Checkpoint Hackers: USB Drives as a Gateway
Check point hackers usb – Checkpoint Hackers: USB Drives as a Gateway – The world of cybersecurity is constantly evolving, and one of the most persistent threats is the use of USB drives to infiltrate sensitive systems. Imagine a seemingly innocuous USB drive, dropped in a high-security area, containing malware that could cripple an entire network.
This is the reality of checkpoint hacking, and it’s a threat that needs to be taken seriously.
From government agencies to corporate headquarters, checkpoints are crucial for maintaining security. But these very checkpoints can be vulnerable to attack, and USB drives are often the weapon of choice for malicious actors. The methods used by hackers are constantly evolving, from cleverly disguised drives to sophisticated malware that can bypass even the most advanced security measures.
Checkpoint Hackers
Checkpoint systems, designed to secure physical access and protect sensitive information, are increasingly becoming targets for cybercriminals. These systems are often overlooked in security assessments, making them vulnerable to exploitation.
Speaking of security, I’ve been thinking about those Check Point hackers who use USB drives to spread malware. It’s like a real-life game of cat and mouse! But just like with a well-loved foundation, you can get the most out of your security measures by staying vigilant and knowing what to do when things go wrong.
Check out this article on tips to get the most uses out of your foundation and what to do when it breaks for some great advice. After all, a little bit of preventative maintenance goes a long way when it comes to protecting your data.
And just like with makeup, you can always layer on extra protection!
Motives of Hackers Targeting Checkpoints
Hackers targeting checkpoint systems have various motives, ranging from financial gain to disrupting operations and causing chaos.
- Financial Gain:Hackers can exploit vulnerabilities in checkpoint systems to steal sensitive information, such as credit card details, financial records, and confidential data. This information can be sold on the dark web for profit.
- Disruption of Operations:By compromising checkpoint systems, hackers can disrupt critical operations, causing delays, financial losses, and reputational damage. This can be achieved by manipulating access control, disabling surveillance systems, or spreading malware.
- Espionage and Intelligence Gathering:Hackers can gain access to sensitive information, such as employee data, strategic plans, and confidential documents, which can be used for espionage or competitive advantage.
- Extortion:Hackers can hold checkpoint systems hostage by encrypting data or disrupting operations, demanding ransom payments for restoring access or preventing further damage.
Real-World Incidents of Checkpoint Compromise
Numerous real-world incidents highlight the vulnerability of checkpoint systems to cyberattacks.
- 2017 Equifax Data Breach:Hackers exploited vulnerabilities in Equifax’s web application, gaining access to sensitive personal information of millions of individuals, including Social Security numbers, credit card details, and birth dates.
- 2019 Marriott Data Breach:Hackers exploited vulnerabilities in Marriott’s Starwood guest reservation system, gaining access to personal information of over 500 million guests worldwide.
- 2020 SolarWinds Hack:Hackers compromised SolarWinds’ Orion software, a widely used network management tool, enabling them to infiltrate the systems of numerous government agencies and private companies.
Common Vulnerabilities Exploited in Checkpoint Systems
Checkpoint systems are often vulnerable to various attack vectors, including:
- Weak Passwords and Authentication:Poor password practices and inadequate authentication mechanisms can allow hackers to easily gain access to checkpoint systems.
- Outdated Software and Patches:Outdated software and missing security patches create vulnerabilities that hackers can exploit.
- Unsecured Network Connections:Unsecured network connections can allow hackers to intercept data or gain access to checkpoint systems.
- Misconfigured Devices:Misconfigured devices, such as security cameras, access control systems, and network equipment, can create vulnerabilities that hackers can exploit.
- Social Engineering:Hackers can use social engineering techniques, such as phishing emails or phone calls, to trick employees into providing access to checkpoint systems.
Malware Used in Checkpoint Hacking
Hackers employ various types of malware to compromise checkpoint systems, including:
- Ransomware:Ransomware encrypts data and demands payment for its decryption, disrupting operations and causing financial losses.
- Spyware:Spyware secretly monitors and steals sensitive information, such as login credentials, financial data, and personal details.
- Trojan Horses:Trojan horses disguise themselves as legitimate software but contain malicious code that can grant hackers remote access to compromised systems.
- Botnets:Botnets are networks of compromised computers that can be used to launch distributed denial-of-service (DDoS) attacks, disrupt operations, and spread malware.
