What Does a DBA Do All Day? A Look at the Behind-the-Scenes Work
What does a DBA do all day? It’s a question that often sparks curiosity, as database administrators work behind the scenes to ensure the smooth operation of the systems we rely on daily. From managing vast amounts of data to ensuring its integrity and security, DBAs play a crucial role in keeping our digital world running.
Imagine a vast library, filled with countless books, each containing a wealth of information. A database administrator is like the librarian, responsible for organizing, maintaining, and ensuring the accessibility of this information. They are the guardians of data, ensuring its accuracy, security, and efficient use.
Database Administration
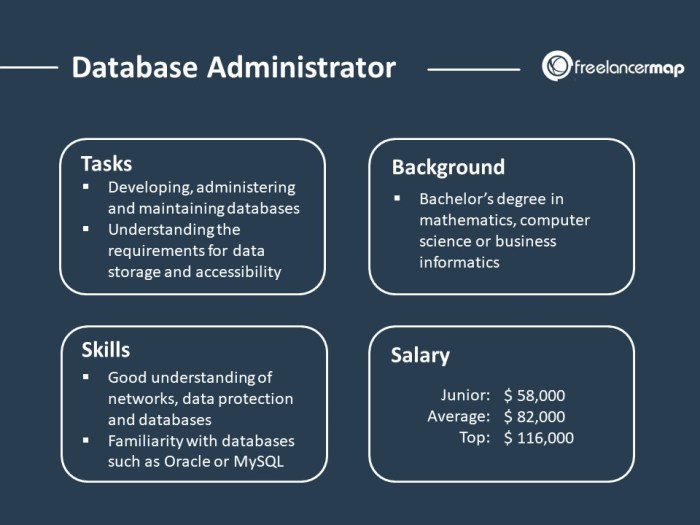
Database administration, often shortened to DBA, is a crucial role in the world of technology. DBAs are the guardians of data, ensuring its integrity, security, and optimal performance. They are the architects and engineers who design, build, maintain, and optimize databases to meet the needs of organizations.
Data Integrity, Security, and Performance
Data integrity, security, and performance are the pillars of effective database management. DBAs strive to ensure that data is accurate, consistent, and reliable. Data integrity is paramount, as errors or inconsistencies can lead to incorrect decisions and costly consequences. Security measures protect sensitive data from unauthorized access, ensuring confidentiality and compliance with regulations.
DBAs are like the behind-the-scenes heroes of the tech world, making sure your data is safe and accessible. They spend their days optimizing databases, troubleshooting performance issues, and ensuring data integrity. Speaking of tech surprises, did you hear about a new version of the Beats Solo headphones just got accidentally revealed in the latest version of iOS ?
It seems even the most meticulous tech giants can have a slip-up. But back to the DBAs, they are essential for any organization that relies on data, and their work is often invisible but crucial to keeping things running smoothly.
Database performance is vital for efficient operations, allowing users to access and process data quickly and effectively.
Types of Databases
Databases come in various forms, each tailored to specific use cases and requirements. Understanding these differences is essential for choosing the right database for a particular application.
Relational Databases
Relational databases are structured using tables with rows and columns, where data is organized in a logical and interconnected manner. They are known for their data integrity and ability to handle complex queries. Examples include MySQL, PostgreSQL, and Oracle Database.
DBAs are the unsung heroes of the tech world, ensuring our data stays safe and accessible. It’s a demanding job, but one that requires a keen eye for detail and a love for problem-solving. Sometimes, though, even DBAs need a break from the complexities of SQL queries and database optimization.
That’s when I turn to gadgets like AirTags, which I thought would be a steal during Prime Day. Unfortunately, the deals weren’t as impressive as I’d hoped, so I decided to check out some alternatives like those mentioned in this article prime day airtag deals a letdown here are 3 tile alternatives id recommend.
Back to my database, though! I’ve got a backup to run and some performance tuning to do.
NoSQL Databases
NoSQL databases offer a more flexible and scalable approach to data storage. They are often used for handling large volumes of unstructured data, such as social media posts, sensor data, and website logs. Common NoSQL databases include MongoDB, Cassandra, and Redis.
