How an 8-Character Password Could Be Cracked in Less Than an Hour
How an 8 character password could be cracked in less than an hour – How an 8-character password could be cracked in less than an hour? It might seem like a secure length, but in the digital age, even seemingly strong passwords can be vulnerable. This isn’t about spreading fear, but about understanding the reality of password security.
The truth is, password cracking techniques have become incredibly sophisticated, allowing attackers to break through seemingly robust defenses. We’ll explore the different methods used to crack passwords, how password length and complexity affect security, and most importantly, what you can do to protect yourself.
The most common methods used to crack passwords are brute force, dictionary attacks, and rainbow tables. Brute force attacks involve trying every possible combination of characters until the correct password is found. Dictionary attacks use lists of common words and phrases to try and guess the password.
Rainbow tables are pre-computed tables that store the hash values of millions of passwords, allowing attackers to quickly look up the hash of a password and find the corresponding password.
The Nature of Password Cracking
Password cracking is the process of attempting to discover a password, often without the legitimate user’s knowledge. It’s a technique commonly employed by cybercriminals to gain unauthorized access to sensitive data or systems. The effectiveness of password cracking depends heavily on the strength of the password and the methods employed by the attacker.
Common Password Cracking Methods
Password cracking techniques can be categorized into several approaches, each with its strengths and weaknesses.
- Brute Force Attacks: This method involves systematically trying every possible combination of characters within a given character set until the correct password is found. Brute force attacks are time-consuming, especially for longer and more complex passwords. However, with advancements in computing power and the availability of specialized hardware, brute force attacks are becoming increasingly feasible.
For example, a dedicated password cracking device like a “GPU cluster” can significantly speed up the process, potentially cracking an 8-character password within minutes.
- Dictionary Attacks: This method utilizes a list of common words, phrases, and patterns, known as a “dictionary,” to guess passwords. Dictionary attacks are more efficient than brute force attacks because they target common password choices. For instance, a dictionary attack could use a list of popular names, words, or dates to try and guess a user’s password.
While effective against weak passwords, dictionary attacks are less effective against passwords that use random combinations of characters.
- Rainbow Tables: Rainbow tables are precomputed tables that store the hash values of millions or even billions of passwords. When a hacker obtains a password hash, they can quickly search the table for a matching hash and retrieve the corresponding password.
It’s crazy to think that an 8-character password, something we might use for a casual online account, can be cracked in less than an hour. It’s a stark reminder that even seemingly secure passwords can be vulnerable. While we’re on the topic of security, I just saw this amazing article about Etros best summer looks fresh and fashionable styles , and it got me thinking about how important it is to protect our online identities, especially when we’re sharing our personal information with brands and retailers.
So, remember to choose strong passwords and keep your online accounts safe, even if you’re just browsing for the latest summer fashion trends!
Rainbow tables are efficient and can crack passwords much faster than brute force or dictionary attacks. However, they require significant storage space and are less effective against passwords using strong algorithms or salting.
“A rainbow table is a precomputed table of hash values that can be used to quickly look up the password corresponding to a given hash.”
Factors Influencing Cracking Time: How An 8 Character Password Could Be Cracked In Less Than An Hour
The speed at which a password can be cracked is influenced by a multitude of factors, each playing a crucial role in determining the overall time required for an attacker to gain unauthorized access. Understanding these factors is essential for crafting strong passwords that effectively resist brute-force attacks.
Password Length
The length of a password is arguably the most significant factor determining its strength. A longer password presents a significantly larger space of possible combinations for an attacker to try. This exponential increase in complexity makes brute-force attacks much less feasible.
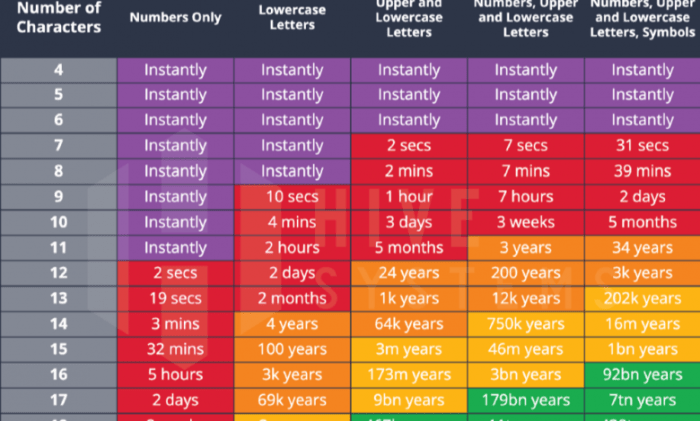
For instance, a password with 8 characters using only lowercase letters has 268(approximately 208 billion) possible combinations. Doubling the length to 16 characters increases the possible combinations to 26 16(approximately 4.3 x 10 23), making it practically impossible to crack using brute-force methods.
It’s shocking to think that an 8-character password, even with a mix of letters and numbers, can be cracked in less than an hour. It’s a reminder that we need to be vigilant about our online security, especially considering the rapid pace of technological advancements.
For instance, if you own an older Apple Watch, it might not be compatible with the latest WatchOS 11 , which could leave you vulnerable to security risks. It’s important to stay informed about these updates and ensure your devices are protected with strong, unique passwords, especially when it comes to sensitive information.
Cracking an 8-Character Password
Let’s delve into the practicalities of cracking an 8-character password. To illustrate, we’ll consider a hypothetical scenario involving a password consisting of eight lowercase letters. We’ll then explore how the time required for cracking changes with increasing password complexity.
