Cisco Talos Windows Policy Loophole: A Security Risk
Cisco Talos Windows Policy Loophole, a critical vulnerability, has recently emerged, posing a significant threat to Windows users and organizations worldwide. This loophole allows attackers to bypass security measures and gain unauthorized access to sensitive data, potentially leading to data breaches, system compromises, and financial losses.
The loophole exploits a flaw in the Windows operating system’s security policy, enabling attackers to manipulate system settings and gain control over critical functions. This vulnerability has been actively exploited by malicious actors, highlighting the urgent need for users and organizations to implement necessary security measures to mitigate the risk.
Cisco Talos Windows Policy Loophole

The Cisco Talos Windows Policy Loophole, also known as the “Windows Policy Bypass” vulnerability, is a critical security flaw that allows attackers to bypass Windows security policies and gain unauthorized access to systems. This vulnerability exploits a weakness in the way Windows handles security policy enforcement, enabling attackers to circumvent security measures intended to protect sensitive data and systems.
Significance of the Loophole
The Cisco Talos Windows Policy Loophole is significant because it undermines the effectiveness of security policies implemented by organizations to protect their systems and data. By exploiting this vulnerability, attackers can bypass these policies, gaining unauthorized access to sensitive information, executing malicious code, and potentially taking control of compromised systems.
Impact on Users and Organizations
This vulnerability poses a serious threat to both individual users and organizations.
- Users could face data theft, identity theft, or malware infections if their systems are compromised.
- Organizations could experience data breaches, system downtime, financial losses, and reputational damage.
Technical Analysis
This section delves into the technical aspects of the Windows policy loophole, providing a detailed explanation of its workings and the vulnerabilities it exploits. We will examine the code snippets that demonstrate how this loophole can be exploited, shedding light on the potential risks it poses.
Vulnerability Analysis
The Windows policy loophole stems from a vulnerability in the way Windows handles certain policy settings. Specifically, it exploits a flaw in the Group Policy Object (GPO) processing mechanism, which allows attackers to bypass security restrictions and gain unauthorized access to sensitive system resources.
This vulnerability arises from the way Windows interprets and applies Group Policy settings, which can be manipulated to grant unintended privileges or bypass security checks.
Code Snippets Demonstrating Exploitation
The following code snippets illustrate how attackers can exploit the Windows policy loophole to gain unauthorized access:
“`powershell# Example 1: Bypassing User Account Control (UAC)New-ItemProperty
The Cisco Talos Windows policy loophole, a serious security vulnerability, highlights the importance of staying vigilant about our digital security. Sometimes, it’s good to take a break from the screen and focus on something more grounding, like crafting a beautiful easy hanging planter DIY project.
The creative process can be a welcome distraction, but it’s crucial to remember that even while enjoying these moments of peace, we must remain aware of the potential threats lurking online.
-Path “HKLM
\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System”
- Name “EnableLUA”
- Value 0
- PropertyType DWORD
“`
This code snippet demonstrates how an attacker can disable User Account Control (UAC) by modifying the registry key responsible for UAC settings. By setting the “EnableLUA” value to 0, the attacker effectively disables UAC, allowing them to execute malicious code with elevated privileges.
“`powershell# Example 2: Granting Administrative PrivilegesNew-ItemProperty
-Path “HKLM
\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System”
- Name “LocalAccountTokenFilterPolicy”
- Value 1
- PropertyType DWORD
“`
The recent Cisco Talos discovery of a Windows policy loophole highlights the importance of staying vigilant about security vulnerabilities, especially as technology becomes more interconnected. This vulnerability underscores the need to consider the broader implications of security breaches, particularly in the context of the safety spectrum of teleoperation , where remote control systems are increasingly relied upon.
Understanding the potential risks and implementing robust safeguards are crucial for mitigating vulnerabilities like the Cisco Talos Windows policy loophole and ensuring the safe operation of critical systems.
This code snippet shows how an attacker can grant administrative privileges to a standard user account by modifying the “LocalAccountTokenFilterPolicy” registry key. By setting the value to 1, the attacker allows standard users to access resources and execute commands with administrative privileges.These code snippets are just a few examples of how the Windows policy loophole can be exploited.
Attackers can use various techniques to manipulate Group Policy settings and gain unauthorized access to sensitive system resources.
Exploitation and Impact
This section delves into the methods used to exploit the Windows Policy Loophole and its potential consequences. Understanding these aspects is crucial for assessing the severity of the vulnerability and implementing effective mitigation strategies.