Cloud-Based Databases
Cloud-based databases provide a hosted solution, offering scalability, flexibility, and cost-effectiveness. These databases are managed by cloud providers, eliminating the need for on-premises infrastructure. Popular cloud database services include Amazon RDS, Google Cloud SQL, and Microsoft Azure SQL Database.
Daily Tasks
A Database Administrator’s (DBA) day is a whirlwind of activity, encompassing a broad spectrum of tasks that ensure the smooth functioning and optimal performance of databases. From routine maintenance to troubleshooting critical issues, a DBA’s responsibilities are essential for any organization that relies on data.
Typical Daily Tasks
The daily tasks of a DBA are diverse and often dictated by the specific needs of the organization and the database systems they manage. However, there are some common activities that most DBAs perform on a regular basis.
- Monitoring Database Performance:DBAs regularly monitor the performance of databases to identify any bottlenecks or issues that could impact application performance. This involves analyzing metrics like CPU usage, disk I/O, and query execution times.
- Backup and Recovery:DBAs are responsible for implementing and maintaining backup procedures to ensure data integrity and recoverability in case of system failures or data loss. This includes scheduling regular backups, testing the restoration process, and managing backup storage.
- Security Auditing:Maintaining data security is paramount. DBAs conduct regular security audits to identify vulnerabilities and implement necessary security measures. This includes reviewing user access permissions, monitoring for suspicious activity, and implementing encryption protocols.
- Performance Tuning:DBAs optimize database performance by analyzing query execution plans, identifying slow queries, and implementing indexing strategies to improve query efficiency. They also work to optimize database configurations to ensure optimal resource utilization.
- Troubleshooting:DBAs troubleshoot database issues, including performance problems, data corruption, and connectivity errors. They diagnose the root cause of the issue, implement solutions, and document the resolution process for future reference.
- Database Administration:DBAs manage the day-to-day operations of databases, including user account management, schema design, and database upgrades. This also includes implementing new database features, managing database versions, and ensuring compatibility with application systems.
Frequency and Tools
The frequency of these tasks can vary depending on the size and complexity of the database environment. Some tasks, like monitoring, are performed continuously, while others, like database upgrades, are less frequent. DBAs use a variety of tools to perform their tasks, including:
| Task | Frequency | Tools |
|---|---|---|
| Monitoring Database Performance | Continuous | Database Management System (DBMS) tools, performance monitoring tools (e.g., Oracle Enterprise Manager, SQL Server Management Studio) |
| Backup and Recovery | Daily, Weekly, Monthly | Backup and recovery tools (e.g., Oracle RMAN, SQL Server Backup and Restore) |
| Security Auditing | Regularly (e.g., monthly, quarterly) | Security auditing tools (e.g., Nessus, OpenVAS), database security features |
| Performance Tuning | As needed | Query analyzers, performance tuning tools, database explain plans |
| Troubleshooting | As needed | Database error logs, debugging tools, network monitoring tools |
| Database Administration | Ongoing | Database Management System (DBMS) tools, scripting languages (e.g., SQL, PL/SQL) |
Routine Maintenance Procedures, What does a dba do all day
In addition to their daily tasks, DBAs are also responsible for performing routine maintenance procedures to ensure the health and stability of the database environment.
- Backups:Regular backups are crucial for data recovery. DBAs typically schedule full backups, incremental backups, and log backups at different frequencies. These backups are tested periodically to ensure they can be restored successfully.
- Performance Tuning:DBAs conduct regular performance tuning activities, such as analyzing query plans, optimizing database configurations, and creating indexes to improve query performance. They also monitor database resource utilization to identify potential bottlenecks.
- Security Audits:Regular security audits help identify potential vulnerabilities and ensure the database is secure. This includes reviewing user permissions, checking for unauthorized access attempts, and implementing security patches.
- Database Updates and Patches:DBAs apply updates and patches to databases to fix bugs, enhance security, and improve performance. They carefully plan and execute these updates to minimize downtime and ensure compatibility with existing applications.
