Cyber Security
-
Technology

OpenAI Hacked: Internal Communications Compromised
OpenAI hacked internal communications: a chilling reminder of the vulnerabilities inherent in the digital age. The incident, which occurred on…
Read More » -
Email Security

Secure Your Email: Top-Rated Backup Services
Secure your email top rated backup service – In today’s digital world, email is more than just a communication tool;…
Read More » -
Technology

Deepfake Attacks and Cyber Extortion: Mounting Risks
Deepfake attacks and cyber extortion are creating mounting risks, threatening individuals, businesses, and even national security. These sophisticated attacks exploit…
Read More » -
Cybersecurity

Cisco Talos Uncovers New Malware from Lazarus Group
Cisco talos lazarus group new malware – Cisco Talos, the threat intelligence arm of Cisco, has uncovered a new malware…
Read More » -
Cyber Security

XLoader Malware Targets macOS Disguised as Officenote App
XLoader malware variant targets macOS disguised as Officenote app, a seemingly harmless note-taking application. This malicious software poses a serious…
Read More » -
Cyber Security

HTTP/2 Rapid Reset DDoS Attack: A New Threat
Http2 rapid reset ddos attack – HTTP/2 Rapid Reset DDoS attacks are a new breed of cyber threat leveraging the…
Read More » -
Cybersecurity

SentinelOne vs Carbon Black: Endpoint Security Showdown
SentinelOne vs Carbon Black: the ultimate endpoint security showdown. In today’s digital landscape, where cyber threats are constantly evolving, safeguarding…
Read More » -
Cybersecurity
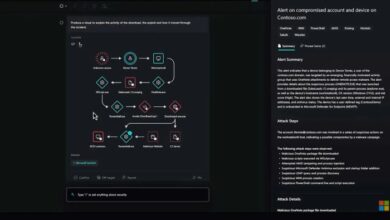
Microsoft Security Copilot Experience Center: Your Security Ally
Microsoft Security Copilot Experience Center is your one-stop shop for comprehensive security solutions, empowering you to navigate the complex world…
Read More » -
Cybersecurity

Google Cloud CSA AI Cyber Security Report: Protecting Your Data in the Age of AI
The Google Cloud CSA AI Cyber Security Report takes center stage, delving into the critical intersection of artificial intelligence and…
Read More » -
Mac Security

Mac Security Best Practices: Protect Your Data
Mac Security Best Practices: Protect Your Data. We all know Macs are known for their sleek design and user-friendly interface,…
Read More »