Time Required for Cracking an 8-Character Password
To estimate the time needed to crack an 8-character password using brute force, we need to consider the number of possible combinations and the processing power of the computer. For an 8-character password consisting of only lowercase letters, there are 26 possible characters for each position, resulting in 26^8 (approximately 208.8 trillion) potential combinations.
Assuming a modern computer capable of testing one billion (10^9) combinations per second, the estimated time to crack this password would be:
208.8 trillion combinations / 1 billion combinations per second = 208,800 seconds
It’s crazy to think that an 8-character password, even with a mix of letters and numbers, can be cracked in less than an hour. It’s like trying to find a needle in a haystack, but with supercomputers, it’s a lot easier.
So, while you’re busy trying to find a needle in a haystack, why not try to make something beautiful? Check out this make it for less beaded pendant necklace project. You’ll be surprised how much fun it is to create something with your hands, and it’s a lot less stressful than trying to remember a complex password.
Plus, you’ll have a beautiful piece of jewelry to show off! And who knows, maybe you’ll even be inspired to create a new password that’s just as strong as your new necklace.
This equates to approximately 2.4 days. However, this is a simplified calculation, and the actual time can vary depending on factors like the specific hardware used, the efficiency of the cracking software, and any limitations imposed by the target system.
Password Complexity and Cracking Time
The complexity of a password significantly impacts the time required to crack it. Let’s examine how cracking time changes with different password complexities:
- All Lowercase Letters:As discussed earlier, an 8-character password consisting only of lowercase letters would take approximately 2.4 days to crack using brute force on a modern computer.
- Mixed Case:If the password includes both uppercase and lowercase letters, the number of possible combinations increases to 52^8 (approximately 5.3 x 10^13), significantly increasing the cracking time. Assuming the same processing power, cracking a mixed-case password could take several years.
- Letters and Numbers:Adding numbers to the password further increases the complexity. With 36 possible characters (26 letters + 10 digits), the number of combinations becomes 36^8 (approximately 2.8 x 10^13). This would likely take even longer to crack than a mixed-case password.
- Letters, Numbers, and Symbols:Including symbols like punctuation marks and special characters drastically increases the number of possible combinations. With 94 possible characters (26 letters + 10 digits + 58 symbols), the number of combinations becomes 94^8 (approximately 4.5 x 10^15), making the password practically impossible to crack using brute force within a reasonable timeframe.
Mitigation Strategies
While the prospect of an 8-character password being cracked in less than an hour might seem daunting, it’s important to remember that we can significantly enhance our password security through proactive measures. By implementing a combination of robust practices and utilizing readily available tools, we can effectively mitigate the risks associated with weak passwords and protect our sensitive information.
Password Security Practices
It’s essential to adopt sound password security practices to make it significantly harder for attackers to crack your passwords. Here’s a table outlining some of the most effective strategies:
| Practice | Description |
|---|---|
| Use Strong Passwords | Employ a combination of uppercase and lowercase letters, numbers, and symbols. Avoid common words or phrases. |
| Avoid Reusing Passwords | Use a unique password for each online account. This minimizes the impact if one account is compromised. |
| Enable Two-Factor Authentication (2FA) | This adds an extra layer of security by requiring a second verification step, typically a code sent to your phone or email. |
| Regularly Update Passwords | Change your passwords periodically, especially for critical accounts, to stay ahead of potential security breaches. |
| Be Wary of Phishing Attempts | Never provide your password or personal information in response to suspicious emails or links. |
Choosing Strong Passwords
Creating strong passwords is crucial for protecting your online accounts. Here are some examples of how to choose passwords that are difficult to crack:
“MyDogSpot123!”
This password combines uppercase and lowercase letters, numbers, and a symbol, making it significantly harder to guess.
“P@$$wOrd_4Ev3r”
This password utilizes a mix of characters, including symbols and numbers, further increasing its complexity.
Password Managers and Two-Factor Authentication
Password managers are invaluable tools for storing and managing your passwords securely. They generate strong, unique passwords for each of your accounts and encrypt them, protecting them from unauthorized access. Popular password managers include LastPass, 1Password, and Dashlane.Two-factor authentication (2FA) adds an extra layer of security by requiring a second verification step, typically a code sent to your phone or email.
This makes it significantly harder for attackers to access your accounts, even if they manage to obtain your password.
Real-World Implications
The speed at which an 8-character password can be cracked underscores the importance of strong password security. Real-world examples demonstrate the devastating consequences of compromised passwords and the need for robust security measures.
Consequences of Compromised Passwords, How an 8 character password could be cracked in less than an hour
Compromised passwords have a significant impact on individuals, organizations, and society as a whole. The consequences range from minor inconveniences to major financial losses and reputational damage.
- Data Breaches:Hackers exploit weak passwords to gain unauthorized access to sensitive data, leading to data breaches. These breaches can expose personal information such as credit card details, social security numbers, and medical records. The 2017 Equifax data breach, which affected over 147 million individuals, is a prime example of the catastrophic consequences of compromised passwords.
- Identity Theft:Stolen passwords can be used to create fake identities and commit identity theft. Criminals can use compromised credentials to open credit card accounts, obtain loans, or even access bank accounts, leading to financial ruin for victims.
- Financial Losses:Organizations suffer significant financial losses due to data breaches, including legal expenses, regulatory fines, and reputational damage. The cost of recovering from a data breach can be substantial, with estimates ranging from millions to billions of dollars depending on the size and scope of the breach.
- Reputational Damage:Data breaches and security incidents can severely damage an organization’s reputation, leading to loss of customer trust and market share. Companies that experience data breaches often face negative media coverage and public scrutiny, impacting their brand image and future business prospects.