Problem Solving and Troubleshooting
Database administrators are often called upon to solve problems and troubleshoot issues that arise within the database environment. This can involve anything from performance bottlenecks to data corruption, and requires a combination of technical expertise, analytical skills, and problem-solving abilities.
Common Database Problems and Their Root Causes
Database problems can stem from various sources, ranging from user errors to system malfunctions. Here are some common issues and their potential root causes:
- Performance Issues:Slow query execution, high resource utilization, and database lock contention are common performance problems. These can be caused by poorly optimized queries, inadequate hardware resources, or excessive concurrent access to the database.
- Data Corruption:Data integrity can be compromised due to hardware failures, software bugs, or human errors. This can lead to data loss, inconsistencies, or inaccurate results.
- Security Breaches:Unauthorized access, data leaks, and denial-of-service attacks are serious security threats. These can be caused by weak passwords, vulnerabilities in the database system, or malicious attacks.
- Backup and Recovery Issues:Inconsistent or incomplete backups can lead to data loss during a disaster or system failure. Improper recovery procedures can also result in data corruption or loss.
Troubleshooting Techniques
Troubleshooting database issues involves a systematic approach to identify the root cause and implement a solution. Here are some common techniques:
- Database Logs:Analyzing database logs provides valuable insights into system events, errors, and performance metrics. By examining log entries, DBAs can identify patterns, pinpoint problematic queries, and diagnose the cause of database issues.
- Performance Monitoring Tools:Monitoring tools collect and analyze real-time performance metrics, such as CPU utilization, memory usage, and disk I/O. These tools help DBAs identify bottlenecks, track performance trends, and proactively address potential problems.
- Query Optimization:DBAs can optimize queries to improve performance by using appropriate indexes, minimizing data access, and reducing query complexity. This involves analyzing query plans, identifying slow-performing queries, and rewriting them for better efficiency.
- Database Configuration Tuning:Configuring database parameters, such as buffer pool size, cache settings, and concurrency levels, can significantly impact performance. By adjusting these parameters, DBAs can optimize the database for specific workloads and improve overall efficiency.
- Replication and High Availability:Implementing replication and high availability solutions ensures data redundancy and minimizes downtime. These techniques provide failover mechanisms and data backups, protecting the database from failures and ensuring continuous operation.
Analyzing Database Logs and Performance Metrics
Database logs and performance metrics provide critical information for troubleshooting and performance optimization.
- Database Logs:Logs contain detailed records of database events, including transactions, errors, and system activities. DBAs can analyze log entries to identify specific errors, track database operations, and diagnose problems. For example, examining the error log can help pinpoint the cause of a database crash or identify specific query errors.
- Performance Metrics:Monitoring tools provide real-time insights into database performance. Key metrics include CPU utilization, memory usage, disk I/O, and query execution times. Analyzing these metrics helps DBAs identify bottlenecks, track performance trends, and proactively address potential issues. For example, high CPU utilization could indicate a poorly optimized query or insufficient hardware resources.
Database Design and Optimization
Database design and optimization are crucial aspects of database administration, ensuring that data is stored efficiently, accessed quickly, and protected from corruption. A well-designed database is the foundation for a reliable and performant application, while optimization techniques can significantly improve its speed and efficiency.
Database Design Principles
Database design involves planning and creating the structure of a database, considering the data to be stored and the ways it will be used. The goal is to create a logical and efficient structure that meets the specific requirements of the application.
- Normalization:Normalization is a process of organizing data in a database to reduce redundancy and improve data integrity. It involves breaking down large tables into smaller, related tables, ensuring that each attribute (column) depends only on the primary key of the table.
This process helps to minimize data duplication, making it easier to update and maintain the database. There are different levels of normalization, with higher levels generally leading to more complex designs.
- Data Modeling:Data modeling involves creating a visual representation of the data structure, including entities, attributes, and relationships. This model serves as a blueprint for the database design, helping to ensure that the database meets the application’s requirements. There are various data modeling techniques, including entity-relationship diagrams (ERDs) and Unified Modeling Language (UML) diagrams.
