Asymmetric vs Symmetric Encryption: A Tale of Two Keys
Asymmetric vs symmetric encryption: these two seemingly complex terms hold the key to unlocking a world of secure communication and data protection. Imagine a world where your online banking transactions, sensitive medical records, and even casual emails are vulnerable to prying eyes.
Encryption, the process of scrambling data into an unreadable form, stands as a powerful shield against these threats. But how does it work, and what are the key differences between asymmetric and symmetric encryption?
In this blog post, we’ll delve into the fascinating world of encryption, exploring the unique characteristics and applications of both symmetric and asymmetric encryption. We’ll uncover their strengths and weaknesses, discover why they’re essential for securing our digital lives, and even peek into the future of encryption.
Asymmetric Encryption: Asymmetric Vs Symmetric Encryption
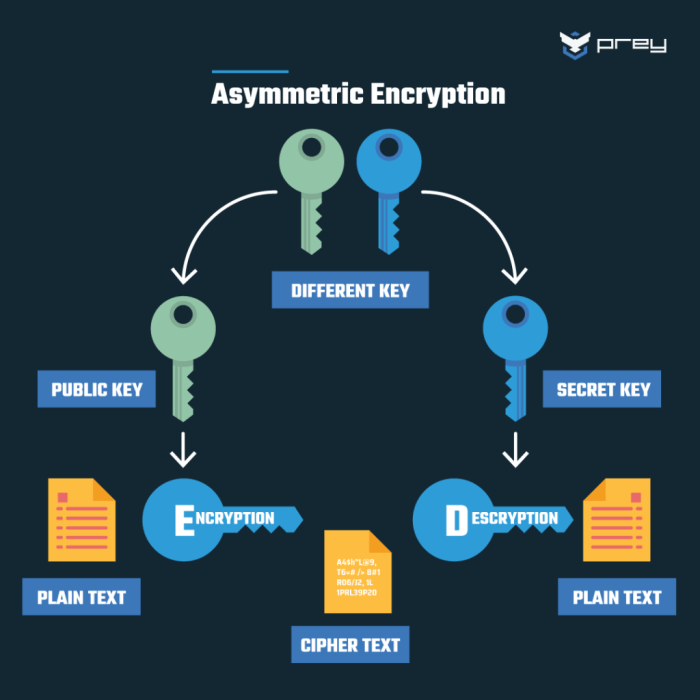
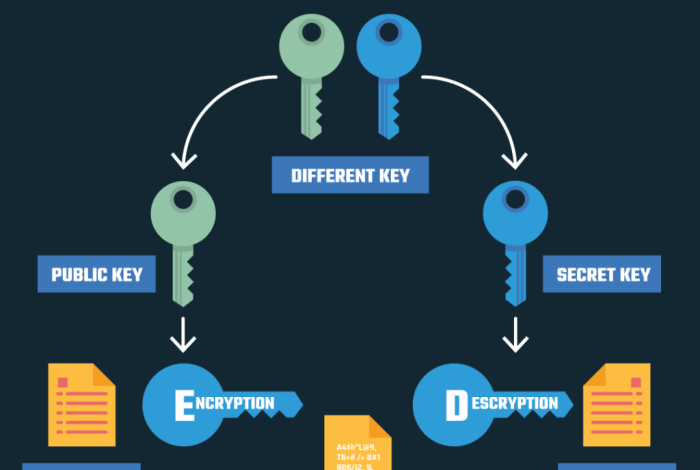
Asymmetric encryption, also known as public-key cryptography, employs two distinct keys for encryption and decryption: a public key and a private key. This system enhances security by ensuring that only the intended recipient can decrypt the message.
Public and Private Keys, Asymmetric vs symmetric encryption
Asymmetric encryption utilizes a pair of mathematically related keys. The public key can be freely shared, while the private key must be kept secret. This key pair allows for secure communication and data protection.
- Public Key:This key is used for encrypting messages. Anyone can access and use the public key to encrypt data intended for the recipient. The public key is designed to be secure and cannot be used to decrypt the message.
- Private Key:This key is kept secret and is used for decrypting messages. Only the owner of the private key can decrypt messages encrypted with the corresponding public key. The private key must be kept secure to prevent unauthorized access to encrypted data.
Common Asymmetric Encryption Algorithms
Several widely used asymmetric encryption algorithms exist, each offering unique characteristics and security levels.
- RSA:RSA, named after its inventors Rivest, Shamir, and Adleman, is one of the oldest and most widely used asymmetric encryption algorithms. It relies on the difficulty of factoring large numbers, making it a robust and secure option. RSA is commonly used for digital signatures, secure communication, and key exchange.
- ECC (Elliptic Curve Cryptography):ECC utilizes elliptic curves to perform cryptographic operations. Compared to RSA, ECC provides similar security levels with smaller key sizes, making it more efficient for resource-constrained devices and mobile applications. ECC is gaining popularity in various applications, including mobile payments, secure messaging, and blockchain technologies.
Asymmetric encryption uses two keys, one public and one private, while symmetric encryption uses a single key for both encryption and decryption. It’s like the difference between a public and private Facebook profile, where you share some information with everyone (public key) and some you keep private (private key).
Speaking of sharing, check out sister style nothing fancy for some stylish tips. Getting back to encryption, asymmetric encryption is often used for secure communication, while symmetric encryption is more suitable for bulk data encryption.
Asymmetric encryption, with its separate keys for encryption and decryption, feels a bit like the duality of my new pineapple tattoo. One side is the vibrant, sunny fruit, while the other showcases the spiky, protective leaves. It’s a perfect representation of the complex, yet secure, nature of asymmetric encryption.
Just as the tattoo’s design is a beautiful interplay of contrasting elements, so too is the strength of asymmetric encryption found in its ability to keep data safe through the use of distinct keys. My new pineapple tattoo is a constant reminder of the intriguing balance of complexity and security that defines asymmetric encryption.
Asymmetric encryption, using separate keys for encoding and decoding, is like a locked box with two keys – one for you and one for the intended recipient. It’s the same principle as the security used for Laura’s Palm Springs mini album, which you can check out here , only much more complex.
Symmetric encryption, on the other hand, uses the same key for both, making it more efficient but less secure in some scenarios.