USB Drives as Vectors for Attacks
USB drives, ubiquitous and convenient, are often overlooked as potential entry points for malicious actors. Their portability and ease of use make them prime targets for exploiting vulnerabilities in security systems, particularly at checkpoints. This section delves into the various ways USB drives can be weaponized to compromise systems and the risks associated with using untrusted drives.
Methods for Disguising Malicious USB Drives
Disguising malicious USB drives is a common tactic employed by attackers to deceive unsuspecting users. The goal is to make the drive appear legitimate and trustworthy, encouraging users to plug it into their systems. Here are some common methods:
- Masquerading as Common Files:Attackers often disguise malicious files as common documents, such as Word files, PDFs, or spreadsheets. This can be achieved by renaming the file with a familiar extension or using a legitimate file icon to trick users into believing it’s safe to open.
- Using Familiar Branding:Malicious USB drives can be designed to resemble official branding, such as logos of reputable companies or government agencies. This can instill a sense of trust and legitimacy, making users more likely to insert the drive into their systems.
- Concealing the Drive:Attackers may conceal malicious USB drives within everyday objects, such as keychains, power banks, or even within seemingly harmless items like pens or lighters. This makes the drive less conspicuous and more likely to be overlooked by security personnel.
Risks Associated with Using Untrusted USB Drives at Checkpoints
Using untrusted USB drives at checkpoints poses significant security risks, potentially compromising sensitive information and critical systems. Here are some of the key risks:
- Malware Infection:The most common risk associated with untrusted USB drives is malware infection. Malicious software can be programmed to execute automatically when the drive is plugged in, potentially infecting the system and compromising data.
- Data Theft:Malicious USB drives can be used to steal sensitive data, such as confidential documents, financial information, or personal details. This can be achieved through keylogging software, data-stealing malware, or by simply copying files from the system onto the drive.
- System Compromise:Malicious USB drives can be used to gain unauthorized access to systems, potentially allowing attackers to control the system remotely, install backdoors, or launch further attacks. This can compromise the integrity of the system and potentially disrupt operations.
- Denial of Service Attacks:Malicious USB drives can be used to launch denial-of-service (DoS) attacks, overloading the system with requests and causing it to crash or become unresponsive. This can disrupt critical operations and cause significant downtime.
Types of Malware Spread via USB Drives
USB drives can be used to spread a wide range of malware, each with its own specific capabilities and objectives. Here is a table outlining some of the common types of malware that can be spread via USB drives:
| Malware Type | Description | Example |
|---|---|---|
| Viruses | Self-replicating programs that spread by attaching themselves to other files. | Win32.Nimda |
| Worms | Self-propagating programs that spread across networks without user interaction. | Conficker |
| Trojan Horses | Programs that appear legitimate but contain hidden malicious code. | Zeus |
| Spyware | Programs that secretly monitor user activity and collect personal information. | BlackHole |
| Ransomware | Programs that encrypt user files and demand payment for decryption. | WannaCry |
Security Measures for Checkpoint Systems

Checkpoint systems, often used in high-security areas like airports and government buildings, are vulnerable to attacks using USB drives. These devices can be used to introduce malware or steal sensitive data. Therefore, implementing robust security measures is crucial to protect these systems.
Best Practices for Securing Checkpoint Systems
Securing checkpoint systems against USB-based attacks requires a multi-layered approach, incorporating both physical and software solutions.
- Disable USB Ports:The simplest and most effective way to prevent USB-based attacks is to disable USB ports on all devices within the checkpoint system. This can be done through BIOS settings or group policy management.
- Implement Whitelisting:Allowing only authorized USB devices to connect to the system can significantly reduce the risk of malware introduction. This involves creating a whitelist of approved devices and blocking any others.
- Regular Software Updates:Keeping all software up-to-date is crucial to patch vulnerabilities that could be exploited by attackers. This includes operating systems, antivirus software, and any other relevant applications.
- Use Strong Passwords:Employing strong passwords for all accounts within the checkpoint system is essential to prevent unauthorized access. Encourage the use of complex passwords with a combination of upper and lowercase letters, numbers, and special characters.
- Data Encryption:Encrypting sensitive data stored on devices within the checkpoint system protects it from unauthorized access even if the device is compromised.
- Employee Training:Educating employees about the risks of USB-based attacks and proper security practices is essential. Training should cover topics like identifying suspicious USB drives, avoiding unauthorized devices, and reporting suspicious activity.
Physical Security Measures
Physical security measures are equally important in protecting checkpoint systems.
