Winter Vivern Exploits Zero-Day Roundcube Webmail Vulnerability
Winter vivern exploits zero day roundcube webmail – Winter Vivern exploits zero-day Roundcube webmail vulnerabilities, posing a serious threat to users worldwide. This exploit leverages unpatched security flaws, allowing attackers to gain unauthorized access to sensitive data. Roundcube webmail, a popular open-source platform, is a prime target for attackers due to its widespread use and potential security weaknesses.
The Winter Vivern exploit highlights the critical importance of staying vigilant against zero-day vulnerabilities, which can have devastating consequences for individuals and organizations alike.
Understanding the nature of this exploit, the vulnerabilities it exploits, and the potential impact on users is crucial for mitigating the risks. This blog post will delve into the intricacies of the Winter Vivern exploit, examining its techniques, potential consequences, and effective countermeasures.
By shedding light on this critical cybersecurity threat, we aim to empower users and administrators to protect their Roundcube webmail accounts and data from malicious actors.
Understanding the Threat
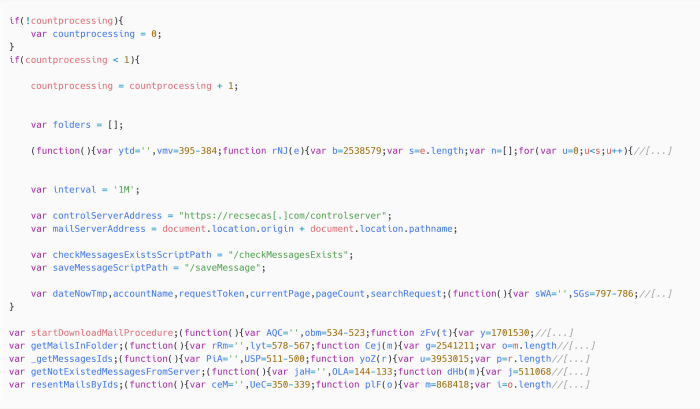
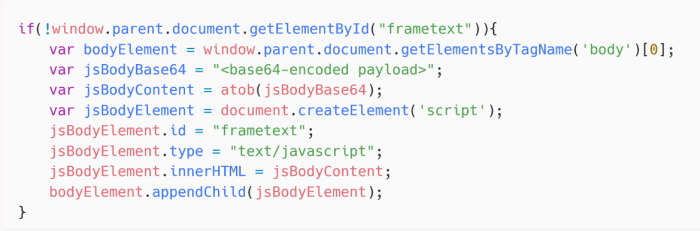
The Winter Vivern exploit is a serious security vulnerability that affects Roundcube webmail users. It leverages multiple vulnerabilities in Roundcube’s code to gain unauthorized access to user accounts and potentially compromise sensitive data. Understanding the nature of this exploit and its potential impact is crucial for protecting your email accounts.
Vulnerabilities Exploited by Winter Vivern
The Winter Vivern exploit targets several vulnerabilities in Roundcube webmail, including:
- Cross-Site Scripting (XSS): This vulnerability allows attackers to inject malicious JavaScript code into web pages viewed by users. When a user visits a compromised page, the injected code can execute on their device, potentially stealing their login credentials or other sensitive information.
The Winter Vivern exploit targeting Roundcube webmail is a serious vulnerability that highlights the importance of keeping software up-to-date. It’s interesting to note that this kind of security breach comes at a time when Apple is appealing a $19 billion EU fine levied following Spotify’s claims of anti-competitive App Store behavior apple appeals a dollar19 billion eu fine levied following spotifys claims of anti competitive app store behavior.
This raises questions about how companies manage security risks across their platforms and the impact on users. Hopefully, the Roundcube webmail vulnerability will be patched quickly, and users can continue to rely on their email services securely.
- SQL Injection: This vulnerability allows attackers to manipulate database queries, potentially gaining access to sensitive information stored in the Roundcube database. Attackers can exploit this vulnerability to retrieve user passwords, email content, or other confidential data.
- Remote Code Execution (RCE): This vulnerability allows attackers to execute arbitrary code on the Roundcube web server. This could enable them to gain full control of the server, potentially installing malware or stealing sensitive data.
Techniques Used to Gain Access
Attackers exploit these vulnerabilities using a variety of techniques, including:
- Phishing Emails: Attackers often send phishing emails disguised as legitimate messages from trusted sources. These emails may contain malicious links or attachments that, when clicked, can lead to compromised web pages or malware downloads.