Database Schema Design
The database schema is the blueprint for the database, defining the tables, columns, relationships, and constraints. Designing a database schema requires careful consideration of the data requirements and how the data will be accessed. The diagram illustrates the steps involved in designing and implementing a database schema:
1. Requirements Gathering
Understanding the application’s data requirements is the first step. This involves identifying the entities, attributes, and relationships between them.
2. Data Modeling
Creating a data model using techniques like ERDs helps to visualize the data structure and relationships.
3. Schema Design
Based on the data model, the database schema is designed, defining the tables, columns, and constraints.
4. Implementation
The schema is implemented in the database management system (DBMS), creating the tables and defining the relationships and constraints.
5. Testing and Validation
The schema is tested and validated to ensure it meets the requirements and performs as expected.
Database Optimization Techniques
Database optimization aims to improve the performance of the database by reducing query execution time, minimizing resource consumption, and enhancing data access speed. There are various techniques used for database optimization, including:
- Indexing:Indexing involves creating a data structure that allows for quick retrieval of data based on specific values. Indexes are like directories in a library, enabling the database to quickly locate the relevant data without searching through the entire table.
- Query Optimization:Query optimization involves analyzing and rewriting SQL queries to improve their execution efficiency. The DBMS uses a query optimizer to determine the most efficient execution plan for each query, minimizing the number of disk accesses and processing steps.
- Database Partitioning:Partitioning involves dividing a large table into smaller, manageable partitions based on specific criteria. This technique can improve query performance by allowing the DBMS to focus on the relevant partition, reducing the amount of data that needs to be scanned.
Security and Compliance
Database security is a critical aspect of database administration. A DBA is responsible for implementing and maintaining security measures to protect sensitive data from unauthorized access, modification, or deletion. This involves understanding common threats and vulnerabilities, complying with industry regulations, and continuously evaluating and updating security practices.
Database Security Measures
Database administrators employ various security measures to safeguard database systems. These measures aim to protect data from unauthorized access, modification, and deletion, while ensuring data integrity and availability.
DBAs are like the behind-the-scenes heroes of the data world, ensuring everything runs smoothly and efficiently. One of their key tools is PowerShell, a scripting language that allows them to automate tasks and manage databases with incredible precision. If you’re curious about mastering this powerful tool, check out powershell the smart persons guide , which dives into the essentials for database administrators.
From backups and performance tuning to security and automation, PowerShell empowers DBAs to take control and streamline their daily tasks.
- Access Control:Restricting access to database objects based on user roles and permissions. This ensures that only authorized individuals can access specific data and perform specific actions. For example, a developer might have read-only access to a database, while an administrator has full access to manage the database.
- Data Encryption:Encrypting data at rest and in transit to protect it from unauthorized access even if the database is compromised. This involves using encryption algorithms to transform data into an unreadable format, making it incomprehensible to unauthorized users. Encryption can be implemented at various levels, including database storage, network communication, and application layers.
- Auditing and Monitoring:Tracking user activities and system events to identify potential security breaches and suspicious behavior. This involves logging user logins, data access attempts, changes to database configuration, and other relevant events. By analyzing these logs, DBAs can detect anomalies and investigate security incidents.
- Security Patching and Updates:Regularly applying security patches and updates to address known vulnerabilities and improve system security. This involves keeping the database software, operating system, and other related components up-to-date with the latest security fixes. Regularly patching systems is essential to mitigate emerging threats and protect against known vulnerabilities.
- Database Firewall:Implementing a firewall to control network traffic and prevent unauthorized access to the database. This involves setting up rules to block or allow specific connections based on IP addresses, ports, and protocols. A firewall acts as a barrier between the database and the outside world, protecting it from malicious attacks.
Common Database Security Threats and Vulnerabilities
Databases are susceptible to various security threats and vulnerabilities that can compromise data integrity and availability. Understanding these threats is crucial for implementing effective security measures.
- SQL Injection:A common attack where malicious code is injected into data input fields to manipulate database queries and gain unauthorized access. For example, an attacker might inject code into a login form to bypass authentication and access sensitive data.