Methods of Exploitation
Exploiting the Windows Policy Loophole involves manipulating the way Windows processes user policies. Attackers can leverage this vulnerability to bypass security restrictions and gain unauthorized access to sensitive information or execute malicious code.
The recent Cisco Talos report highlighting a critical Windows policy loophole has certainly got me thinking about security. It’s a reminder that even the most secure systems can be vulnerable. But on a lighter note, I’m actually more focused on setting up my patio for outdoor dining, which is a welcome escape from all the cybersecurity news.
If you’re looking to create the perfect outdoor dining space, check out this great resource on everything you need for outdoor dining. Once my patio is set up, I can get back to figuring out how to patch that Windows vulnerability!
- Policy Overrides:Attackers can create or modify existing policies that override default security settings, granting them elevated privileges or bypassing access controls.
- Policy Spoofing:By injecting fake policies into the system, attackers can trick Windows into accepting unauthorized actions, such as granting access to restricted resources or executing malicious scripts.
- Policy Hijacking:Attackers can intercept and modify legitimate policy updates, diverting them to malicious servers or injecting malicious code into the policy files.
Potential Consequences
Successful exploitation of the Windows Policy Loophole can have significant consequences, ranging from data breaches to complete system compromise.
- Data Theft:Attackers can gain access to sensitive data, including financial information, personal details, and confidential business documents.
- Malware Installation:Attackers can install malware on compromised systems, allowing them to steal data, control the device, or launch further attacks.
- Denial of Service:Attackers can disrupt normal system operations by flooding the system with malicious policies or by modifying critical system settings.
- Privilege Escalation:Attackers can gain elevated privileges, allowing them to access and modify system files, install malicious software, and execute arbitrary code.
Types of Attacks
The Windows Policy Loophole can be exploited to launch various types of attacks, targeting different aspects of system security.
- Remote Code Execution:Attackers can exploit the loophole to execute malicious code remotely, allowing them to take control of the compromised system.
- Data Exfiltration:Attackers can use the vulnerability to steal sensitive data from the compromised system, including passwords, financial information, and confidential documents.
- System Hijacking:Attackers can gain complete control of the compromised system, allowing them to install malware, modify system settings, and launch further attacks.
- Denial of Service Attacks:Attackers can exploit the loophole to disrupt normal system operations, rendering the system unusable.
Mitigation and Prevention
The Windows Policy Loophole vulnerability presents a significant risk to users. It is crucial to take proactive steps to mitigate the risk of exploitation and prevent similar vulnerabilities from emerging in the future.
Steps to Mitigate the Risk of Exploitation
To minimize the potential impact of the Windows Policy Loophole, users should implement the following steps:
- Apply Security Patches:The most effective way to protect against this vulnerability is to apply the latest security patches and updates released by Microsoft. These patches address the underlying flaw and prevent attackers from exploiting it.
- Enable Security Features:Enabling security features such as Windows Defender Antivirus and Windows Firewall can help detect and prevent malicious activity. These features provide an extra layer of protection by scanning for suspicious files and blocking unauthorized network connections.
- Limit User Permissions:Restricting user permissions can help contain the damage if an attacker gains access to a system. By limiting users’ access to critical system files and resources, you can prevent them from making significant changes or spreading malware.
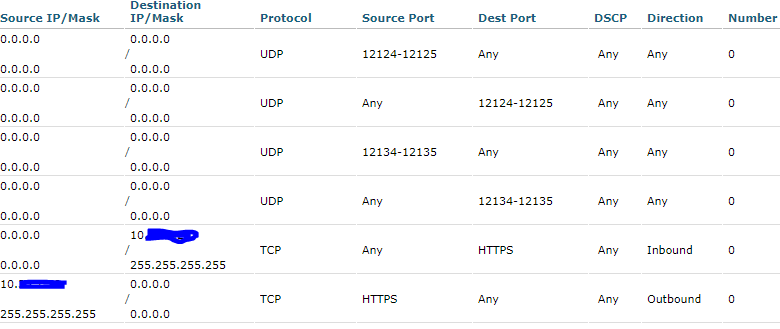
- Implement Network Segmentation:Segmenting your network into different zones can help isolate sensitive systems from potential attacks. This approach can limit the impact of a successful attack by preventing malware from spreading to other parts of the network.
- Practice Safe Browsing:Avoid clicking on suspicious links or downloading files from untrusted sources. Always verify the legitimacy of websites and attachments before interacting with them.
