security
-
Technology

Leaders Banning AI-Generated Code: A Controversial Trend
Leaders banning ai generated code – Leaders banning AI-generated code is a topic that’s sparking heated debate in the tech…
Read More » -
Security
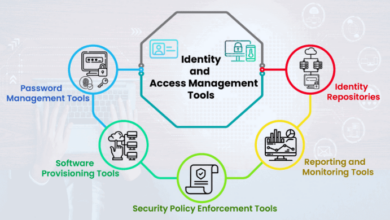
Best Open Source IAM Tools: Secure Your Digital Assets
Best open source IAM tools are the unsung heroes of the digital world, quietly safeguarding our data and access rights.…
Read More » -
Apple News
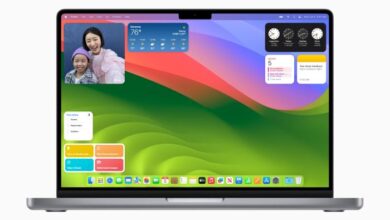
iOS 18 & macOS 15: Whats New in System Settings?
Heres what could be new in ios 18 and macos 15 system settings – Here’s what could be new in…
Read More » -
Apple
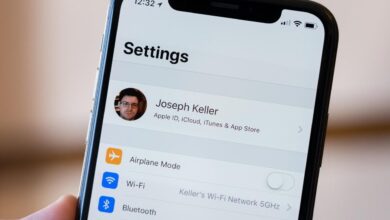
How to Change Your Apple ID on iPhone or iPad
How change apple id your iphone or ipad – How to Change Your Apple ID on iPhone or iPad is…
Read More » -
Technology

Your New M3 MacBook Air: macOS Update on Arrival
Your brand new M3 MacBook Air will receive a macOS update the moment it gets through the door, setting the…
Read More » -
Tech & Gadgets
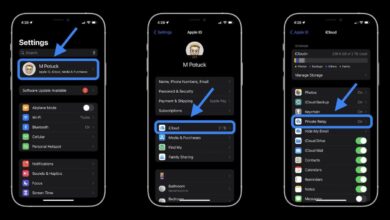
iCloud Private Relay Down: Its Not Just You
Icloud private relay down its not just you – iCloud Private Relay Down: It’s Not Just You sets the stage…
Read More » -
Security & Privacy
LastPass Premium vs Free: Which is Right for You?
LastPass Premium vs Free: Choosing the right password manager can be a tough decision, especially when you’re faced with a…
Read More » -
Technology

1Password: Password Free Future?
1password password free future – 1Password: Password Free Future? sets the stage for this enthralling narrative, offering readers a glimpse…
Read More » -
Technology

Digital Drivers License Rollout Stumbles as Florida Suspends Support
Digital drivers license rollout in us hits a hurdle as florida suspends support. The nationwide push to adopt digital driver’s…
Read More » -
DevOps

GitLab CISO Automation: DevSecOps for Modern Teams
Gitlab ciso automation devops – GitLab CISO automation DevSecOps is the new frontier in securing modern development workflows. This approach…
Read More »