- Cross-Site Scripting (XSS):A vulnerability that allows attackers to inject malicious scripts into web applications to steal user credentials or hijack user sessions. These scripts can be embedded in web pages or forms and executed when a user interacts with the application.
- Denial of Service (DoS):An attack that aims to overwhelm a database server with excessive traffic, making it unavailable to legitimate users. This can be achieved by sending a large number of requests to the server, overloading its resources and causing it to crash or become unresponsive.
- Data Breaches:Unauthorized access to sensitive data, often through exploiting vulnerabilities in the database or application security. Data breaches can result in significant financial losses, reputational damage, and legal consequences.
- Insider Threats:Unauthorized access to sensitive data by authorized users with malicious intent. This can involve employees with access to confidential data who abuse their privileges for personal gain or sabotage. Insider threats can be challenging to detect and prevent as they often exploit legitimate access privileges.
Compliance with Industry Regulations and Standards
DBAs must ensure that database systems comply with relevant industry regulations and standards related to data privacy and security. These regulations aim to protect sensitive data and ensure responsible data handling practices.
- General Data Protection Regulation (GDPR):A comprehensive data protection law in the European Union that sets strict rules for handling personal data. GDPR requires organizations to implement robust security measures, obtain consent for data processing, and provide individuals with control over their data.
- California Consumer Privacy Act (CCPA):A data privacy law in California that grants consumers certain rights regarding their personal data, including the right to access, delete, and opt-out of the sale of their data. CCPA requires organizations to implement security measures to protect personal data and comply with consumer requests.
- Payment Card Industry Data Security Standard (PCI DSS):A set of security standards for organizations that handle credit card data. PCI DSS mandates specific security controls to protect cardholder data, including encryption, access control, and vulnerability scanning.
- Health Insurance Portability and Accountability Act (HIPAA):A US law that sets standards for protecting sensitive health information. HIPAA requires organizations to implement security measures to safeguard electronic protected health information (ePHI), including access controls, encryption, and data integrity controls.
Working with Developers and Users
A DBA’s role extends beyond just managing databases. They are essential collaborators with software developers and users, ensuring smooth operation and data integrity. Effective communication and collaboration are key to success.
Collaborating with Developers
The DBA works closely with developers to ensure the database design and implementation align with the application’s requirements. This involves understanding the application’s data needs, providing guidance on database schema design, and optimizing database performance for the application’s specific workload.
- Database Schema Design:The DBA advises developers on creating a database schema that is efficient, scalable, and meets the application’s data storage and retrieval needs. They may suggest normalization techniques, data types, and indexing strategies to optimize performance.
- Performance Tuning:DBAs work with developers to identify and resolve performance bottlenecks. They may suggest query optimization techniques, index tuning, and database configuration changes to improve application response times.
- Data Migration:When applications are updated or migrated to new platforms, the DBA plays a crucial role in planning and executing data migration processes, ensuring data integrity and minimal downtime.
Communicating with Users
Clear and concise communication with users is vital for a DBA. It helps in managing expectations, resolving issues quickly, and ensuring user satisfaction.
- Reporting Database Issues:DBAs communicate database issues to users in a clear and understandable manner, providing context and potential impact. This allows users to plan accordingly and minimize disruptions to their work.
- Explaining Database Changes:When database changes are planned, DBAs communicate the impact of these changes to users, including potential downtime or data access limitations. This helps users prepare and avoid unexpected disruptions.
- User Training:DBAs may provide user training on how to access and utilize the database effectively, promoting data integrity and efficiency.
Managing User Access and Permissions
DBAs are responsible for managing user access to the database, ensuring data security and integrity. This involves defining roles and permissions, granting access based on user needs, and auditing access activities.
- Role-Based Access Control (RBAC):DBAs implement RBAC to define roles and assign permissions based on job functions. This ensures that users only have access to the data they need, minimizing the risk of unauthorized access or data modification.
- User Authentication and Authorization:DBAs configure user authentication and authorization mechanisms, such as passwords and multi-factor authentication, to prevent unauthorized access to the database.