- Malicious Websites: Attackers can create malicious websites that mimic legitimate websites, such as email login pages. When users enter their login credentials on these fake websites, the information is stolen by the attackers.
- Exploiting Weak Passwords: Attackers can use brute-force attacks or password guessing techniques to gain access to accounts with weak or easily guessable passwords.
Data at Risk
If successful, the Winter Vivern exploit can compromise a wide range of sensitive data, including:
- Email Content: Attackers can access and steal the content of your emails, including personal correspondence, financial transactions, and other confidential information.
- User Credentials: Attackers can steal your email login credentials, giving them access to your account and all associated data.
- Contact Information: Attackers can gain access to your contact list, including names, email addresses, and phone numbers.
- Attachments: Attackers can download and steal any attachments stored in your email account, including sensitive documents, financial statements, and other confidential files.
Roundcube Webmail

Roundcube Webmail is a popular and widely used web-based email client that has gained significant traction among individuals and organizations alike. Its open-source nature, flexibility, and user-friendly interface have made it a preferred choice for managing email communications.
Roundcube Webmail Security Features and Limitations
Roundcube Webmail offers a range of security features, including encryption, authentication, and access control mechanisms. However, like any software application, it has its limitations.
- Encryption:Roundcube supports various encryption protocols, such as TLS/SSL, to secure communication between the client and the server. However, the effectiveness of encryption depends on the configuration and implementation of the underlying email server and the user’s security practices.
- Authentication:Roundcube provides robust authentication mechanisms, such as password-based authentication and two-factor authentication (2FA), to prevent unauthorized access. However, the strength of authentication depends on the user’s choice of passwords and the implementation of 2FA.
- Access Control:Roundcube allows administrators to define access control policies and user permissions. This helps to limit access to sensitive information and prevent unauthorized actions. However, the effectiveness of access control depends on the administrator’s vigilance and the configuration of the system.
The Winter Vivern exploit targeting Roundcube webmail is a serious threat, highlighting the importance of staying vigilant about security vulnerabilities. While we’re on the topic of online security, you might find it helpful to learn how to stream Google Meet to YouTube , especially if you’re hosting online meetings or events.
This could help you create a more secure and controlled environment for your virtual interactions, similar to how understanding and addressing the Winter Vivern exploit can strengthen your webmail security.
- Vulnerabilities:Roundcube, like any software application, is susceptible to vulnerabilities that can be exploited by attackers. These vulnerabilities can arise from code flaws, outdated software versions, or misconfigurations.
Attractiveness of Roundcube Webmail to Attackers
Roundcube Webmail’s popularity and widespread use make it an attractive target for attackers. The reasons for this include:
- Large User Base:Roundcube’s vast user base provides attackers with a large pool of potential victims. This increases the chances of success for attacks.
- Common Vulnerabilities:Like any software application, Roundcube has vulnerabilities that can be exploited by attackers. These vulnerabilities can be used to gain unauthorized access to user accounts, steal sensitive data, or launch further attacks.
- Lack of Security Awareness:Many users may not be fully aware of the security risks associated with using webmail clients. This can make them more susceptible to attacks.
- Outdated Software:Many organizations and individuals may not keep their Roundcube installations up to date with the latest security patches. This can leave them vulnerable to known vulnerabilities.
Security Features Comparison
Here is a table comparing the security features of Roundcube Webmail with other popular email platforms:
| Feature | Roundcube Webmail | Gmail | Outlook.com | Yahoo Mail |
|---|---|---|---|---|
| Encryption | TLS/SSL | TLS/SSL | TLS/SSL | TLS/SSL |
| Authentication | Password-based, 2FA | Password-based, 2FA | Password-based, 2FA | Password-based, 2FA |
| Access Control | User permissions, policies | User permissions, policies | User permissions, policies | User permissions, policies |
| Security Updates | Regular updates | Regular updates | Regular updates | Regular updates |
| Security Features | Spam filtering, phishing detection | Spam filtering, phishing detection, advanced security settings | Spam filtering, phishing detection, advanced security settings | Spam filtering, phishing detection, advanced security settings |
Zero-Day Vulnerability: Winter Vivern Exploits Zero Day Roundcube Webmail
In the realm of cybersecurity, the term “zero-day vulnerability” refers to a previously unknown weakness in a software system or application. This vulnerability is so named because it is discovered on the day it is exploited, leaving developers with zero days to patch it before attackers can take advantage of it.