I’m always on the lookout for ways to stay ahead of the curve when it comes to cybersecurity, especially with things like checkpoint hackers using USB drives to spread malware. It’s amazing how quickly technology evolves, and it’s always a good idea to stay informed.
Speaking of evolving, I’ve been wanting to add some personality to my home office, and I’ve been thinking about building some DIY diamond-shaped book shelves. They’d be a great way to showcase my collection of tech books, and maybe even hide a few extra USB drives in case I need to test some security protocols! Anyway, back to the topic at hand, it’s important to be vigilant and keep up with the latest security threats.
You never know when you might need to defend yourself against a checkpoint hacker’s USB drive.
- Controlled Access:Restricting access to the checkpoint system to authorized personnel only. This can be achieved through physical barriers, security cameras, and access control systems.
- Surveillance:Installing surveillance cameras to monitor activity around the checkpoint system can deter potential attackers and provide evidence in case of an incident.
- Secure Storage:Store all USB drives in a secure location when not in use. This prevents unauthorized access and potential theft.
- Regular Inspections:Conducting regular physical inspections of the checkpoint system to identify any potential vulnerabilities or security breaches is crucial.
Software Solutions for Detecting and Preventing USB-based Threats
Various software solutions can help detect and prevent USB-based threats.
Sometimes, when I’m feeling overwhelmed by the constant threat of check point hackers and USB vulnerabilities, I find solace in creative projects. A recent favorite has been crafting a copper pipe pineapple mirror DIY , which allows me to channel my anxieties into something beautiful and functional.
The process is surprisingly calming, and the finished product is a reminder that even in the face of digital threats, there’s always room for creativity and self-expression. Perhaps, with a little ingenuity, we can even find ways to use our crafting skills to enhance our cybersecurity efforts.
- Antivirus Software:Antivirus software plays a crucial role in identifying and removing malware from USB drives. Regularly updating antivirus software ensures it can detect the latest threats.
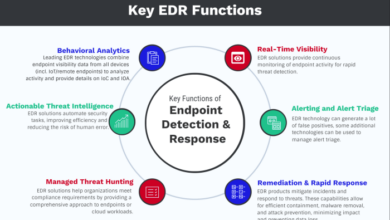
- Endpoint Detection and Response (EDR):EDR solutions monitor system activity for suspicious behavior, including USB drive access. They can detect and prevent attacks in real-time.
- Data Loss Prevention (DLP):DLP software can prevent sensitive data from being copied to unauthorized USB drives. This helps protect against data theft and leakage.
- USB Port Control Software:These solutions allow administrators to control USB port access, enabling them to block specific devices or restrict access to specific functions.
Comparison of Security Solutions, Check point hackers usb
| Security Solution | Pros | Cons |
|---|---|---|
| Disabling USB Ports | Simple and effective, eliminates the risk of USB-based attacks. | Can be inconvenient for legitimate use cases, requires alternative data transfer methods. |
| Whitelisting | Reduces the risk of malware introduction by allowing only authorized devices. | Requires careful device management, may not be suitable for dynamic environments. |
| Antivirus Software | Provides comprehensive protection against malware on USB drives. | May not detect all threats, requires regular updates. |
| EDR | Offers real-time monitoring and threat detection, can prevent attacks. | May be resource-intensive, requires specialized expertise. |
| DLP | Prevents data leakage to unauthorized USB drives. | Can be complex to configure, may impact legitimate data transfers. |
| USB Port Control Software | Provides granular control over USB port access. | May require additional administration overhead, can be challenging to manage. |
Awareness and Training for Checkpoint Personnel
Training checkpoint personnel about USB-based threats is crucial for safeguarding sensitive information and preventing security breaches. Effective training empowers personnel to identify potential threats, understand the risks associated with USB drives, and implement appropriate security measures.
Training Materials for Educating Checkpoint Personnel
Providing comprehensive training materials is essential for equipping checkpoint personnel with the knowledge and skills to handle USB-based threats effectively. These materials should cover various aspects of USB security, including:
- Understanding USB-based threats: Training materials should clearly explain the different types of threats associated with USB drives, such as malware infections, data exfiltration, and unauthorized access. Examples of common threats like ransomware, spyware, and data-stealing Trojans should be discussed, highlighting their potential impact on the organization.