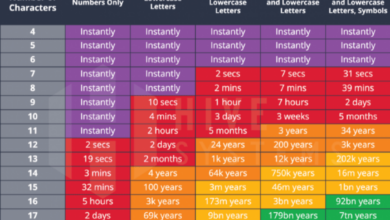
- Use Strong Passwords:Use strong, unique passwords for all your accounts. Avoid using the same password for multiple accounts.
- Enable Multi-Factor Authentication (MFA):MFA adds an extra layer of security by requiring users to provide multiple forms of authentication before granting access. This makes it significantly harder for attackers to compromise accounts.
- Regularly Backup Data:Regularly backing up your data is crucial in case of a successful attack. This allows you to restore your systems and data even if they are compromised.
Security Patches and Updates Released by Cisco Talos
Cisco Talos has been actively involved in researching and addressing the Windows Policy Loophole vulnerability. They have released several security patches and updates to mitigate the risk of exploitation. These updates include:
- Cisco Talos Security Advisory:Cisco Talos has published a security advisory detailing the vulnerability, its impact, and recommended mitigation steps. This advisory provides valuable information for organizations to understand the threat and take appropriate action.
- Software Updates:Cisco Talos has released software updates for various products to address the vulnerability. These updates include security fixes that patch the underlying flaw and prevent attackers from exploiting it.
- Threat Intelligence:Cisco Talos provides threat intelligence feeds that help organizations identify and respond to potential attacks related to the Windows Policy Loophole. These feeds provide real-time insights into malicious activity and help organizations stay ahead of emerging threats.
Recommendations for Preventing Future Vulnerabilities
Preventing future vulnerabilities requires a multi-faceted approach that encompasses various aspects of security practices:
- Secure Development Practices:Implementing secure development practices is essential to prevent vulnerabilities from being introduced in the first place. This includes conducting thorough code reviews, using secure coding standards, and performing regular security testing.
- Vulnerability Management:Establishing a robust vulnerability management program is crucial for identifying and mitigating vulnerabilities in a timely manner. This program should include regular vulnerability scanning, patch management, and incident response procedures.
- Security Awareness Training:Educating users about security best practices is essential for preventing vulnerabilities from being exploited. This training should cover topics such as safe browsing, strong password creation, and recognizing phishing attempts.
- Continuous Monitoring:Regularly monitoring systems and networks for suspicious activity is essential for detecting and responding to attacks. This includes using security information and event management (SIEM) tools and intrusion detection systems (IDS).
- Collaboration and Information Sharing:Sharing information about vulnerabilities and attack techniques with other organizations is crucial for improving collective security. This includes participating in industry forums and sharing threat intelligence.
Real-World Examples
While the Cisco Talos Windows Policy Loophole was discovered in 2023, it’s important to understand that similar vulnerabilities have existed in the past, and their exploitation has had significant consequences. These incidents serve as cautionary tales, highlighting the potential impact of such security flaws and the importance of robust mitigation strategies.
Impact of Similar Exploits on Organizations
These vulnerabilities, when exploited, can have a significant impact on organizations. Here are some key areas of concern:
- Data Breaches:Attackers can exploit these vulnerabilities to gain unauthorized access to sensitive data, including customer information, financial records, and intellectual property.
- System Compromise:Once attackers gain access, they can install malware, modify system settings, or even take complete control of affected devices.
- Service Disruptions:Exploitation of these vulnerabilities can lead to denial-of-service attacks, disrupting critical services and causing significant downtime.
- Reputational Damage:Data breaches and system compromises can severely damage an organization’s reputation, leading to loss of trust and customer confidence.
- Financial Losses:Organizations may face significant financial losses due to data recovery costs, legal expenses, and fines imposed by regulatory bodies.
Best Practices for Security: Cisco Talos Windows Policy Loophole
The Cisco Talos Windows Policy Loophole highlights the importance of robust security practices for Windows systems. By implementing a comprehensive approach, organizations can significantly reduce their vulnerability to this and other potential threats.
Security Recommendations for Windows Systems
A strong security posture involves a multi-layered approach that encompasses various aspects of system configuration, user behavior, and ongoing monitoring.
| Recommendation | Description |
|---|---|
| Keep Software Updated | Regularly update operating systems, applications, and drivers to patch vulnerabilities. |
| Enable Windows Defender | Windows Defender provides real-time protection against malware and other threats. |
| Use Strong Passwords | Implement complex passwords and multi-factor authentication for user accounts. |
| Limit Administrative Privileges | Restrict administrative access to only authorized personnel. |
| Implement Network Segmentation | Isolate sensitive systems and data from public networks. |
| Use a Firewall | Configure a firewall to block unauthorized access to the network. |
| Enable System Monitoring | Monitor system logs and events for suspicious activity. |
| Regularly Backup Data | Implement regular data backups to recover from potential data loss. |
| Educate Users | Train users on security best practices and phishing awareness. |
Vulnerability Assessment Checklist
A comprehensive assessment helps identify potential weaknesses that could be exploited.
