What Is Data Loss Prevention: Protecting Your Digital Assets
What is data loss prevention? It’s the proactive approach to safeguarding your sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction. Imagine your company’s financial records, customer data, or confidential research falling into the wrong hands. Data loss prevention (DLP) solutions act as digital guardians, implementing security measures to prevent such breaches and ensure the integrity of your valuable information.
In today’s digital world, where data is constantly in motion, DLP has become an essential component of any comprehensive cybersecurity strategy. It’s no longer enough to simply build firewalls and implement antivirus software. DLP goes a step further, actively monitoring and controlling data flow, identifying potential threats, and preventing data loss before it happens.
Definition of Data Loss Prevention (DLP): What Is Data Loss Prevention
Data loss prevention (DLP) is a crucial aspect of cybersecurity that focuses on preventing sensitive information from leaving the organization’s control. It involves implementing technologies and processes to identify, monitor, and block unauthorized data transfers.DLP solutions aim to protect sensitive data by detecting and preventing its unauthorized access, use, disclosure, or modification.
They work by analyzing data in transit and at rest, identifying patterns and anomalies that indicate potential data breaches.
Types of Data Targeted by DLP Solutions
DLP solutions are designed to protect a wide range of sensitive data, including:
- Personally identifiable information (PII):This includes names, addresses, social security numbers, credit card details, and other information that can be used to identify individuals.
- Financial data:This encompasses bank account numbers, transaction records, and other sensitive financial information.
- Intellectual property:This includes trade secrets, patents, research data, and other confidential information that gives a company a competitive edge.
- Customer data:This includes customer lists, purchase history, and other information that can be used to target marketing campaigns or identify customer preferences.
- Employee data:This includes employee records, performance reviews, and other confidential information that can be used to discriminate or harm employees.
Importance of DLP in Today’s Digital Landscape
The importance of DLP has become increasingly paramount in today’s digital landscape due to the following factors:
- Increased reliance on digital data:Organizations increasingly rely on digital data for operations, communication, and decision-making, making data breaches more disruptive and costly.
- Growing number of cyber threats:The rise of sophisticated cyberattacks, such as ransomware and phishing, has increased the risk of data loss and theft.
- Data privacy regulations:Governments worldwide are enacting stricter data privacy regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), imposing significant penalties for data breaches.
- Remote work and cloud computing:The shift towards remote work and cloud computing has created new vulnerabilities, as data is increasingly stored and accessed outside of traditional corporate networks.
Types of Data Loss Prevention
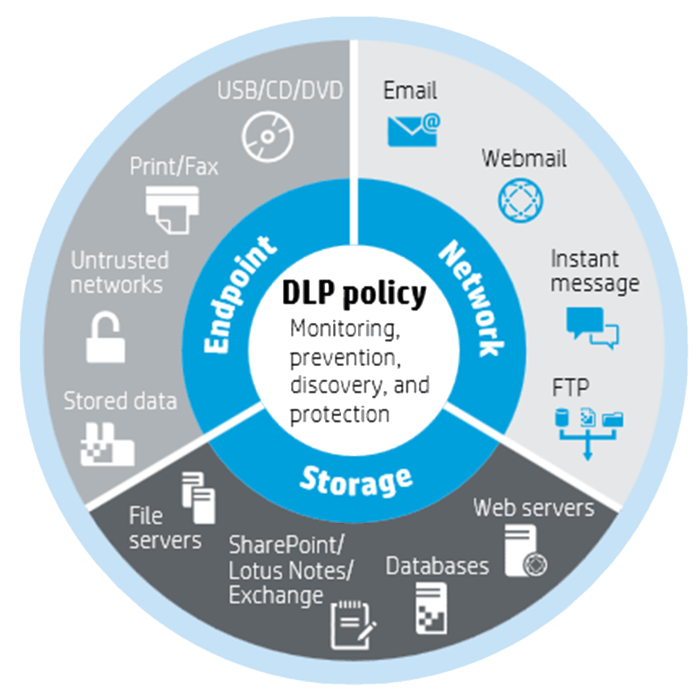
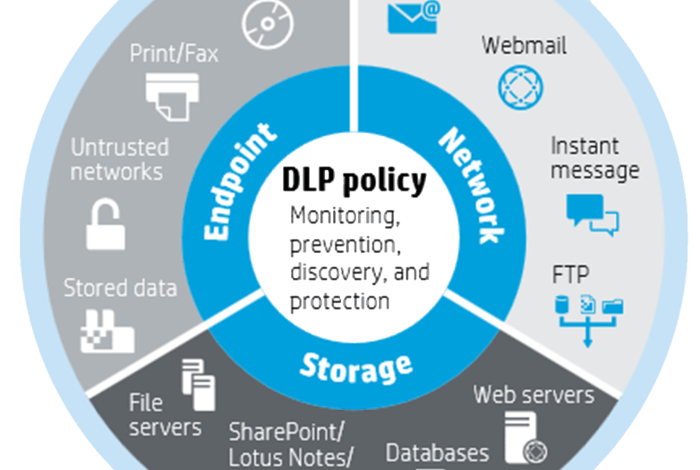
Data loss prevention (DLP) methods are employed to safeguard sensitive data from unauthorized access, use, disclosure, modification, or destruction. These methods can be categorized based on their approach to data protection, offering various levels of security and control.
Network-Based DLP
Network-based DLP solutions monitor network traffic for suspicious activity and prevent data leakage through network connections. These systems work by analyzing data packets passing through the network, identifying patterns indicative of data loss, and blocking or alerting on suspicious activity.
