importance of Standards and Regulations
Compliance with relevant standards and regulations demonstrates an organization’s commitment to security and helps build trust with stakeholders. It also helps reduce the risk of legal and financial penalties, data breaches, and reputational damage.