- Access Auditing:DBAs monitor and audit user access activities to detect any suspicious behavior or unauthorized access attempts. This helps in identifying and mitigating security threats.
The Evolving Landscape of Database Administration: What Does A Dba Do All Day
The realm of database administration is constantly evolving, driven by the rapid advancements in technology, particularly in cloud computing and the emergence of new data management paradigms. These changes are reshaping the skills and responsibilities of DBAs, demanding a shift in focus and a continuous pursuit of knowledge to remain relevant and effective in this dynamic field.
The Impact of Cloud Computing
Cloud computing has profoundly impacted database administration, offering a paradigm shift in how databases are provisioned, managed, and scaled. Cloud database services, provided by major vendors like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), offer a range of advantages, including:
- Scalability and Elasticity:Cloud databases can be easily scaled up or down based on demand, eliminating the need for upfront infrastructure investments and allowing for flexible resource allocation.
- Cost-Effectiveness:Pay-as-you-go pricing models and reduced infrastructure costs make cloud databases an attractive option for organizations of all sizes.
- Simplified Management:Cloud providers handle many aspects of database management, such as patching, backups, and security, freeing DBAs to focus on higher-level tasks.
- Global Availability:Cloud databases offer high availability and disaster recovery capabilities, ensuring data accessibility from anywhere in the world.
However, the shift to cloud also presents new challenges for DBAs. They need to adapt to new technologies, learn cloud-specific tools and services, and understand the intricacies of managing databases in a distributed, cloud-based environment.
Emerging Technologies
The landscape of database administration is further evolving with the emergence of new technologies like:
- NoSQL Databases:These databases, designed for handling unstructured data, have gained popularity for applications like social media, e-commerce, and real-time analytics. DBAs need to understand the different NoSQL database models, such as document, key-value, and graph databases, and be proficient in managing and optimizing these systems.
- Big Data and Analytics:The explosion of data has led to the rise of big data technologies like Hadoop and Spark. DBAs need to be familiar with these platforms and understand how to manage and analyze large datasets efficiently.
- Artificial Intelligence (AI) and Machine Learning (ML):AI and ML are being increasingly used in database management, automating tasks like performance optimization, anomaly detection, and security threat identification. DBAs need to understand the principles of AI and ML and be able to leverage these technologies to enhance database operations.
Skills and Knowledge for Success
To thrive in this evolving landscape, DBAs need to acquire a diverse set of skills and knowledge:
- Cloud Computing Expertise:Proficiency in cloud platforms like AWS, Azure, and GCP is essential, including knowledge of cloud database services, security best practices, and cost optimization strategies.
- NoSQL Database Management:Understanding the different NoSQL database models and gaining experience in managing and optimizing these systems is crucial.
- Big Data and Analytics:Familiarity with big data technologies like Hadoop and Spark, along with the ability to analyze large datasets efficiently, is becoming increasingly important.
- AI and ML Concepts:A basic understanding of AI and ML principles and their applications in database management can enhance efficiency and automation.
- Automation and Scripting:DBAs need to be proficient in automation tools and scripting languages to streamline repetitive tasks and improve efficiency.
- Security and Compliance:Understanding database security best practices, compliance regulations, and data privacy laws is essential to protect sensitive information.
- Problem-Solving and Troubleshooting:Strong analytical and problem-solving skills are critical for diagnosing and resolving database issues.
Continuous Professional Development
Staying ahead in database administration requires continuous learning and professional development. DBAs can leverage various resources to enhance their skills:
- Online Courses and Certifications:Platforms like Coursera, Udemy, and edX offer a wide range of database administration courses and certifications, covering topics like cloud databases, NoSQL databases, and big data technologies.
- Industry Events and Conferences:Attending industry events and conferences provides opportunities to network with peers, learn about the latest trends, and gain insights from industry experts.
- Professional Organizations:Joining professional organizations like the International DBA Group (IDBG) or the Database Administrators Association (DBA) provides access to resources, networking opportunities, and industry updates.
- Open-Source Projects:Contributing to open-source projects can provide practical experience and expose DBAs to new technologies and best practices.