cybersecurity
-
Technology

Google Workspace Vulnerability Exposes Accounts
Google workspace vulnerability accounts exposed – Google Workspace Vulnerability Exposes Accounts: Imagine a world where your emails, files, and even…
Read More » -
Technology

IBM Expands Cloud Security and Compliance Center
IBM Expands Cloud Security and Compliance Center, a move that signals a significant shift in the company’s commitment to bolstering…
Read More » -
Cybersecurity
Israel Threat Actors Target Organizations with Email Attacks
Israel threat actors email attacks are a growing concern for organizations in the region. These attacks often leverage sophisticated phishing…
Read More » -
Cybersecurity

CBA AI Cybersecurity: An Interview with Andrew Pade
Cba ai cybersecurity andrew pade interview – CBA AI Cybersecurity: An Interview with Andrew Pade delves into the crucial role…
Read More » -
Cybersecurity
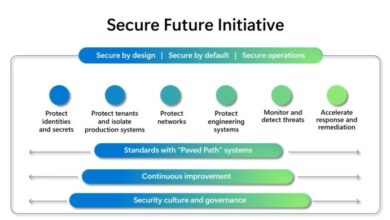
Microsoft Secure Future Initiative Report: Shaping a Safer Digital World
The Microsoft Secure Future Initiative Report delves into the ever-evolving landscape of cybersecurity, highlighting the crucial role technology plays in…
Read More » -
Cybersecurity

Ransomware Attackers Target Backups: A Growing Threat
Ransomware attackers target backups, a chilling reality that has sent shockwaves through the digital world. This tactic, a strategic shift…
Read More » -
Cybersecurity

Cybersecurity Training: IBM & ISC2
Cybersecurity training ibm isc2 – Cybersecurity training from IBM and ISC2 is your passport to a rewarding career in a…
Read More » -
Cybersecurity

CrowdStrike Outage: $54 Billion Cost for Top Companies
Crowdstrike outage reportedly cost over dollar54 billion for top companies alone – CrowdStrike outage reportedly cost over $54 billion for…
Read More » -
Cybersecurity

Kaspersky Report: Top Cyber Threats Facing SMBs
Kaspersky report top cyber threats smbs – Kaspersky Report: Top Cyber Threats Facing SMBs reveals a sobering reality: small and…
Read More » -
Cybersecurity

Google Cloud CISO Nick Godfrey Interview: Insights on Cybersecurity
Google Cloud CISO Nick Godfrey interview provides a fascinating glimpse into the world of cybersecurity at one of the world’s…
Read More »