- Operating System and Software Updates:Are all systems and software components up-to-date with the latest patches and security updates?
- Security Software:Is a robust antivirus solution like Windows Defender enabled and configured effectively?
- User Account Security:Are strong passwords and multi-factor authentication enforced for all user accounts?
- Administrative Privileges:Are administrative privileges restricted to authorized personnel and used only when necessary?
- Network Security:Is network segmentation implemented to isolate sensitive systems? Is a firewall in place to block unauthorized access?
- System Monitoring:Are system logs and events regularly monitored for suspicious activity?
- Data Backup:Are regular data backups implemented to ensure data recovery in case of a security incident?
- User Awareness:Are users trained on security best practices and phishing awareness?
Mitigation and Prevention Flowchart
This flowchart Artikels a structured approach to mitigate the risks associated with the Cisco Talos Windows Policy Loophole.
Step 1: Identify Vulnerable Systems
Use vulnerability scanning tools to identify systems that are susceptible to the loophole.
Conduct a thorough review of system configurations and security settings.
Step 2: Patch and Update Systems
Apply all relevant security updates and patches released by Microsoft.
Verify that the updates have been successfully installed and are effective.
Step 3: Review and Adjust Security Policies
Evaluate existing security policies and ensure they adequately address the loophole.
Make necessary adjustments to policies to strengthen security measures.
Step 4: Implement Security Controls
Deploy appropriate security controls such as firewalls, intrusion detection systems, and network segmentation.
Configure these controls to effectively mitigate the risks associated with the loophole.
Step 5: Monitor and Review
Regularly monitor system logs and security events for any suspicious activity.
Conduct periodic reviews of security controls and policies to ensure their effectiveness.
Future Implications
The Cisco Talos Windows Policy Loophole, while seemingly a specific vulnerability, has far-reaching implications for the future of cybersecurity. Its existence highlights the ongoing battle between attackers and defenders, with attackers constantly seeking new ways to exploit vulnerabilities, while defenders strive to stay ahead of the curve.
This loophole serves as a stark reminder of the need for continuous vigilance and adaptation in the face of evolving threats.
The Evolving Landscape of Cyber Threats
The landscape of cyber threats is constantly evolving, with attackers becoming more sophisticated and their tactics more complex. The Cisco Talos Windows Policy Loophole exemplifies this trend. Attackers are no longer limited to traditional methods of exploiting vulnerabilities. Instead, they are actively seeking out and exploiting vulnerabilities in the core infrastructure of operating systems, such as the Windows Policy Loophole.
This shift in focus requires a corresponding shift in defensive strategies, moving beyond traditional security measures and embracing more proactive approaches.
Ongoing Research and Development in Cybersecurity
The discovery and exploitation of the Cisco Talos Windows Policy Loophole have spurred further research and development in cybersecurity. Researchers are actively exploring new ways to identify and mitigate similar vulnerabilities. This includes the development of advanced security tools and techniques that can detect and prevent exploitation of these types of loopholes.
Additionally, there is an increased focus on security awareness training for users, emphasizing the importance of recognizing and avoiding potential threats.
Potential Future Impact of the Loophole, Cisco talos windows policy loophole
The potential future impact of the Cisco Talos Windows Policy Loophole is significant. The vulnerability could be exploited by attackers to gain unauthorized access to systems, steal sensitive data, and launch further attacks. This could have a devastating impact on individuals, businesses, and governments.
“The Cisco Talos Windows Policy Loophole serves as a stark reminder of the need for continuous vigilance and adaptation in the face of evolving threats.”
Examples of Real-World Impact
The WannaCry ransomware attack, which exploited a vulnerability in the Windows operating system, is a prime example of the potential impact of a security loophole. The attack crippled businesses and organizations worldwide, causing billions of dollars in damage. The NotPetya ransomware attack, which also exploited a vulnerability in the Windows operating system, caused even more damage, with an estimated cost of over $10 billion.
These attacks demonstrate the real-world impact of security vulnerabilities and the importance of proactive security measures.