Zero-day vulnerabilities pose a significant threat to individuals, organizations, and governments, as they can be exploited to steal sensitive data, disrupt critical systems, or gain unauthorized access to networks.
The Winter Vivern exploit targeting Roundcube webmail is a serious threat, exploiting a zero-day vulnerability to gain unauthorized access. It’s a stark reminder of the constant need for vigilance in cybersecurity. Meanwhile, the AI landscape is heating up with the release of Meta’s Llama 2, an open-source rival to ChatGPT ( meta llama 2 open source rival chatgpt ).
While AI advancements are exciting, it’s important to remember that security vulnerabilities can be exploited by malicious actors, making it crucial to stay informed and proactive in protecting our systems.
Exploiting Zero-Day Vulnerabilities
Attackers who discover zero-day vulnerabilities often exploit them before patches are available, making them highly effective in bypassing security measures. They can achieve this through various methods:
- Malicious Software (Malware):Attackers create and distribute malware designed to exploit the vulnerability and gain access to targeted systems.
- Targeted Attacks:Highly skilled attackers may craft customized exploits to target specific organizations or individuals, exploiting the vulnerability to gain access to sensitive data or systems.
- Exploit Kits:Attackers may develop and sell exploit kits that contain tools and instructions for exploiting zero-day vulnerabilities, allowing other attackers to leverage them without needing to discover them themselves.
Challenges Faced by Software Developers
Addressing zero-day vulnerabilities presents significant challenges for software developers:
- Rapid Discovery:New vulnerabilities are constantly emerging, making it difficult for developers to keep up with the pace of discovery and patching.
- Limited Information:Developers often have limited information about the vulnerability itself, making it difficult to identify the root cause and develop an effective patch.
- Time Constraints:Developers must prioritize patching vulnerabilities based on their severity and impact, often working under tight deadlines to minimize the risk of exploitation.
Examples of Zero-Day Exploits
Throughout history, numerous zero-day exploits have been used to attack individuals, organizations, and governments. Some notable examples include:
- Stuxnet:This sophisticated malware, discovered in 2010, exploited vulnerabilities in industrial control systems to disrupt Iran’s nuclear program.
- WannaCry:This ransomware, which spread globally in 2017, exploited a zero-day vulnerability in Microsoft Windows to encrypt data and demand payment for its release.
- NotPetya:Another ransomware attack that occurred in 2017, NotPetya leveraged a zero-day vulnerability in a Ukrainian accounting software to cripple businesses worldwide.
Consequences of Exploitation
A successful Winter Vivern exploit can have far-reaching consequences for individuals and organizations alike, impacting everything from financial stability to reputation and legal standing. This section will delve into the potential ramifications of such a breach, exploring the financial, reputational, and legal implications of compromised data.
We’ll also examine real-world examples of data breaches and their impact, illustrating the severity of the situation.
Financial Implications
The financial impact of a data breach can be substantial and multifaceted. Stolen data can be used for various malicious activities, leading to significant financial losses.
- Identity Theft:Stolen personal information, such as credit card numbers, social security numbers, and bank account details, can be used for identity theft, leading to financial ruin for individuals.
- Financial Fraud:Hackers can exploit stolen credentials to access bank accounts and financial platforms, leading to unauthorized transactions and financial losses.
- Ransomware Attacks:Organizations can fall victim to ransomware attacks where hackers encrypt their data and demand a ransom for its decryption. This can lead to costly downtime, data loss, and reputational damage.
- Legal Expenses:Organizations facing data breaches often incur significant legal expenses related to investigations, regulatory compliance, and potential lawsuits.
- Loss of Revenue:A data breach can disrupt business operations, leading to lost revenue and decreased productivity.
Reputational Damage
Data breaches can severely damage an organization’s reputation, leading to a loss of trust among customers, partners, and investors.
- Loss of Customer Trust:Customers may lose faith in an organization’s ability to protect their data, leading to decreased loyalty and potential customer churn.
- Negative Media Coverage:Data breaches often attract negative media attention, damaging an organization’s public image and brand value.
- Reduced Investor Confidence:Investors may lose confidence in an organization’s ability to manage risk and protect its assets, leading to decreased investment and share value.
Legal Implications
Data breaches can trigger legal consequences, including regulatory fines, lawsuits, and reputational damage.
- Regulatory Fines:Organizations may face hefty fines from regulatory bodies like the GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) for failing to adequately protect personal data.