Network-based DLP solutions are typically deployed at the network perimeter, acting as a gatekeeper for data flow. They offer a broad view of data movement within the network, enabling detection of data breaches and unauthorized access attempts.
Strengths of Network-Based DLP
- Provides comprehensive visibility into network traffic, enabling detection of data loss attempts regardless of the endpoint used.
- Offers centralized control over data flow, simplifying policy enforcement and management.
- Can be deployed quickly and easily, with minimal impact on existing network infrastructure.
Weaknesses of Network-Based DLP
- May miss data loss attempts that occur outside the network perimeter, such as through personal devices or cloud services.
- Can be prone to false positives, as it relies on pattern matching and may flag legitimate traffic as suspicious.
- May not be effective against sophisticated attackers who can bypass network security measures.
Endpoint-Based DLP
Endpoint-based DLP solutions focus on protecting data stored and accessed on individual devices, such as laptops, desktops, and mobile phones. These solutions use a combination of software and hardware to monitor data activity on endpoints, detecting and preventing data loss attempts at the source.Endpoint-based DLP solutions typically involve installing software agents on individual devices, which monitor data access, usage, and transfer.
They can identify sensitive data based on predefined rules and policies, preventing unauthorized access, copying, or sharing of data.
Strengths of Endpoint-Based DLP
- Provides granular control over data access and usage on individual devices, offering a higher level of security.
- Can detect and prevent data loss attempts that occur outside the network perimeter, such as through personal devices or cloud services.
- Offers real-time monitoring and control over data activity, allowing for immediate action in case of suspicious behavior.
Weaknesses of Endpoint-Based DLP
- Requires installation and configuration on each endpoint, which can be time-consuming and resource-intensive.
- Can be intrusive and impact user productivity, as it monitors data activity on individual devices.
- May not be effective against sophisticated attackers who can bypass endpoint security measures.
Cloud-Based DLP
Cloud-based DLP solutions are hosted in the cloud and provide data loss prevention capabilities for cloud applications and services. These solutions typically integrate with cloud platforms, such as Google Cloud Platform, Microsoft Azure, and Amazon Web Services, to monitor data activity and enforce data protection policies.Cloud-based DLP solutions offer a flexible and scalable approach to data loss prevention, allowing organizations to protect data across multiple cloud platforms and services.
They typically use a combination of machine learning and artificial intelligence to detect and prevent data loss attempts.
Strengths of Cloud-Based DLP
- Provides a scalable and flexible approach to data loss prevention, enabling organizations to protect data across multiple cloud platforms and services.
- Offers real-time monitoring and control over data activity in the cloud, providing immediate action in case of suspicious behavior.
- Can be easily integrated with existing cloud infrastructure, reducing deployment time and complexity.
Weaknesses of Cloud-Based DLP
- May not be as effective as on-premises solutions in protecting data stored on local devices.
- Reliance on cloud providers for data security and privacy, which may raise concerns about data sovereignty and compliance.
- Can be more expensive than on-premises solutions, especially for organizations with large data volumes.
Content-Aware DLP, What is data loss prevention
Content-aware DLP solutions analyze the content of data to identify sensitive information, such as credit card numbers, social security numbers, and confidential documents. These solutions use a combination of pattern matching, machine learning, and natural language processing to detect sensitive data within files, emails, and other data sources.Content-aware DLP solutions can be deployed as part of network-based, endpoint-based, or cloud-based DLP systems.
They provide a more granular level of data protection by focusing on the content of data rather than just the network traffic or device activity.
Strengths of Content-Aware DLP
- Provides a more accurate and effective way to identify and protect sensitive data, as it analyzes the content of data rather than just the network traffic or device activity.
- Can be used to detect and prevent data loss attempts that involve the use of sophisticated techniques, such as data obfuscation or encryption.
- Offers a higher level of data protection by preventing the unauthorized use or disclosure of sensitive data, even if it is not being transmitted over the network.
Weaknesses of Content-Aware DLP
- Requires a high level of expertise to configure and manage, as it involves complex data analysis techniques.
- Can be computationally intensive, requiring significant processing power to analyze large volumes of data.
- May be prone to false positives, as it relies on pattern matching and may flag legitimate data as sensitive.
Data loss prevention is like a security guard for your digital life, protecting your sensitive information from unauthorized access. Just like you might customize your shoes with a unique look by learning how to make your own studded converse , data loss prevention helps you control what information goes out and how it’s used.
It’s all about making sure your digital world is as secure and personalized as your favorite pair of shoes.
Data loss prevention (DLP) is a crucial aspect of cybersecurity, ensuring sensitive information stays protected. It’s like having a digital gatekeeper, preventing unauthorized access and accidental leaks. Think of it like Laura’s new home mood board, lauras new home mood board , which carefully curates her vision for her dream space.
DLP tools work similarly, carefully filtering and safeguarding your digital assets, ensuring they remain secure and accessible only to those who need them.
Data loss prevention is a crucial aspect of cybersecurity, ensuring that sensitive information doesn’t fall into the wrong hands. It’s like carefully guarding your favorite chilled wines at a New Year’s Eve wine bar, making sure they stay perfectly chilled in a DIY ice bucket.
This DIY ice bucket guide can help you create the perfect setup for your New Year’s Eve party. Just like protecting your data, ensuring your wines stay chilled is essential for a successful celebration.







