Volexity Ivanti Connect Secure VPN Vulnerabilities: A Cybersecurity Threat
Volexity Ivanti Connect Secure VPN vulnerabilities have shaken the cybersecurity world, raising concerns about the security of virtual private networks (VPNs). This discovery highlights the importance of staying vigilant and proactive in securing our online activities. Ivanti Connect Secure VPN, a popular solution designed to protect sensitive data and provide secure remote access, has been found to contain critical flaws that could potentially allow attackers to compromise user devices and steal confidential information.
These vulnerabilities, identified by the cybersecurity firm Volexity, range in severity and exploit methods. Understanding the nature of these vulnerabilities, their potential impact, and effective mitigation strategies is crucial for safeguarding sensitive data and maintaining a secure online environment.
Impact of the Vulnerabilities: Volexity Ivanti Connect Secure Vpn Vulnerabilities
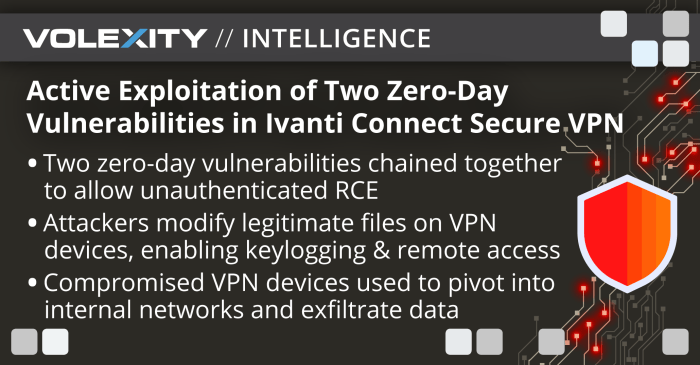
The vulnerabilities discovered in Volexity Ivanti Connect Secure VPN could have significant and far-reaching consequences if exploited successfully. Attackers could gain unauthorized access to sensitive data, compromise systems, and disrupt operations, leading to various security risks and potential data breaches.
Potential Data Breaches
Successful exploitation of these vulnerabilities could lead to the theft of sensitive data, including confidential information, personal data, and intellectual property. Attackers could gain access to user credentials, financial records, trade secrets, and other valuable information. For example, an attacker could steal customer credit card details from a company’s database, leading to financial fraud and reputational damage.
System Compromises
Exploiting these vulnerabilities could allow attackers to compromise the affected systems, giving them complete control over the device or network. Attackers could install malware, steal data, and even launch further attacks against other systems within the network. For instance, an attacker could gain control of a company’s server, install ransomware, and demand a ransom payment to decrypt the company’s data.
Other Security Risks
Besides data breaches and system compromises, these vulnerabilities could lead to other security risks, such as denial-of-service attacks, unauthorized access to sensitive applications, and disruption of business operations. Attackers could launch denial-of-service attacks to disrupt the availability of the VPN service, making it inaccessible to legitimate users.
They could also gain access to sensitive applications and steal data or disrupt their functionality.
Exploiting these vulnerabilities could have serious consequences for organizations and individuals, leading to data breaches, system compromises, financial losses, reputational damage, and legal repercussions.
Future Implications and Recommendations

The Volexity Ivanti Connect Secure VPN vulnerabilities underscore the critical need for ongoing vigilance and proactive security measures in the evolving landscape of VPN technology. These vulnerabilities highlight the persistent challenges of securing remote access solutions and emphasize the importance of a comprehensive approach to VPN security.
Implications for VPN Security
The discovery of these vulnerabilities has significant implications for the future of VPN security. It underscores the constant need for robust security practices and emphasizes the importance of proactive vulnerability management. These vulnerabilities serve as a stark reminder that even established and widely deployed VPN solutions can be susceptible to security flaws.
This necessitates a shift towards a more proactive and holistic approach to VPN security, encompassing regular vulnerability assessments, prompt patching, and the implementation of multi-layered security controls.
Recommendations for Enhanced VPN Security, Volexity ivanti connect secure vpn vulnerabilities
Organizations should implement a multi-layered approach to enhance their VPN security posture. This includes:
- Regular Vulnerability Assessments:Organizations must prioritize regular vulnerability assessments of their VPN infrastructure. This involves identifying and mitigating potential vulnerabilities before they can be exploited by attackers. This can be achieved through penetration testing, vulnerability scanning, and the use of security information and event management (SIEM) systems.
- Prompt Patching:Organizations should promptly patch vulnerabilities identified through assessments or reported by vendors. Timely patching is crucial to mitigate the risk of exploitation. Organizations should establish clear processes for patch management, including testing patches in non-production environments before deploying them to production systems.
- Multi-Factor Authentication (MFA):Implementing MFA adds an extra layer of security by requiring users to provide multiple forms of authentication before granting access. This significantly reduces the risk of unauthorized access, even if credentials are compromised.
- Strong Password Policies:Enforcing strong password policies is essential for protecting VPN accounts. This includes requiring complex passwords with a combination of uppercase and lowercase letters, numbers, and special characters. Organizations should also encourage users to change their passwords regularly and avoid using the same password across multiple accounts.
- Network Segmentation:Isolating the VPN infrastructure from other critical systems within the organization can limit the impact of a successful attack. This involves creating separate network segments for VPN users, ensuring that a compromise of the VPN network does not allow attackers to access other sensitive systems.
- Secure Configuration:Organizations should carefully configure their VPN devices and software to minimize security risks. This includes disabling unnecessary services, implementing strong encryption protocols, and configuring appropriate access controls.
- Security Awareness Training:Educating users about VPN security best practices is crucial for mitigating the risk of social engineering attacks and phishing scams. This training should cover topics such as password hygiene, recognizing phishing attempts, and reporting suspicious activity.
Ongoing Vulnerability Monitoring and Proactive Measures
The discovery of vulnerabilities, such as those found in the Volexity Ivanti Connect Secure VPN, highlights the importance of ongoing vulnerability monitoring and proactive security measures. This requires a continuous and coordinated effort to identify and address potential vulnerabilities before they can be exploited.
Organizations should:
- Subscribe to Security Advisories:Organizations should subscribe to security advisories from VPN vendors and other reputable security organizations. This allows them to stay informed about newly discovered vulnerabilities and receive timely updates on available patches.
- Implement a Vulnerability Management Program:Organizations should establish a comprehensive vulnerability management program that includes regular scanning, patch management, and incident response planning. This program should be integrated with the organization’s overall security strategy.
- Embrace Threat Intelligence:Organizations should leverage threat intelligence feeds to stay informed about emerging threats and vulnerabilities. This allows them to proactively assess and mitigate risks before they become significant problems.