- Class-Action Lawsuits:Individuals whose data has been compromised may file class-action lawsuits against organizations, seeking compensation for damages.
- Criminal Charges:In severe cases, individuals involved in data breaches may face criminal charges and imprisonment.
Real-World Examples
The consequences of data breaches are real and devastating. Several high-profile cases highlight the impact on individuals and organizations:
- Equifax Breach (2017):This massive breach affected over 147 million individuals, exposing sensitive personal information like Social Security numbers, credit card details, and birth dates. The incident led to significant financial losses, reputational damage, and legal action against Equifax.
- Target Breach (2013):Hackers stole credit card information from millions of customers during the holiday season, causing significant financial losses for Target and its customers.
- Yahoo Breach (2014-2016):A series of breaches affected billions of Yahoo users, exposing personal data like email addresses, passwords, and security questions. This incident led to a loss of trust in Yahoo and resulted in a significant drop in its market value.
“Data privacy and security are not just technical issues, they are fundamental human rights. We have a moral obligation to protect the information of individuals and organizations from harm.”
The Future of Webmail Security
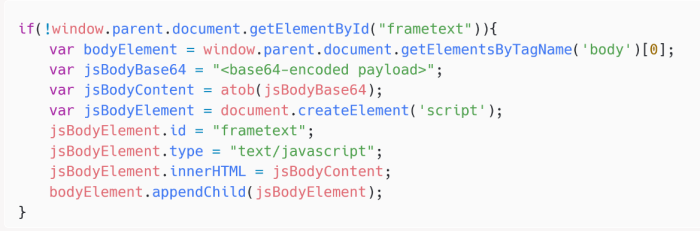
The Winter Vivern zero-day exploit serves as a stark reminder of the ever-evolving threat landscape facing webmail services. As attackers become more sophisticated, we must adapt our security strategies to stay ahead of the curve. This necessitates a proactive approach to safeguarding user data and ensuring the integrity of our communication channels.
The Evolving Threat Landscape
The threat landscape for webmail services is constantly evolving, driven by factors such as:* Increasingly sophisticated attack techniques:Attackers are constantly developing new techniques to bypass security measures, such as zero-day exploits, phishing campaigns, and social engineering attacks.
The rise of artificial intelligence (AI)
AI is being used by both attackers and defenders. While AI can be used to detect and prevent attacks, it can also be used to create more sophisticated and targeted attacks.
The growth of mobile and cloud computing
The increasing use of mobile devices and cloud-based services has expanded the attack surface for webmail providers.
The proliferation of malware
Malware is becoming increasingly prevalent and sophisticated, posing a significant threat to webmail security.
The Role of Artificial Intelligence and Machine Learning in Cybersecurity
AI and machine learning (ML) are playing an increasingly important role in cybersecurity. These technologies can be used to:* Detect and prevent attacks:AI and ML algorithms can analyze large datasets of network traffic, user behavior, and other data to identify suspicious activity and potential threats.
Improve security posture
AI and ML can be used to automate security tasks, such as vulnerability scanning and patch management.
Enhance threat intelligence
AI and ML can help to analyze threat data and identify emerging threats.
“AI and ML are powerful tools that can be used to enhance webmail security, but it is important to note that they are not a silver bullet. These technologies must be used in conjunction with other security measures to ensure a robust defense.”
Future Webmail Security Challenges and Potential Solutions, Winter vivern exploits zero day roundcube webmail
Here are some potential future webmail security challenges and potential solutions:* Challenge:The increasing use of AI by attackers to create more sophisticated and targeted attacks.
Solution
Develop AI-powered defenses to counter AI-based attacks.
Challenge
The growing number of zero-day vulnerabilities.
Solution
Invest in robust vulnerability management programs and encourage responsible disclosure of vulnerabilities.
Challenge
The increasing use of mobile devices and cloud-based services.
Solution
Implement security measures specifically designed for mobile and cloud environments.
Challenge
The proliferation of malware.
Solution
Invest in advanced malware detection and prevention technologies.
Illustration of the Dynamic Nature of Cyberattacks and Security Measures
Imagine a game of chess between a skilled attacker and a determined defender. The attacker seeks to exploit weaknesses in the defender’s defenses, while the defender strives to anticipate and counter the attacker’s moves. The game is constantly evolving, with each player adapting their strategy based on the opponent’s actions.
This dynamic nature of cyberattacks and security measures highlights the need for constant vigilance and innovation.