cybersecurity
-
Cybersecurity

Massive Ransomware Operation Targets VMware ESXi
Massive ransomware operation targets VMware ESXi, a chilling headline that sent shockwaves through the tech world. This attack wasn’t just…
Read More » -
Cybersecurity

Contis Fragmentation: More Dangerous Than Ever?
Conti reforms into several smaller groups are they now more dangerous than ever – Conti’s reforms into several smaller groups…
Read More » -
Cybersecurity
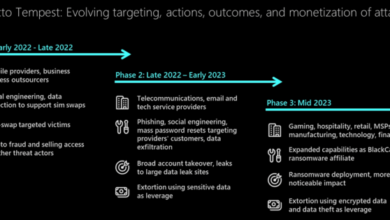
Microsoft Octo Tempest Threat Actor: A Cybersecurity Threat
Microsoft Octo Tempest threat actor is a sophisticated and persistent cyber threat group known for its targeted attacks against various…
Read More » -
Technology

IBM Executive on the Future of Cybersecurity
Ibm executive on future cybersecurity – IBM Executive on the Future of Cybersecurity: In an era where digital threats are…
Read More » -
Cybersecurity

Cyber Security Trends UK: Navigating the Evolving Threat Landscape
Cyber Security Trends UK takes center stage as the digital world evolves, presenting a landscape of constant change. From the…
Read More » -
Data Security

Data Recovery: Defending Against Data Breaches with Rubrik
Data recovery data breaches rubrik takes center stage in today’s digital landscape, where the threat of data breaches looms large.…
Read More » -
Technology

White House Report: Memory Safe Programming Languages for Secure Software
White house report memory safe programming languages – The White House report on memory safe programming languages has ignited a…
Read More » -
Technology

Study Reveals Most Vulnerable IoT Connected Assets
The Internet of Things (IoT) has exploded in recent years, connecting our homes, businesses, and even our bodies in ways…
Read More » -
Cybersecurity

Cybersecurity: FBI & Homeland Security United
Cybersecurity fbi homeland security – Cybersecurity: FBI & Homeland Security United – these three entities are intertwined in a complex…
Read More »