- Identifying suspicious USB drives: Training materials should provide clear guidelines for identifying suspicious USB drives. These guidelines could include factors like:
- The presence of unusual labels or markings
- The lack of an expected logo or branding
- The presence of unusual file names or extensions
- The presence of unusual file sizes or dates
- Security measures for handling USB drives: Training materials should emphasize the importance of security measures, such as:
- Never connecting an unknown USB drive to a company network: This is a fundamental principle that should be emphasized throughout the training.
- Scanning USB drives for malware: Training should include information on how to use antivirus software and other security tools to scan USB drives for malware before connecting them to any device.
- Implementing access control measures: Training should cover the importance of implementing access control measures, such as password protection and encryption, to prevent unauthorized access to sensitive data stored on USB drives.
- Reporting suspicious USB drives: Training materials should clearly Artikel the procedure for reporting suspicious USB drives to the appropriate security personnel.
Awareness Campaigns for Mitigating USB-Based Threats
Awareness campaigns play a crucial role in mitigating USB-based threats. These campaigns should be designed to educate employees about the risks associated with USB drives and encourage them to adopt safe practices.
- Regular reminders and updates: Regular reminders and updates through emails, posters, and intranet announcements can help maintain employee awareness about USB security risks.
- Interactive training sessions: Interactive training sessions can help employees understand the importance of USB security and provide them with practical tips for protecting themselves from threats. These sessions can include real-life scenarios, quizzes, and role-playing exercises to enhance learning.
- Sharing real-world examples: Sharing real-world examples of USB-based attacks can effectively illustrate the potential consequences of neglecting USB security. These examples can be sourced from news articles, industry reports, or case studies.
Sample Training Scenario
- Scenario: A checkpoint personnel at a company entrance discovers a USB drive lying unattended near the security gate. The USB drive is labeled “Important Files” and has no other identifying information.
- Response: The checkpoint personnel should immediately:
- Secure the USB drive: The USB drive should be placed in a secure container and isolated from any other devices.
- Report the incident: The checkpoint personnel should immediately report the incident to their supervisor or the security team.
- Follow company policy: The checkpoint personnel should follow the company’s established policy for handling suspicious USB drives, which may involve further investigation or disposal of the drive.
Emerging Trends in Checkpoint Hacking: Check Point Hackers Usb
The landscape of checkpoint security is constantly evolving, driven by advancements in technology and the ingenuity of attackers. As new technologies emerge, they present both opportunities and challenges for security, creating new vulnerabilities that hackers can exploit. Understanding these emerging trends is crucial for staying ahead of the curve and implementing effective security measures.
The Impact of Emerging Technologies on Checkpoint Security
Emerging technologies like artificial intelligence (AI), Internet of Things (IoT), and 5G are transforming various industries, including security. These technologies offer potential benefits for checkpoint security, such as automated screening and enhanced threat detection. However, they also introduce new vulnerabilities that attackers can exploit.
For instance, AI-powered systems can be manipulated through adversarial machine learning techniques, leading to false positives or negatives. Similarly, IoT devices can be compromised, providing attackers with access to sensitive data or control over physical systems.
Emerging Threats Targeting Checkpoint Systems
The evolution of hacking techniques is a constant challenge for security professionals. Attackers are increasingly utilizing sophisticated methods to bypass checkpoint security measures. Here are some examples of emerging threats:
- Deepfakes and Facial Recognition Bypass:Deepfake technology allows attackers to create highly realistic fake videos or images of individuals, potentially enabling them to bypass facial recognition systems used at checkpoints.
- Drone-Based Attacks:Drones can be used to smuggle contraband or deliver malicious payloads, posing a significant threat to checkpoint security. Hackers can exploit vulnerabilities in drone systems to hijack them or use them to launch attacks.
- Social Engineering and Deception:Attackers are increasingly using social engineering tactics to deceive checkpoint personnel. This can involve impersonating authorized personnel, using forged documents, or exploiting human error to gain unauthorized access.
Evolving Tactics for Bypassing Checkpoint Security
Hackers are constantly refining their tactics to bypass checkpoint security. Some emerging trends include:
- Exploiting Software Vulnerabilities:Attackers are actively searching for and exploiting software vulnerabilities in checkpoint systems, such as those found in access control software, security cameras, or other critical infrastructure.
- Using Physical Methods:Attackers may employ physical methods to bypass security measures, such as using 3D-printed replicas of keys or access cards, or using hidden compartments to smuggle contraband.
- Advanced Malware and Ransomware:Hackers are developing more sophisticated malware and ransomware that can target checkpoint systems, disrupt operations, or steal sensitive data.